By Wei Li, Apache RocketMQ Committer, RocketMQ Python Client Project Owner, Apache Doris Contributor, and TencentDB Development Engineer
Namesrv: 5.1.0
Broker: 5.1.0
Dashboard: 1.0.1-SNAPSHOT
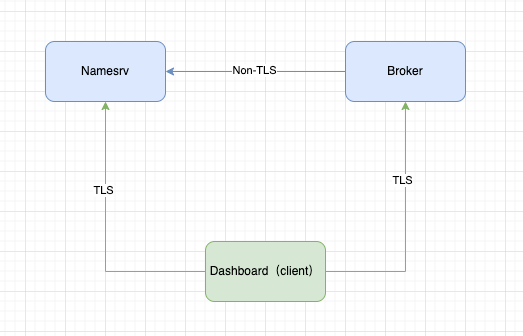
All the following operations are performed in the directory /etc/rocketmq, and Namesrv, Broker, and Dashboard are on the same machine. The Dashboard or the Client can also be on other machines.
Enter and confirm the password for the CA certificate. The characters you enter will not be visible.
openssl req -newkey rsa:2048 -keyout ca_rsa_private.pem -x509 -days 365 -out ca.pem• Enter additional information. If you do not want to provide any, simply enter a period (.)
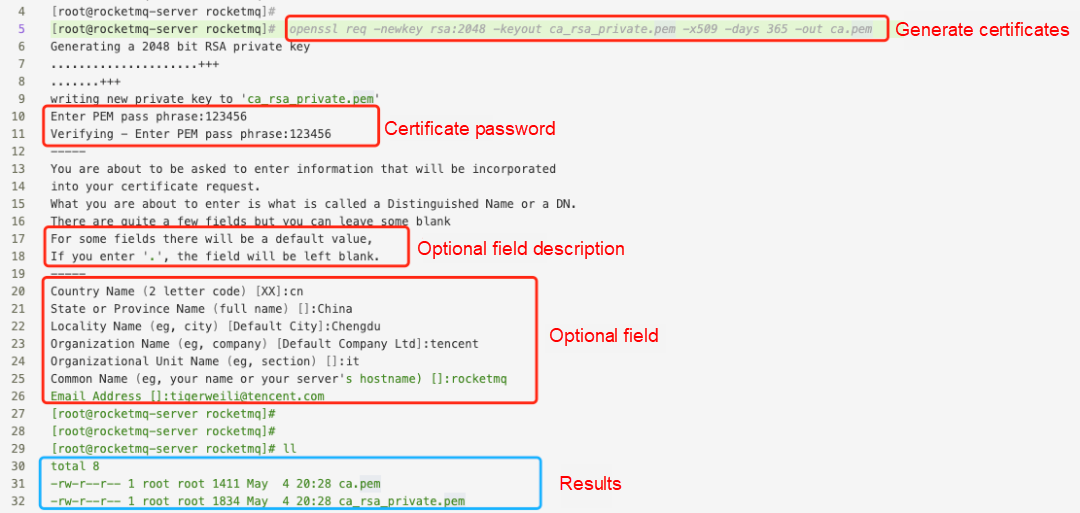
Generate CA certificates
openssl req -newkey rsa:2048 -keyout server_rsa.key -out server.csr
Generating a 2048 bit RSA private key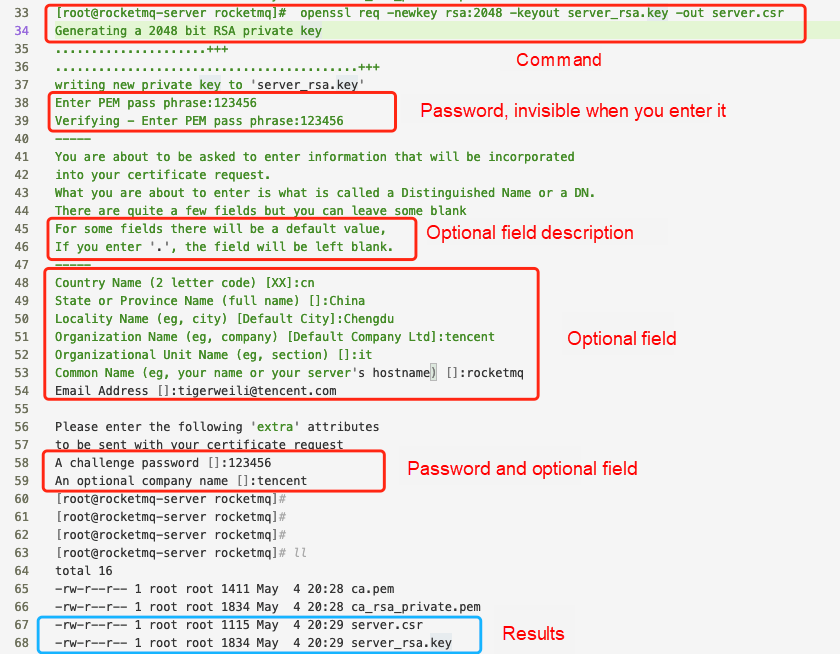
