By Alain Francois
When you are offering some services accessible through the Internet, it means you have some ports opened on your servers. In networking, a port can be described as a way for network traffic to identify a destination app or service. When installing and configuring some tools, you may need to open some ports. When doing this all the time, you can lose track of the ports that you have opened. If it happens, you can need to examine your server to know all the ports opened on the servers.
You also need to pay attention to open ports to detect an intrusion. Whether you are troubleshooting network connectivity issues or configuring a firewall, one of the first things to check is what ports are opened on your system. Linux systems offer you some commands to do this. This article explains several approaches on how to find out what ports are opened outside of your Linux system.
Ports are categorized into three categories. Each category is labeled as the range of port value:
Linux systems have the ports contained in the /etc/services file, with the services referring to the different ports.
You can check the ports whereyour applications are listening on your Linux systems with some useful commands.
The netstat command is useful to display network connections, routing tables, and various network interfaces. It can generate displays that show network status and protocol statistics with which ports are open or have established connections. It comes with the net-tools packages. If netstat is not present, you should install it:
For Debian's based systems:
$ sudo apt install net-toolsFor CentOS or RHEL based systems:
$ yum install net-toolsIf you run the command, you will have a lot of information:
$ netstat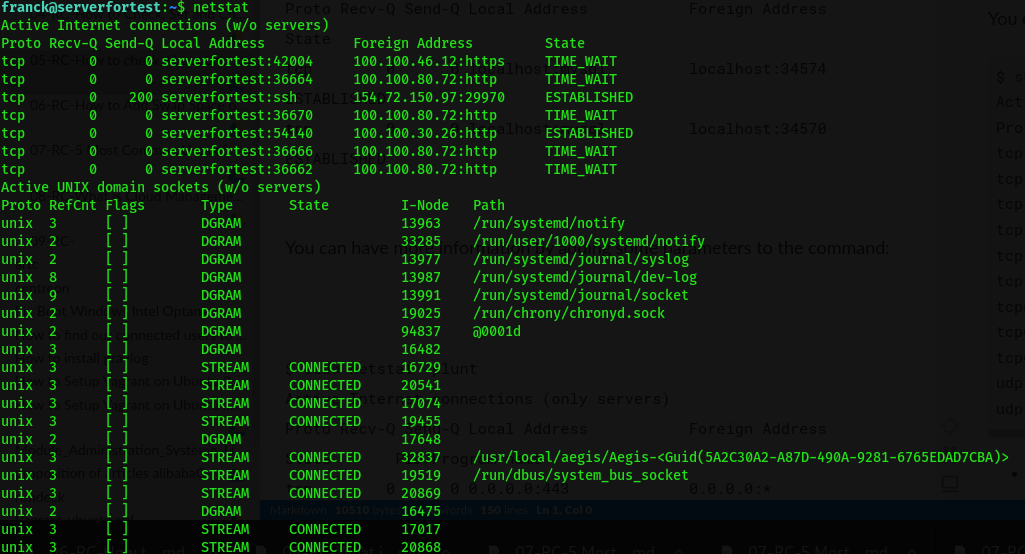
You can have more information by adding some parameters to the command:
$ sudo netstat -plunt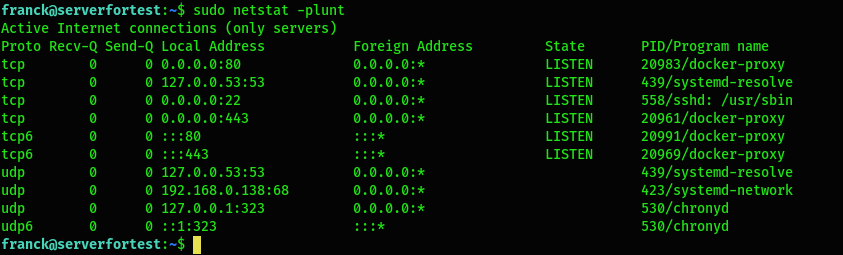
p: Display the PID/Program name related to a specific connectionl: Only show listening portsu: List UDP portsn: Show numerical addressest: List TCP portsNmap is a network scanning tool mainly used for security audits and penetration testing since it can discover open ports and services and detect vulnerabilities. If it's not present, you should install it:
For Debian's based systems:
$ sudo apt install nmapFor CentOS or RHEL based systems:
$ yum install nmapThe nmap command is used for many purposes, and you need to use some parameters to use it for port scanning purposes. If there is no parameter regarding the protocol, it will only scan the TCP port, so you should indicate it for UDP:
