
Business is taking off. You are hiring new people, expanding your customer base and you have just bought a new work van to handle the recent spike in orders.
Purchasing the vehicle is a significant investment for your business, including the extra expenditure to brand the vehicle with your company logo.
But all week you’re beaming with delight at the sight of your company’s new vehicle; which doubles as a portable billboard for your company.
However, four days in you wake up to a nasty surprise. Overnight a local graffiti gang has vandalized and tagged the van in three different colors. The news only gets worst when you spot a crude artistic attempt to depict the male genitalia next to your logo. Having just spent a small fortune (from the company’s point of view) to invest in the new vehicle, this was the last thing you needed!
The cyber world is no different when it comes to malicious operators damaging company assets.
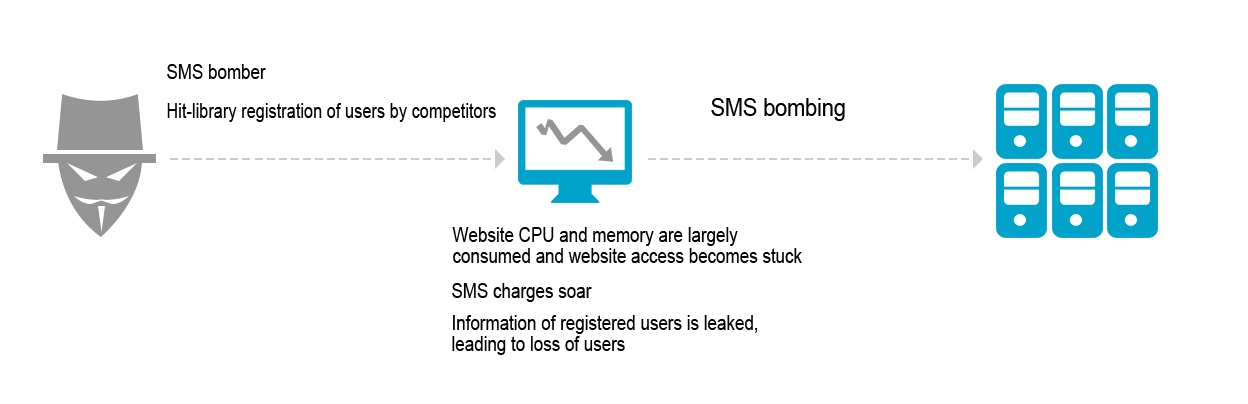
Distributed Denial of Service (DDoS) is one particular attack you want to avoid as a law-abiding netizen. DDoS attacks come in various shapes and sizes, and one common category of DDoS attack is a SMS flooding attack. An SMS flooding attack occurs when a high volume of cellular SMS messages are sent to saturate and overload the website’s server.
This leads to slow website server performance, soaring SMS registration verification charges and leaking of customer contact information.
What is a SMS traffic flooding attack?
For many websites, online users must provide their mobile phone number upon registration in order to validate their identity. Normally, users will click a button during the registration process to send a SMS message and a SMS message is sent to verify the user’s mobile phone number. However, if there are no defense policies protecting the SMS interface, attackers can leverage programs to send high frequency requests to the SMS interface.
