Key Management Service (KMS) integrates with Cloud Monitor (CMS) to monitor system events and provide alerts. This integration helps you stay informed about events and handle them promptly. This topic describes how to query system events and set alerts.
KMS system event types
System events do not require manual configuration. When the trigger conditions for a system event are met, the event is automatically displayed in the KMS console and the CloudMonitor console. To receive alert notifications for events, you can set them in the CloudMonitor console. For more information, see Set alert notifications for system events.
System event | Event level | Trigger condition |
QPS has reached 90% | CRITICAL | This event is triggered when the real-time queries per second (QPS) of a KMS instance reaches 90% of its quota. |
Key scheduled for deletion | WARN | This event is triggered when a key is scheduled for deletion. |
Key deleted | WARN | This event is triggered when a key is deleted. |
Secret scheduled for deletion | WARN | This event is triggered when a secret is scheduled for deletion. |
Secret deleted | WARN | This event is triggered when a secret is deleted. |
Managed secret rotation failed | CRITICAL | This event is triggered when a secret rotation fails. |
Managed secret rotation succeeded | INFO | This event is triggered when a secret rotation succeeds. |
Key sync failed | CRITICAL | This event is triggered when a key in a KMS instance fails to sync across regions. For more information, see Cross-region synchronization. |
Key sync succeeded | INFO | This event is triggered when a key in a KMS instance successfully syncs across regions. For more information, see Cross-region synchronization. |
ClientKey expiration reminder | CRITICAL | This event is triggered 180, 90, 30, and 7 days before a ClientKey expires. For more information about ClientKeys, see Overview of application access points. |
QPS has reached 70% | INFO | This event is triggered when the real-time QPS of a KMS instance reaches 70%. If the limit is exceeded, KMS may become inaccessible and affect business continuity. |
Access management usage has reached 70% | INFO | This event is triggered when the access management usage of a KMS instance reaches 70%. If the limit is exceeded, you cannot create new access management policies. |
Access management usage has reached 90% | WARN | This event is triggered when the access management usage of a KMS instance reaches 90%. If the limit is exceeded, you cannot create new access management policies. |
Key usage has reached 70% | INFO | This event is triggered when the key usage of a KMS instance reaches 70%. If the limit is exceeded, you cannot create new keys. |
Key usage has reached 90% | WARN | This event is triggered when the key usage of a KMS instance reaches 90%. If the limit is exceeded, you cannot create new keys. |
Log analysis log volume has reached 70% | INFO | This event is triggered when the log analysis log volume of a KMS instance reaches 70%. If the limit is exceeded, new logs cannot be written. |
Log analysis log volume has reached 90% | WARN | This event is triggered when the log analysis log volume of a KMS instance reaches 90%. If the limit is exceeded, new logs cannot be written. |
Secret usage has reached 70% | INFO | This event is triggered when the Secret usage of a KMS instance reaches 70%. If the limit is exceeded, you cannot create new secrets. |
Secret usage has reached 90% | WARN | This event is triggered when the secret usage of a KMS instance reaches 90%. If the limit is exceeded, you cannot create new secrets. |
Supported CloudMonitor metrics
Metric | Description | Alerting supported | Dimensions | Statistics |
Requests per minute for an instance | Number of requests per minute. | Yes | userId, regionId, instanceId | Value |
Symmetric encryption/decryption requests per minute | Number of symmetric operation requests per minute. | Yes | userId, regionId, instanceId | Value |
Asymmetric encryption requests per minute | Number of asymmetric encryption requests per minute. | Yes | userId, regionId, instanceId | Value |
Asymmetric decryption requests per minute | Number of asymmetric decryption requests per minute. | Yes | userId, regionId, instanceId | Value |
Asymmetric signing requests per minute | Number of asymmetric signing requests per minute. | Yes | userId, regionId, instanceId | Value |
Asymmetric signature verification requests per minute | Number of asymmetric signature verification requests per minute. | Yes | userId, regionId, instanceId | Value |
Secret operation requests per minute | Number of secret requests per minute. | Yes | userId, regionId, instanceId | Value |
Other requests per minute | Number of other operation requests per minute. | Yes | userId, regionId, instanceId | Value |
5xx error requests | Number of requests with 5xx error codes per minute. | Yes | userId, regionId, instanceId | Value |
4xx error requests | Number of requests with 4xx error codes per minute. | Yes | userId, regionId, instanceId | Value |
Request latency | Average latency of all requests per minute. | Yes | userId, regionId, instanceId | Value |
KMS instance CPU utilization | CPU utilization of the instance. | Yes | user_id, instance_id | Value |
KMS instance symmetric QPS utilization | Symmetric QPS utilization of the instance. | Yes | user_id, instance_id | Value |
KMS instance asymmetric QPS utilization | Asymmetric QPS utilization of the instance. | Yes | user_id, instance_id | Value |
View system events
You can view system events from the last 90 days.
