The alert management system is a subsystem of Simple Log Service that denoises alerts.
Architecture
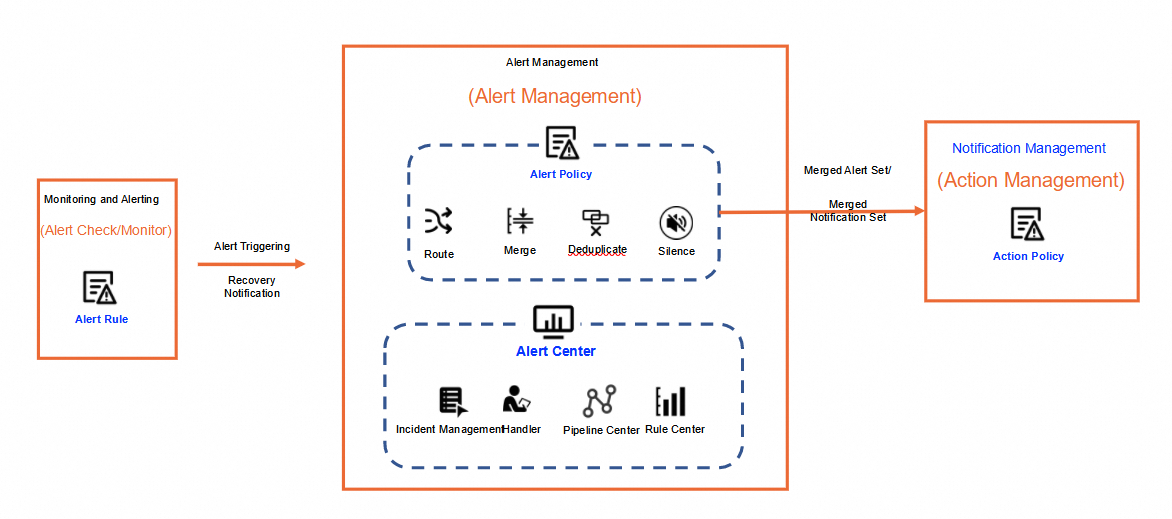
The alert management system receives alerts from the alert monitoring system, completes alert orchestration, and sends the alerts to the notification management system. Then, the notification management system notifies users. Alert orchestration includes the silence, suppress, and deduplicate operations. Simple Log Service provides the Alert Center module for the alert management system. You can manage alerts in Alert Center. You can also view dashboards on the Alert Pipeline Center and Alert Rule Center tabs.
The following figure shows the architecture of the alert management system.
Alert policies
Alert policies are configuration entities of the alert management system. After the alert management system receives alerts and recovery notifications, alerts are handled based on alert policies, such as denoising the alerts.
