You can add tags to Elastic Compute Service (ECS) instances, specify tags in custom Resource Access Management (RAM) policies, and attach the policies to RAM users based on your business requirements. This way, the RAM users can view and manage only authorized ECS instances.
Background information
You can use tags to manage the resource access and operation permissions of RAM users. This indicates that you can implement RAM user authentication based on tags. The following figure shows how to implement the authentication.

You can specify tags in the Condition element of a custom policy. Tags support the following condition keys:
acs:RequestTag/<tag-key>: the tag that is passed in a request. This condition key indicates that you must specify the tag in the request when you call an API operation.acs:ResourceTag/<tag-key>: the tag that is added to the requested resource. This condition key indicates that the tag must be added to the resource on which you perform an operation.
Procedure
This section describes how to enable the RAM user Alice to view and manage only the ECS instances to which the owner:alice and environment:production tags are added.
During the authorization process, the ECS instances can work as expected.
Perform the following steps by using an account administrator:
Log on to the RAM console and create a RAM user named Alice.
For more information, see Create a RAM user.
Add tags to ECS instances.
In this example, the
owner:aliceandenvironment:productiontags are added to ECS instances.You can use one of the following methods to add tags:
Add tags to ECS instances on the Tags page of the Resource Management console. For more information, see Add a custom tag.
Add tags to ECS instances in the ECS console. For more information, see Create or add a tag.
Create a custom policy named UseTagAccessRes in the RAM console.
The following code provides the document of the policy. For more information, see Create a custom policy.
{ "Version": "1", "Statement": [ { "Effect": "Allow", "Action": "ecs:*", "Resource": "*", "Condition": { "StringEquals": { "acs:ResourceTag/owner": [ "alice" ], "acs:ResourceTag/environment": [ "production" ] } } }, { "Effect": "Allow", "Action": "ecs:*", "Resource": "*", "Condition": { "StringEquals": { "acs:RequestTag/owner": [ "alice" ], "acs:RequestTag/environment": [ "production" ] } } }, { "Effect": "Allow", "Action": [ "ecs:List*", "ecs:DescribeInstanceStatus", "ecs:DescribeInstanceVncUrl", "ecs:DescribeInstanceAutoRenewAttribute", "ecs:DescribeInstanceRamRole", "ecs:DescribeInstanceTypeFamilies", "ecs:DescribeInstanceTypes", "ecs:DescribeInstanceAttachmentAttributes", "ecs:DescribeInstancesFullStatus", "ecs:DescribeInstanceHistoryEvents", "ecs:DescribeInstanceMonitorData", "ecs:DescribeInstanceMaintenanceAttributes", "ecs:DescribeInstanceModificationPrice", "ecs:DescribeA*", "ecs:DescribeC*", "ecs:DescribeD*", "ecs:DescribeE*", "ecs:DescribeH*", "ecs:DescribeIm*", "ecs:DescribeInv*", "ecs:DescribeK*", "ecs:DescribeL*", "ecs:DescribeM*", "ecs:DescribeN*", "ecs:DescribeP*", "ecs:DescribeR*", "ecs:DescribeS*", "ecs:DescribeT*", "ecs:DescribeZ*", "vpc:DescribeVpcs", "vpc:DescribeVSwitches" ], "Resource": "*" }, { "Effect": "Deny", "Action": [ "ecs:DeleteTags", "ecs:UntagResources", "ecs:CreateTags", "ecs:TagResources" ], "Resource": "*" } ] }The following table describes the configurations in the policy.
Configuration
Description
{ "Effect": "Allow", "Action": "ecs:*", "Resource": "*", "Condition": { "StringEquals": { "acs:RequestTag/owner": "alice", "acs:RequestTag/environment": "production" } } }Allows the filtering of ECS instances based on the
owner:aliceandenvironment:productiontags.{ "Effect": "Allow", "Action": "ecs:*", "Resource": "*", "Condition": { "StringEquals": { "acs:ResourceTag/owner": [ "alice" ], "acs:ResourceTag/environment": [ "production" ] } } }Allows management operations on ECS instances to which the
owner:aliceandenvironment:productiontags are added.{ "Effect": "Allow", "Action": [ "ecs:List*", "ecs:DescribeInstanceStatus", "ecs:DescribeInstanceVncUrl", "ecs:DescribeInstanceAutoRenewAttribute", "ecs:DescribeInstanceRamRole", "ecs:DescribeInstanceTypeFamilies", "ecs:DescribeInstanceTypes", "ecs:DescribeInstanceAttachmentAttributes", "ecs:DescribeInstancesFullStatus", "ecs:DescribeInstanceHistoryEvents", "ecs:DescribeInstanceMonitorData", "ecs:DescribeInstanceMaintenanceAttributes", "ecs:DescribeInstanceModificationPrice", "ecs:DescribeA*", "ecs:DescribeC*", "ecs:DescribeD*", "ecs:DescribeE*", "ecs:DescribeH*", "ecs:DescribeIm*", "ecs:DescribeInv*", "ecs:DescribeK*", "ecs:DescribeL*", "ecs:DescribeM*", "ecs:DescribeN*", "ecs:DescribeP*", "ecs:DescribeR*", "ecs:DescribeS*", "ecs:DescribeT*", "ecs:DescribeZ*", "vpc:DescribeVpcs", "vpc:DescribeVSwitches" ], "Resource": "*" }Allows the viewing of information about the ECS instances.
{ "Effect": "Deny", "Action": [ "ecs:DeleteTags", "ecs:UntagResources", "ecs:CreateTags", "ecs:TagResources" ], "Resource": "*" }Denies the operations of creating, adding, deleting, and removing tags.
This prevents the RAM user to which this policy is attached from modifying the tags. If the RAM user modifies the tags on an ECS instance, the RAM user no longer has the related permissions on the ECS instance.
Attach the created policy to the RAM user Alice in the RAM console.
Select Alibaba Cloud Account for Authorized Scope, the RAM user Alice for Principal, and the custom policy UseTagAccessRes for Select Policy. For more information, see Grant permissions to RAM users.
Verify the result
Log on to the ECS console as the RAM user Alice.
For more information, see Log on to the Alibaba Cloud Management Console as a RAM user.
In the left-side navigation pane, choose .
In the top navigation bar, select the region in which the ECS instances reside.
On the Instances page, click Filter by Tag on the right side of the search box, and select the
owner:aliceandenvironment:productiontags.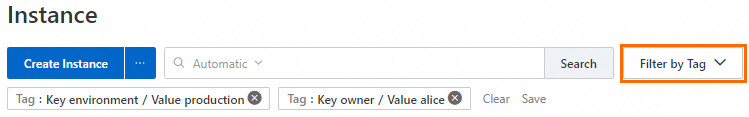 Important
ImportantThe RAM user can view the ECS instances to which the tags are added only after the RAM user selects the tags. If no tag is selected, the RAM user cannot view any ECS instances.
View and manage only ECS instances to which the
owner:aliceandenvironment:productiontags are added.
References
For information about RAM authentication rules for ECS, see Authentication rules.