This topic describes the concepts and capabilities that are related to Serverless App Engine (SAE) networks.
Concepts and capabilities
Alibaba Cloud network infrastructure
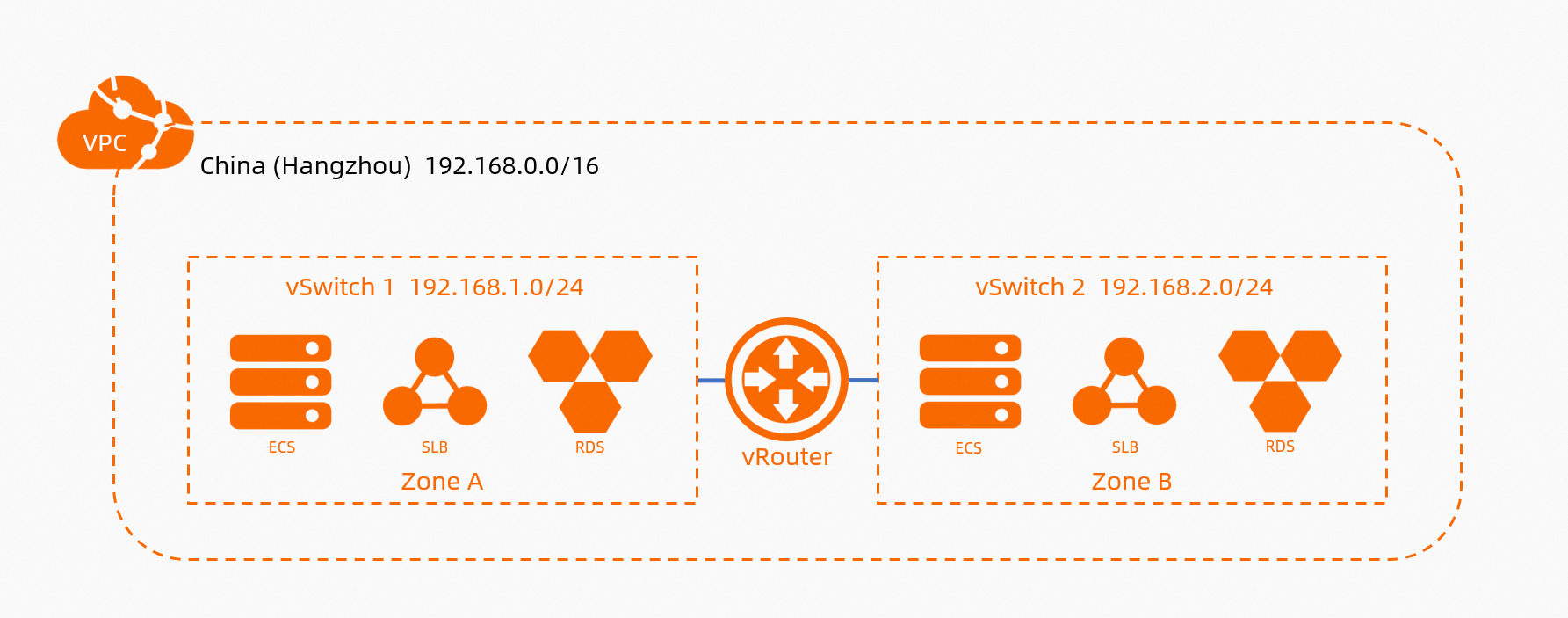
Virtual private cloud (VPC): A VPC is a private network on Alibaba Cloud. VPCs are logically isolated from each other.
NoteBy default, access from VPCs to the Internet is denied.
vSwitch: A vSwitch is a basic network component that connects different cloud resources in a VPC. A vSwitch corresponds to a physical server. When you create a cloud resource in a VPC, you must specify a vSwitch to which the cloud resource is connected.
