Very secure FTP daemon (vsftpd) is a popular, open-source FTP server software known for its high performance, security, and stability. vsftpd supports various protocols, such as FTP, SFTP over Secure Shell (SSH), and FTP over Transport Layer Security (TLS)/Secure Sockets Layer (SSL) encryption. This topic describes how to install and configure vsftpd on a Linux Elastic Compute Service (ECS) instance.
Quick deployment
Click Run Now to open Terraform Explorer. You can then view and run the Terraform code to automatically build an FTP site on an ECS instance.
Prerequisites
An ECS instance that meets the following requirements is required. If you have not created an instance, see Create an instance using the wizard.
Operating system: Alibaba Cloud Linux 3 or 2, CentOS 7.x 64-bit, Ubuntu, or Debian.
IP address: The instance must have a static public IP address or be associated with an Elastic IP Address (EIP). For more information, see Elastic IP Address.
Introduction to VSFTP
vsftpd (Very Secure FTP Daemon) is an open-source FTP server software designed for UNIX and Linux systems. Its main features include the following:
High security: vsftpd is subject to strict security audits and uses multiple security mechanisms to prevent common attacks and vulnerabilities.
High performance: It provides high-performance file transfer and supports many concurrent user connections.
Simple configuration: It provides flexible and easy-to-understand configuration options.
IPv6 support: It supports the next-generation network protocol.
Build the VSFTP service
Alibaba Cloud Linux 3 and 2 / CentOS 7.x
Step 1: Install vsftpd
Run the following commands to update system components and install the
vsftpdservice.sudo yum update -y sudo yum install vsftpd -yRun the following commands to start the FTP service and enable it to start automatically on system startup.
sudo systemctl start vsftpd sudo systemctl enable vsftpdRun the following command to check if the service has started.
netstat -antup | grep ftpIf output similar to the following is returned, the FTP service has started.
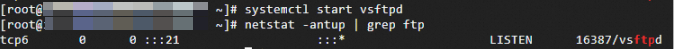
By default, vsftpd has anonymous user mode enabled. You can log on to the FTP server without a username and password. Users who log on in this mode do not have permission to modify or upload files.
Step 2: Configure vsftpd
Run the following commands to create a dedicated user for the FTP service and set a password. This topic uses
ftpuseras an example.sudo useradd -d /data/ftp -s /sbin/nologin ftpuser # Specify the home directory and disable Shell access sudo passwd ftpuserRun the following commands to create a folder for the FTP service and configure its permissions.
sudo mkdir -p /data/ftp # Create a custom storage folder sudo chown ftpuser:ftpuser /data/ftp sudo chmod 750 /data/ftp # Permissions must be 755 or 750Edit the
vsftpdconfiguration file.NoteFTP can connect to clients and transfer data in active or passive mode. Because of client-side firewalls and potential issues with obtaining public IP addresses, we recommend that you configure the FTP service to use passive mode. The following steps describe how to configure passive mode.
Run the following command to back up the
vsftpdconfiguration file.sudo cp /etc/vsftpd/vsftpd.conf /etc/vsftpd/vsftpd.conf.bakRun the following command to modify the configuration file.
sudo vim /etc/vsftpd/vsftpd.confModify the basic security settings for the FTP service.
listen=YES # Enable IPv4 listener anonymous_enable=NO # Disable anonymous access local_enable=YES # Enable local user logon write_enable=YES # Allow file uploads chroot_local_user=YES # Lock user to home directory allow_writeable_chroot=YES # Resolve chroot write errorAdd the passive mode configuration at the end of the configuration file.
pasv_enable=YES # Enable passive mode pasv_min_port=40000 # Lower bound of passive port range pasv_max_port=40100 # Upper bound of passive port range pasv_address=public_IP_address # Must be set to the server's public IP address
Run the following command to restart the
vsftpdservice.sudo systemctl restart vsftpd
Step 3: Set security group rules
After you build the FTP service, you must add inbound rules to the security group of the Linux ECS instance based on the FTP mode that you are using. For more information, see Add a security group rule.
Most clients are on local area networks (LANs), where their IP addresses are translated. If you use FTP active mode, you must ensure that the clients can obtain their public IP addresses. Otherwise, clients may fail to log on to the FTP server. A proper configuration helps prevent connection issues and improves the stability and availability of the FTP service.
Active mode: Allow traffic on port 21.
Passive mode: Allow traffic on port 21 and on the port range defined by pasv_min_port and pasv_max_port in the /etc/vsftpd/vsftpd.conf file. In this topic, the allowed port range is 40000 to 40100. For information about why you need to allow a port range for passive mode and for configuration suggestions, see FTP passive mode port configuration suggestions.
Step 4: Verify the FTP service
You can use an FTP client, browser, or file explorer to verify the FTP service. This topic uses a client's file explorer as an example.
Test the local connection.
Run the following command to test the connection on the local machine.
ftp ftpuser@localhostA
Login successfulmessage in the output indicates a successful connection.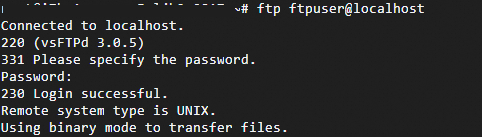
Test the client connection.
On the client computer, open File Explorer and enter the FTP address in the address bar, as shown in the following figure.
