This glossary sorts the terms alphabetically.
A
APK/AAB package hardening (Android)
Provides overall security protection for APK/AAB packages, including anti-decompilation protection for APK/AAB packages, overall protection for DEX files, anti-tampering protection for DEX files, anti-white box attacks, shell encryption algorithm protection, anti-debugging protection, anti-memory tampering protection, anti-hook protection, anti-simulator protection, anti-repackaging protection for APK/AAB packages, and anti-memory dump protection.
Anti-formatting (HTML5)
Force the code to be displayed as a single line. If the code is formatted or renamed, the code cannot be executed.
B
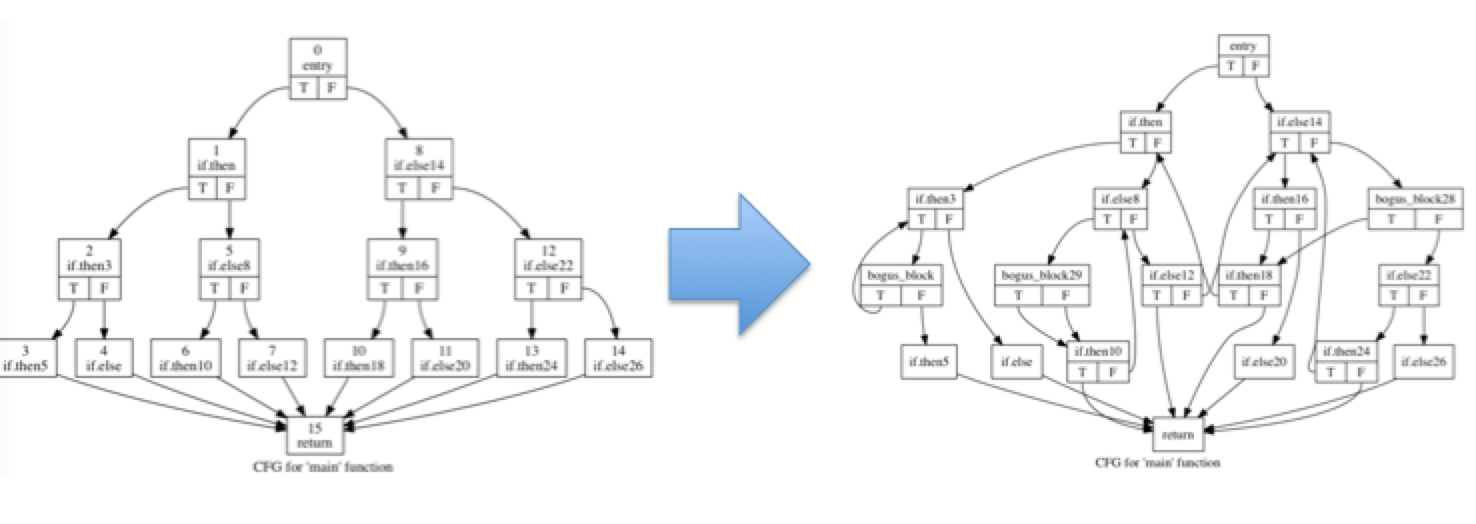
Branch forgery (iOS)
The branch forgery module is a built-in security compiler based control flow obfuscation method based on opaque predicates. Combining the control flow reachability analysis results and the random opaque predicate constructor, the branch forgery module can achieve the purpose of control flow transformation at a lower cost (little performance impact, less file bloat).
C
Constant encryption (iOS)
The constant encryption feature supports compile-time encryption for various types of array constants. The purpose is to hide the display string such as log information to reduce the risk of information leakage, and to hide the contents of static constant arrays such as AES-SBOX to improve the difficulty of static feature recognition of general algorithms.
Code compression (HTML5)
Remove unnecessary spaces, line breaks and other content in JavaScript code, or process some possibly common code for sharing, and finally compress the output into a few lines, reducing the readability of the code.
