安全组在ECS的使用中扮演了云上虚拟防火墙的角色,通过管理安全组和规则,可提供精细化的网络安全隔离与访问控制。
下图示例通过配置两条安全组规则,实现仅允许授权IP远程管理实例,并阻止实例访问公网风险站点的场景。
入方向规则:允许特定IP(
121.XX.XX.XX)通过SSH(22端口)访问实例。出方向规则:拒绝实例访问某个已知的风险IP(
XX.XX.XX.XX)。

为新建实例配置安全组
前往购买实例:前往ECS控制台-自定义购买页面,选择实例配置。
新建安全组:在网络和安全组内新建普通安全组或企业级安全组,并编辑安全组名称。
快捷配置常用规则:购买实例时,控制台提供了常用的端口/协议,勾选后可以允许所有 IP 地址(
0.0.0.0/0)来源访问目标端口,或允许遵循目标协议的流量访问创建的实例。
购买实例时新建安全组不支持精细配置新建安全组的规则,可以在实例创建后配置。若在快速配置勾选了管理实例使用的端口(如远程连接实例常用的SSH(22)、RDP(3389)等),建议创建实例后将安全组规则设置为仅允许从安全的IP地址进行访问。
创建后修改/添加/删除安全组规则:购买实例后,可参考安全组规则的配置信息,为新建的实例添加/修改/删除安全组规则。
可以查看安全组应用指导和案例,了解如限制实例访问、数据库安全策略等更多业务情况下的安全组规则配置案例方法。
管理安全组
随ECS实例新建的安全组可以在创建后进行安全组规则修改。安全组也可以独立于实例创建管理,并将其关联至已有的ECS实例。
创建安全组
控制台
前往ECS控制台-安全组页面,单击创建安全组。
设置安全组名称及专有网络 VPC。
选择安全组类型为普通安全组或企业级安全组。
为安全组配置安全组规则后,单击确定创建。
API
调用CreateSecurityGroup,创建安全组。
创建的普通安全组若未配置规则时,入方向默认会允许同安全组内其他ECS的流量,拒绝其他所有入方向流量,出方向允许所有流量。
添加/修改/删除安全组规则
安全组规则定义了允许或禁止出入安全组的网络流量应匹配的条件。配置规则时,须指定流量方向、访问目的及优先级等。 安全组规则为有状态的规则,只需配置入方向规则,安全组会自动放行对应的出方向响应流量。
控制台
前往ECS控制台-安全组页面,单击目标安全组ID进入安全组详情页。
配置安全组规则。
添加规则:在目标安全组详情页面,选择规则需要控制方向,单击增加规则。
修改规则:在目标安全组详情页访问规则区域,找到目标规则,单击操作列中的编辑。
删除规则:在目标安全组详情页访问规则区域,找到目标规则,单击操作列中的删除。
API
调用AuthorizeSecurityGroup,添加入方向规则。
调用AuthorizeSecurityGroupEgress,添加出方向规则。
调用ModifySecurityGroupRule,修改入方向规则。
调用ModifySecurityGroupEgressRule,修改出方向规则。
调用RevokeSecurityGroup,删除入方向规则。