Elastic IP address (EIP): You can associate an EIP with only one resource, such as an Elastic Compute Service (ECS) instance or an SAE instance. Then, the associated resource can access and be accessed by other services over the Internet.
NAT gateway: The source network address translation (SNAT) feature of a NAT gateway allows all resources in a VPC to access the Internet. An Internet NAT gateway is suitable for all resources in a VPC, whereas an EIP is suitable for only one resource in a VPC.
Scenarios and methods of SAE network access
After you deploy an application on SAE, you may have various network access requirements. The following figure shows the network access scenarios. 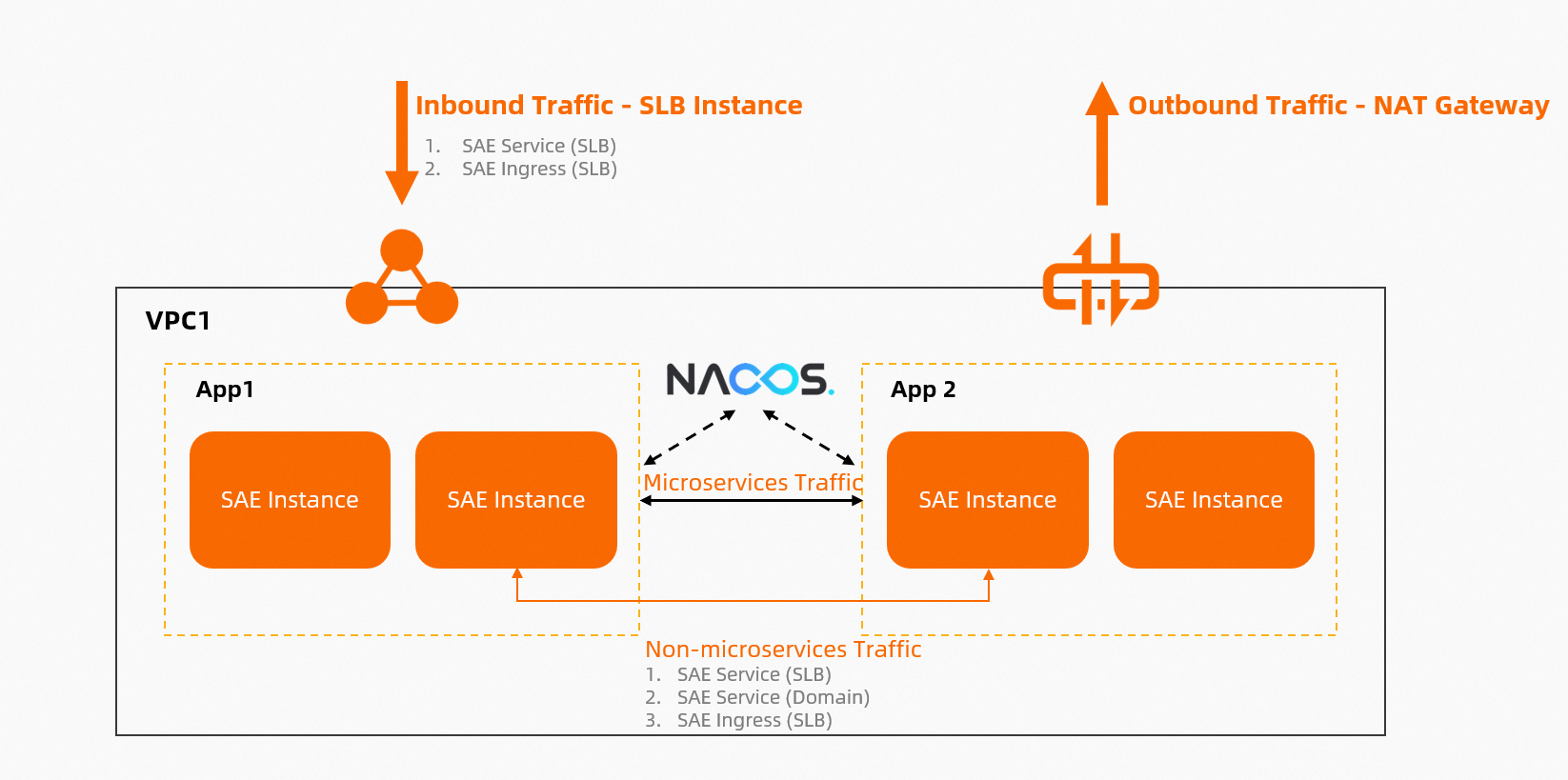
Mutual access between SAE applications over an internal network (non-microservices scenarios)
In serverless mode, new internal IP addresses are generated each time you deploy an application. However, you cannot access the application by using the IP addresses of the instances in the application. You can use one of the following methods to enable access:
SAE Service (CLB): You can configure SAE service access based on internal-facing Classic Load Balancer (CLB) instances. For more information, see Configure application access based on CLB instances.
