The first Istio version (V1.0) available for production was officially released on July 31, 2018.

Istio is an open platform used to connect, manage, and secure microservices. It provides a simple method for creating a microservice network, and delivers capabilities such as load balancing, service-to-service authentication, and monitoring. In addition, these functions can be implemented without any changes to services themselves.
Istio provides the following functions:
This article describes how to use Alibaba Cloud Container Service for Kubernetes to quickly build an Istio open platform for connecting, managing, and securing microservices, and to introduce and configure multiple relevant services for applications.
In terms of architecture, Istio is divided into two parts:
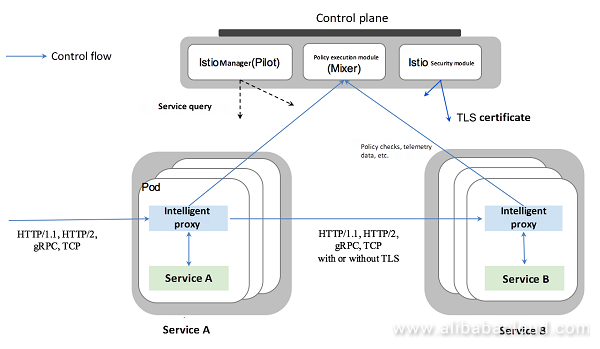
Envoy is deployed as an independent sidecar to the relevant microservice in the same Kubernetes pod, and provides a series of attributes for Mixer. Based on these attributes, Mixer enforces policies and sends these attributes to the monitoring system.
This type of sidecar proxy model does not need to change the logic of any service. In addition, it can add many functions.
Mixer enforces access control and usage policies across the service mesh, and collects the telemetry data from the Envoy proxy and other services.The proxy extracts request level attributes, and sends them to Mixer for evaluation.
Mixer includes a flexible plugin model. This model enables Istio to interface with a variety of host environments and infrastructure backends. Thus, Istio abstracts the Envoy proxy and Istio-managed services from these details.The relevant content will be described in subsequent articles.
Pilot collects and authenticates the configurations, and propagates them to various Istio components.It extracts environment-specific implementation details from Mixer and Envoy, and provides abstract representation of user services for them, which are independent of the underlying platform.In addition, Pilot can be used to program the traffic management rules at runtime, that is, the universal layer-4 and layer-7 HTTP/gRPC routing rules.
Citadel provides inter-service and inter-user authentication and enhances security between services without any changes in service code.Citadel consists of the following three components:
The following describes how to quickly build an Istio open platform for connecting, managing, and securing microservices on the basis of Alibaba Cloud Container Service for Kubernetes.
Alibaba Cloud Container Service for Kubernetes V1.10.4 has been released. You can use the container service console to conveniently and quickly create a Kubernetes cluster.For more information about the process, see create a Kubernetes cluster.
Click App Catalog on the left-side navigation bar, and select ack-istio on the right side, as shown below:
Click Parameters. You can modify parameter settings to customize Istio. The following table lists the common parameters.
| Parameter | Description | Default |
global.hub |
Specifies the HUB for most images used by Istio | registry.cn-hangzhou.aliyuncs.com/aliacs-app-catalog |
global.tag |
Specifies the TAG for most images used by Istio | 1.0.0 |
global.proxy.image |
Specifies the proxy image name | istio-proxyv2 |
global.imagePullPolicy |
Specifies the image pull policy | IfNotPresent |
global.controlPlaneSecurityEnabled |
Specifies whether control plane mTLS is enabled | false |
global.mtls.enabled |
Specifies whether mTLS is enabled by default between services | false |
global.mtls.mtlsExcludedServices |
List of FQDNs to exclude from mTLS | -"kubernetes.default.svc.cluster.local" |
global.rbacEnabled |
Specifies whether to create Istio RBAC rules or not | true |
global.refreshInterval |
Specifies the mesh discovery refresh interval | 10s |
global.arch.amd64 |
Specifies the scheduling policy for amd64 architectures | 2 |
global.arch.s390x |
Specifies the scheduling policy for s390x architectures | 2 |
global.arch.ppc64le |
Specifies the scheduling policy for ppc64le architectures | 2 |
galley.enabled |
Specifies whether Galley should be installed for server-side config validation.Requires k8s >= 1.9 | false |
