How it works
RAM Role A within Account 123456 assumes RAM Role B within Account 654321 to manage the resources within Account 654321.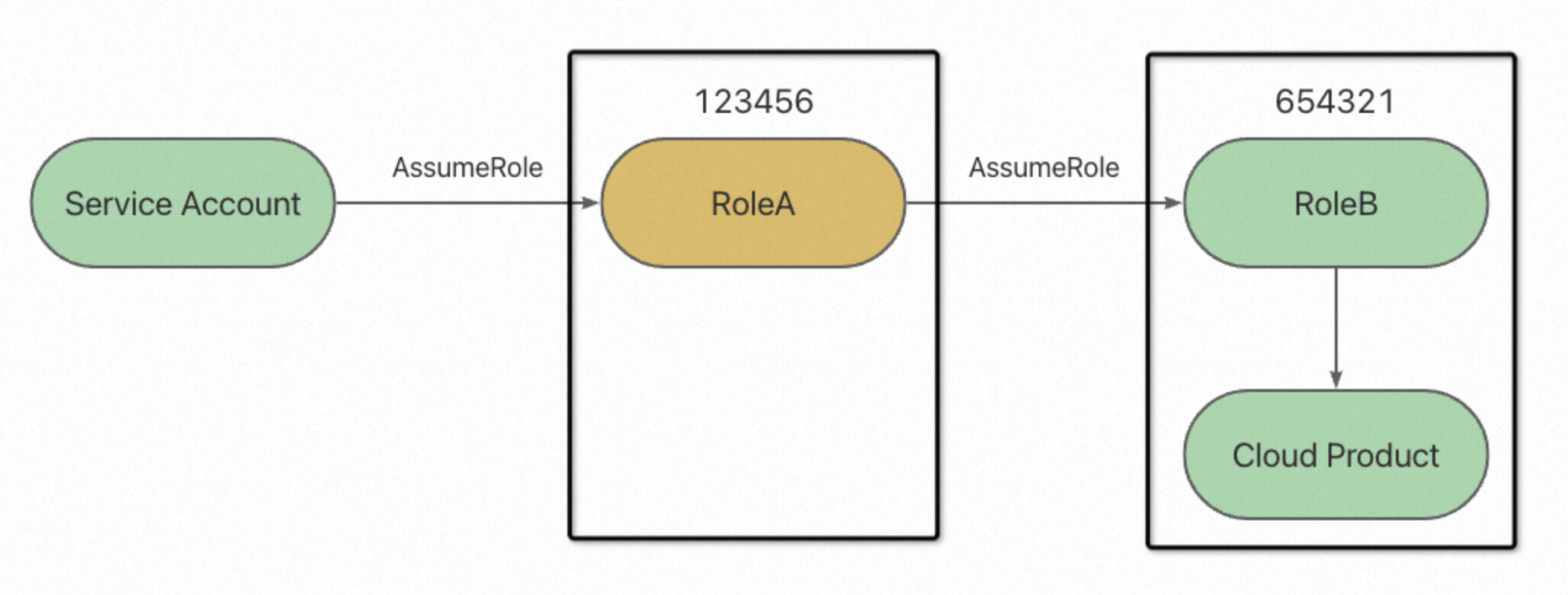
Preparations
Create RAM roles
Create RAM roles named OOSServiceRole within Account 123456 and Account 654321. For more information, see Use RAM to grant permissions to OOS.
Modify the trust policy of the RAM roles
Trust policy for the OOSServiceRole role within Account 654321:
{
"Statement": [
{
"Action": "sts:AssumeRole",
"Effect": "Allow",
"Principal": {
"RAM": [
"acs:ram::123456:root"
]
}
}
],
"Version": "1"
}Trust policy for the OOSServiceRole role within Account 123456:
{
"Statement": [
{
"Action": "sts:AssumeRole",
"Effect": "Allow",
"Principal": {
"Service": [
"oos.aliyuncs.com"
]
}
}
],
"Version": "1"
}Grant permissions to the RAM roles
1. Grant the AliyunSTSAssumeRoleAccess permission to the OOSServiceRole role within Account 123456.
2. Grant the required permissions to the OOSServiceRole role within Account 654321. In this example, the AliyunECSFullAccess permission is granted to the OOSServiceRole role within Account 654321.