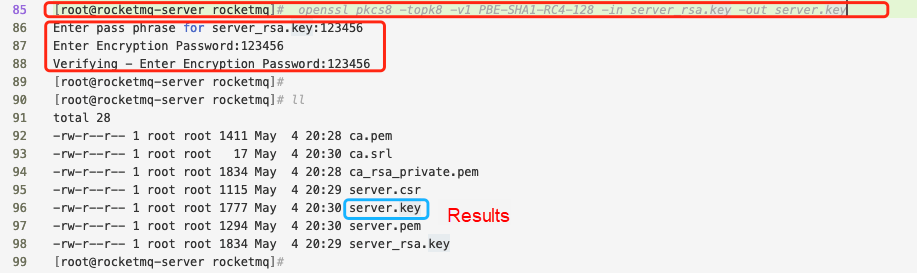
Generate encryption key pairs
openssl req -newkey rsa:2048 -keyout server_rsa.key -out server.csrGenerating a 2048 bit RSA private key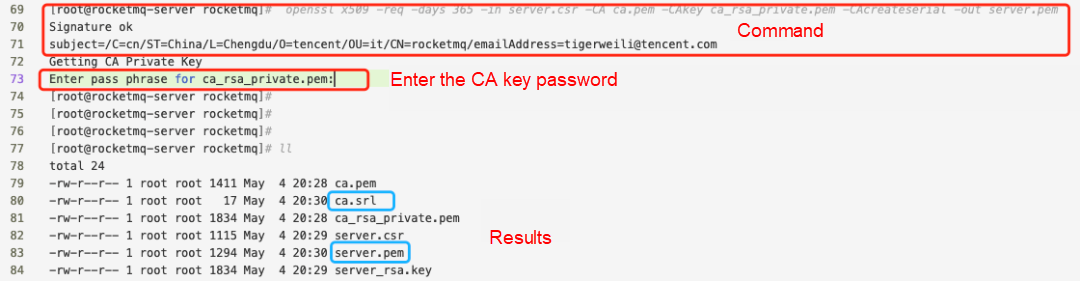
Generate keys and issue certificates for the namesrv and the broker
• tls-broker.properties
tls.test.mode.enable=false
tls.server.need.client.auth=none
tls.server.keyPath=/etc/rocketmq/server.key
tls.server.keyPassword=123456
tls.server.certPath=/etc/rocketmq/server.pem
tls.client.authServer=false
tls.client.trustCertPath=/etc/rocketmq/ca.pem• tls-namesrv.properties
tls.test.mode.enable=false
tls.server.need.client.auth=none
tls.server.keyPath=/etc/rocketmq/server.key
tls.server.keyPassword=123456
tls.server.certPath=/etc/rocketmq/server.pem• tls-client.properties
tls.client.trustCertPath=/etc/rocketmq/ca.pemThen, you have all the tls configuration files:
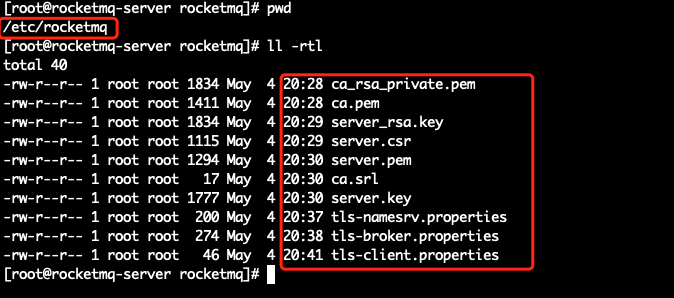