Method 1: View in the KMS console
Log on to the KMS console. In the top navigation bar, select a region. In the navigation pane on the left, choose .
On the CloudMonitor Alerts tab, select the system event and time range that you want to query.
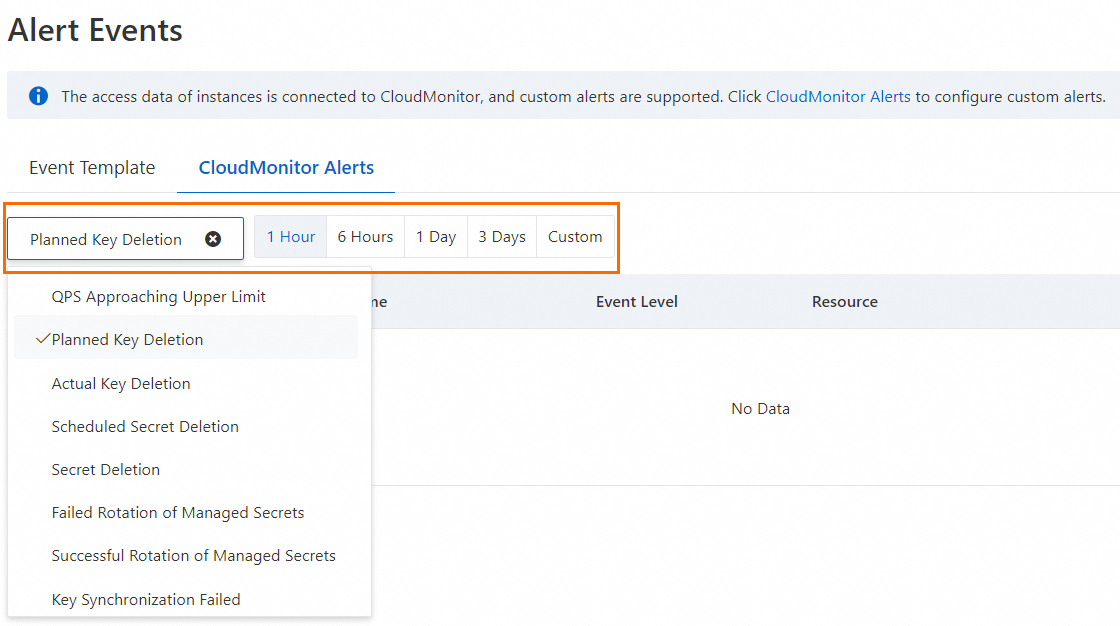
In the Actions column, click Details to view the event details.
Method 2: View in the CloudMonitor console
Log on to the Cloud Monitor console.
In the navigation pane on the left, choose .
On the Event Monitoring tab, set Product to Key Management Service, select the event level, event name, and time period, and then click Search.
In the event list, click Details in the Actions column for the target event.
Set alert notifications for system events
You can set alert rules for system events to receive prompt notifications when exceptions occur. This helps you quickly analyze and locate issues. You can set these rules only in the CloudMonitor console.
Log on to the Cloud Monitor console.
In the navigation pane on the left, choose .
On the Event Monitoring tab, click Save as Alert Rule.