调用RevokeSecurityGroupEgress,删除出方向规则。
同优先级下,拒绝规则优先生效。对于部分特定网络流量,安全组会默认放行。
为减少业务生产安全问题,建议按照最小范围(白名单)开放原则配置安全组规则,尽量避免涉及登录、管理ECS实例等高危场景下允许全量访问(慎用0.0.0.0/0或::/0)。
避免直接修改生产环境的安全组。可以先克隆安全组,在测试环境调试,确保修改后实例流量正常,再对线上环境的安全组规则进行修改。
为实例关联安全组
当您为ECS实例关联安全组时,实际上是在为ECS实例的主网卡关联安全组。
控制台
前往ECS控制台-实例单击目标实例ID进入实例详情页。
在实例详情页切换至安全组页签,在安全组列表页单击更换安全组,按需将安全组加入实例或者移除实例。关联多个安全组时,安全组规则会合并,且按照优先级排序生效。
API
调用ModifyInstanceAttribute,为一台ECS实例设置多个安全组。
调用JoinSecurityGroup,将一台ECS实例加入到指定的安全组。
调用LeaveSecurityGroup,将一台ECS实例移出指定的安全组。
为辅助弹性网卡关联安全组
安全组实际作用在ECS实例的弹性网卡上。实例有多张弹性网卡时,为弹性网卡关联不同的安全组,并配置差异化的安全组规则,可以实现实例内部网络流量的分级管控与业务隔离。
控制台
前往ECS控制台-弹性网卡页面,单击目标辅助网卡的ID,进入辅助弹性网卡详情页。
单击更换安全组,勾选要关联的安全组,单击确定。
API
调用JoinSecurityGroup将弹性网卡加入到指定的安全组。
调用LeaveSecurityGroup将弹性网卡移出指定的安全组。
使用ModifyNetworkInterfaceAttribute为弹性网卡指定多个安全组。
使用前缀列表
当需对多个IP地址段进行统一授权时,可使用前缀列表集中管理,从而简化安全组规则配置,提升批量维护效率。
控制台
创建前缀列表:
前往ECS控制台-前缀列表。
根据需求选择到目标页签,单击创建前缀列表。
引用前缀列表的安全组,规则数量会根据列表设置的最大条目数计算。
在目标安全组详情页访问规则区域增加或修改规则:
设置访问来源为前缀列表,选择目标前缀列表。
API
调用CreatePrefixList,创建一个前缀列表。创建完成后,可以通过DescribePrefixListAttributes查询前缀列表的详细信息。
调用AuthorizeSecurityGroup在安全组入方向规则中,设置SourcePrefixListId授权已经创建的前缀列表。
调用AuthorizeSecurityGroupEgress在安全组出方向规则中,设置DestPrefixListId授权已经创建的前缀列表。
克隆安全组
当需要批量创建带有相同配置的安全组,或进行跨地域、跨网络类型复制和备份时,可通过克隆安全组功能快速实现。克隆成功后,可在目标地域的安全组列表中看到新安全组。