All configuration files
vim bin/runserver.sh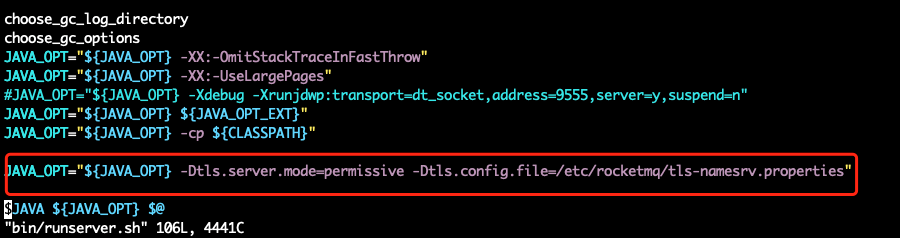
Modify the namesrv startup script
• Modify the broker startup script and configure the jvm to support tls
vim bin/runbroker.sh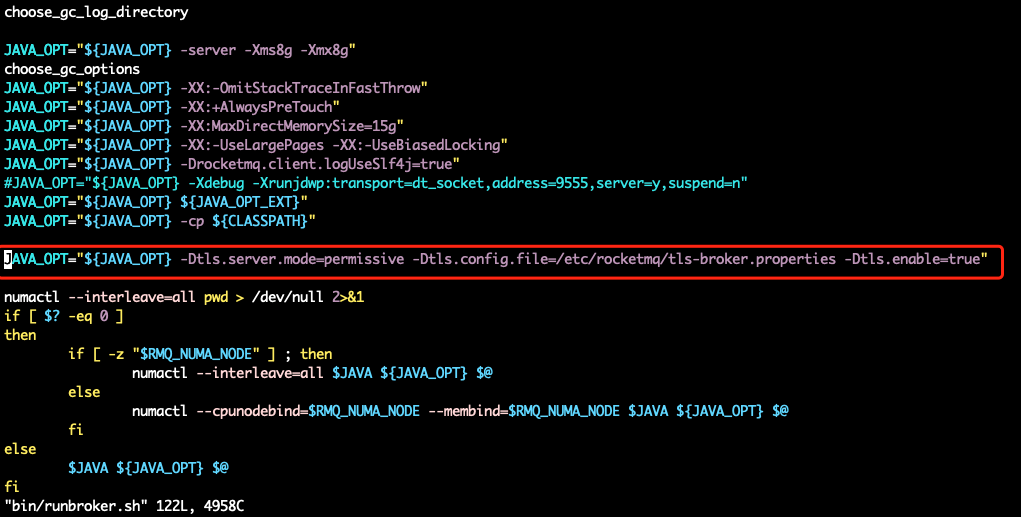
Modify the broker startup script
• Add broker.conf
brokerClusterName = DefaultCluster
brokerName = broker-a
brokerId = 0
deleteWhen = 04
fileReservedTime = 48
brokerRole = ASYNC_MASTER
flushDiskType = ASYNC_FLUSH
namesrvAddr = 127.0.0.1:9876• Modify the namesrv address
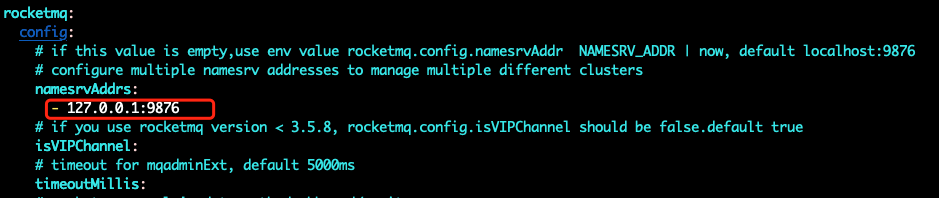
Modify the namesrv address
• Enable tls
vim rocketmq-dashboard-1.0.1-SNAPSHOT.jar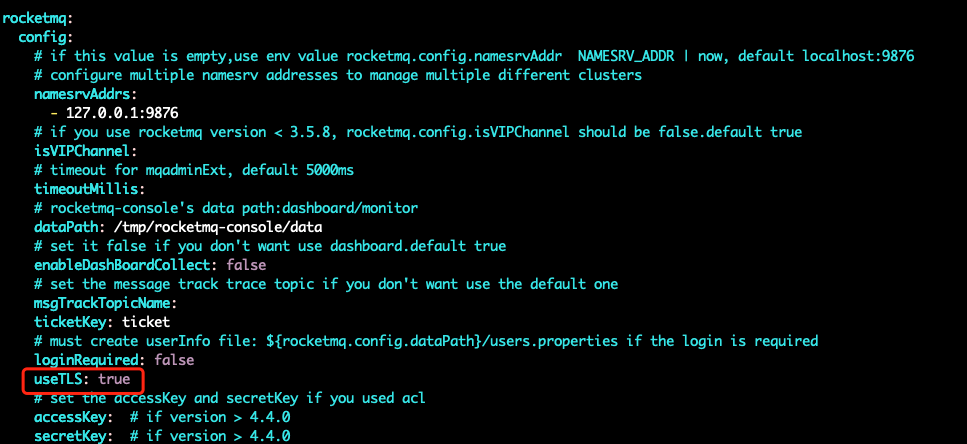
Modify the dashboard configuration
Note: For producer and consumer clients, configure the following parameters:
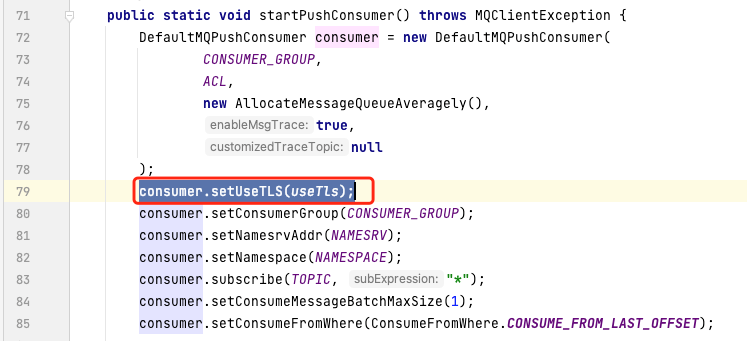
Enable tls on the consumer client