sT: Scan TCP portssU: Scan UDP portsp: Scan all the ports (0-65535)$ sudo nmap -sT -sU -p- localhost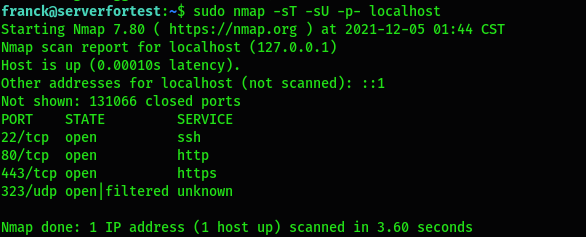
The ss command-line can be considered as a replacement of the netstat command. It is considered simpler and faster than netstat. It also gives a lot of information when used without any parameters:
$ ss
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
u_str ESTAB 0 0 * 3035735 * 3035736
u_str ESTAB 0 0 * 39874 * 39876 You can filter the result with some parameters like the ones used for the netstat command:
$ ss -lntup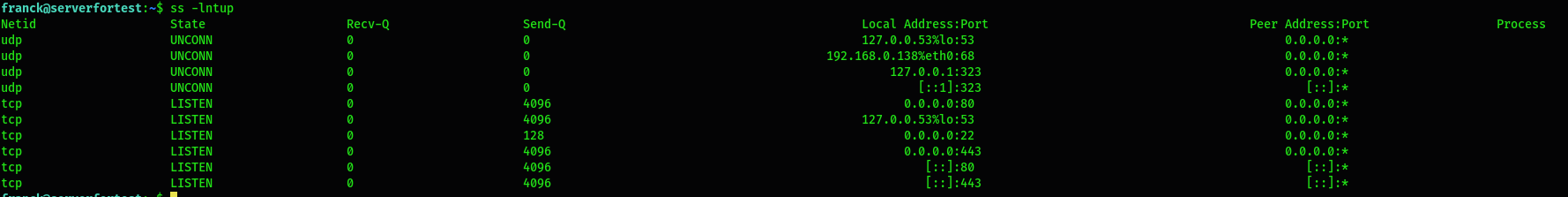
It's good to have another level of security besides your Linux firewall where you need to close all the unnecessary ports. Normally, when you host your server on Alibaba Cloud, they offer a virtual firewall called a Security Group as the first level of security to protect your server before reaching your Linux firewall. This tool ensures that there are no risks if a port is opened on your server and not open with the virtual cloud firewall. This is useful because you can open some ports on your cloud networks between your servers for tests purposes. Alibaba Cloud also offers another service called Cloud Firewall that provides a built-in intrusion prevention system (IPS). It is the primary infrastructure that you can use to protect your services in Alibaba Cloud.
The security of your servers is the most important thing. You should focus the security on your firewall system and add another layer of security through some other security services offered by your cloud provider.

1,310 posts | 461 followers
FollowAlibaba Cloud Native Community - September 13, 2023
Alibaba Clouder - August 2, 2019
Alibaba Clouder - December 28, 2018
Alibaba Clouder - March 7, 2019
Alibaba Cloud Community - January 15, 2024
Alibaba Cloud Native Community - March 14, 2023

1,310 posts | 461 followers
Follow Alibaba Cloud Linux
Alibaba Cloud Linux
Alibaba Cloud Linux is a free-to-use, native operating system that provides a stable, reliable, and high-performance environment for your applications.
Learn More Web Hosting Solution
Web Hosting Solution
Explore Web Hosting solutions that can power your personal website or empower your online business.
Learn More Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn More Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn MoreMore Posts by Alibaba Cloud Community
Dikky Ryan Pratama May 6, 2023 at 12:24 pm
wow . very easy article to understand.