Procedure
1. Log on to the Operation Orchestration Service (OSS) console.
2. In the left-side navigation pane, click My Templates to go to the My Templates page. In the upper-left corner, click Create Template. Use the template code in the Appendix to create a template for running commands across accounts and regions.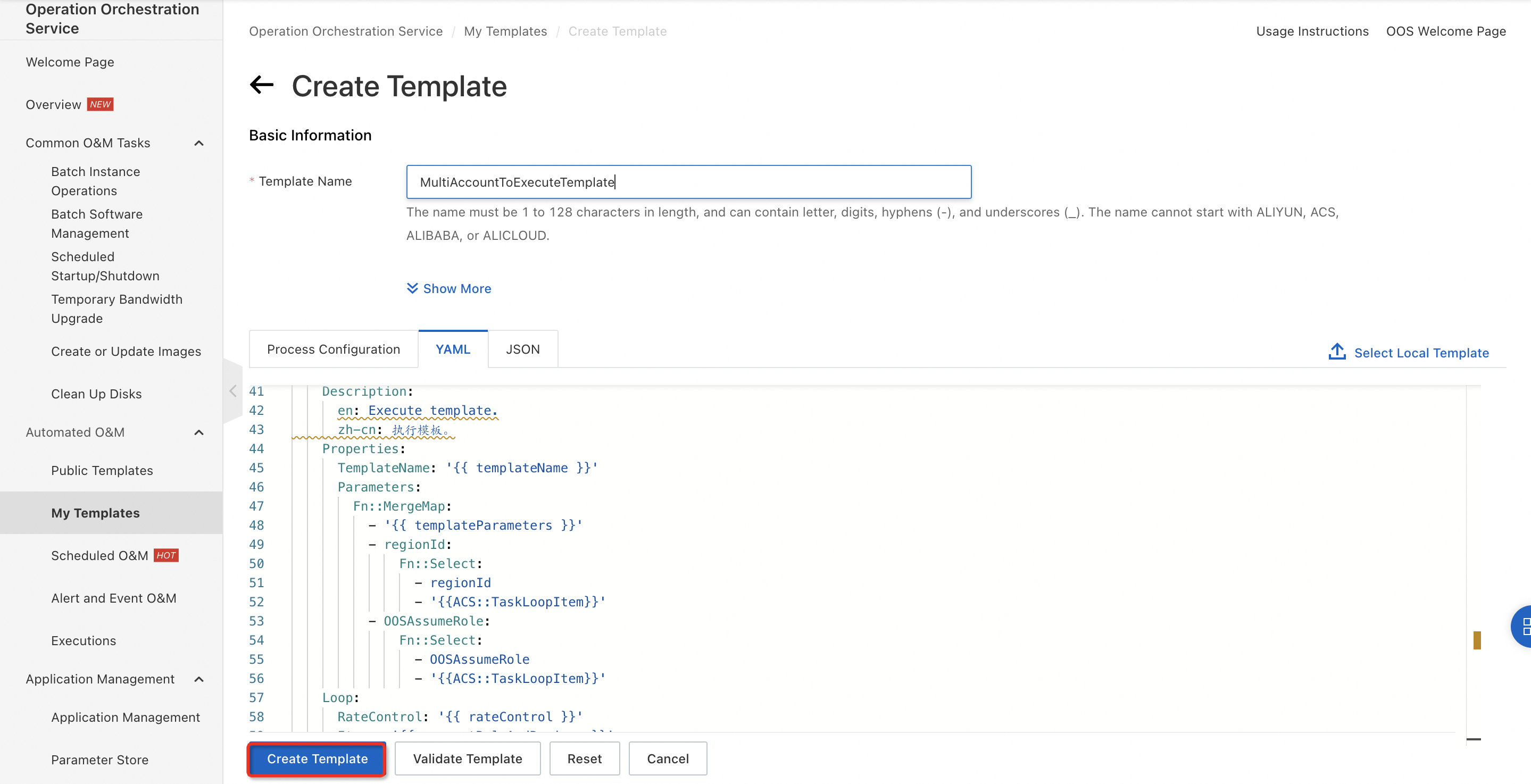
3. In the left-side navigation pane, click Executions to go to the Executions page. In the upper-left corner, click Create to create an execution.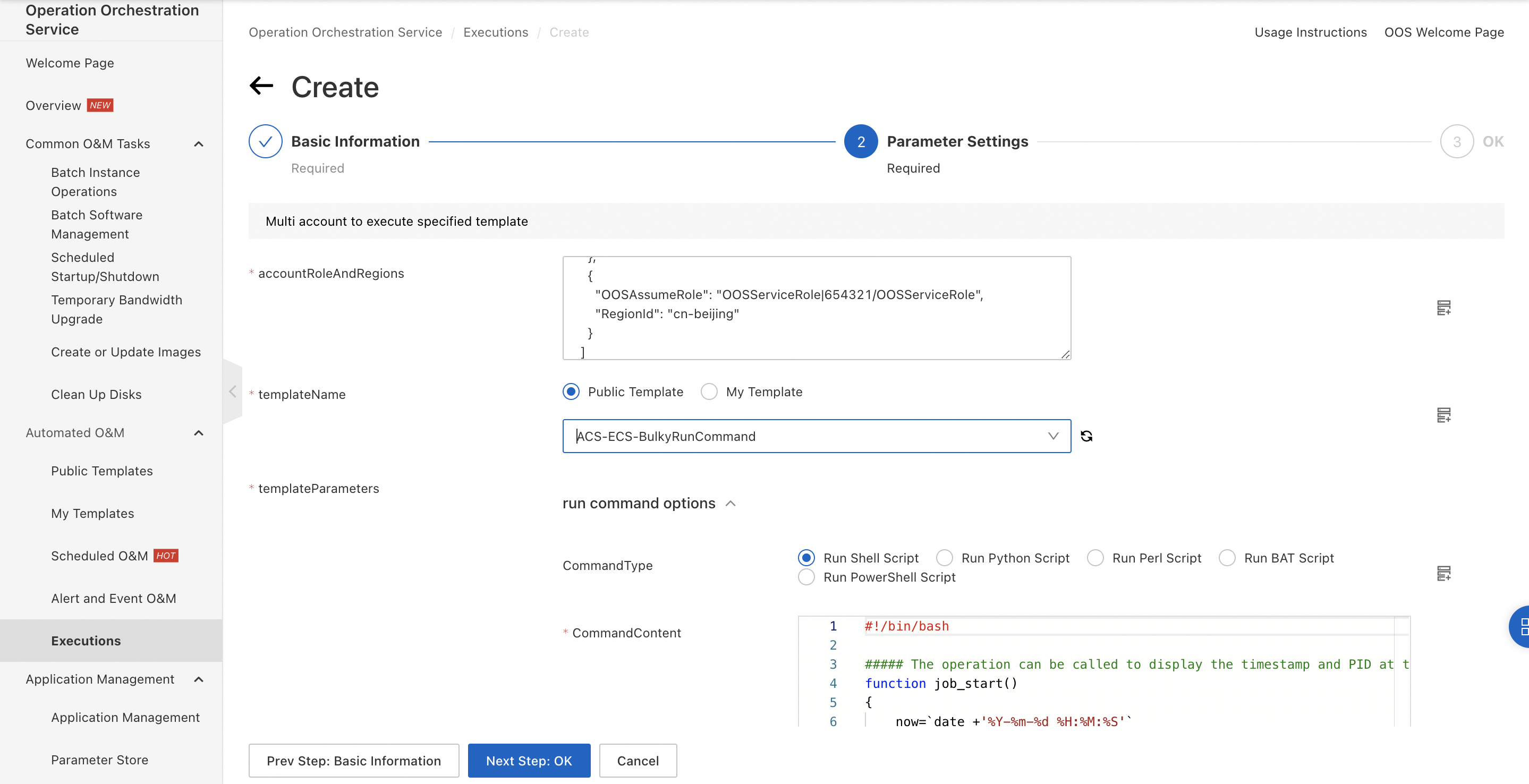
The following part describes the configurations of some parameters in the Basic Information step of the Create page:
accountRoleAndRegions:
Enter the following code in the accountRoleAndRegions field to allow the execution of commands on running ECS instances in the China (Shanghai) and China (Bejing) regions within Account 654321:
[
{
"OOSAssumeRole": "OOSServiceRole|654321/OOSServiceRole",
"RegionId": "cn-shanghai"
},
{
"OOSAssumeRole": "OOSServiceRole|654321/OOSServiceRole",
"RegionId": "cn-beijing"
}
]templateParameters:
targets: Select running instances in the specified region within the specified account.
{
"commandType": "RunShellScript",
"commandContent": "echo hello",
"workingDir": "",
"windowsPasswordName": "",
"rateControl": {
"MaxErrors": 0,
"Concurrency": 10,
"Mode": "Concurrency"
},
"enableParameter": false,
"targets": {
"Type": "All",
"Parameters": {
"Status": "Running",