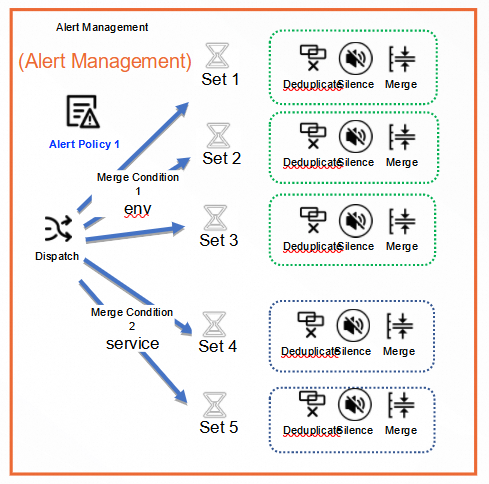
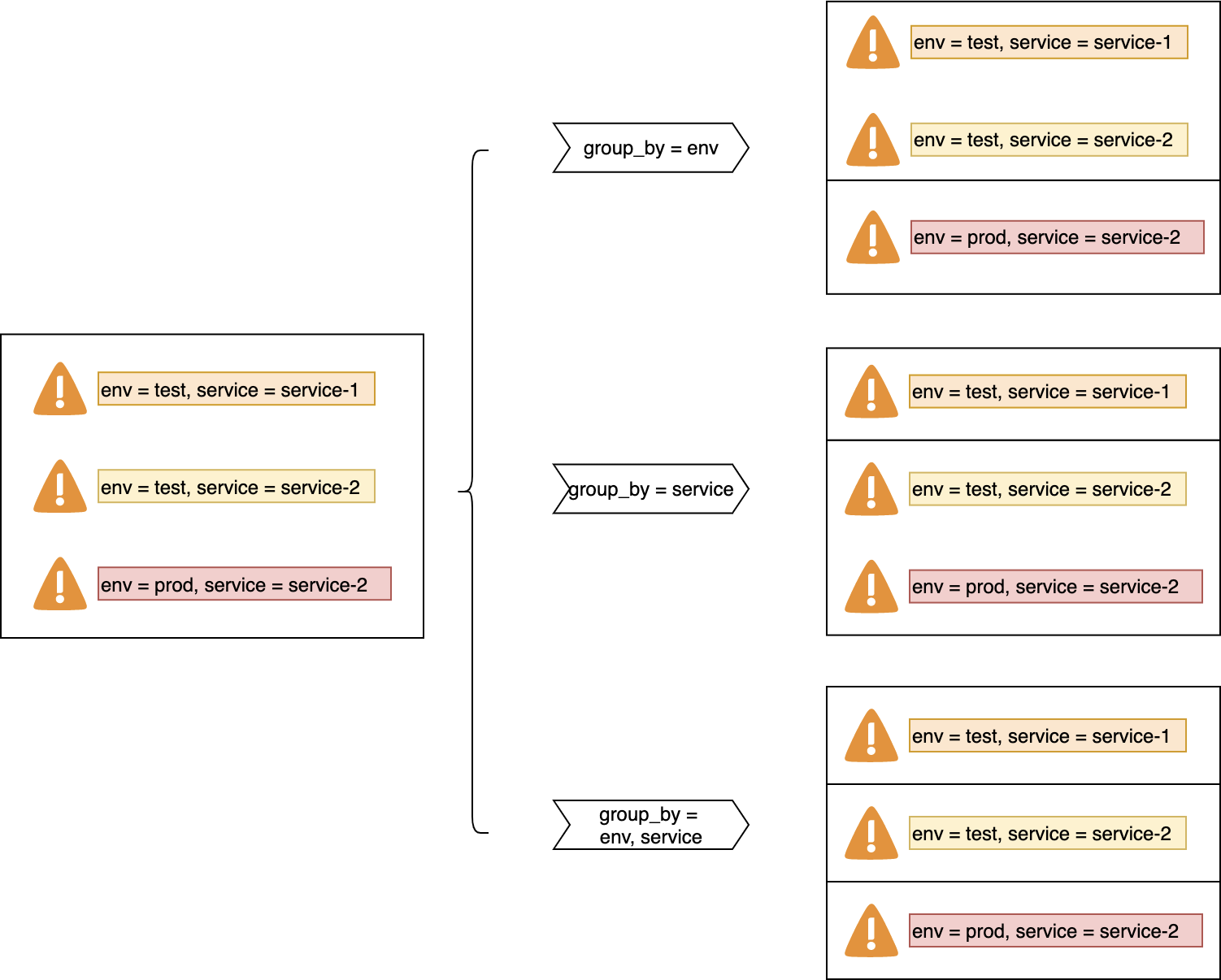
Merge alerts
You can merge alerts that have similar attributes into an alert set. This way, you can handle alerts and send notifications in a centralized manner. This also prevents alert storms. For more information, see Merge alerts.
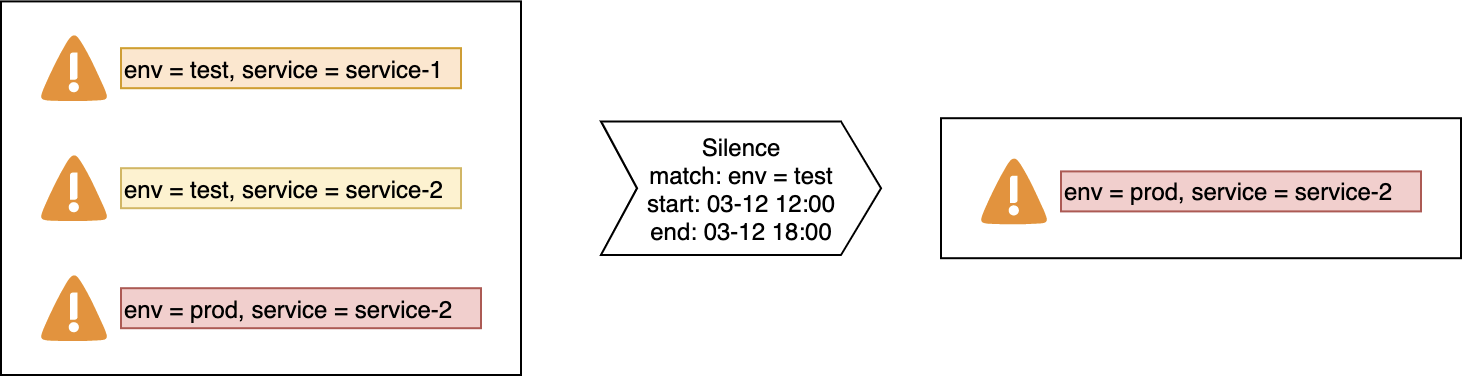
Silence alerts
You can specify a time range during which no alert notifications can be sent. For example, if a large number of alerts are triggered during a maintenance and test period, you can specify a time range to silence alerts. This way, you can prevent a large number of alert notifications. For more information, see Silence policies.
Inherit alert policies
Alert policies can be inherited. If an alert policy is inherited, alerts are processed based on a combination of the parent and child policies. For more information, see Inherit alert policies.
Isolate data
Data is isolated between alert policies.