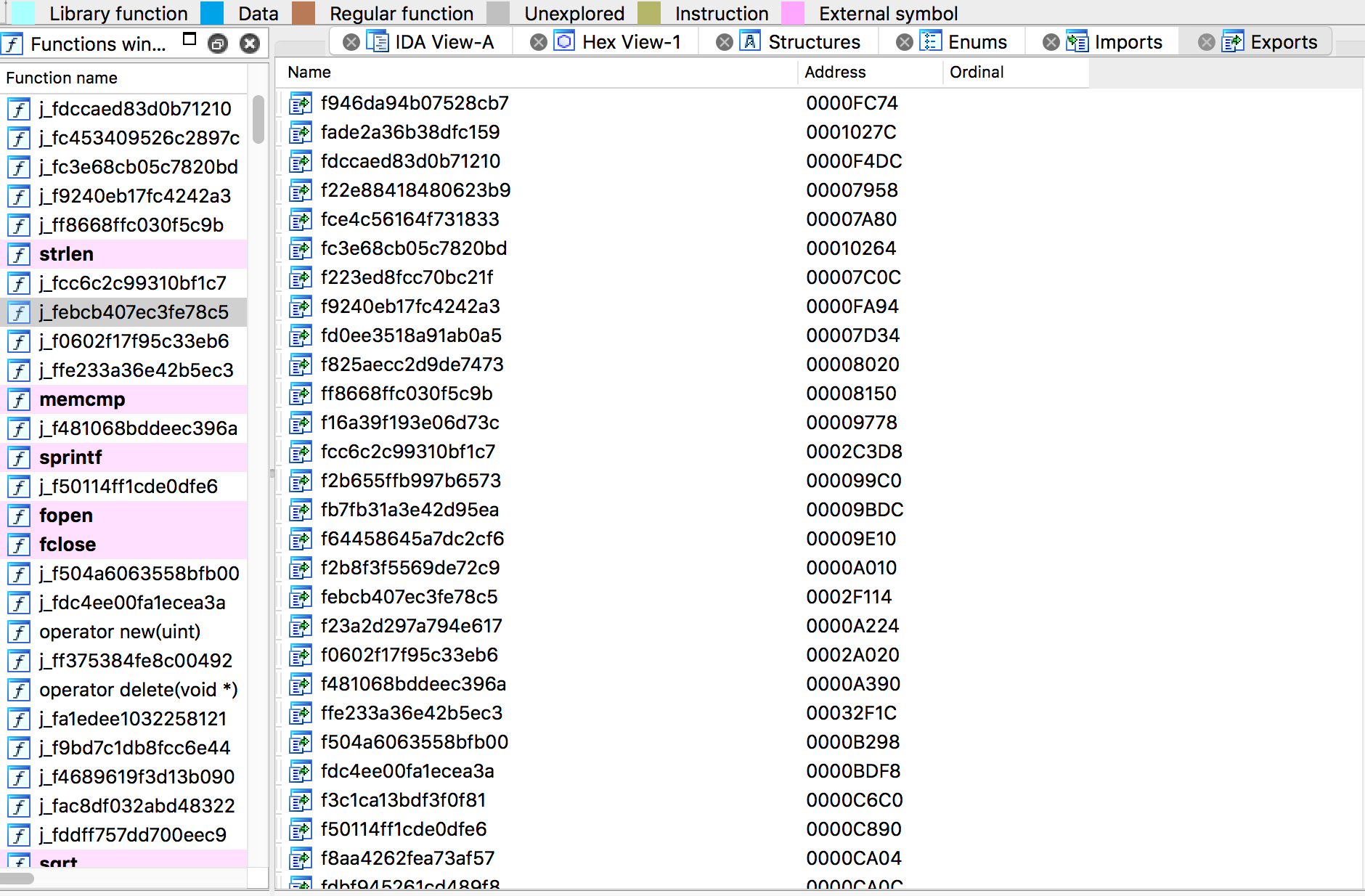
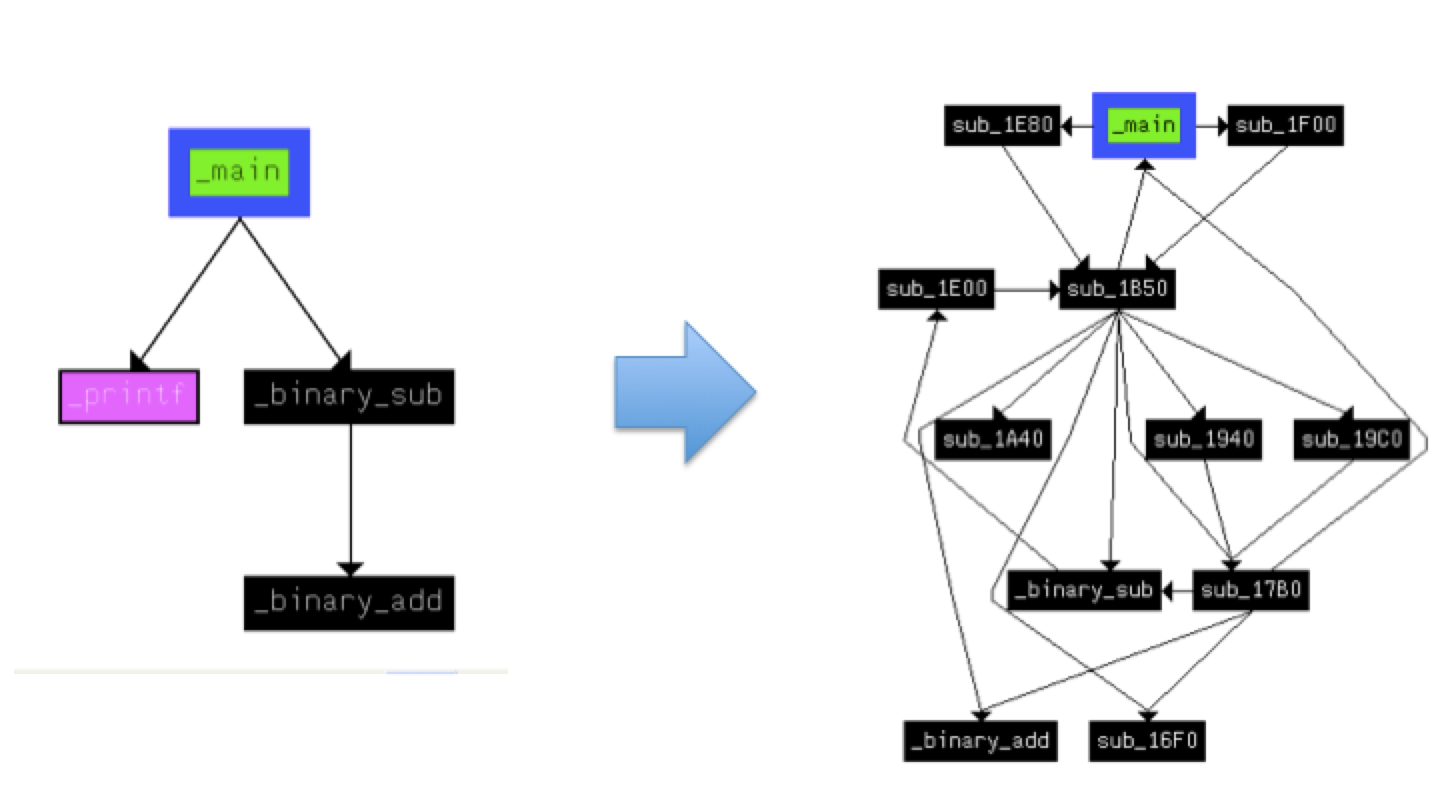
Call graph obfuscation (iOS)
The call graph refers to the cross-call relationship between functions and is an important indicator of the macro structure of the program. Compared with the obfuscation technique for the control flow graph within the process, the call graph obfuscation module is a module-level, inter-function reference relationship obfuscation technique. The call graph transformation module can destroy the structure of the source program from the macro level and eliminate the modular design characteristics of the source program by transforming all the call instructions of the source program.