"RegionId": "{{regionId}}"
},
"RegionId": "{{regionId}}"
},
"timeout": 600,
"username": ""
}Appendix
Template code for running commands across accounts and regions
FormatVersion: OOS-2019-06-01
Description:
en: Multi account to execute specified template
zh-cn: description in Chinese
name-en: MultiAccountToExecuteTemplate
name-zh-cn: name in Chinese
Parameters:
accountRoleAndRegions:
Type: Json
templateName:
Type: String
AssociationProperty: TemplateName
templateParameters:
Description:
en: Template parameters to execute with.
zh-cn: description in Chinese
Type: Json
AssociationProperty: TemplateParameter
AssociationPropertyMetadata:
TemplateName: $templateName
rateControl:
Description:
en: Concurrency ratio of task execution.
zh-cn: description in Chinese
Type: Json
AssociationProperty: RateControl
Default:
Mode: Concurrency
MaxErrors: 0
Concurrency: 10
OOSAssumeRole:
Description:
en: The RAM role to be assumed by OOS.
zh-cn: description in Chinese
Type: String
Default: OOSServiceRole
RamRole: '{{ OOSAssumeRole }}'
Tasks:
- Name: executeTemplate
Action: 'ACS::Template'
Description:
en: Execute template.
zh-cn: description in Chinese
Properties:
TemplateName: '{{ templateName }}'
Parameters:
'Fn::MergeMap':
- '{{ templateParameters }}'
- regionId:
'Fn::Select':
- RegionId
- '{{ACS::TaskLoopItem}}'
- OOSAssumeRole:
'Fn::Select':
- OOSAssumeRole
- '{{ACS::TaskLoopItem}}'
Loop:
RateControl: '{{ rateControl }}'
Items: '{{ accountRoleAndRegions }}'