SAE ServiceName: You can configure SAE application access based on Kubernetes Service names. Each SAE application has a domain name that can be accessed in the SAE environment. For more information, see Configure application access based on Kubernetes Service names.
SAE Ingress (ALB/CLB): You can configure gateway routing for application access based on internal-facing Application Load Balancer (ALB) and internal-facing CLB instances. Then, you can access different SAE applications by using different domain names and paths. For more information, see Configure gateway routing for application access based on ALB and CLB instances.
Access to SAE applications from the Internet (inbound traffic)
You can use one of the following methods to enable access:
SAE Service (CLB): You can configure SAE service access based on Internet-facing CLB instances. For more information, see Configure application access based on CLB instances.
SAE Ingress (ALB/CLB): You can configure gateway routing for application access based on Internet-facing ALB and Internet-facing CLB instances. Then, you can access different SAE applications by using different domain names and paths. For more information, see Configure gateway routing for application access based on ALB and CLB instances.
SAE EIP: If you associate each instance of an SAE application with an EIP, the instances can access and be accessed by other services over the Internet. For more information, see Enable Internet access for SAE instances based on EIPs.
Access to the Internet from SAE applications (outbound traffic)
You can use one of the following methods to enable access:
NAT gateway: If you configure a NAT gateway for the VPC or vSwitch that is associated with an SAE application, the SAE applications that use the same VPC or vSwitch can access the Internet. For more information, see Configure a NAT gateway for an SAE application to enable Internet access.
SAE EIP: If you associate each instance of an SAE application with an EIP, the instances can access and be accessed by other services over the Internet. For more information, see Enable Internet access for SAE instances based on EIPs.
Access to ECS instances, ApsaraDB RDS databases, and ApsaraDB for Redis databases from SAE applications in a VPC
SAE integrates with Alibaba Cloud VPCs. An SAE application can access resources in the VPC where the application resides without other configurations. For example, an SAE application in a VPC can access ECS instances, ApsaraDB RDS databases, and ApsaraDB for Redis databases that reside in the VPC.
You must check whether the related security groups and service whitelists are configured. If an issue occurs, perform the steps that are described in FAQ.
Access to registries from microservices applications and mutual access between instances
For more information, see Concepts and capabilities related to SAE microservices.