前往ECS控制台-安全组,在目标安全组的操作栏单击克隆安全组。
设置目标安全组,克隆后,新的安全组显示在目标地域的安全组列表中。
专有网络ID:新安全组的网络类型,选择经典网络或者具体的专有网络。
保留规则:勾选将保留原安全组中所有规则,优先级大于100的规则将调整为100。
复制本安全组标签到克隆安全组:选择是否需要将原安全组的标签复制到新安全组。
检查是否存在冗余规则
安全组健康检查功能可以识别冗余规则。当规则A的条件被规则B完全包含,且规则A的优先级不高于规则B时,规则A即为冗余规则。冗余规则会占用安全组规则配额,建议定期清理,以避免因规则数量达到上限而无法添加新规则。
前往ECS控制台-安全组在目标安全组详情页面的访问规则页签中,单击健康检查。
在健康检查对话框中,选中待删除的冗余规则,单击删除上述规则。
导入/导出规则
如果需要备份、恢复和迁移规则,可以使用导入导出功能。
导入规则
导入的安全组规则需遵循以下要求:
文件格式:JSON或CSV。
规则数量:单次导入不超过200条。
规则优先级:1到100之间。优先级高于100的规则将被忽略。
在跨地域导入规则时,不支持安全组规则中授权对象为安全组和前缀列表,不支持安全组规则中端口范围为端口列表。
前往ECS控制台-安全组在目标安全组详情页面访问规则区域,单击导入安全组规则。
在导入安全组规则页面,单击选择文件并选中本地的JSON或CSV文件,单击确认。
导入失败时,将鼠标悬停在警告图标上可查看原因。
导出规则
前往ECS控制台-安全组,在目标安全组详情页访问规则区域,单击导出。导出的规则文件的命名格式:
JSON格式:ecs_${region_id}_${groupID}.json。
示例:如果Region ID为
cn-qingdao,安全组ID为sg-123,则导出的文件名为ecs_cn-qingdao_sg-123.json。CSV格式:ecs_sgRule_${groupID}_${region_id}_${time}.csv。
示例:如果Region ID为
cn-qingdao,安全组ID为sg-123,导出日期为2020-01-20,则导出的文件名为ecs_sgRule_sg-123_cn-qingdao_2020-01-20.csv。
安全组快照
安全组快照可自动备份安全组规则。当安全组规则发生变更时,系统会自动创建快照。通过快照可恢复指定时间点的安全组规则,防止因误操作导致规则丢失。
安全组规则变更后,系统将在5分钟后创建快照。若5分钟内发生多次变更,系统仅会基于首次变更前的规则创建一次快照。
安全组快照使用对象存储服务(OSS)存储备份数据。OSS为按量计费服务,使用安全组快照会产生相应的OSS存储和请求费用。
创建快照策略
前往ECS控制台-安全组快照,单击新建安全组快照策略。
在新建快照策略对话框中,配置以下信息:
策略名称:输入快照策略的名称。
策略状态:选择启用或禁用。仅当策略为启用状态时,才会为关联的安全组创建快照。
快照保留时间:设置快照保留天数,范围为1-30天,默认值为1天。超过保留时间的快照将被自动删除。
