After you add a website to Web Application Firewall (WAF), you can configure a custom protection policy to protect the website. You can configure access control rules and throttling rules based on exact match conditions for different scenarios, such as hotlink protection and website backend protection. This topic describes how to configure a custom protection policy.
Background information
The custom protection policy feature is implemented by using custom protection rules. Custom protection rules include access control list (ACL) rules and HTTP flood protection rules.
An ACL rule filters requests based on precise match conditions such as client IP addresses, request URLs, and common request headers.
An HTTP flood protection rule filters requests based on the precise match conditions and rate limiting you have configured.
Limits
The number and specifications of custom rules that can be configured vary based on the editions of subscription WAF instances.
Specification | Description | Pro edition | Business edition | Enterprise edition and higher |
Number of custom protection rules | The maximum number of custom protection rules that you can create. | 200 per domain name | 200 per domain name | 200 per domain name |
Advanced match fields | The advanced match fields other than IP addresses and URLs that you can specify in custom protection rules. | Not supported | Supported | Supported |
Rate limiting | The rate limiting settings in a custom protection policy. The settings define an HTTP flood protection rule. | Not supported | Supported | Supported |
Custom statistical objects | The custom statistical objects other than IP addresses and sessions that can be used to configure rate limiting. | Not supported | Supported | Supported |
Prerequisites
A WAF instance is purchased.
Your website is added to WAF. For more information, see Tutorial.
Procedure
Log on to the WAF console.
In the top navigation bar, select the resource group and the region in which the WAF instance is deployed. You can select Chinese Mainland or Outside Chinese Mainland.
In the left-side navigation pane, choose .
In the upper part of the Website Protection page, select the domain name for which you want to configure protection from the Switch Domain Name drop-down list.
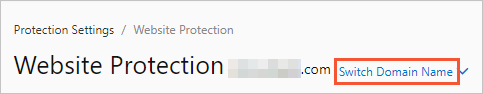
Click the Access Control/Throttling tab and find the Custom Protection Policy section. Then, turn on Status and click Settings.
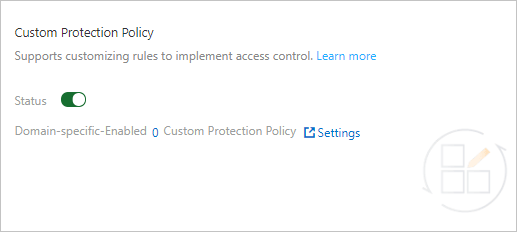 Note
NoteWhen the custom protection policy feature is enabled, all requests destined for your website are checked by the feature. You can configure a whitelist rule for Access Control/Throttling to allow requests that match the whitelist rule to bypass the check. For more information, see Configure a whitelist for Access Control/Throttling.
Create a custom rule.
On the Custom Protection Policy page, click Create Custom Protection Policy.
In the Add Rule dialog box, configure the parameters. The following table describes the parameters.
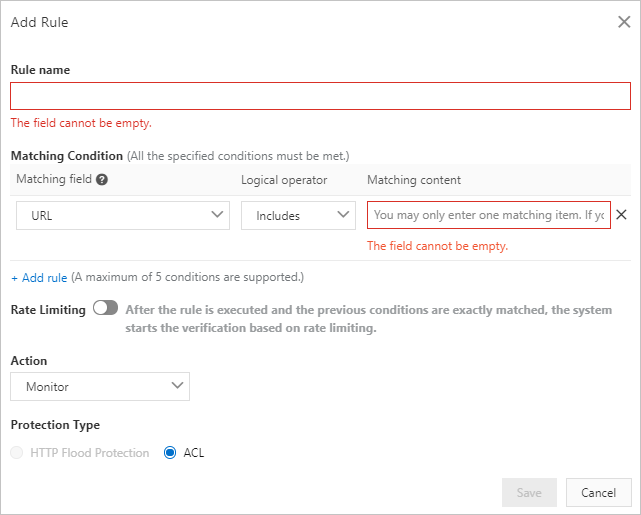
Parameter
Description
Rule name
The name of the rule.