Comparison items in SAE networks
Differences between ServiceName and gateway routing in SAE
The gateway routing feature of SAE is implemented based on ALB and CLB instances that belong to the Server Load Balancer (SLB) family. This feature allows you to access different applications by using domain names and paths, as shown in the following figure. The ServiceName method does not provide this capability. We recommend that you use the gateway routing feature if your business requirements can be met. If you require access over Layer 4 TCP or you cannot access an application by using a domain name, you can use the ServiceName method. 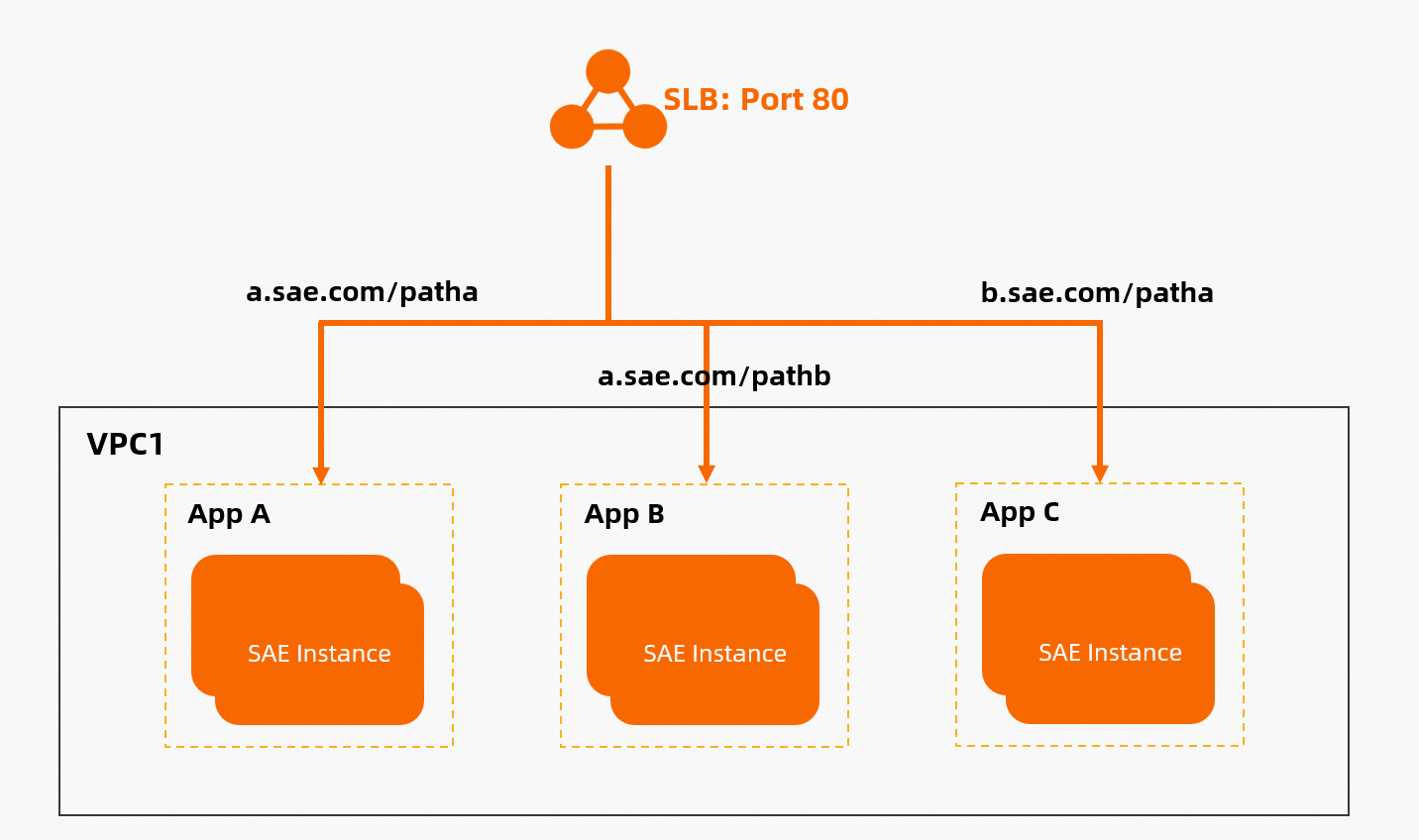
For more information, see the following topics:
Differences between CLB-based application access and Kubernetes Service name-based application access
Kubernetes Services are classified into the following types: CLB-based Services and ClusterIP-based Services. SAE provides an accessible domain name for each application instead of specific ClusterIPs. The following table describes the differences between the Service types.