Control flow flattening (HTML5)
Control flow flattening is an in-process control flow processing technology that can disrupt the original code execution flow and function call relationship, making the code logic chaotic. It aims to eliminate the predecessor-sequence relationship between semantic blocks and improve the cost of algorithm understanding.
The security compiler has a variety of built-in flattening implementations, which can be automatically selected when processing the target program; at the same time, the security compiler has improved many detailed processing methods, and it also has strong resistance to the control flow analysis method based on symbolic execution technology.
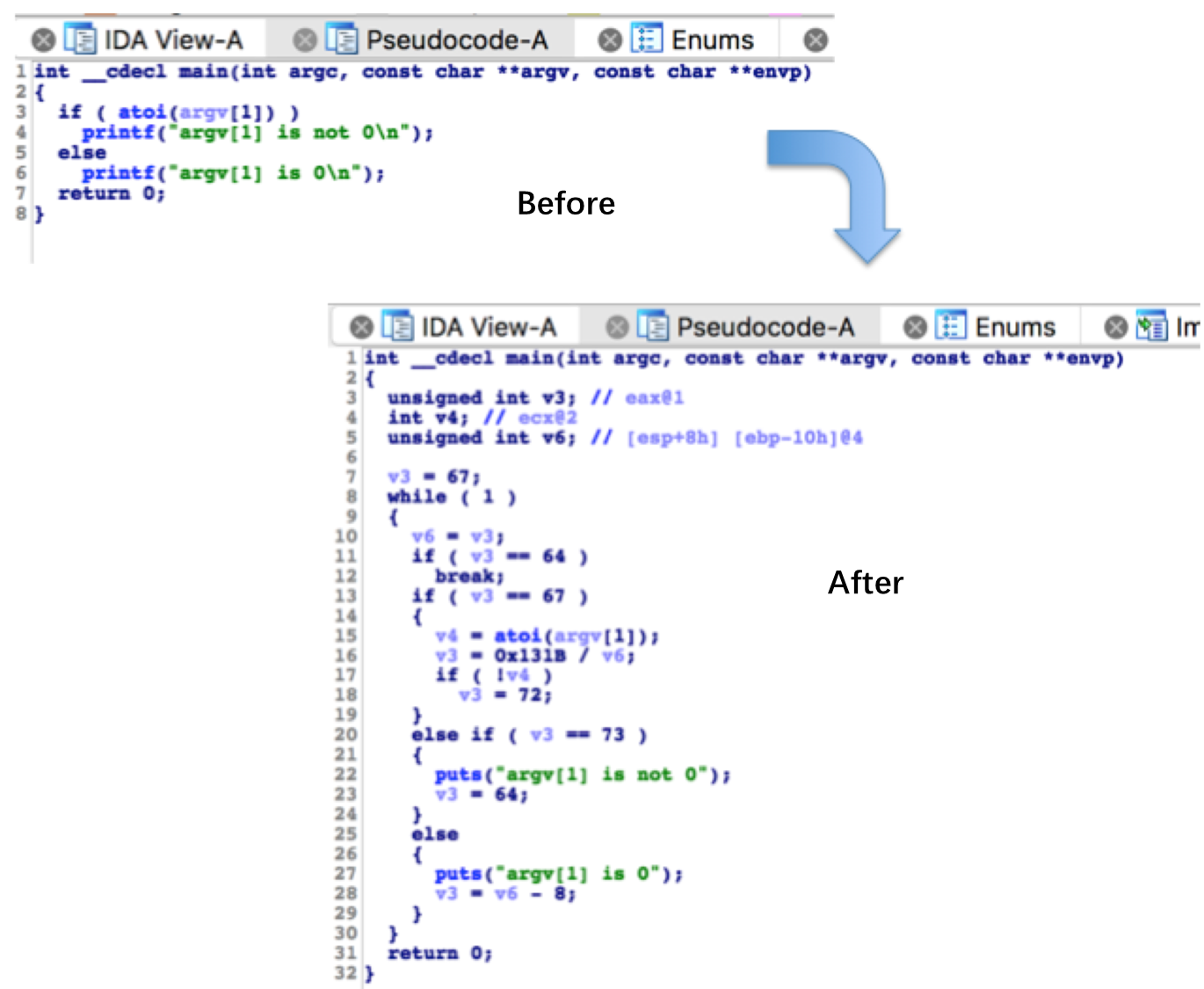
Class security hardening (Android)
The Java code is obfuscated to hide the real running process and prevent decompilation of jadx-gui and jeb tools, making the hardened code difficult to be directly read by humans.
