When testing the security of an Internet of Things (IoT) network, people naturally take embedded devices as the key test objects. This approach, while convenient, provides only a partial understanding of the entire end-to-end ecosystem. Effective evaluation methods should consider the entire IoT solution or the entire IoT product ecosystem. In short, security teams should evaluate every item in the product security evaluation in the context of the entire IoT product ecosystem.

The IoT product ecosystem consists of the following aspects:
The following figure shows the complete IoT product ecosystem:
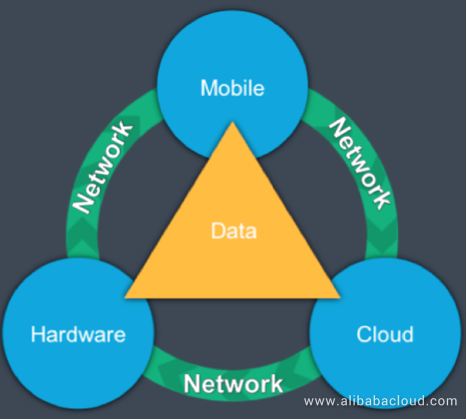
Security teams must conduct a comprehensive security check on the entire IoT ecosystem to ensure that all related products or components are secure. Failures of any component in the product ecosystem may affect the security of the ecosystem. For example, due to security vulnerabilities of the cloud APIs, it is easy for hackers to access and control embedded hardware without authorization. Consequently, they can launch malicious attacks on users' IoT products, such as refrigerators and DVDs, among others.
We will show how to conduct a complete IoT security evaluation covering every aspect of the IoT product ecosystem.
When testing the IoT product ecosystem, we will first configure various functions of IoT products under the common product specifications. To achieve better test effects, we need to configure two mutually independent Internet product running environments to test the danger of attacks. This is because hackers may implement cross-user or cross-system attacks on two independent environments. Besides, we can use the two independent environments to compare security configuration of products. By testing the functions of each product, we can efficiently evaluate functional security features, component features, and the communication path of every product in the product ecosystem, thus covering the entire IoT product ecosystem.
In addition to testing, we will also need to obtain all IoT information related to the tested product. Such information includes the information about the related product components, infrastructure that supports running of the product, support software required for running the product, and external components that are used to implement various cloud functions of the product.
An IoT network typically uses various network services for remote control, data collection, and product management. Generally, network services and cloud APIs are the weakest parts in the IoT product ecosystem. Developers can use cloud APIs for encoding, and each API has a service of the cloud provider. Meanwhile, cloud APIs may bring security risks to cloud applications, because threat actors can easily attack APIs putting sensitive service data at risk. This means that providers and software developers must determine the security of cloud APIs on priority.
Therefore, to ensure authentication security on the cloud, we need to test functions of and communications between the cloud service and all components in the IoT product ecosystem, to perform a comprehensive evaluation on the related cloud service. In this way, we can verify the general security status of the product and confirm security problems that are caused by the cloud. Consequently, we can evaluate the impact of these problems on security between the components.
Additionally, we will use OWASP Top10 for the focus test during the cloud test.
Note: Open Web Application Security Project (OWASP) is an open community dedicated to the discussion of applications and code development threats. OWASP Top10 aims to locate the top 10 risks faced by enterprises or organizations to increase people's concerns on security of applications.
The IoT technology often uses various types of remote control services, such as mobile applications (Android or iOS), to remotely manage and control IoT. In this test process, we perform an in-depth test and analysis of the mobile and remote applications that are used to manage IoT products. Like the cloud test, we test all functions of and communications between mobile applications and all components in the IoT product ecosystem to verify the general security state of the product. Also, we will use OWASP Top10 for the focus test during the mobile application test.
IoT often uses standard network communication paths, such as Ethernet and Wi-Fi, to access various services. This is convenient but also introduces many risks. In this test phase, we are going to identify all TCP and UDP ports in the IoT ecosystem infrastructure that are connected to the product. Through these ports, we can conduct a thorough penetration test to identify services that are vulnerable to attacks or have configuration errors. Hackers often use these service vulnerabilities to attack the IoT system and obtain key access information.
We will also check IoT devices to evaluate security against the physical layer attacks. Checked objects also include devices with the JTAG port and serial port, power devices of various components, and data and control pins. Although devices have different components or configurations, they have some common attack vectors, for example:
The physical check of a device is the key to thwarting physical attacks. As mentioned earlier, after checking each component of the device, we can start the physical attack test. Although the attack media may be different, the measures and methods are the same as we have listed above:
Currently, most of the IoT devices still rely on radio communication. Testing security of the communication methods is also a key task of security evaluation. For this purpose, we conduct dedicated tests and analysis on radio communication to check whether communication meets the following expected encryption and protection requirements:
We hope that this article will provide a fresh perspective to cybersecurity practitioners for evaluating security in the world of IoT devices.
You can find similar articles and learn more about Alibaba Cloud's products and solutions at https://www.alibabacloud.com/blog.
From Single-tenant IaaS to Multi-tenant PaaS - Multi-tenant Isolation with MaxCompute

2,605 posts | 747 followers
FollowAlibaba Clouder - November 11, 2020
Alibaba Clouder - October 27, 2020
Alibaba Clouder - July 5, 2019
Alibaba Clouder - January 26, 2021
zcm_cathy - December 7, 2020
Alibaba Cloud ECS - September 10, 2020

2,605 posts | 747 followers
Follow IoT Platform
IoT Platform
Provides secure and reliable communication between devices and the IoT Platform which allows you to manage a large number of devices on a single IoT Platform.
Learn More IoT Solution
IoT Solution
A cloud solution for smart technology providers to quickly build stable, cost-efficient, and reliable ubiquitous platforms
Learn More Quick Starts
Quick Starts
Deploy custom Alibaba Cloud solutions for business-critical scenarios with Quick Start templates.
Learn More Global Internet Access Solution
Global Internet Access Solution
Migrate your Internet Data Center’s (IDC) Internet gateway to the cloud securely through Alibaba Cloud’s high-quality Internet bandwidth and premium Mainland China route.
Learn MoreMore Posts by Alibaba Clouder