Item | CLB | Domain (ClusterIP) |
Fee | Free of charge | |
O&M | CLB is an independent Alibaba Cloud service that provides multiple features: monitoring, alerting, and log collection to Log Service. CLB provides fine-grained troubleshooting capabilities. | This type of Service do not provide independent monitoring, alerting, or access log collection capabilities. You need to configure alerts and logs for an application. |
Differences between ALB-based gateway routing and CLB-based gateway routing
ALB is a load balancing service that runs at the application layer, and supports protocols such as HTTP, HTTPS, and QUIC. We recommend that you use an ALB instance in gateway routing scenarios. For more information, see SLB overview.
Differences between NAT-based Internet access and EIP-based Internet access
The following figure shows how to enable EIP-based Internet access. Each instance is associated with an EIP. If the quota of EIPs in the current Alibaba Cloud account is insufficient, EIPs fail to be created. In this case, the instances with which no EPIs are associated cannot access or be accessed by other services over the Internet. 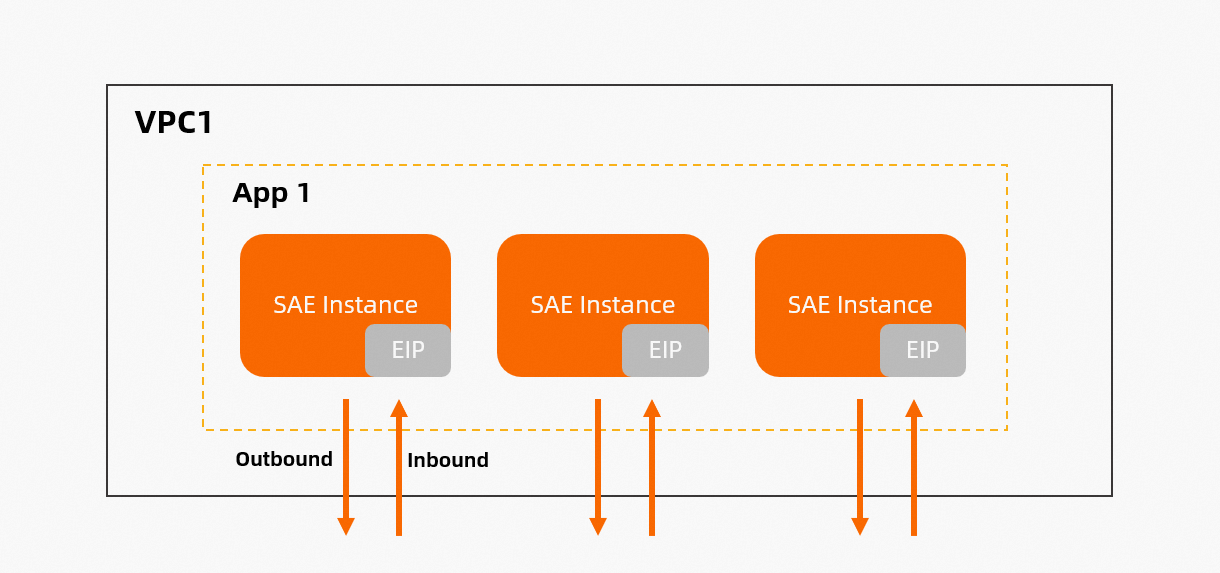
The following table shows the differences between NAT-based Internet access and EIP-based Internet access.
