Web Application Firewall (WAF) provides an account security feature that helps you identify account risks. This topic describes how to protect interfaces in different scenarios. You can follow the instructions in this topic to better protect interfaces on which user authentication is performed.
Background information
Use verification services to protect common and HTML5 web pages
Verification services are the easiest and most effective approaches to protect interfaces. The integration of verification services into your business typically requires minor code changes. It may take one or two business days to modify the code.
Common verification methods can block direct calls launched from simple tools or scripts. However, due to the adaptation of attack methods and tools, the common verification methods can be easily bypassed. We recommend that you use professional verification services to better protect interfaces against attacks.
Use SDK signatures to protect native apps
Verification services may be unsuitable for native apps. Alibaba Cloud provides an SDK solution for native apps. The solution collects the information about the hardware and environment of a mobile device, calculates signatures, and verifies signatures of requests. This ensures that only requests from verified apps are directed to the origin server. Requests sent from scripts, automated programs, simulators, and other unverified sources are blocked.
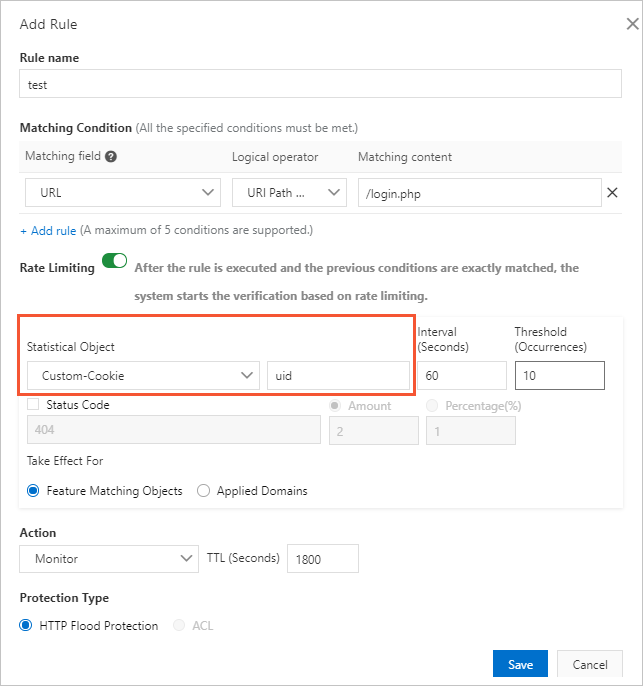
Configure frequency control to block attack sources
Frequency control helps you identify requests that contain a common field among a large number of requests. You can specify the maximum occurrences of the common field. The source of the requests is blocked when the maximum occurrences are exceeded. Traditional protection methods typically block malicious IP addresses. Malicious requests sent from proxies or rotating IP addresses may contain the same token, for example, the same UID, in their cookies. In this case, you can configure the maximum occurrences based on the cookies to block malicious accounts.
Analyze suspicious requests
Malicious requests have certain common characteristics. The following examples describe common characteristics among malicious requests.
- Incomplete HTTP headers. Malicious requests may exclude certain fields, such as Referer, Cookie, or Content-Type.
- Abnormal User-Agent values. User-Agent headers used in requests that target Java or Python-based websites are found in requests sent to common websites. User-Agent headers used in requests initiated from desktop browsers are found in requests sent to WeChat mini programs. In these cases, requests that contain abnormal User-Agent headers may be malicious.
- Missing cookies. Typically, multiple cookies are used in an application. Common cookies include SessionID, userid, deviceid, and lastvisit. However, crawlers may include only one or two cookies that are required for retrieving information and exclude other cookies that identify users.
- Abnormal parameters. Similar to missing cookies, some parameters are not required for crawlers to retrieve information. Crawlers may exclude or repeatedly submitted these parameters in requests.
- Suspicious fields. Suspicious fields may be contained in email addresses, phone numbers, and account information.
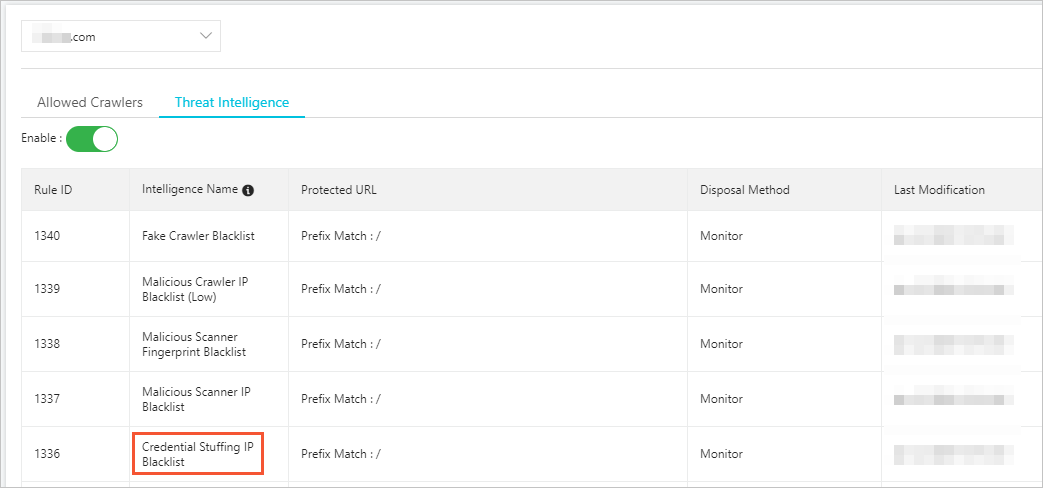
Enable credential stuffing and bot threat intelligence
WAF provides a Bot Management feature. This feature uses algorithms and identifies malicious IP addresses from credential stuffing attacks detected by Alibaba Cloud. A credential stuffing IP address blacklist is created and updated dynamically. You can use the Bot Threat Intelligence function from the Bot Management tab to set the credential stuffing IP address blacklist to the Monitor, Block, or Captcha mode. For more information, see Set a bot threat intelligence rule.