Cloud Firewall's Intrusion Prevention System (IPS) detects and blocks malicious traffic in real time, such as hacker attacks, Vulnerability Exploits, Brute-force Attacks, Worms, Mining Programs, Backdoor Trojans, and Denial of Service (DoS) attacks. It safeguards your information systems and network architecture from intrusions, preventing unauthorized access, data breaches, and service downtime.
Limitations
Cloud Firewall's IPS cannot decrypt, inspect, or block TLS or SSL encrypted traffic. However, it supports some IPS detection rules based on encrypted fingerprints.
IPS statistics are subject to latency due to data aggregation. To query real-time data, use Log Auditing or log analysis. For more information, see Log Auditing or Query and analyze logs.
When querying data from the last hour, there is a 10-minute latency in the statistics.
For queries spanning more than one hour, the statistics have a 30-minute latency.
For example, if you query data from 12:00:00 to 15:00:00 at 15:00:00, the results exclude data from 14:30:00 to 15:00:00. A query for the range 12:00:00 to 14:30:00 returns all data from that period.
View or modify IPS rules
After you activate Cloud Firewall, its IPS engine is set to Block Mode by default. Cloud Firewall also automatically selects a protection level (Loose, Medium, or Strict) based on your business traffic. Threat Intelligence, Basic Protection, and Virtual Patching are enabled by default.
To manage protection policies, go to the IPS Private IP Tracing page using one of the following methods:
On the IPS page, click the link in the upper-right corner of the Protection Details list.

In the navigation pane on the left, choose .

On the Basic Protection card, view the default IPS rules. To modify a rule based on your business requirements, find the rule and change its setting in the Current Action column. For more information, see IPS Configuration.
Enable IPS private IP tracing
Entry point:
On the Current Action page, click the link in the upper-right corner of the Protection Details list to go to the IPS Private Network Tracing Configuration page.

Enable the feature:
On the IPS Private IP Tracing page, enable tracing for a specific resource to quickly locate an `At-risk Asset` when its internal IP address is not exposed.
NoteUsing `IPS private network tracing` requires enabling both `Internet Firewall` and `NAT Gateway Flow Log` for the asset. For details, see IPS Private Network Tracing Configuration.

Trace sources:
After you enable tracing, you can view the IP addresses of At-risk Assets in the Protection Details list and the Details page on the IPS page.
List
Details


