By Juan Patrick, Solution Architect Intern
In the technology today, authentication is essential for securing users when they access information from systems and services. We need to make sure that only the authorized users can access the information, and authentication mechanism is always implemented for each system and applications. Standard password is still used as a solution for a traditional authentication method in many applications. Users need to remember their user name and password during registration. This implementation can make it easier for the system architect to prevent unauthorized access.
However, the password is the weakest link in security, which can lead to data breaches and vulnerabilities. According to the 2022 Verizon Data Breach Investigations Report, more than 80% of data breaches were caused by stolen credentials. It makes “Passwordless” authentication an alternative method to be developed. This article will discuss about “Passwordless” authentication and related technologies in Alibaba Cloud to implement this solution.
The purpose of the article is to introduce to the reader about the design of “Passwordless” authentication. The topics to be covered in the article will be:
Before talking about passwordless, we understand that there is no best practice in security. We can consider the system secure if its resources are accessed as intended under all circumstances. There is no absolute security that can ensure the system from several threats and unauthorized access. When we talk about security, it refers to how can a system authenticates users. So, we want to make sure that only authorized users can access system information. In the CIA triad, strengthening the user authentication mechanism was applied in Confidentiality. In the end, we need to take other practices of security to minimize potential cyber threats.
Passwordless Authentication means verifying the user without using the password, but it replaces with something you have, like a fingerprint, face, eye scan, or voice. You don’t have to remember your password or write it on the note. This makes good for the user experience, you don’t need to worry about forgetting your password. The main goal of passwordless is to erase the plaintext password and reduce the cyber risks associated with them.
There are different ways to implement the Passwordless Authentication:
Magic Link
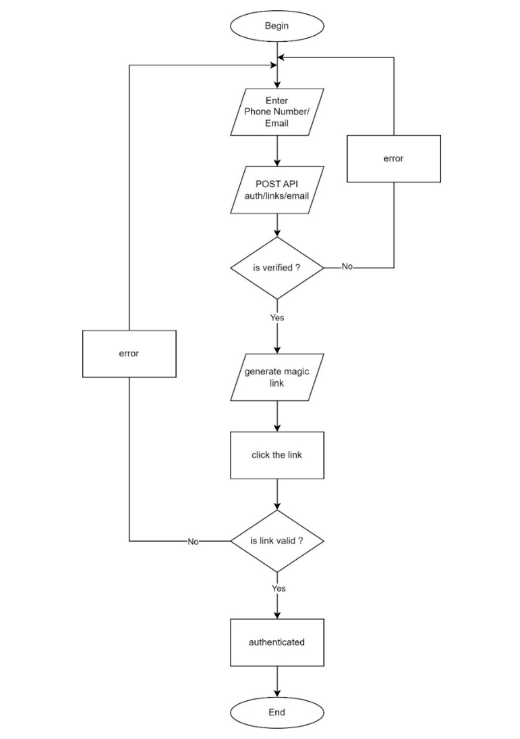
Magic Link is authentication sent to an email containing a link to instantly log users into their desired application. It replaces the password with the one-time link but has some threats, like compromised email, MITM (Man-in-the-Middle attack), and no assurance of the recipient user.
The figure below is a flowchart describing the way the system works when users authenticated with a magic link. Users enter their mobile phone number or email registered to get system access as a link consisting of token code. This link redirects the user immediately to the application and the system checks whether the link is verified or not.
Possession Factor
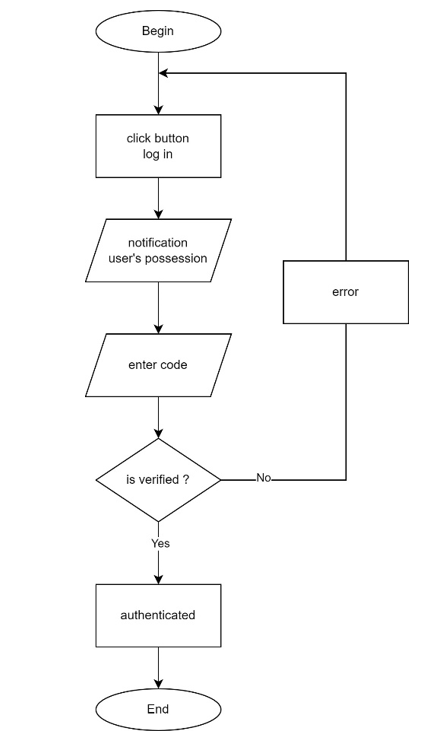
The possession factor is user authentication credentials based on something you have, like a smart card, hard token, or phone with an authenticator app. It's also called the ownership factor. Users show the authenticator as identity verification and bring it everywhere.