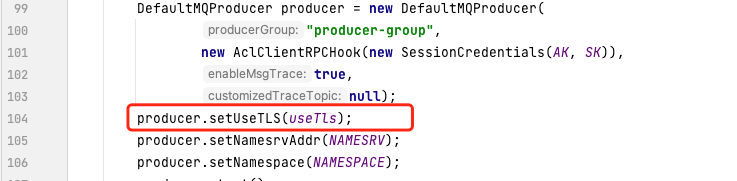
Enable tls on the producer client
• Start the namesrv
nohup sh bin/mqnamesrv &• Start the broker
nohup sh bin/mqbroker -c conf/broker.conf &• Start the dashboard
java -Dtls.client.authServer=true -Dtls.enable=true -Dtls.test.mode.enable=false -Dtls.config.file=/etc/rocketmq/tls-client.properties -jar rocketmq-dashboard-1.0.1-SNAPSHOT.jar• Check and analyze the captured packet by using the tcpdump
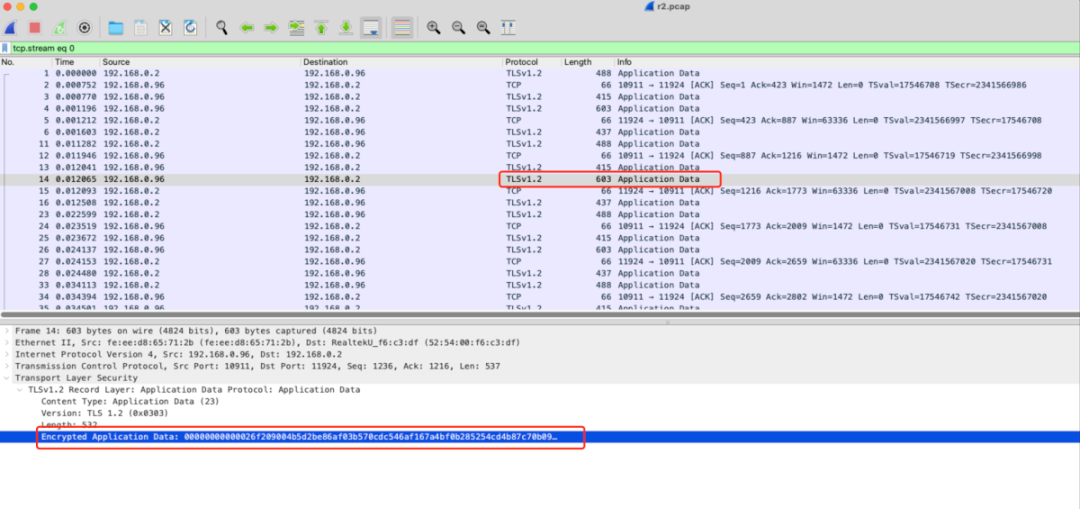
Packet capture result by using TLS
• Check the logs of the rocketmq dashboad:
~/logs/rocketmqlogs/rocketmq_client.log
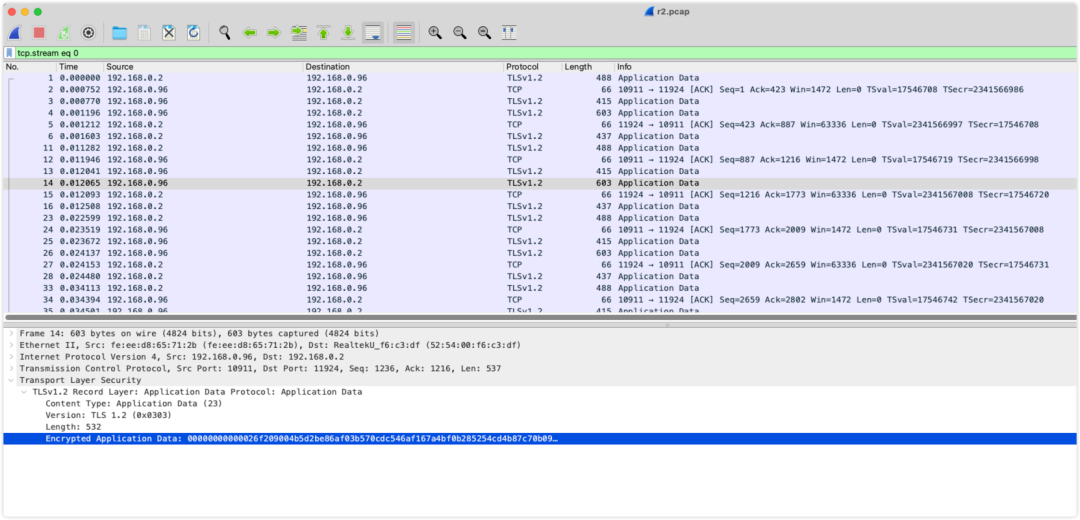
• Why is TCP still present in the packet capture result?
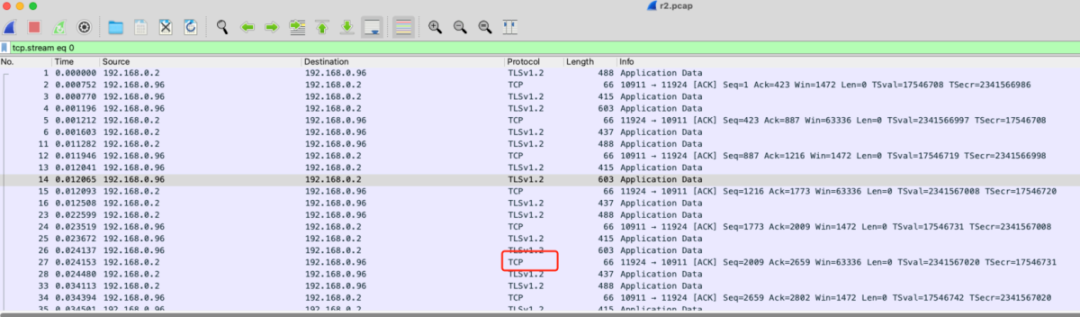
• You can enable tls on the client by setting the -Dtls.enable value to true. However, you still need to set the code "producer.setUseTLS(useTls);" or "consumer.setUseTLS(useTls);". Why?