Screenshot of online sign up form with SMS verification
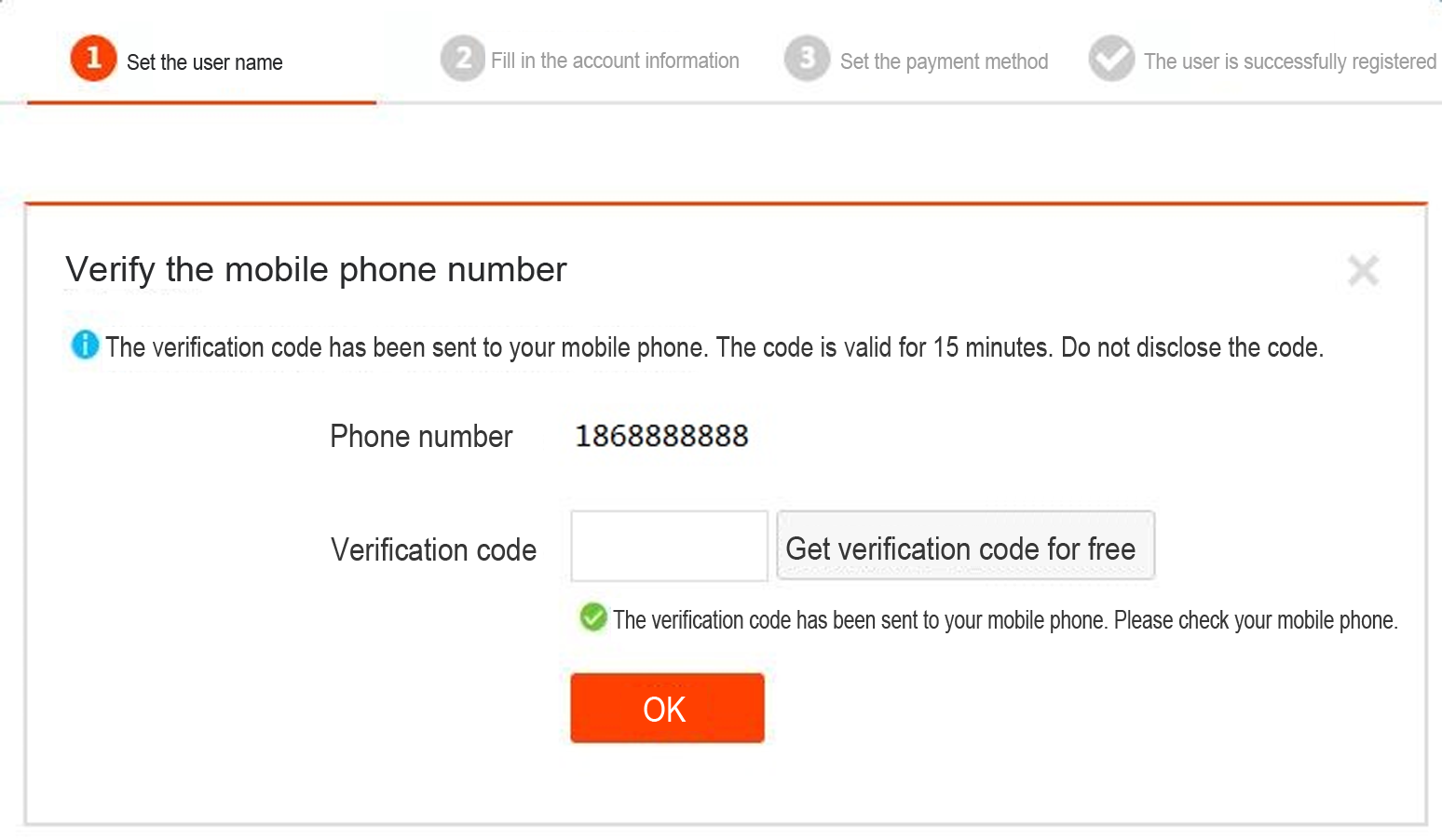
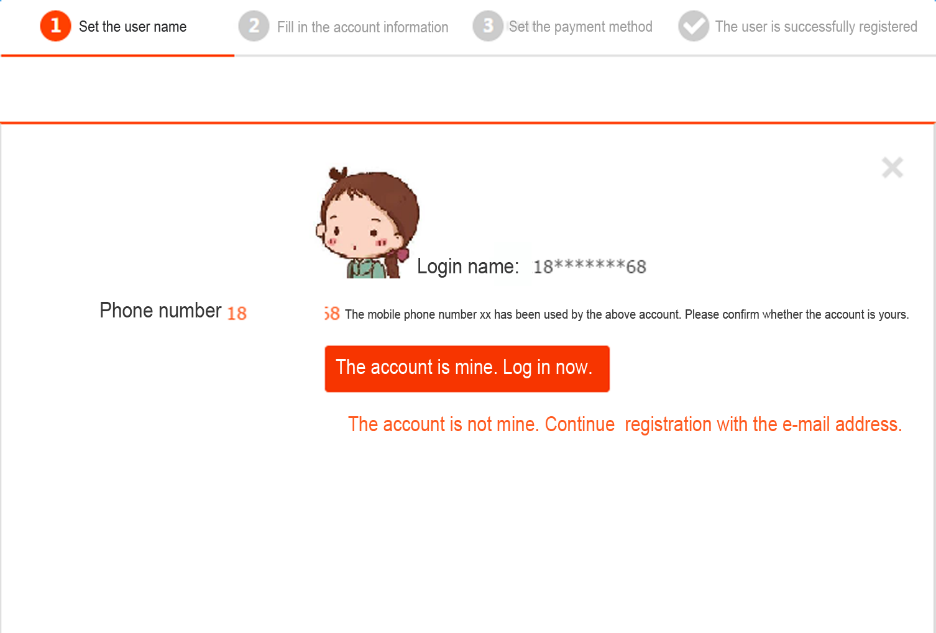
Screenshot of a flood attached registered
user:
Harm to website owner
1) SMS verification requests consume website CPU and memory which can lead to poor performance issues.
2) SMS charges soar!
3) Information of registered users can be leaked, and threaten the business’ reputation and customer base. Explanation: Users that later go to login or signup for an account and whose number has been already registered under a flood attack may be asked to verify their account via email. After adding their email contact details to the account, the hacking party then has access to their email details. The hacker can then sell email contact details to your competitors for precision marketing purposes.
SMS flooding can also be used in special circumstances to assist cybercriminal activities, such as account hacking and transferring money out of a compromised account. Flood attacks that generate thousands of SMS messages can be used to prevent the account owner from detecting a SMS notification of the fraudulent behaviour/transaction.
Defense Policy
The Alibaba Cloud “Web Application Firewall” (For Enterprise) provides defense against traffic flooding attacks to SMS interfaces. Based on big data analysis on access behavior and SMS bomber behavior modeling, Web Application Firewall matches the attack behavior and adds the IP address initiating such behaviors to a blacklist.