Using the assist device, users access the system by receiving a code notification when logging in, as shown in the figure below. The assist device is a trusted device that has been granted access to the system. Consequently, users must have an assist device to access the system.
Take the Possession Factor based Passwordless Authentication as example, we can see the benefits of Passwordless Authentication methods:
1) High security: passwordless offers increased levels of assurance to providers that a person is real through verifying a real-world trait as each something a person has and is.
2) Convenient and fast: passwordless authentication is easier to take an action than password authentication. Showing your face to log in to the system and be authenticated in seconds.
3) Spoof proof: those methods are hard to replicate it.
4) Non-transferable: unique set of hardware.
At the same time, to implement Passwordless Authentication, there are some challenges to take note:
1) Costs: require significant investment in biometrics for security.
2) Tracking and data: limit privacy users.
3) False positives and inaccuracy: false rejection can still happen when users access the system.
A passwordless authentication system can be overwhelming for you. You do not need to build it from scratch, we may use the services available on Alibaba Cloud. Part of Alibaba Cloud ecosystems, ZOLOZ RealID provides liveness detection with ± 99.9% accuracy and spoof detection. ZOLOZ also has an eKYC service for the identity proofing process. To implement ownership factors, KeyCloak provides OTC (One-Time Code) and you can set it up on ECS. These are the following related articles:
ZOLOZ Practices:
SSO Practices:
Passwordless is a good choice as a primary authentication solution for the system. Passwordless offers higher security for our data. Many SaaS services provide passwordless authentication. In the future, organizations have started deploying passwordless authentication.
References:
[1] Gordin, A. Graur, S. Vlad and C. I. Adomniței, "Moving forward passwordless authentication: challenges and implementations for the private cloud," 2021 20th RoEduNet Conference: Networking in Education and Research (RoEduNet), 2021, pp. 1-5, doi: 10.1109/RoEduNet54112.2021.9638271.
[2] V. Parmar, H. A. Sanghvi, R. H. Patel and A. S. Pandya, "A Comprehensive Study on Passwordless Authentication," 2022 International Conference on Sustainable Computing and Data Communication Systems (ICSCDS), 2022, pp. 1266-1275, doi: 10.1109/ICSCDS53736.2022.9760934.
[3] https://www.pingidentity.com/en/resources/content-library/white-papers/3480-passwordless-authentication.html (Accessed 2 November 2022)
[4] https://www.verizon.com/business/resources/reports/dbir/2022/results-and-analysis-intro/ (Accessed 2 November 2022)
[5] https://www.scmagazine.com/resource/identity-and-access/passwordless-authentication-getting-started-on-your-passwordless-journey-part-1 (Accessed 2 November 2022)
Service Mesh Configuration In A Microservice Application - Step By Step
117 posts | 21 followers
FollowAlibaba Clouder - June 18, 2019
CloudSecurity - December 9, 2025
Alibaba Cloud Indonesia - December 14, 2022
Hiteshjethva - March 2, 2020
Alibaba Cloud Native - March 6, 2024
Alibaba Cloud Security - November 17, 2018
117 posts | 21 followers
Follow Intelligent Speech Interaction
Intelligent Speech Interaction
Intelligent Speech Interaction is developed based on state-of-the-art technologies such as speech recognition, speech synthesis, and natural language understanding.
Learn MoreMore Posts by Alibaba Cloud Indonesia
Kidd Ip April 4, 2023 at 12:52 am
Agree, convenience and secure!