An Alibaba Cloud account can use Microservices Engine (MSE) to grant permissions for the Microservices Governance Center to Resource Access Management (RAM) users. You can grant these permissions in the console or by calling OpenAPI operations. This practice avoids the security risk of exposing your Alibaba Cloud account keys. After permissions are granted, a RAM user can use the MSE Microservices Governance Center. This topic describes how to create a RAM user and grant permissions to the user in the console.
Scenarios
An enterprise uses MSE. Its employees have different job responsibilities and require different permissions for resources. For example, Operations and Maintenance (O&M) engineers manage applications and permissions, and developers configure application rules. The enterprise has the following requirements:
For security reasons, the enterprise wants to avoid exposing its Alibaba Cloud account keys to employees. Instead, it wants to grant specific permissions to each employee's account.
User accounts can operate resources only if they have the required permissions. These accounts do not require separate billing. All costs are charged to the enterprise account.
The permissions for a user account can be revoked at any time. The user account can also be deleted at any time.
An application owner has permissions only for the application that they manage and cannot access or operate other applications.
Testers have permissions only for applications in the test namespace. They cannot access or operate applications in the production namespace.
Step 1: Create a RAM user
For more information, see Create a RAM user.
Step 2: Grant permissions to the RAM user
Before using a RAM user, you must grant the required permissions to the user.
Log on to the RAM console as a RAM administrator.
In the left-side navigation pane, choose .
On the Users page, find the required RAM user, and click Add Permissions in the Actions column.
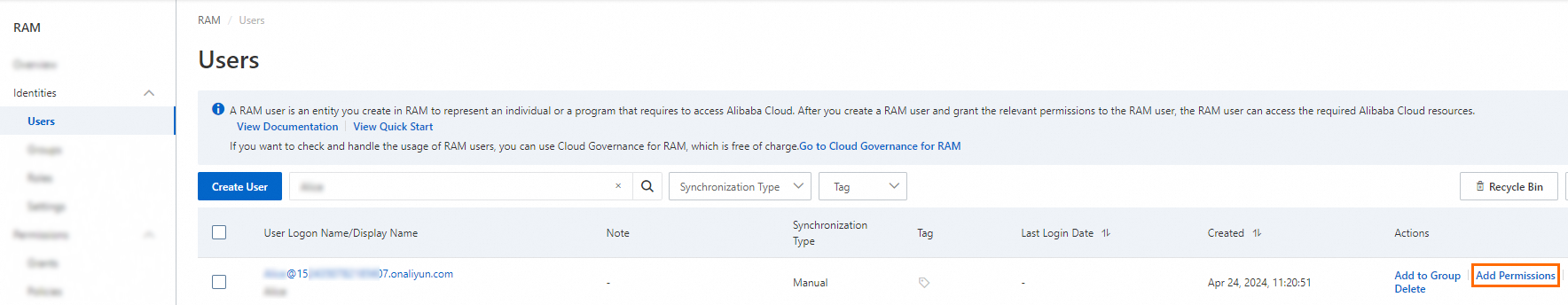
You can also select multiple RAM users and click Add Permissions in the lower part of the page to grant permissions to the RAM users at a time.
In the Add Permissions panel, select access policies and click OK.
Select an access policy type. In the text box, enter a keyword for the policy that you want to add. Click the policy in the search results to add it to the Selected Policy list on the right.
Access policy types include system policies and custom policies:
System policies (Coarse-grained authorization)
Access Policy Name
Description
AliyunMSEFullAccess
Permissions to manage MSE. This policy is equivalent to the permissions of an Alibaba Cloud account. A RAM user who is granted this policy has permissions to perform all operations in the MSE console.
AliyunMSEReadOnlyAccess
Read-only permissions for MSE. A RAM user who is granted this policy has read-only permissions in the MSE console.
NoteGrant the AliyunMSEFullAccess policy to O&M engineers to allow them to create and delete resources. Grant the AliyunMSEReadOnlyAccess policy to developers to allow them to view resources but not create or delete them.