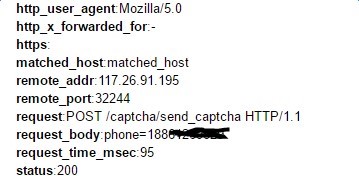
For example, the figure below shows a traffic flooding attack to the SMS interface:
Alibaba Cloud “Web Application Firewall” not only protects SMS interfaces against traffic flooding attacks, but also:
1. Prevents data leaks
2. Defends against malicious CC attacks
3. Prevents Trojan horse attacks and tampering of websites
4. Offers virtual patching to repair loopholes
Cloud Computing, Big Data and VR are Transforming the Real Estate Industry

2,605 posts | 747 followers
FollowAlibaba Clouder - July 30, 2020
Alibaba Clouder - June 28, 2020
Alibaba Clouder - December 23, 2020
Alibaba Clouder - July 8, 2019
Alibaba Cloud New Products - June 10, 2020
Alibaba Cloud Security - December 25, 2018

2,605 posts | 747 followers
Follow Anti DDoS Basic
Anti DDoS Basic
A cloud-based security service that protects your data and application from DDoS attacks
Learn More Anti-DDoS
Anti-DDoS
A comprehensive DDoS protection for enterprise to intelligently defend sophisticated DDoS attacks, reduce business loss risks, and mitigate potential security threats.
Learn More Short Message Service
Short Message Service
Short Message Service (SMS) helps enterprises worldwide build channels to reach their customers with user-friendly, efficient, and intelligent communication capabilities.
Learn More Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn MoreMore Posts by Alibaba Clouder
Raja_KT March 3, 2019 at 8:57 am
Interesting. SMS traffic flooding vs network latency can be misleading if we blacklist the IPs .