OSS 存储配置:配置用于存储快照数据的OSS Bucket。若Bucket名称留空,系统将使用默认Bucket。
单击确定。
首次创建快照策略时,系统会提示授权服务关联角色(SLR)
ALIYUNSECURITYGROUPSNAPSHOTROLE以访问OSS存储桶。若该角色已存在,则无需重复授权。
关联安全组到快照策略
创建快照策略后,需将其与安全组关联,才能开始备份安全组规则。
关联安全组到快照策略时,系统会立即为该安全组创建一次快照。
前往ECS控制台-安全组快照,找到目标快照策略,在操作列单击关联安全组。
在关联安全组对话框中,选择要关联的安全组。
一个快照策略最多可关联10个安全组,一个安全组可关联多个策略不同的快照策略。
单击确定完成关联。
从快照恢复规则
恢复操作会立即生效,当前所有规则将被快照中的规则完全覆盖。恢复后无法撤销。
前往ECS控制台-安全组页面,单击目标安全组ID进入安全组详情页。
在安全组详情页,切换至快照列表页签,找到目标快照,在操作列单击恢复快照。
在恢复安全组快照对话框中,确认恢复信息。
在入方向和出方向页签下,对比当前安全组规则和恢复后安全组规则。
确认无误后,单击确定。
删除安全组
删除安全组是一个不可逆的操作,将永久删除安全组下所有规则。在执行删除操作前,请确保备份相关配置。
控制台
前往ECS控制台-安全组,在目标安全组的操作栏单击删除。
在删除安全组对话框中,确认信息后,单击确定。
如果安全组没有关联的ECS实例和弹性网卡,在删除安全组对话框中仍提示不可删除时,可以单击尝试强制删除。
API
调用DeleteSecurityGroup,删除安全组。
安全组在以下场景时无法删除:
已关联ECS实例或弹性网卡时无法删除,需先将其移除。
被其他安全组规则授权,需先删除授权规则。
托管安全组仅支持查看,不可删除。
开启了删除保护,请先关闭删除保护,然后再尝试操作。如果无法关闭删除保护则无法删除安全组。
在使用DeleteSecurityGroup接口删除安全组时返回错误码
InvalidOperation.DeletionProtection,或使用控制台删除安全组看到类似删除保护的提示时,说明该安全组开启了删除保护功能。
安全组内实例网络互通
默认情况下,同一普通安全组内的ECS实例间内网互通。为提高安全性,可以将组内连通策略调整为组内隔离,禁止实例间的内网互通。
企业级安全组不支持修改组内连通策略。
当实例关联多个安全组时,只要其中任一安全组的组内连通策略设置为组内互通,实例间即可内网互通。
安全组的组内连通策略设置为组内隔离时,可通过配置安全组规则,允许实例间通信。
控制台
前往ECS控制台-安全组,单击目标安全组ID进入安全组详情页。
在安全组详情页面,页签基本信息区域,单击修改组内网络连通策略。
安全组的组内连通策略已更改为组内隔离。
API
调用ModifySecurityGroupPolicy,修改普通安全组的组内连通策略。
安全组间实例网络互通