Custom policies (Granular authorization)
If you require more granular authorization, you can create custom policies. For examples, see Examples of common permission configurations. To learn how to create a custom policy, see Create a custom policy.
In the Add Permissions panel, confirm that the authorization is complete, and then click Close.
Examples of common permission configurations
Read-only permissions for all applications
You can grant read-only permissions for all applications. This allows users in your enterprise to view key information about the applications.
For example, you can use an Alibaba Cloud account to grant a RAM user read-only permissions for all microservices governance applications that belong to the account.
The corresponding access policy is as follows:
{
"Version": "1",
"Statement": [
{
"Effect": "Allow",
"Action": [
"mse:QueryNamespace",
"mse:GetApplicationListWithMetircs",
"mse:ListNamespaces",
"mse:GetEventFilterOptions",
"mse:ListEventRecords",
"mse:GetEventDetail",
"mse:FetchLogConfig",
"mse:QueryBusinessLocations",
"mse:GetApplicationInstanceList",
"mse:listGrayTag",
"mse:QueryServiceDetailWithMetrics",
"mse:GetEventDetail",
"mse:ListEventsPage",
"mse:ListEventsByType",
"mse:GetApplicationTagList"
],
"Resource": "acs:mse:*:*:*"
},
{
"Effect": "Allow",
"Action": "mse:GetApplicationList",
"Resource": "acs:mse:*:*:namespace/${ns}"
}
]
}Full permissions for a specific application
As the owner of an application in an enterprise, you can obtain full permissions for that application. Your permissions are strictly limited to the application that you manage.
For example, you can use an Alibaba Cloud account to grant the following permissions to a RAM user:
The RAM user has read-only permissions for all microservices governance applications that belong to the Alibaba Cloud account.
The RAM user has read-only permission on the specified microservice administration application.
The corresponding access policy is as follows:
{
"Version": "1",
"Statement": [
// Grants full permissions for a specific microservices governance application
{
"Effect": "Allow",
"Action": "mse:*",
"Resource": "acs:mse:*:*:namespace/${ns}/application/${appName}"
},
// The following policy grants read-only permissions for all microservices governance applications
{
"Effect": "Allow",
"Action": [
"mse:QueryNamespace",
"mse:GetApplicationListWithMetircs",
"mse:ListNamespaces",
"mse:GetEventFilterOptions",
"mse:ListEventRecords",
"mse:GetEventDetail",
"mse:FetchLogConfig",
"mse:QueryBusinessLocations",
"mse:GetApplicationInstanceList",
"mse:listGrayTag",
"mse:QueryServiceDetailWithMetrics",
"mse:GetEventDetail",
"mse:ListEventsPage",
"mse:ListEventsByType",
"mse:GetApplicationTagList"
],
"Resource": "acs:mse:*:*:*"
},
{
"Effect": "Allow",
"Action": "mse:GetApplicationList",
"Resource": "acs:mse:*:*:namespace/${ns}"
}
]
Full permissions for a specific namespace
As a tester in an enterprise, you can obtain permissions to operate all applications in the test environment (test namespace). Your permissions are strictly limited to the test environment (test namespace).
For example, you can use an Alibaba Cloud account to grant the following permissions to a RAM user:
The RAM user has read-only permissions for all microservices governance applications that belong to the Alibaba Cloud account.
The RAM user has read and write permissions for the specified microservices governance namespace.