Command replacement (iOS)
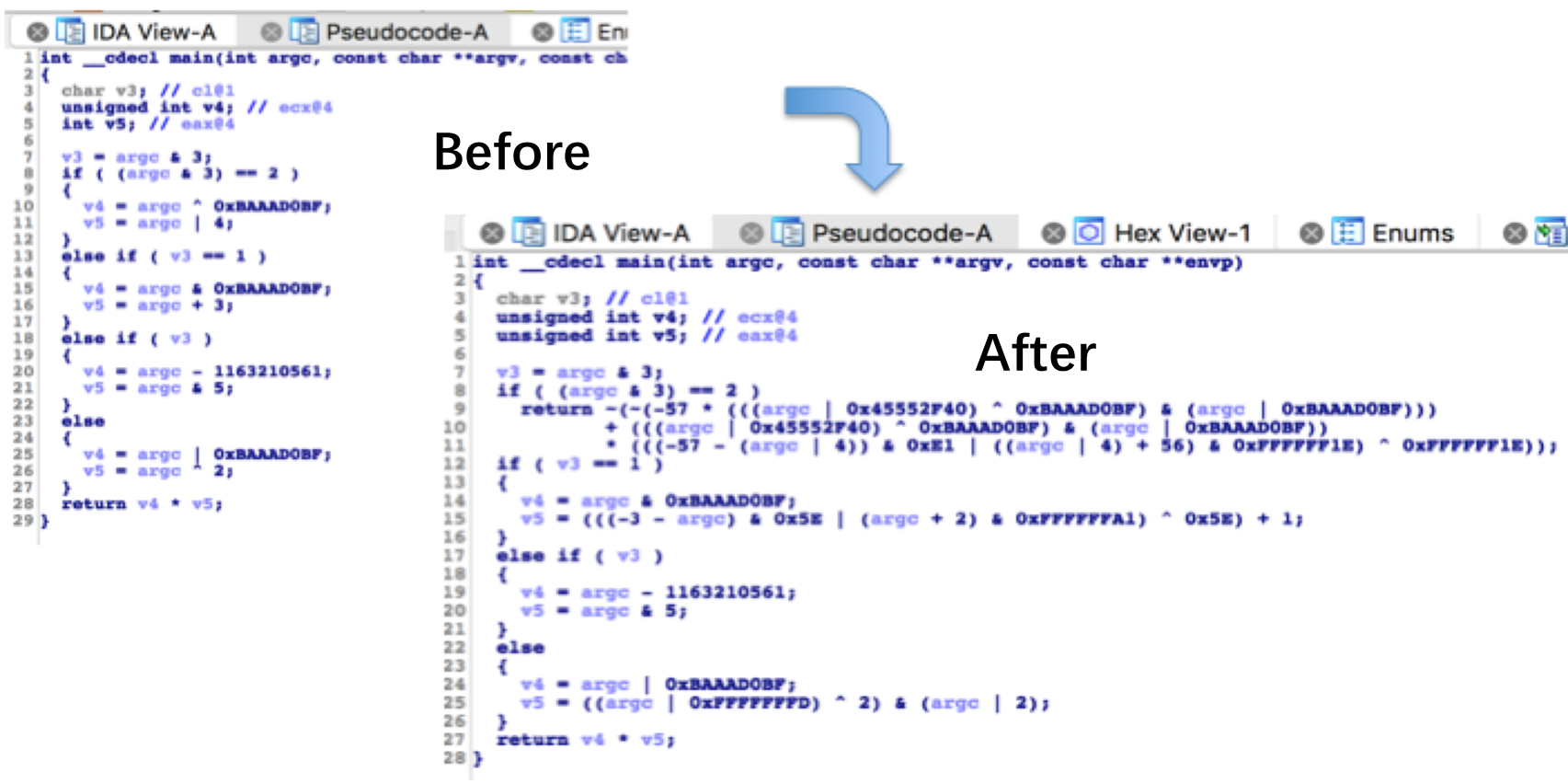
The command replacement component is used to transform or unfold the simple binary operations of the source code such as arithmetic operations and boolean operations. The processed operations are incomprehensible enough to counter the cracking by developers. The command replacement component has dozens of built-in replacement rules which are randomly selected for the replacement process, thus diversifying the generated commands.