In addition to the preceding common parameters, you can customize different modules. For example, you can determine whether to enable Grafana, Prometheus, tracing, Weave Scope, and Kiali.
#
# addons configuration
#
grafana:
enabled: true
replicaCount: 1
image: istio-grafana
service:
name: http
type: ClusterIP
externalPort: 3000
internalPort: 3000
....
prometheus:
enabled: true
replicaCount: 1
image:
repository: registry.cn-hangzhou.aliyuncs.com/aliacs-app-catalog/istio-prometheus
tag: latest
....
tracing:
enabled: true
jaeger:
enabled: true
....
weave-scope:
enabled: true
global:
# global.image: the image that will be used for this release
image:
repository: weaveworks/scope
tag: "1.9.0"
# global.image.pullPolicy: must be Always, IfNotPresent, or Never
pullPolicy: "IfNotPresent"
....
kiali:
enabled: true
replicaCount: 1
image:
repository: registry.cn-hangzhou.aliyuncs.com/aliacs-app-catalog/istio-kiali
tag: devAfter modification, select the corresponding cluster and namespace on the right, specify the release name, and click Deploy. It is recommended that you create a namespace, such as istio-system.
Several minutes later, an Istio instance, which is an open platform for connecting, managing, and securing microservices, is created.
Click Container Group on the left-side navigation bar. The container group information related to the created Istio instance is displayed on the right side, as shown below:
Click Services on the left-side navigation bar. The access addresses of services related to the created Istio instance are displayed on the right side, as shown below:
By default, the following function modules are enabled:
The next article uses an official example to explain how to use Istio to develop, manage, protect, and monitor microservices on the basis of Alibaba Cloud Container Service for Kubernetes.
We can use Alibaba Cloud Container Service for Kubernetes to quickly build an Istio open platform for connecting, managing, and securing microservices, and to introduce and configure multiple relevant services for applications.You are welcome to use Alibaba Cloud Container Service for Kubernetes to quickly build an Istio open platform and integrate Istio to microservice development in your project.
This article series introduces Istio and its core components, as well as describes how to quickly build an Istio open platform for connecting, managing, and securing microservices on the basis of Alibaba Cloud Container Service for Kubernetes. These articles also use an official example to demonstrate how to deploy an application in the Istio environment; how to configure intelligent routing and distributed tracing; and how to configure Istio functions of collecting, querying, and visualizing the telemetry data.
To review these articles, see:
Using Istio to support Service Mesh on Multiple Alibaba Cloud Kubernetes Clusters
Go through Istio features with samples on Alibaba Cloud Container Service for Kubernetes

56 posts | 8 followers
FollowXi Ning Wang - August 23, 2018
Xi Ning Wang - August 30, 2018
Xi Ning Wang - August 21, 2018
Xi Ning Wang - August 17, 2018
Xi Ning Wang - August 23, 2018
Xi Ning Wang - August 30, 2018

56 posts | 8 followers
Follow Container Service for Kubernetes
Container Service for Kubernetes
Alibaba Cloud Container Service for Kubernetes is a fully managed cloud container management service that supports native Kubernetes and integrates with other Alibaba Cloud products.
Learn More ACK One
ACK One
Provides a control plane to allow users to manage Kubernetes clusters that run based on different infrastructure resources
Learn More Cloud-Native Applications Management Solution
Cloud-Native Applications Management Solution
Accelerate and secure the development, deployment, and management of containerized applications cost-effectively.
Learn More Container Registry
Container Registry
A secure image hosting platform providing containerized image lifecycle management
Learn MoreMore Posts by Xi Ning Wang(王夕宁)
Raja_KT February 15, 2019 at 3:59 am
Nice one. I have not experimented it but if we can manage microservices in a well-balanced mode, then it will be promising.