System | Procedure for changing a logon password |
Linux | Log on to your Linux server and run the passwd <UserName> command to change the logon password. After you run the command, enter a new password as prompted. If you do not specify a username for <UserName>, the password of the current user is changed. |
Windows | In this example, the logon password for a server that runs Windows Server 2019 is changed. Log on to your Windows server. In the lower-left corner of the Windows desktop, click the  icon. icon. Click the  icon. In the Windows Settings window, click Accounts. icon. In the Windows Settings window, click Accounts. In the left-side navigation pane, click Sign-in options. Change the logon password of the server as prompted.
|
MySQL database | Log on to your MySQL database. Run the following command to view the password information about database users: SELECT user, host, authentication_string FROM user;
Note The command may not be supported by some versions of MySQL databases. If you cannot obtain the password information after you run the command, you can run the following command: SELECT user, host, password FROM user;
Run the following command to change the password of a specific user based on the query results and the alert information about weak passwords: ALTER USER '<UserName>'@'<HostName>' IDENTIFIED BY '<NewPassword>';
Run the flush privileges; command.
|
Redis database | Log on to your Redis database and open the redis.conf file. Run the following command to change the current password or configure a password: requirepass <NewPassword>
If a logon password is configured, the logon password is changed after you run the command. If no logon password is configured, configure a password after you run the command. Restart the Redis service.
|
SQL Server database | Linux operating system Log on to your SQL Server database and run the following command to change the logon password: EXEC sp_password @old=N'<OldPassword>', @new=N'<NewPassword>', @loginame=N'<UserName>';
Windows operating system Log on to your SQL Server database client, choose , find the required username, and then change the weak password to a complex password.
|
MongoDB database | Log on to your MongoDB database. Run the use admin command to switch to user admin. Run the db.changeUserPassword("<UserName>", "<NewPassword>") command to change the logon username and password of the database. We recommend that you configure a complex password that is greater than 12 characters in length and contains digits, uppercase letters, lowercase letters, and special characters. Enable the identity authentication feature. Open the mongod.conf file of the MongoDB database, set the security.authorization configuration item to enabled or the auth configuration item to true. Run the systemctl restart mongod command to restart the MongoDB service.
|
PostgreSQL database | Log on to your PostgreSQL database. Run the following command to change the weak password: ALTER USER <UserName> WITH PASSWORD <NewPassword>;
|
Tomcat | Go to the root directory of your Tomcat server and open the conf/tomcat-user.xml file. Change the password attribute value of the user node to a complex password.
|
Rsync | Open the rsyncd.conf file of your rsync server. Find the secrets file configuration item and obtain the path to the rsyncd.secret file in the configuration item. Edit the rsyncd.secret file in the <UserName>:<NewPassword> format, and change the password of the logon user to a complex password. Restart the rsync service.
|
SVN | Open the directory of the Subversion (SVN) repository. Find password-db in the <path>/conf/svnserve.conf file. Locate the path to the password configuration file based on the configuration of password-db and change the password in the password configuration file to a specified password. By default, the password configuration file is named passwd. Restart the SVN service.
|
vsftpd | Local user Open the vsftpd.conf file. Add the anonymous_enable configuration item and set the configuration item to NO. If the configuration item already exists, change the value of the configuration item to NO. This denies anonymous logons. Run the passwd <UserName> command to change the password of the user who uses the FTP service. Configure a complex password that meets the requirements as prompted.
Virtual user Open the /etc/vsftpd/login.txt file. Change the passwords of users and save the new passwords. In the file, line 1 contains the username of user A, line 2 contains the password of user A, line 3 contains the username of user B, line 4 contains the password of user B, and so on. Run the db_load -T -t hash -f /etc/vsftpd/login.txt /etc/vsftpd/login.db command. Edit the /etc/pam.d/vsftpd file. Append the db=/etc/vsftpd/login parameter to the lines that contain auth pam_userdb.so and account pam_userdb.so. Then, save the modification. The following figure shows an example.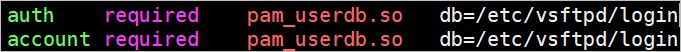 Restart the vsftpd service.
|
FTP | Log on to your Linux server as the root user. Run the following command: passwd <UserName>
Enter a new password as prompted. If the all authentication tokens updated successfully message appears, the password is changed.
|
InfluxDB database | Log on to your InfluxDB database. Run the following command to change the password of the account that is used to log on to the database: Replace NewPassword with the new password. The new password must be enclosed in single quotation marks ('). set password for "<UserName>" = "<NewPassword>"
|
JBoss 6 and JBoss 7 | JBoss 6 Find the /conf/props/jmx-console-users.properties file and change the password in the file. The new password must be in the <UserName> =<Password> format. Restart the JBoss6 service. Run the ps -ef|grep jboss command to view the current process of JBoss6. Run the kill -9 process ID command to terminate the process. Replace process ID with the process ID of JBoss 6. Run the following command to start the JBoss service: Replace jboss6_path with the installation directory of JBoss 6. jboss6_path/bin/run.sh
JBoss 7 Find the /configuration/mgmt-users.properties file and delete the usernames whose passwords are weak. Run the bin/adduser.sh script in the installation directory of JBoss. Then, add new users for which you configure complex passwords as prompted.