E
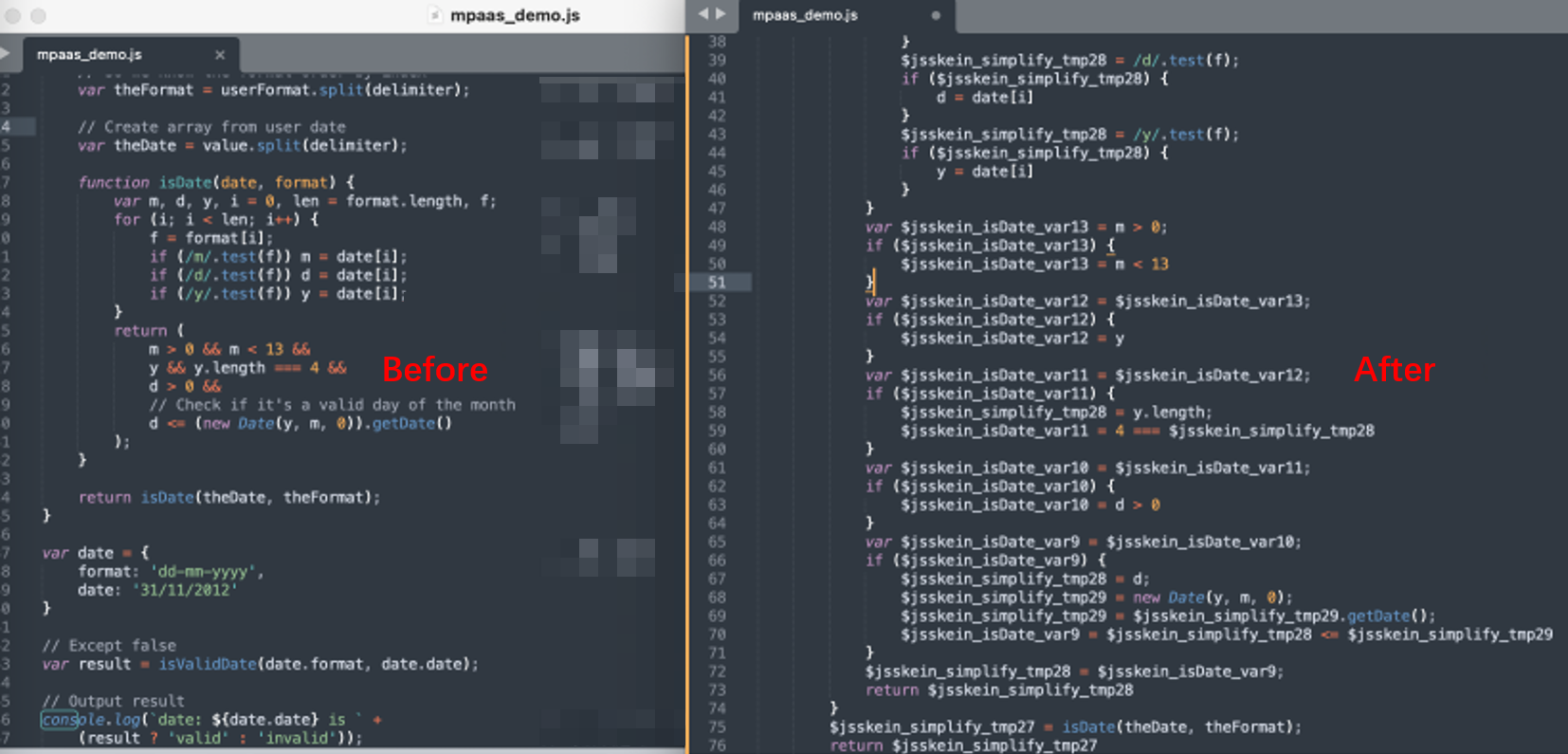
Expression replacement (HTML5)
Convert binary expressions in JavaScript into equivalent function call forms, referring to simple expressions such as a + b, and replace them with equivalent complex expressions, such as a + (-b), to increase analysis difficulty of cracking analysis.
