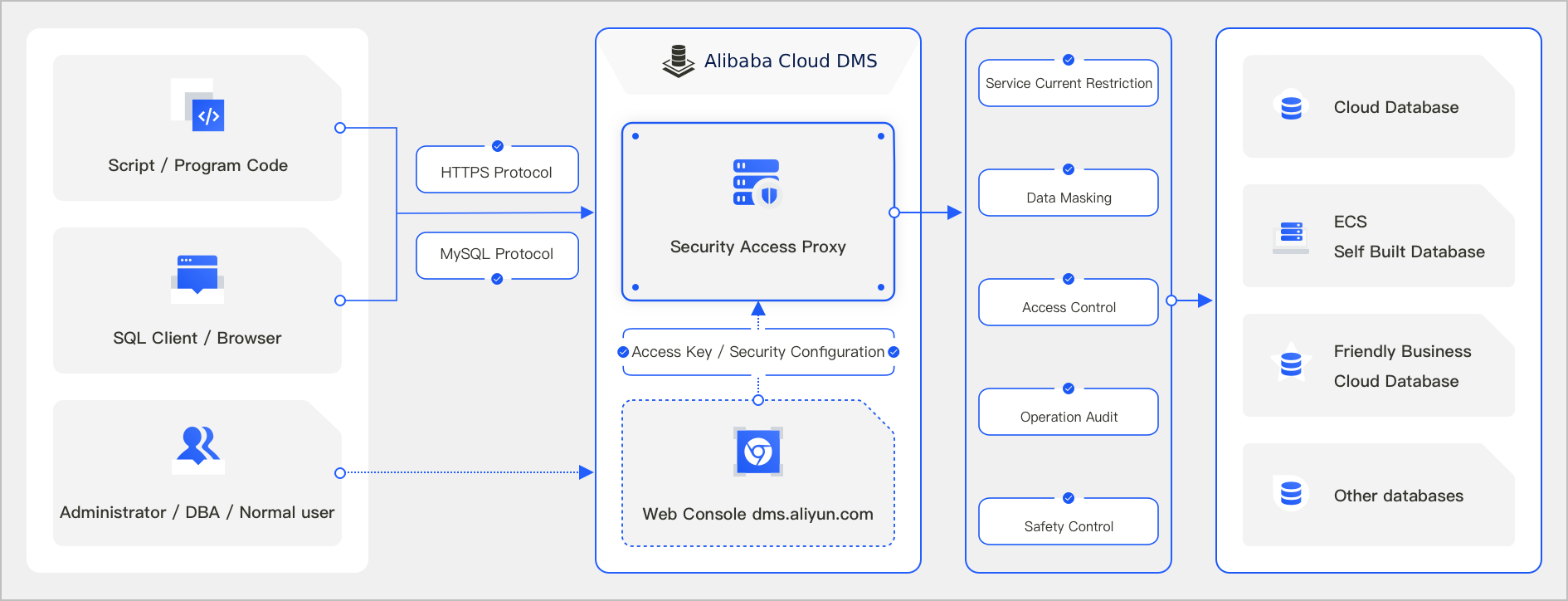
The secure access proxy feature of Data Management (DMS) provides comprehensive security for database access. After you enable this feature for an instance, you can securely access the target instance. You can use standard MySQL or HTTPS protocols to connect to the address that is generated by the proxy from the command line, a database management tool, or your application code.
Prerequisites
DMS is deployed in the Singapore or Indonesia (Jakarta) region. For more information, see Switch DMS deployment regions.
The database instance and DMS are in the same region.
NoteOn the homepage, in the instance list on the left, you can hover over the target instance to view its region.
The following database types are supported:
MySQL: RDS MySQL, PolarDB for MySQL, MyBase MySQL, PolarDB Distributed Edition, AnalyticDB for MySQL, and self-managed MySQL databases.
MariaDB: RDS MariaDB and self-managed MariaDB databases.
Your system role is Administrator or DBA. For more information, see View my system role.
Function Introduction
The secure access proxy reuses existing security rules, data permissions, and sensitive column configurations in DMS. This feature provides enterprises with comprehensive database security management capabilities, such as security control, access control, data masking, and operation auditing.
Procedure
- Log on to the DMS console V5.0.
On the homepage, right-click the target instance in the instance list on the left and select Secure Access Proxy.
NoteIf you use the console in simple mode, click Database Instances in the navigation pane on the left. In the instance list, right-click the target instance, and then click Secure Access Proxy.
On the secure access proxy details page, click the Enable Secure Access Proxy button.
In the Enable Secure Access Proxy dialog box, enter the Database Account and Database Password, and click Next.
In the Secure Access Proxy - Authorization dialog box, configure settings such as Authorized Personnel, Use Independent Database Account, and Configure Security Policy. Authorized users can then use the authentication information generated by the secure access proxy to call the database instance. For more information, see Grant secure access proxy permissions.
Click Confirm.
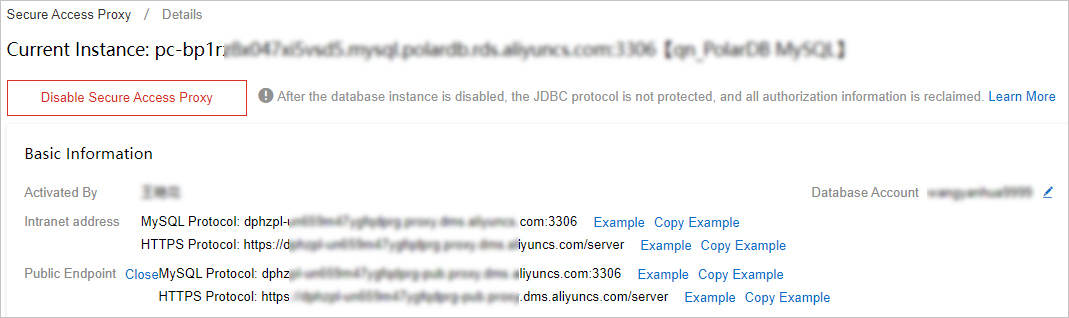
The following figure shows the page after you enable the secure access proxy.
References
After you enable the secure access proxy for an instance, you might need to perform the following operations:
Access the instance. For more information, see Access an instance over the MySQL protocol and Access an instance over the HTTPS protocol.
To disable the secure access proxy, click Disable Secure Access Proxy in the upper-left corner of the secure access proxy details page.
Enable an Internet address: To call the target instance from a local application or an application in a different VPC, click Enable to the right of Internet Address.
Change the database account: Click the edit icon next to Database Account to modify the account that is used to connect to the database instance.
You can also call API operations to enable or disable the secure access proxy for an instance.