The corresponding access policy is as follows:
{
"Version": "1",
"Statement": [
// Grants full permissions for a specific microservices governance namespace
{
"Effect": "Allow",
"Action": "mse:*",
"Resource": "acs:mse:*:*:namespace/${ns}/application/*"
},
// The following policy grants read-only permissions for all microservices governance applications
{
"Effect": "Allow",
"Action": [
"mse:QueryNamespace",
"mse:GetApplicationListWithMetircs",
"mse:ListNamespaces",
"mse:GetEventFilterOptions",
"mse:ListEventRecords",
"mse:GetEventDetail",
"mse:FetchLogConfig",
"mse:QueryBusinessLocations",
"mse:GetApplicationInstanceList",
"mse:listGrayTag",
"mse:QueryServiceDetailWithMetrics",
"mse:GetEventDetail",
"mse:ListEventsPage",
"mse:ListEventsByType",
"mse:GetApplicationTagList",
"mse:QueryAllSwimmingLaneGroup",
"mse:QueryAllSwimmingLane",
"mse:ListAppBySwimmingLaneGroupTags",
"mse:ListAppBySwimmingLaneGroupTag",
"mse:QuerySwimmingLaneById",
"mse:GetTagsBySwimmingLaneGroupId",
"mse:ListSwimmingLaneGateway",
"mse:ListSwimmingLaneGatewayRoute",
"mse:ListAuthPolicy",
"mse:GetServiceList",
"mse:GetServiceListPage"
],
"Resource": "acs:mse:*:*:*"
},
// Grants full permissions for a specific microservices governance namespace
{
"Effect": "Allow",
"Action": [
"mse:GetApplicationList",
"mse:CreateOrUpdateSwimmingLaneGroup",
"mse:CreateOrUpdateSwimmingLane",
"mse:DeleteSwimmingLaneGroup",
"mse:DeleteSwimmingLaneGroup",
"mse:DeleteSwimmingLane"
],
"Resource": "acs:mse:*:*:namespace/${ns}"
}
]
}Permissions for quick integration by a RAM user
If a RAM user needs to complete the quick integration process, the user must have at least all the permissions that are shown in the following example.
{
"Version": "1",
"Statement": [
{
"Effect": "Allow",
"Action": [
"mse:CheckServiceLinkRole",
"mse:GetUserStatus",
"mse:QueryNamespace",
"mse:ListCsKubernetesClusters",
"mse:CheckEciRole",
"mse:ListCsKubernetesClusters",
"mse:CheckCsRole",
"mse:GetClusterOnePilotInfo",
"mse:GetGovernanceKubernetesCluster",
"mse:InstallOnePilot",
"mse:CreateNamespace",
"mse:ModifyGovernanceKubernetesCluster",
"mse:QueryGovernanceKubernetesCluster",
"mse:ListNamespaces"
],
"Resource": "*"
}
]
}Read and write permissions for all governed resources (for permission testing only, not recommended for production)
This section lists the read and write permissions for all resources that might be used in service administration. This helps you review and verify the permissions of RAM users. Do not copy this policy directly to a production environment. In the following policy, you can replace the Action and Resource configurations with mse:* and acs:mse:*:*:*, respectively:
{
"Version": "1",
"Statement": [
{
"Effect": "Allow",
"Action": [
"mse:AddAuthPolicy",
"mse:AddServiceTimeConfig",
"mse:AddWhiteScreenRule",
"mse:ApplyGlobalReadWriteSplitRule",
"mse:ApplyReadWriteSplitRule",
"mse:ApplyTagPolicies",
"mse:BatchUpdateRulesEnable",