View blocked Internet traffic events
Cloud Firewall provides statistics on inbound and outbound Internet traffic protection for your assets, helping you understand their protection status and ensure their security. You can query blocked traffic data from the last 90 days, with a maximum time range of 31 days per query.
Go to the page. On the Protection Status tab, specify a time range to view protection statistics and details.
The Protection Statistics module shows the total number of attacks, attack type distribution, and blocked data.
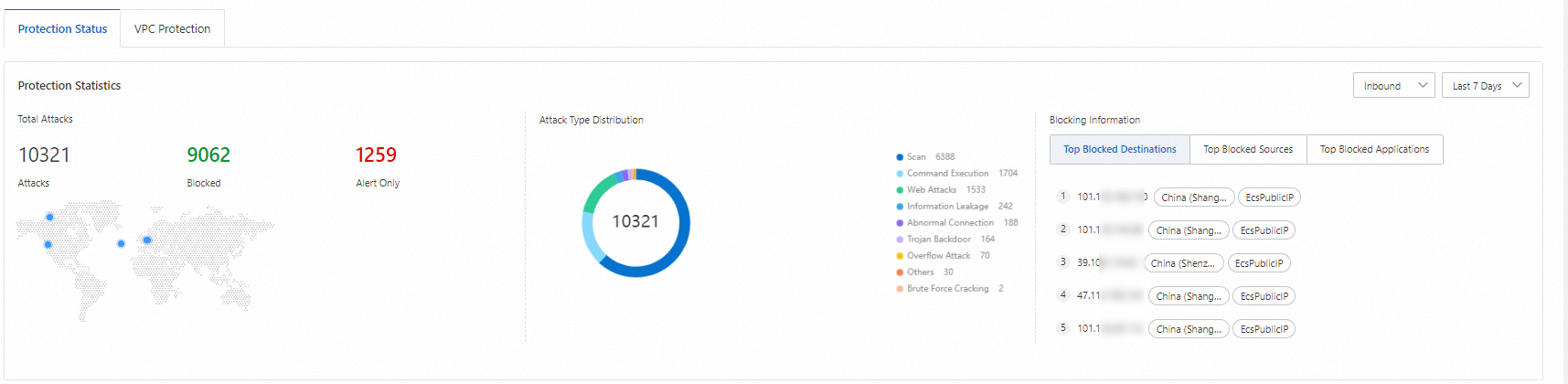
The following metrics describe the blocked data:
Top Blocked Destinations: The top five destination IP addresses in traffic blocked by Cloud Firewall.
Hover over a blocked destination IP address and click the
 icon to go to the Log Audit page. There, you can view details such as the destination port, application type, and action for the traffic to that IP address.
icon to go to the Log Audit page. There, you can view details such as the destination port, application type, and action for the traffic to that IP address.Top Blocked Sources: The top three source types in traffic blocked by Cloud Firewall.
Top Blocked Applications: The top five application types in traffic blocked by Cloud Firewall.
Protection details: Displays details about how Cloud Firewall protects your assets from attack traffic based on the specified query conditions. The details include the risk level, number of events, Source IP, and Destination IP.
 Note
NoteIf a Source IP is an origin IP address of WAF or Anti-DDoS, Cloud Firewall identifies it and displays the WAF Origin IP or DDoS Origin IP label.
In this module, you can perform the following operations:
Search for events: Specify conditions such as Risk Level, Protection Status, Attack Type, Source of Detection, Direction, and Time Range, and click Search to view events that meet the conditions.
View event details: In the Actions column, click Details to view details such as Basic Information and Basic Information. The Attack Payload shows the 5-tuple information and payload content of attack traffic, which helps you trace the attack source and reduce security risks.
Download events: To the right of the search box, click the
 icon to download the filtered events. You can monitor the download progress in the Download Task Management pane in the upper-right corner.
icon to download the filtered events. You can monitor the download progress in the Download Task Management pane in the upper-right corner.Use AI to analyze events: In the AI Analysis column, click the
 icon to use the Security AI Assistant to analyze the event.
icon to use the Security AI Assistant to analyze the event.The analysis results include the following information:
Payload analysis: Includes a brief description of the request and an AI analysis of the request action.

Threat intelligence: The result of comparing the destination address with the threat intelligence library.
NoteThis feature is not supported by Cloud Firewall Premium Edition and Pay-as-you-go Edition.
Attacker intent: The attacker's behavior as predicted by AI.
Protection recommendations: Provides recommendations for Cloud Firewall configurations (such as access control policies and IPS configurations) and asset investigation.
View blocked VPC traffic events
Cloud Firewall provides statistics on traffic protection between virtual private clouds (VPCs), showing the status of both allowed and blocked traffic. You can query up to 90 days of blocked VPC traffic data, with a maximum range of 31 days per query.
Cloud Firewall Premium Edition does not support VPC Firewalls, so it does not show the VPC Protection tab.
Go to the page. On the VPC Protection tab, you can view details about blocked VPC traffic events within a specified time range, such as the event name, risk level, and attack type.

You can perform the following operations:
Search for events: Specify conditions such as Risk Level, Protection Status, Attack Type, and Time, and click Search to view events that meet the conditions.
View event details: In the Action column, click Details to view details such as Basic Information and Attack Payload. The Attack Payload shows the 5-tuple information and payload content of attack traffic, which helps you trace the attack source and reduce security risks.
Download events: To the right of the search box, click the
 icon to download the filtered events. You can monitor the download progress in the Download Task Management pane in the upper-right corner.
icon to download the filtered events. You can monitor the download progress in the Download Task Management pane in the upper-right corner.Use AI to analyze events: In the AI Analysis column, click the
 icon to use the Security AI Assistant to analyze the event.
icon to use the Security AI Assistant to analyze the event.The analysis results include the following information:
Payload analysis: Includes a brief description of the request and an AI analysis of the request action.

Threat intelligence: The result of comparing the destination address with the threat intelligence library.
NoteThis feature is not supported by Cloud Firewall Premium Edition and Pay-as-you-go Edition.
Attacker intent: The attacker's behavior as predicted by AI.
Protection recommendations: Provides recommendations for Cloud Firewall configurations (such as access control policies and IPS configurations) and asset investigation.