J
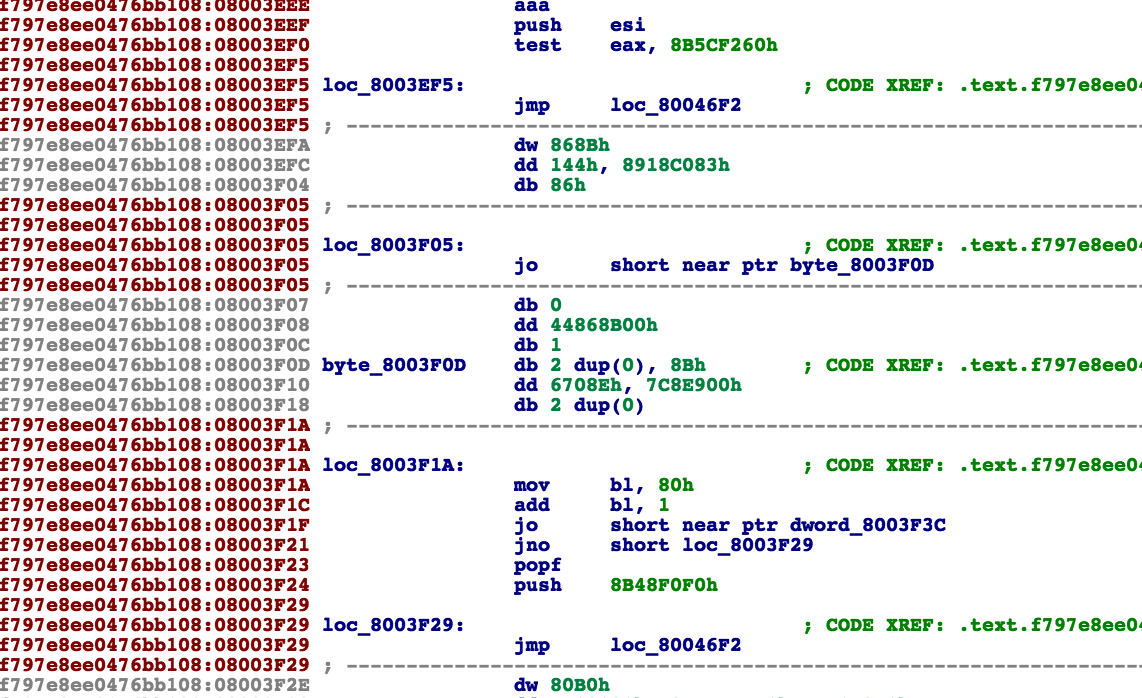
Junk instruction and bad instruction injection (iOS)
The junk instruction refers to the instruction that can be executed while interfering with analysis. The bad instruction refers to the illegal instruction that cannot be executed. The junk instruction and bad instruction injection component is used to counter the analysis capability provided by decompilers which is capable of analyzing static instruction flow.
O
Object key name replacement (HTML5)
Converts the property names of an object to hide the calling relationship between code.
P
Pointer encryption (iOS)
The pointer encryption component is used to remove the explicit reference relationships between functions and data.