"mse:BindSentinelBlockFallbackDefinition",
"mse:CheckCanaryPolicy",
"mse:CheckCsRole",
"mse:CheckEciRole",
"mse:CheckRole",
"mse:CheckServiceLinkedRoleForDeleting",
"mse:CheckUserReadinessConfig",
"mse:CheckXTraceServiceStatus",
"mse:CloneSentinelRuleFromAhas",
"mse:CreateApplication",
"mse:CreateCircuitBreakerRule",
"mse:CreateFlowRule",
"mse:CreateGovernanceKubernetesCluster",
"mse:CreateHotParamRule",
"mse:CreateIsolationRule",
"mse:CreateLicenseKey",
"mse:CreateMseServiceApplication",
"mse:CreateNamespace",
"mse:CreateOrUpdateEmptyPushSetting",
"mse:CreateOrUpdateSwimmingLane",
"mse:CreateOrUpdateSwimmingLaneGroup",
"mse:CreateSentinelBlockFallbackDefinition",
"mse:CreateWebFlowRule",
"mse:DeleteCircuitBreakerRules",
"mse:DeleteFaultInjectionRule",
"mse:DeleteFlowRules",
"mse:DeleteGovernanceKubernetesCluster",
"mse:DeleteHotParamRules",
"mse:DeleteIsolationRules",
"mse:DeleteNamespace",
"mse:DeleteSentinelBlockFallbackDefinition",
"mse:DeleteSwimmingLane",
"mse:DeleteSwimmingLaneGroup",
"mse:DeleteWebFlowRules",
"mse:DeleteWhiteScreenRule",
"mse:DescribeAppAgentStatus",
"mse:FetchAppLogConfig",
"mse:FetchDataSourceConfig",
"mse:FetchGlobalReadWriteSplitRules",
"mse:FetchLogConfig",
"mse:FetchLosslessRuleList",
"mse:FetchReadWriteSplitRules",
"mse:FetchRoutePolicyList",
"mse:FetchWhiteScreenRule",
"mse:GenerateAgentLogSts",
"mse:GetAppMessageQueueRoute",
"mse:GetApplicationDetail",
"mse:GetApplicationInstanceList",
"mse:GetApplicationInstancesWithMetircs",
"mse:GetApplicationList",
"mse:GetApplicationListWithMetircs",
"mse:GetApplicationTagList",
"mse:GetAuthPolicyInfo",
"mse:GetCanaryStatus",
"mse:GetClusterOnePilotInfo",
"mse:GetDubboServicePageWithMetrics",
"mse:GetDubboTestMethod",
"mse:GetGovernanceKubernetesCluster",
"mse:GetGovernanceKubernetesClusterList",
"mse:GetLicenseKey",
"mse:GetLocalityDistributionMetrics",
"mse:GetLocalityRule",
"mse:GetLosslessRuleByApp",
"mse:GetMockRuleByConsumerAppId",
"mse:GetMockRuleById",
"mse:GetMockRuleByProviderAppId",
"mse:GetNetworkInfo",
"mse:GetOpenSergoInfoByClusterId",
"mse:GetOutlierPolicyInfo",
"mse:GetOverview ",
"mse:GetResourcePackageStatus",
"mse:GetResourcePackageStatusWithVersion",
"mse:GetRetryRule",
"mse:GetRoutePolicy",
"mse:GetServiceConsumersPage",
"mse:GetServiceDetail",
"mse:GetServiceList",
"mse:GetServiceListPage",
"mse:GetServiceMethodPage",
"mse:GetServiceMethodPageWithMetrics",
"mse:GetServiceProvidersPage",
"mse:GetSpringCloudTestMethod",
"mse:GetTagKey",
"mse:GetTagVal",
"mse:GetTagsBySwimmingLaneGroupId",
"mse:GetTrace",
"mse:GetUserStatus",
"mse:InstallOnePilot",
"mse:InvokeDubboTestMethod",
"mse:InvokeIstioTestMethod",
"mse:InvokeSpringCloudTestMethod",
"mse:ListAdaptiveOverloadProtectionConfig",
"mse:ListAppBySwimmingLaneGroupTag",
"mse:ListAppBySwimmingLaneGroupTags",
"mse:ListAppResource",
"mse:ListAppResourceWithMetrics",
"mse:ListApplicationTagInstancese",
"mse:ListApplicationsWithTagRules",
"mse:ListAuthPolicy",