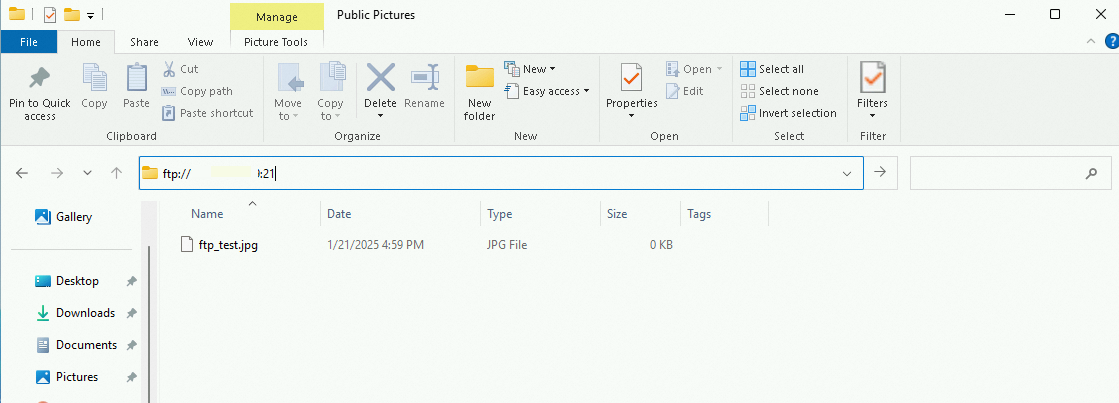
In the logon window, enter the FTP username and password. After you successfully log on, you can upload and download files.
Ubuntu and Debian
Step 1: Install VSFTP
Run the following commands to update system components and install the
vsftpdservice.sudo apt update && sudo apt upgrade -y sudo apt install vsftpd -yRun the following commands to start the
vsftpdservice and enable it to start automatically on system startup.sudo systemctl start vsftpd sudo systemctl enable vsftpd
Step 2: Configure VSFTP
Run the following commands to create a dedicated FTP user.
sudo useradd -m -s /bin/bash ftpuser # Create a user and automatically generate a home directory sudo passwd ftpuser # Set the user password (a strong password is recommended)Run the following commands to create a file storage folder and configure permissions.
sudo mkdir /home/ftpuser/ftp-files sudo chown ftpuser:ftpuser /home/ftpuser/ftp-files sudo chmod 755 /home/ftpuser/ftp-filesRun the following command to back up the original configuration file.
sudo cp /etc/vsftpd.conf /etc/vsftpd.conf.bakRun the following command to edit the configuration file.
sudo nano /etc/vsftpd.confModify the following parameters in the file:
# Basic configuration listen=YES anonymous_enable=NO # Disable anonymous access local_enable=YES # Allow local user logon write_enable=YES # Enable write permissions chroot_local_user=YES # Lock user to home directoryAdd the following parameters to the end of the file:
allow_writeable_chroot=YES # Allow writing to the chroot directory local_root=/home/ftpuser/ftp-files # Specify the root directory for the ftp user # Passive mode configuration (to resolve external network connection issues) pasv_enable=YES pasv_address=xx.xx.xx.xx # Replace with your public IP address pasv_min_port=40000 pasv_max_port=40100Run the following command to restart the FTP service.
sudo systemctl restart vsftpd
Step 3: Set security group rules
After you build the FTP service, you must add inbound rules to the security group of the Linux ECS instance based on the FTP mode that you are using. For more information, see Add a security group rule.
Most clients are on local area networks (LANs), where their IP addresses are translated. If you use FTP active mode, you must ensure that the clients can obtain their public IP addresses. Otherwise, clients may fail to log on to the FTP server. A proper configuration helps prevent connection issues and improves the stability and availability of the FTP service.
Active mode: Allow traffic on port 21.
Passive mode: Allow traffic on port 21 and on the port range defined by pasv_min_port and pasv_max_port in the /etc/vsftpd/vsftpd.conf file. For information about why you need to allow a port range for passive mode and for configuration suggestions, see Build an FTP site on a Windows instance.
Step 4: Verify the FTP service
You can use an FTP client, browser, or file explorer to verify the FTP service. This topic uses a client's file explorer as an example.
Test the local connection.
Run the following command to test the connection on the local machine.
ftp ftpuser@localhostA
Login successfulmessage in the output indicates a successful connection.
Test the client connection.
On the client computer, open File Explorer and enter the FTP address in the address bar, as shown in the following figure.

In the logon window, enter the FTP username and password. After you successfully log on, you can upload and download files.
Common errors
Symptom | Solution |
The connection times out after the | Check the public IP address binding and ensure that the firewalls on both the client and the server allow the required traffic. |
| Change the directory permissions to 755. |
An empty directory is listed. | Check the |
The | Run the |
The connection times out in passive mode. | Check the firewall rules and the pasv_address parameter. |
Files cannot be uploaded. | Verify that the directory permissions are set to 755 or 750. |
Appendix
vsftpd configuration file and parameters
The following list describes the files in the /etc/vsftpd directory:
/etc/vsftpd/vsftpd.confis the core configuration file of vsftpd./etc/vsftpd/ftpusersis a blacklist file. Users listed in this file cannot access the FTP server./etc/vsftpd/user_listis a whitelist file. Users listed in this file are allowed to access the FTP server.
The following tables describe the parameters in the vsftpd.conf configuration file.
The following table describes the parameters for logon control.
Parameter
Description
anonymous_enable=YES
Accepts anonymous users.
no_anon_password=YES
Anonymous users can log on without a password.
anon_root=(none)
Specifies the home directory of anonymous users.
local_enable=YES
Accepts local users.
local_root=(none)
Specifies the home directory of local users.
The following table describes the parameters for user permission control.
Parameter
Description
write_enable=YES
Allows file uploads (global control).
local_umask=022
File permissions for files uploaded by local users.
file_open_mode=0666
File permissions for uploaded files. Used with umask.
anon_upload_enable=NO
Anonymous users can upload files.
anon_mkdir_write_enable=NO
Anonymous users can create directories.
anon_other_write_enable=NO
Anonymous users can modify and delete files.
chown_username=lightwiter
Specifies the owner of files uploaded by anonymous users.