Item | NAT | EIP |
Effective scope | The effective scope of a NAT gateway is a VPC or a vSwitch. An Internet NAT gateway allows all instances that are deployed in a VPC or vSwitch to access the Internet even when no public IP addresses are associated with the instances. Only one NAT gateway is required in a VPC or vSwitch. Then, all instances that reside in the VPC can access the Internet. | The effective scope of an EIP is an instance. If you have 10 instances, you must configure 10 EIPs for the instances. After you associate an EIP with an instance, the instance can access and be accessed by other services over the Internet. |
Fixed public IP address | Yes. | No. SAE releases original instances and disassociates EIPs from the original instances only if new instances are associated with EIPs. In this case, you must prepare additional EIPs for the new instances. An EIP is a pool of IP addresses. |
Scenario | NAT-based Internet access is suitable for scenarios in which auto scaling policies are configured for applications, and new instances require access to the Internet by default and require fixed IP addresses. This method can meet the business requirements of 95% SAE users. | EIP-based Internet access is suitable for scenarios in which EIPs are changeable, instances need to be directly connected (such as online conferences), and the lifecycle of each instance need to be managed in a fine-grained manner. |
Fee | For more information, see Billing of Internet NAT gateways. | For more information, see EIP billing. If the number of instances is less than or equal to 20, the EIP-based Internet access method is more cost-efficient. |
FAQ
How can an SAE application access the Internet?
SAE supports the following types of Internet access: outbound access and inbound access, as shown in the following figure. For information about outbound access over the Internet, see the methods that are described in this section. For information about inbound access over the Internet, see How can an SAE application be accessed over the Internet?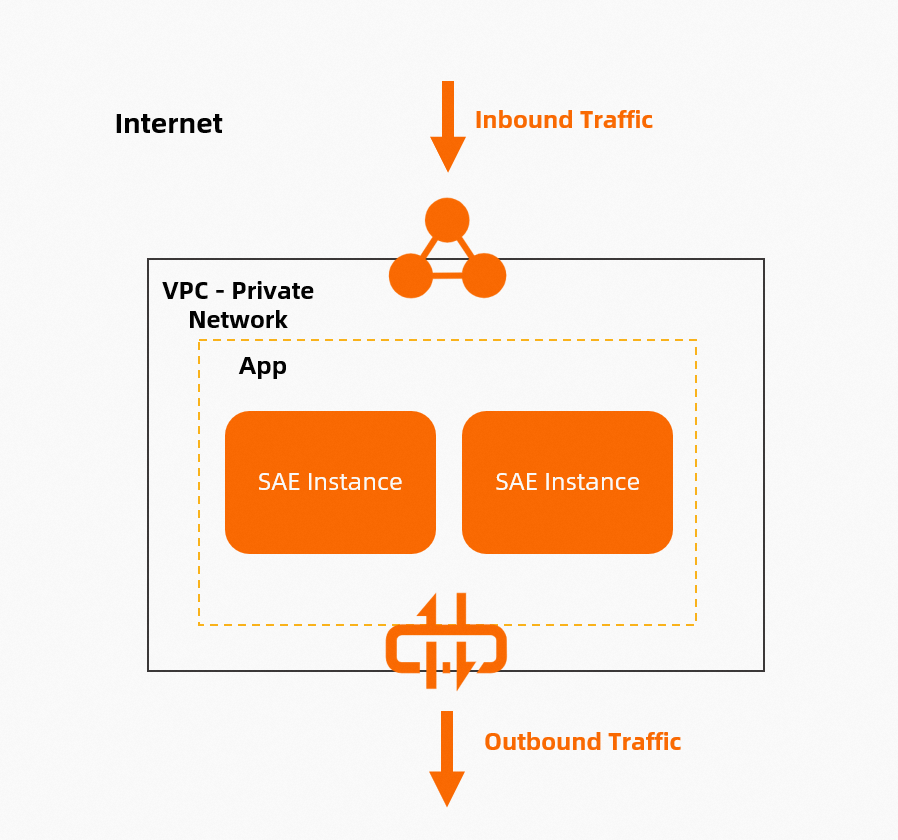
SAE allows you to enable Internet access for an application by using one of the following methods: Configure a NAT gateway for an SAE application to enable Internet access and Enable Internet access for SAE instances based on EIPs. We recommend you enable Internet access for an application by using a NAT gateway. For information about the differences between the preceding methods, see Differences between NAT-based Internet access and EIP-based Internet access.