"mse:ListCircuitBreakerRules",
"mse:ListConnectedSwimmingLaneGroup",
"mse:ListCsKubernetesClusters",
"mse:ListDefaultCircuitBreakerRules",
"mse:ListEventOfReource",
"mse:ListEventRecords",
"mse:ListEventsByType",
"mse:ListEventsPage",
"mse:ListEventsPageByType",
"mse:ListFlowRules",
"mse:ListHotParamRules",
"mse:ListIpOrHosts",
"mse:ListIsolationRules",
"mse:ListKubernetesNamespace",
"mse:ListLogSpanServices",
"mse:ListMscEventRecords",
"mse:ListNamespaces",
"mse:ListProtectedAppResourceWithMetrics",
"mse:ListResourceWhiteListConfigs",
"mse:ListResources",
"mse:ListSentinelBlockFallbackDefinitions",
"mse:ListSpanNames",
"mse:ListSwimPathPercent",
"mse:ListSwimmingLaneGatewayRoute",
"mse:ListWebFlowRules",
"mse:ModifyAdaptiveOverloadProtectionConfig",
"mse:ModifyGovernanceKubernetesCluster",
"mse:ModifyLosslessRule",
"mse:ModifyNamespace",
"mse:OpenXTraceService",
"mse:QueryAhasUserStatus",
"mse:QueryAllSwimmingLane",
"mse:QueryAllSwimmingLaneGroup",
"mse:QueryAppDataSourceList",
"mse:QueryAppListMetrics",
"mse:QueryAppMethodMetrics",
"mse:QueryAppMethodMetricsWithSentinel",
"mse:QueryAppRPCMacMetrics",
"mse:QueryAppResourceMetrics",
"mse:QueryAppResourceMetricsByInstance",
"mse:QueryAppSummaryMetricsOverview",
"mse:QueryAppSummaryMetricsOverviewWithSentinel",
"mse:QueryAppSystemMetricsOfGroup",
"mse:QueryAppSystemMetricsOfGroupByInstance",
"mse:QueryAppTopNMacs",
"mse:QueryDatabaseRoute",
"mse:QueryEmptyPushSetting",
"mse:QueryEventOverview",
"mse:QueryGovernanceKubernetesCluster",
"mse:QueryMetricsAveragedByInstance",
"mse:QueryNamespace",
"mse:QueryNginxIngressGateway",
"mse:QueryResourceTopN",
"mse:QueryServiceDetailWithMetrics",
"mse:QuerySwimmingLaneById",
"mse:RemoveApplication",
"mse:RemoveApplications",
"mse:RemoveAuthPolicy",
"mse:RemoveOutlierPolicy",
"mse:RemoveRoutePolicy",
"mse:ReportAgentInfoForm",
"mse:ReportAgentStartupStatus",
"mse:ReportAppProfile",
"mse:ReportEventBatchForm",
"mse:ReportMetadataForm",
"mse:ReportOneAgentInfo",
"mse:ReportOnePilotInfo",
"mse:ReportSpanStatInfoForm",
"mse:RevertApplicationRoutePolicy",
"mse:SearchTraces",
"mse:TagResources",
"mse:UnbindSentinelBlockFallbackDefinition",
"mse:UpdateAppLogConfig",
"mse:UpdateAuthPolicy",
"mse:UpdateCircuitBreakerRule",
"mse:UpdateCircuitBreakerRulesStatus",
"mse:UpdateDatabaseRoute",
"mse:UpdateDefaultCircuitBreakerRule",
"mse:UpdateFlowRule",
"mse:UpdateFlowRulesStatus",
"mse:UpdateGovernanceServiceSubscribe",
"mse:UpdateHotParamRule",
"mse:UpdateHotParamRulesStatus",
"mse:UpdateInstanceRegisterStatus",
"mse:UpdateIsolationRule",
"mse:UpdateIsolationRulesStatus",
"mse:UpdateLocalityRule",
"mse:UpdateLogConfig",
"mse:UpdateMessageQueueRoute",
"mse:UpdateOpenSergoStatusByClusterId",
"mse:UpdateResourceWhiteListConfig",
"mse:UpdateSentinelBlockFallbackDefinition",
"mse:UpdateWebFlowRule",
"mse:UpdateWebFlowRulesStatus",
"mse:UpdateWhiteScreenRule",
"mse:listGrayTag"
],
"Resource": "acs:mse:*:*:*"
}
]
}