S
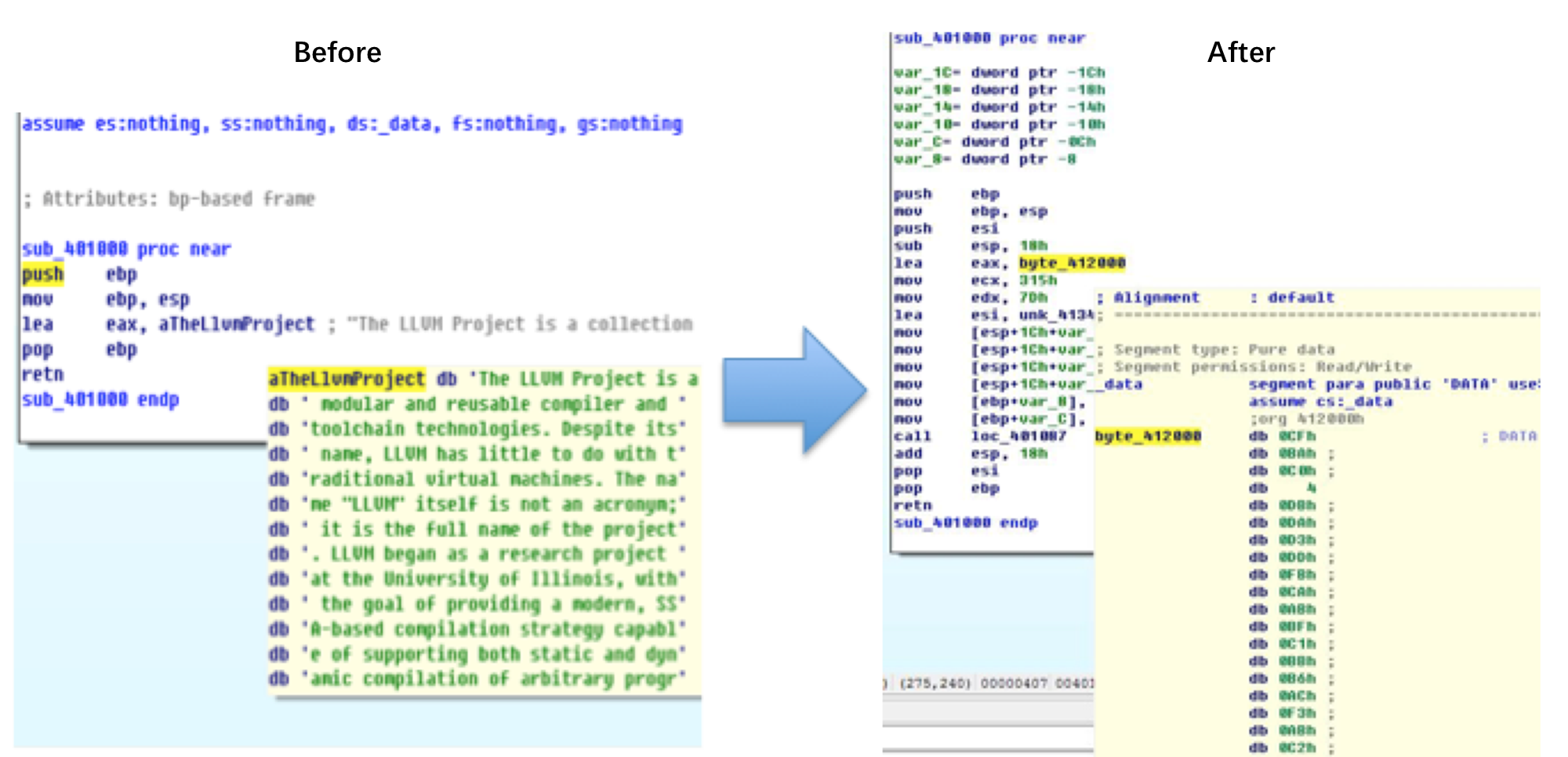
Symbol information encryption (iOS)
Symbol information is the function names and global variable names that are retained in the compiled binary file. Symbol information encryption, that is, according to the specified rules of the specified, consistent with the characteristics of the function name, global variable name, etc. are encrypted.