|
Jenkins | Log on to the Jenkins console. Click Configure to go to the Configure page. Enter a new password in the Password field.
|
OpenLDAP | Run the following command to query the value and position of the password of the OpenLDAP administrator: ldapsearch -H ldapi:// -LLL -Q -Y EXTERNAL -b "cn=config" "(olcRootDN=*)" dn olcRootDN olcRootPW
Run the following command to generate a password: slappasswd -s <NewPassword>
After you run the command, the hash value of the new password is returned. Create a file named newpassword.ldif and add the following content to the file: dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcRootPW
olcRootPW: NewHash
The content of the line that contains dn is the value of dn returned by the command that is run in Step 1, and the value of NewHash is the hash value of the new password. Run the following command to import the created .ldif file: ldapmodify -H ldapi:// -Y EXTERNAL -f newpassword.ldif
|
Linux OpenVPN | Perform the following steps to edit the pwd-file file and change the password of OpenVPN: Find the pwd-file file. In most cases, the file is stored in the /etc/openvpn directory. Append the following statement to the file to cancel the client certificate authentication: client-cert-not-required
Append the following statement to the file to enable the user password script: auth-user-pass-verify /etc/openvpn/checkpsw.sh via-env
Append the following statement to the file to block the alerts that are generated by the system: script-security 3
Edit the /etc/openvpn/psw-file file. Each row represents an account. Separate a username and its password with spaces. Examples: cat /etc/openvpn/psw-file
abcdocker <NewPassWord>
abc <NewPassWord>
test <NewPassWord>
Run the following command to obtain the checkpsw.sh script: wget http://openvpn.se/files/other/checkpsw.sh
Note By default, the checkpsw.sh script reads usernames and passwords from the /etc/openvpn/psw-file file.
|
Oracle database | Log on to your Oracle database. Run the following command to change the password: alter user <UserName> identified by <NewPassWord>;
|
pptpd | Edit the /etc/ppp/chap-secrets file. Specify the username and password in the <UserName> pptpd <NewPassword> format. Separate UserName, pptpd, and NewPassword with tabs. Restart the pptpd service.
|
Proftpd | Run the following command and enter a new password as prompted: File_Path specifies the file path of the virtual user that is involved.
ftpasswd --passwd --name=<UserName> --change-password --file=File_Path
|
RabbitMQ | Run the following command to change the weak password: rabbitmqctl change_password <UserName> '<NewPassword>'
|
VncServer | Disable VNC Server and go to the installation directory of VNC Server on the server where VNC Server is installed. If the weak password does not belong to the root user, log on or switch to the user to which the weak password belongs after you go to the installation directory. For example, if the user whose password you want to change is aliuser, run the su - aliuser command. Delete the passwd file from the installation directory. Example: /home/aliuser/.vnc/passwd. Run the vncpasswd command to reset the password.
Important For a VNC Server password, the system checks only the first eight characters of the password. For example, if you set the new password to Aliyunpasswd, only the first eight characters Aliyunpa take effect. If the new password does not meet the complexity requirements, the new password has a high risk of being cracked. Make sure that the new password meets the complexity requirements.
|
Weblogic 12c | Log on to the WebLogic console. In the left-side navigation pane, choose . Select the user whose password you want to change. On the Passwords tab, enter and confirm the new password, and click Save. If Activate Changes is displayed in the Change Center section in the upper-left corner of the WebLogic console, click Activate Changes. Log on to your server and change the value of the password field for the selected user in the `%DOMAIN_HOME%/servers/AdminServer/security/boot.properties file. The new password must be the same as the password that you enter in the WebLogic console. After you change the password, AES encryption is automatically enabled. Run the %DOMAIN_HOME%/bin/stopWeblogic.sh command to securely stop WebLogic. Then, restart WebLogic.
Note The new password takes affect only after you restart WebLogic. If you cannot modify the configurations, find the Change Center section in the upper-left corner of the WebLogic console and click Lock & Edit. WebLogic must be securely stopped. Otherwise, WebLogic may fail to start.
|
Activemq | Go to the activemq_/pathconf/ directory and find the configuration file. activemq_path specifies the installation path of the application. Run the vim jetty-realm.properties command to edit the configuration file. Add or modify a user. Change the username and password to a value in the <UserName>: <NewPassword>,RoleName format. RoleName specifies the role name. Example: admin: passwd123!@#, admin. After the modification is complete, save the modification and exit. Then, restart the ActiveMQ service.
|
Elasticsearch |
Note Install the X-Pack plug-in by using the security policies of Elasticsearch. The X-Pack plug-in is built in Elasticsearch V7.X or later. If you use Elasticsearch of a version that is earlier than V7.X, you must enable the configuration of the X-Pack plug-in. In the elasticsearch.yml file, change the value of xpack.security.enabled to true. Run the following command to change the password of a user: ES_HOME_PATH specifies the installation path of Elasticsearch and passwd specifies the new password.
ES_HOME_PATH/bin/elasticsearch-users passwd <UserName>
|
Samba | Run the smbpasswd <UserName> command to change the password of a user. Enter a new password as prompted.
|
Zabbix | Log on to the Zabbix web interface by using the administrator account. In the top navigation bar, choose to view users. Click the username whose password you want to change and click Change password. Enter a new password and click Update.
|