• ca.pemca, root certificate
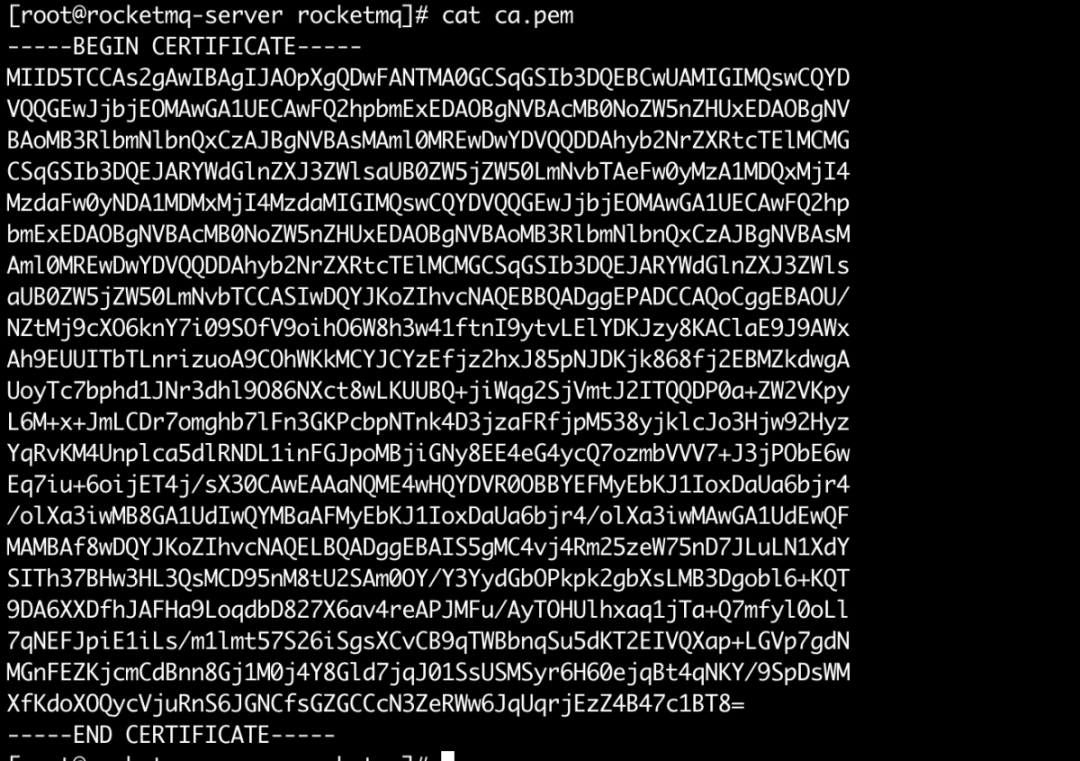
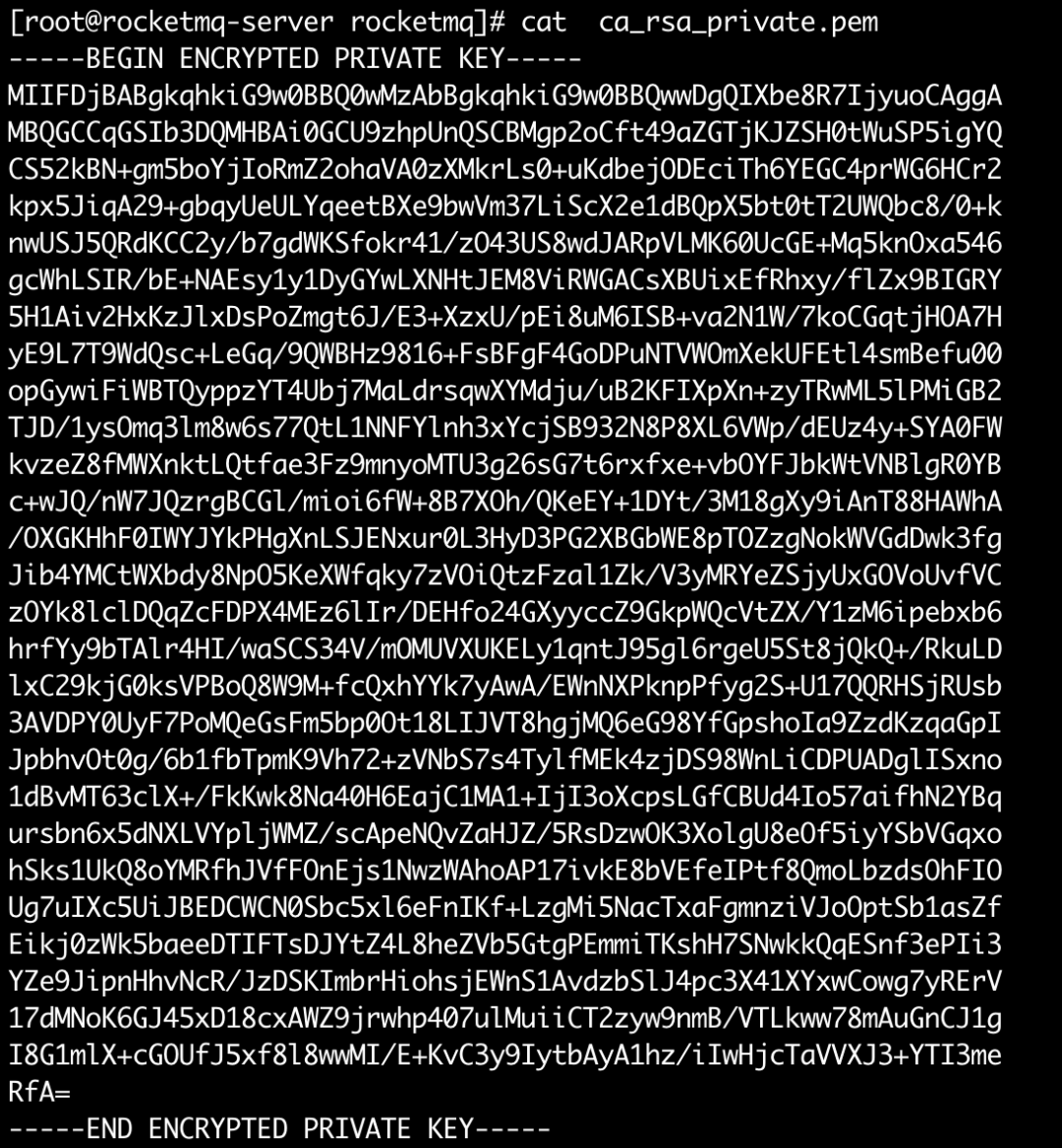
• ca_rsa_private.pemca, the encrypted private key of the root certificate
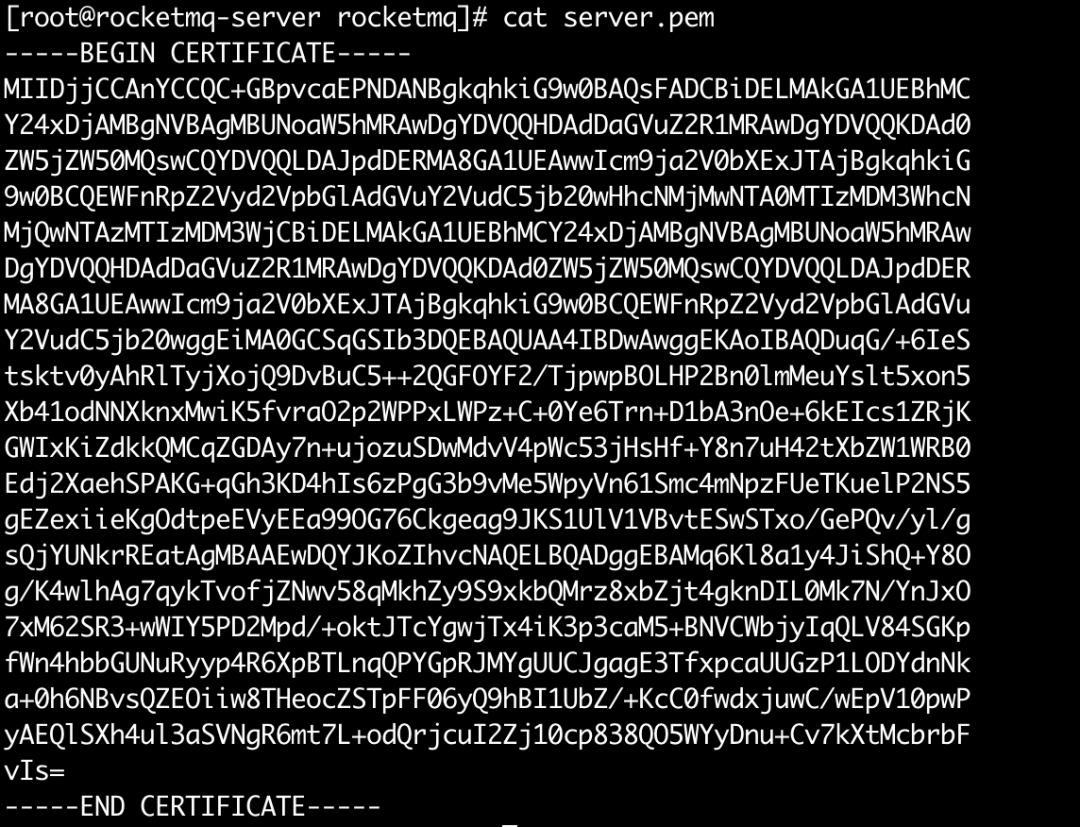
• server.pem, the certificate for the namesrv and the broker that is issued by using the root certificate
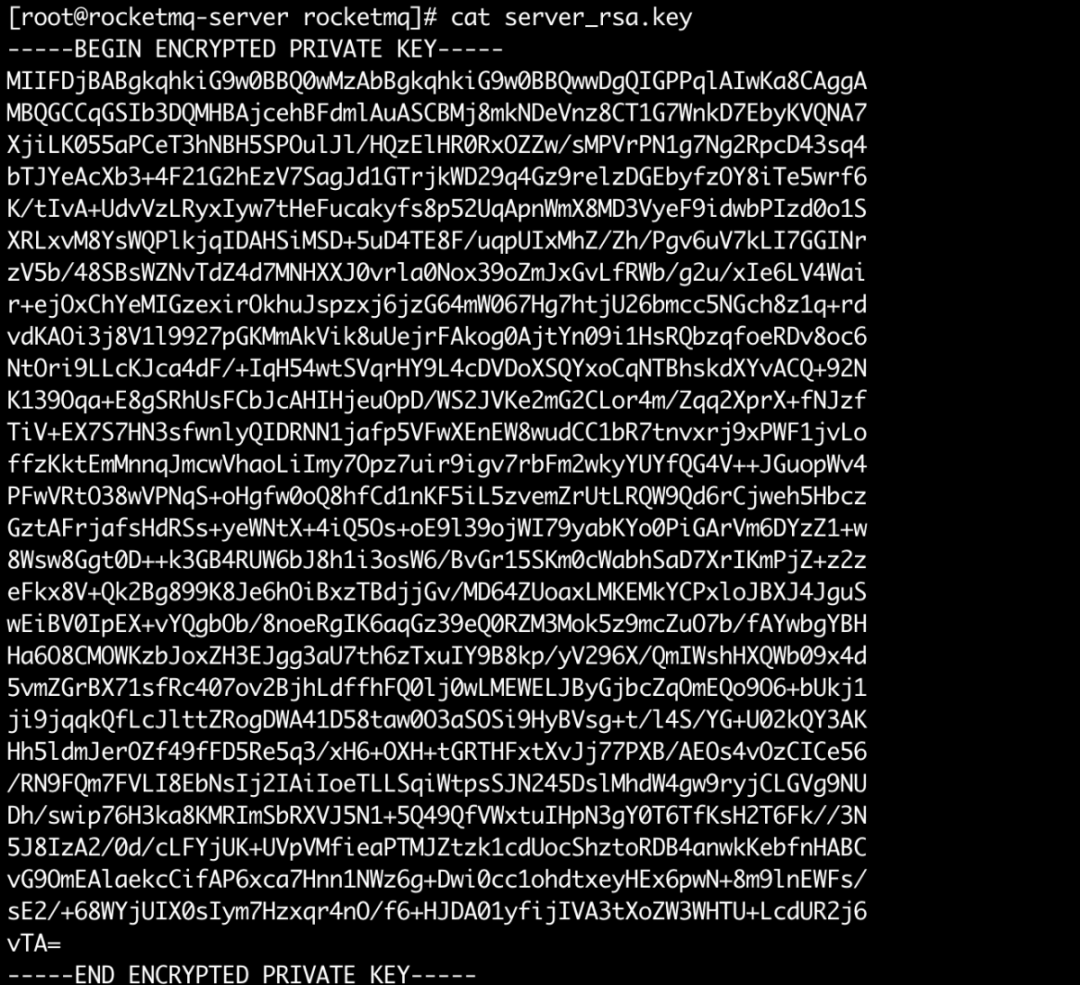
• server_rsa.key, the encrypted private key of the namesrv and the broker
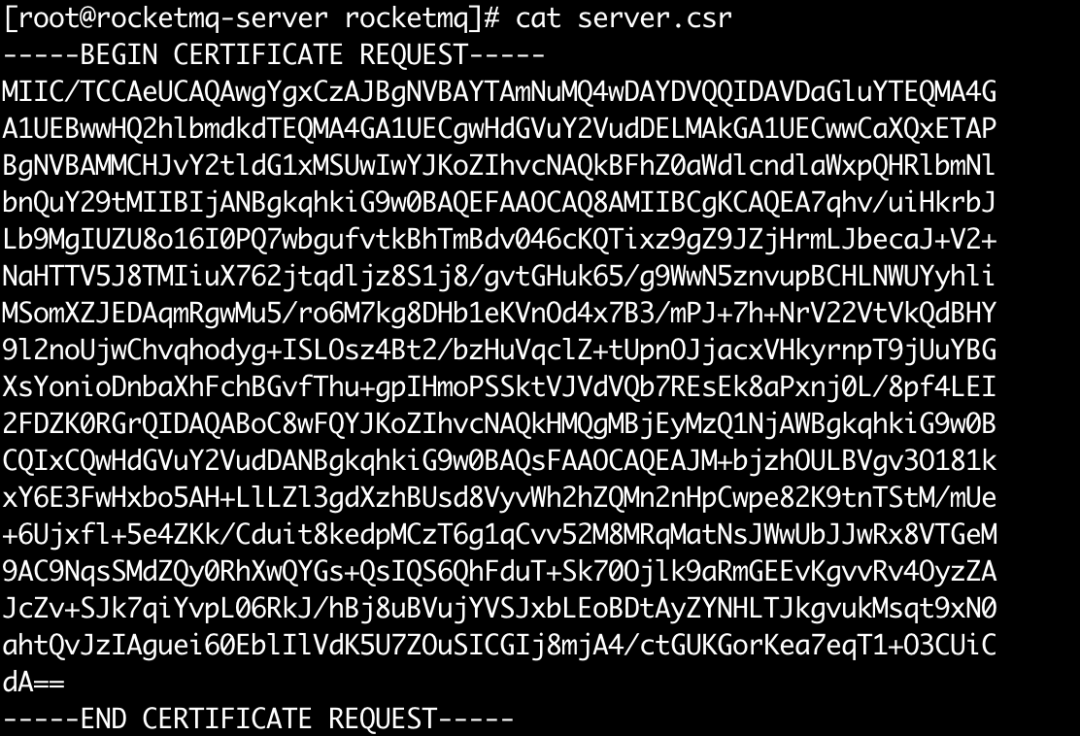
• server.csr, the public key of the encryption certificates of the namesrv and the broker, and name to identify the certificate migration authority
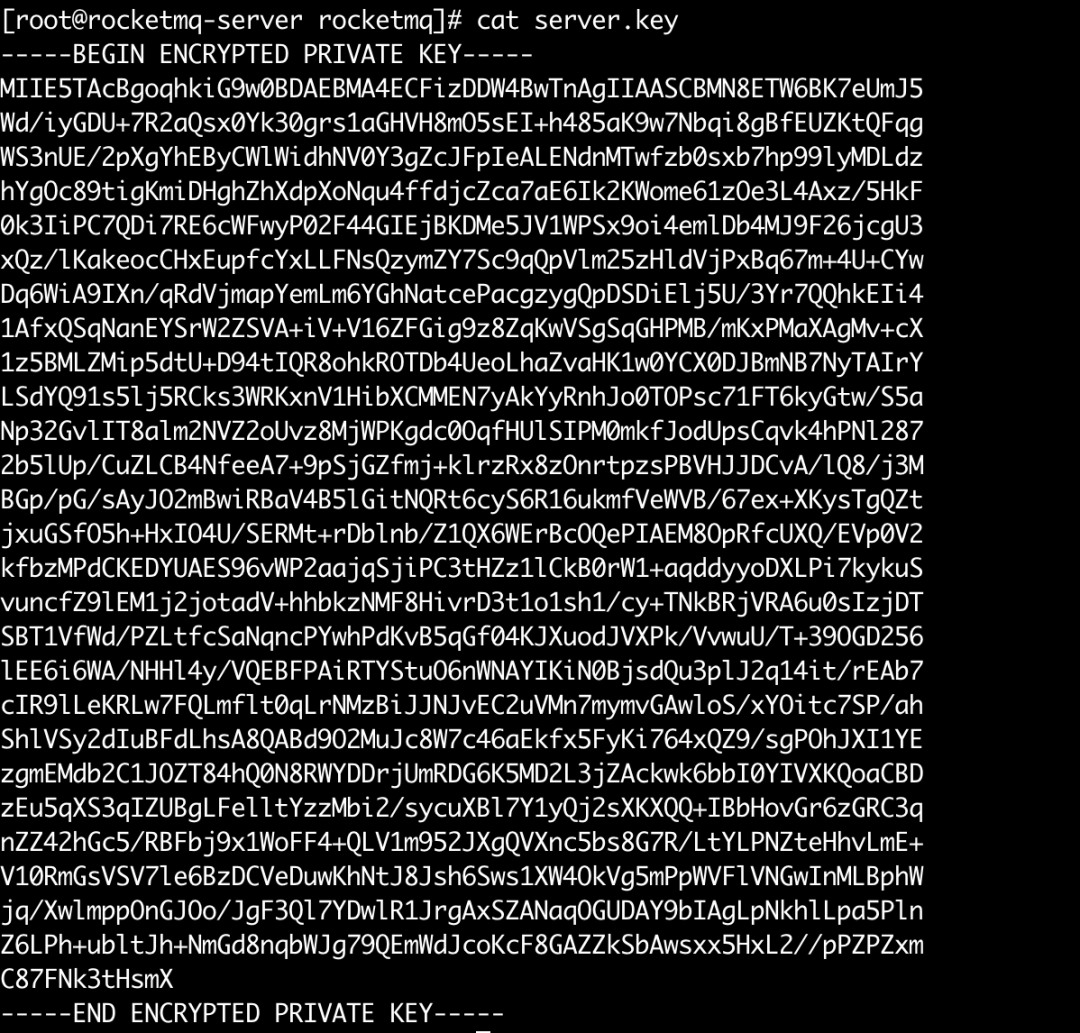