How can an SAE application be accessed over the Internet?
SAE supports the following types of Internet access: outbound access and inbound access, as shown in the following figure. For information about inbound access over the Internet, see the methods that are described in this section. For information about outbound access over the Internet, see How can an SAE application access the Internet?
We recommend that you enable Internet access for applications by configuring gateway routing based on ALB and CLB instances. If the gateway routing method cannot meet your requirements, see Configure application access based on CLB instances or Enable Internet access for SAE instances based on EIPs. The following table describes the differences between the preceding methods.
Item | Gateway routing (ALB or CLB) | Service (CLB) | EIP |
Routing | Supported. You can route traffic to different applications by | Not supported. Only one application of the specified port can be accessed. | Not supported. In most cases, you need to obtain the EIP list and manage the access policy. |
Layer 7 protocols | Supported. | Supported. | Supported. |
Layer 4 protocols | Not supported. | Supported. | Supported. |
Features such as cross-region and rewrite | Supported. | Not supported. You can implement the features based on your business requirements. | Not supported. You can implement the features based on your business requirements. |
Fixed IP address | Yes. | Yes. | No. |
Fee |
How do I bind a public domain name to an SAE application?
SAE does not provide features that are related to domain names. To bind a domain name to an SAE application, perform the following operations: Configure an ALB instance or CLB instance for the SAE application, obtain the related public IP address or domain name, and then bind the IP address or domain name to the SAE application in the Alibaba Cloud DNS console.
What do I do if an SAE application cannot access an ECS instance?
To troubleshoot the issue, perform the following steps:
Check whether the SAE application and the ECS instance reside in the same VPC, and check whether the related ports are configured in the corresponding security group.
Run the ping <Service address> command or telnet <Service address> command in a container to check the connectivity. If the preceding commands are not available, install common commands.
For information about how to access a public ECS endpoint, see How can an SAE application access the Internet?
What do I do if an SAE application cannot access an ApsaraDB RDS instance or ApsaraDB for Redis instance?
Check whether the endpoint of the ApsaraDB RDS instance or ApsaraDB for Redis instance is a public endpoint or an internal endpoint. The SAE application accesses the ApsaraDB RDS instance or ApsaraDB for Redis instance by using the corresponding endpoint. The network quality and latency of an internal endpoint are better than that of a public endpoint. If the SAE application resides in the same VPC as the ApsaraDB RDS instance or ApsaraDB for Redis instance, we recommend that you use the internal endpoint of the ApsaraDB RDS instance or ApsaraDB for Redis instance. Network fees vary based on the types of resources that you create. For more information, see Billing. If the SAE application resides in a different VPC as the ApsaraDB RDS instance or ApsaraDB for Redis instance, we recommend that you use a Cloud Enterprise Network (CEN) instance to connect the VPCs, and then use the internal endpoint of the ApsaraDB RDS instance or ApsaraDB for Redis instance. Then, perform the following steps to troubleshoot the issue:
Check whether a whitelist is configured.
NoteTo enable internal access, you must add the CIDR blocks of the VPC and vSwitch of the SAE application to a whitelist. To enable Internet access, you must add the EIP of the SAE application to the whitelist.
If no whitelist is configured, configure a whitelist based on the steps that are described in the following topics:
Run the ping <Service address> or telnet <Service address> command in a container. If the preceding commands are not available, install common commands.
If the output of the ping or telnet command indicates normal, you can install a MySQL client or Redis client to test whether the ApsaraDB RDS instance or ApsaraDB for Redis instance can be connected. For more information, see Use a database client to connect to an RDS instance or Use a client to connect to an ApsaraDB for Redis instance. If the instance can be connected, the SAE network environment is normal. In this case, you must check the configurations of your program.