Matching Condition
The match conditions of the rule. The rule is triggered only when match conditions are met. Click Add rule to add more conditions. You can add up to five conditions. If you specify multiple match conditions, the rule is triggered only when all match conditions are met.
For more information about match conditions, see Fields in match conditions.
Rate Limiting
The status of rate limiting. WAF starts calculating the request rate only when match conditions are met. If you enable rate limiting, you must configure rate limiting parameters.
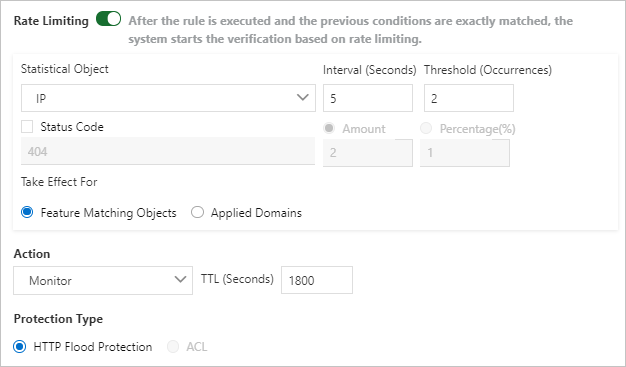
For more information about rate limiting parameters, see Rate limiting parameters.
Action
The action that you want WAF to perform on requests that trigger the rule. Valid values:
Monitor: triggers alerts but does not block requests.
Block: blocks requests.
CAPTCHA: redirects requests to another page to implement CAPTCHA verification.
Strict Captcha: redirects requests to another page to implement strict slider CAPTCHA verification.
JavaScript Validation: triggers JavaScript validation.
If you enable Rate Limiting, you must configure the TTL (Seconds) parameter to specify the validity period of the action.
NoteLatency may occur during the statistical process because WAF collects data from multiple servers in a cluster to calculate the request rate.
JavaScript validation and slider CAPTCHA verification are applicable only to static pages. If you want JavaScript validation and common slider CAPTCHA to be supported for asynchronous requests, such as requests that are initiated by using XMLHttpRequest and Fetch, you can enable JavaScript validation and common slider CAPTCHA when you configure the bot management module. For more information, see Configure anti-crawler rules for websites.
Protection Type
The type of the rule. This parameter is automatically specified based on the status of Rate Limiting.
If rate limiting is enabled, the value is set to HTTP Flood Protection.
If rate limiting is disabled, the value is set to ACL.
The following table describes the rate limiting parameters.
Parameter
Description
Statistical Object
The object based on which the request rate is calculated. Valid values:
IP: calculates the number of requests that are sent from a specific IP address.
Session: calculates the number of requests that are sent from a specific session.
Custom-Header: calculates the number of requests that contain the same header content.
Custom-Param: calculates the number of requests that contain the same parameter content.
Custom-Cookie: calculates the number of requests that contain the same cookie content.
Interval (Seconds)
The time period during which the number of requests is calculated.
Threshold (Occurrences)
The maximum number of requests that can be sent from the object during the specified time period. If this limit is exceeded, rate limiting is triggered.
Status Code
The HTTP status code. After the detection logic takes effect, the number or percentage of the specified status code within the specified time period is calculated. You can select whether to calculate the amount or percentage of the status code.
Amount: the maximum number of the specified HTTP status code.
Percentage (%): the maximum percentage of the specified HTTP status code.
Take Effect For
The objects for which you want rate limiting to take effect. Valid values:
Feature Matching Objects: Only requests that meet the match conditions of the protection rule are calculated.
Applied Domains: All requests that are destined for the domain name are calculated.
Click Save.
After a custom protection rule is created, the rule is automatically enabled. You can view, disable, modify, or delete the rule in the rule list based on your business requirements.
Related operations
After you configure a custom protection policy, you can use CloudMonitor and Log Service to configure monitoring and alerting for WAF. When traffic to your website matches the protection rules, alert notifications are sent. This way, you can monitor the security status of your website at the earliest opportunity. For more information, see Configure WAF alerting.