• server.key, the packaged and encrypted private key of the namesrv and the broker (server_rsa.key)
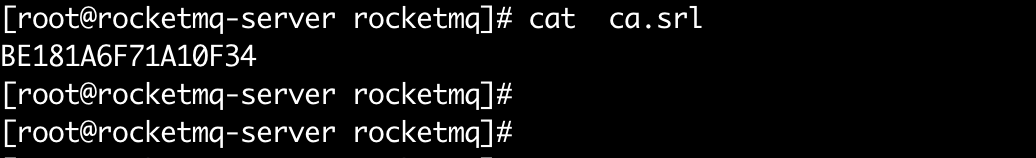
• ca.srlca, the serial number of the issued certificates
1. tls-namesrv.properties
Configuration for TLS encryption transmission identified by Netty in the Namesrv. For more details, refer to the previous section.
2. tls-broker.properties
Configuration for TLS encryption transmission identified by Netty in the Broker. For more details, refer to the previous section.
3. tls-client.properties
Configuration for TLS encryption transmission identified by Netty in the Client. For more details, refer to the previous section.
Note: The TLS configuration in RocketMQ Version 4.X is similar to that of Version 5.X. Both versions support TLS encryption.

634 posts | 55 followers
FollowAlibaba Cloud Native Community - March 20, 2023
Alibaba Cloud Community - December 21, 2021
Alibaba Cloud Native Community - July 4, 2023
Alibaba Cloud Native - June 6, 2024
Alibaba Cloud Native Community - May 16, 2023
Alibaba Cloud Community - June 2, 2022

634 posts | 55 followers
Follow ApsaraMQ for RocketMQ
ApsaraMQ for RocketMQ
ApsaraMQ for RocketMQ is a distributed message queue service that supports reliable message-based asynchronous communication among microservices, distributed systems, and serverless applications.
Learn More Function Compute
Function Compute
Alibaba Cloud Function Compute is a fully-managed event-driven compute service. It allows you to focus on writing and uploading code without the need to manage infrastructure such as servers.
Learn More Elastic High Performance Computing Solution
Elastic High Performance Computing Solution
High Performance Computing (HPC) and AI technology helps scientific research institutions to perform viral gene sequencing, conduct new drug research and development, and shorten the research and development cycle.
Learn More Quick Starts
Quick Starts
Deploy custom Alibaba Cloud solutions for business-critical scenarios with Quick Start templates.
Learn MoreMore Posts by Alibaba Cloud Native Community