将其他安全组设为规则的授权对象时,可允许其他安全组内实例,通过内网访问本安全组内的实例。图中为安全组A设置了入方向的授权对象安全组B后,安全组B内的实例可以通过内网访问安全组A内的实例。
企业级安全组规则不支持添加授权对象为安全组的规则。
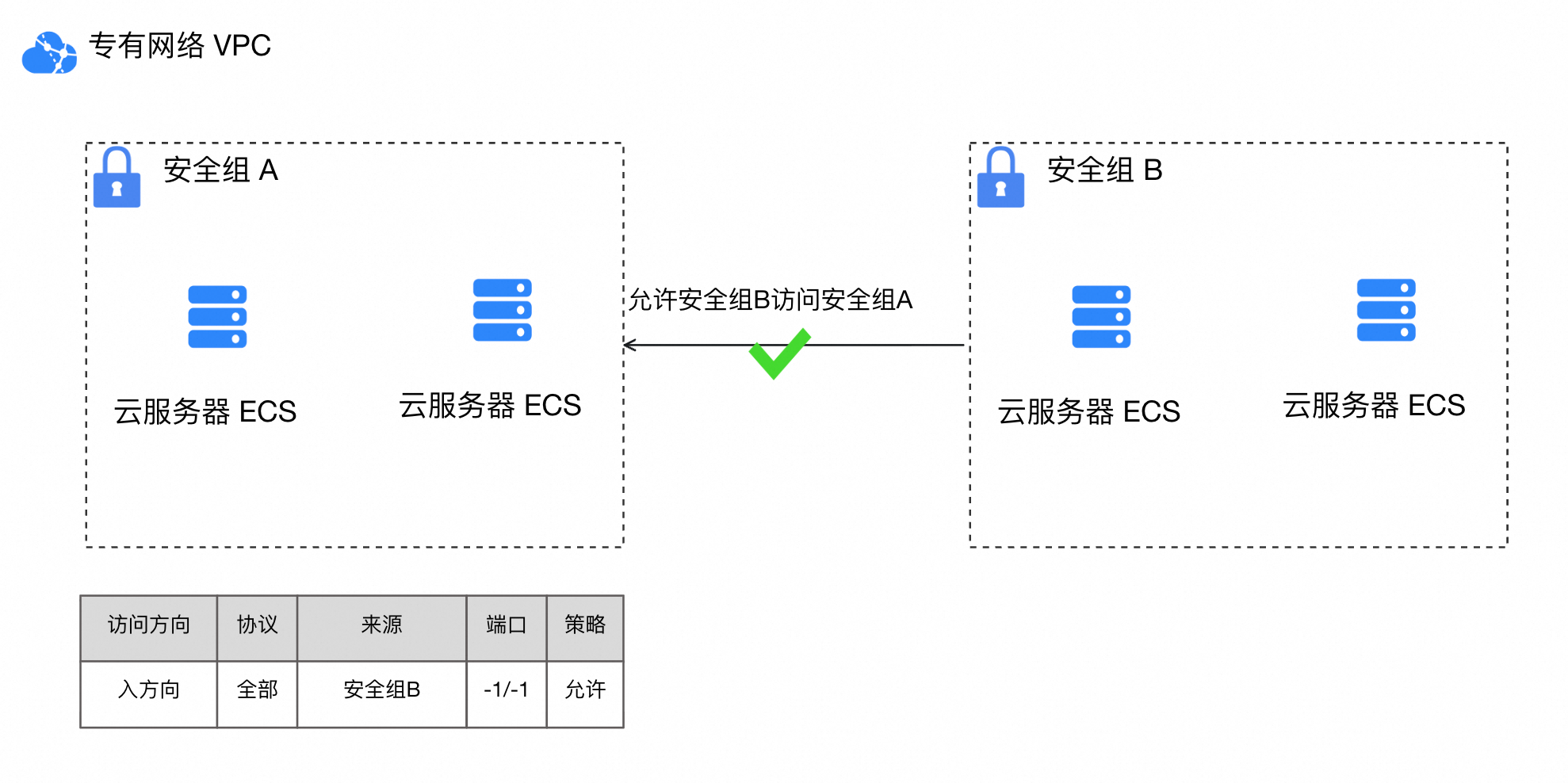
控制台
前往ECS控制台-安全组,单击目标安全组ID进入安全组详情页。
在目标安全组详情页面,选择规则需要控制方向,单击增加规则。
在新建安全组规则页面选择访问来源为安全组或跨账号安全组。
API
调用AuthorizeSecurityGroup在安全组入方向规则中设置SourceGroupId授权已创建的安全组。
调用AuthorizeSecurityGroupEgress在安全组出方向规则中设置DestGroupId授权已创建的安全组。
生产应用建议
安全组规划
职责单一:Web、数据库、缓存等各业务场景下安全组应各自独立。
环境隔离:生产、测试环境的安全组须分离,避免混用。
命名规范:采用
环境-应用-用途-sg格式,如prod-mysql-db-sg。
规则配置
最小权限:仅对必要的源开放必要的端口。避免对SSH(22)、RDP(3389)等管理端口开放
0.0.0.0/0应始终限定为可信的固定IP。默认拒绝:默认拒绝所有入方向流量。仅在必要时,添加入方向规则,放行特定端口和来源的访问。
规则优先级冲突:当实例关联多个安全组时,低优先级的允许规则会被高优先级的拒绝规则覆盖。排查网络不通时,需检查所有关联的安全组。
变更管理
避免直接修改生产环境: 直接修改生产环境的安全组是高危操作。可以先克隆安全组,在测试环境调试,确保修改后实例流量正常,再对线上环境的安全组规则进行修改。
计费规则
安全组免费使用。
使用限制
限制项 | 普通安全组限制 | 企业级安全组限制 |
单个阿里云账号在特定地域下的安全组总数量上限 | 请根据配额ID | 与普通安全组相同 |
单张弹性网卡可以关联的安全组数量 | 10 | 与普通安全组相同 |
单张弹性网卡关联的所有安全组的规则(包括入方向规则与出方向规则)数量之和的上限 | 1,000 | 与普通安全组相同 |
单个安全组中,授权对象为安全组的规则数量 | 20 | 0条,在企业级安全组中,您不能添加授权对象为安全组的规则,也不能将企业级安全组作为其他安全组规则中的授权对象。 |
单个专有网络VPC类型的安全组能容纳的VPC类型ECS实例数量 | 不固定,受安全组能容纳的私网IP地址数量影响。 | 无限制 |
单个阿里云账号在特定地域下单个专有网络VPC类型的安全组能容纳的私网IP地址数量 | 6,000 说明
| 65,536 说明 IP占用数按照安全组关联的弹性网卡(包括实例主网卡、辅助网卡)的数量计数,即关联的所有弹性网卡的数量总和。 |
公网访问端口 | 基于安全考虑,ECS实例25端口默认受限,建议您使用SSL加密端口(通常是465端口)来对外发送邮件。 | 与普通安全组相同 |