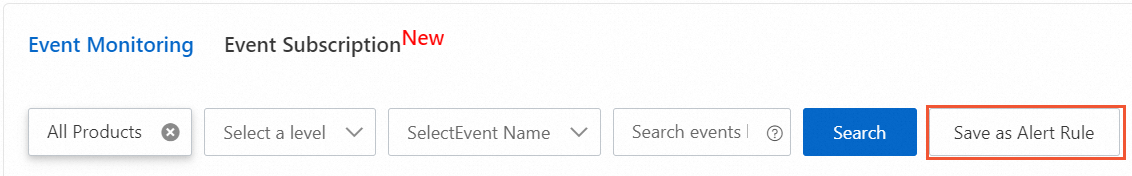 Note
NoteTo perform custom processing on alert notifications, such as merging and noise reduction, configure the notifications on the Event Subscription page. For more information, see Manage event subscriptions (recommended).
In the Create/Modify Event-triggered Alert Rule panel, configure the alert settings.
NoteFor more information about the configuration items, see Create an alert rule for a system event.
View statistical data
For information about configuring KMS CloudMonitor alerts and viewing CloudMonitor statistics, see Overview.
Appendix: Description of JSON fields in event notifications
QPS has reached 90%
{
"product": "kms",
"resourceId": "acs:kms:cn-shanghai:119285********60:instance/<resource-id>",
"level": "CRITICAL",
"instanceName": "instanceName",
"regionId": "cn-hangzhou",
"name": "Instance:QPS:Reminder",
"content": {
"eventId": "119285********60:0d603b4a-********71:175*****07",
"qps": "***",
"kmsInstanceId": "kst***pn8",
"time": "2025-08-26 05:43:00",
"qpsQuota": "***"
},
"status": "normal"
}Description of the content fields:
Field | Description | Example |
eventId | The event ID. | 119285********60:0d603b4a-********71:175*****07 |
qps | The current QPS. | 10000 per second |
kmsInstanceId | The KMS instance ID. | kst***pn8 |
qpsQuota | The QPS limit. | 10000 per second |
Key scheduled for deletion
{
"id": "83d05dd6-1066-4b3f-99be-********19",
"status": "normal",
"instanceName": "0d603b4a-********71be",
"resourceId": "acs:kms:cn-hangzhou:119285********60:key/0d603b4a-********71be",
"content": {
"eventId": "119285********60:0d603b4a-********71:175*****07",
"keyId": "0d603b4a-********71be",
"deleteEntityArn": "acs:kms:cn-hangzhou:119285********60:key/0d603b4a-********71be",
"plannedDeleteTime": "2025-09-01T07:15:07Z"
},
"product": "kms",
"time": 1756106122000,
"level": "WARN",
"regionId": "cn-hangzhou",
"groupId": "0",
"name": "Key:DeleteKey:ScheduleDeletion"
}Description of the content fields:
Field | Description | Example |
eventId | The event ID. | 119285********60:0d603b4a-********71:175*****07 |
keyId | The key ID. | 0d603b4a-********71be |
deleteEntityArn | The Alibaba Cloud Resource Name (ARN) of the resource to be deleted. | acs:kms:cn-hangzhou:119285********60:key/0d603b4a-********71be |
plannedDeleteTime | The scheduled deletion time. | 2025-09-01T07:15:07Z |
Key deleted
{
"id": "40d14dbc-5b49-481f-********ce",
"status": "normal",
"instanceName": "key-hzz68916ed********q4",
"resourceId": "acs:kms:cn-hangzhou:119285********60:key/key-hzz6********pq4",
"content": {
"eventId": "119285********60:key-hzz6********pq4:1755855590",
"keyId": "0d603b4a-********71be",
"deleteEntityArn": "acs:kms:cn-hangzhou:119285********60:key/0d603b4a-********71be",
"deleteTime": "2025-08-22T09:39:50Z"
},
"product": "kms",
"time": 1755855632000,
"level": "WARN",
"regionId": "cn-hangzhou",
"groupId": "0",
"name": "Key:DeleteKey:ActualDeletion"
}Description of the content fields:
Field | Description | Example |
eventId | The event ID. | 119285********60:0d603b4a-********71:175*****07 |
keyId | The key ID. | 0d603b4a-********71be |
deleteEntityArn | The ARN of the deleted resource. | acs:kms:cn-hangzhou:119285********60:key/0d603b4a-********71be |
deleteTime | The actual key deletion time. | 2025-08-22T09:39:50Z |
Secret scheduled for deletion
{
"id": "a065edc8-*******f9ba432",
"status": "normal",
"instanceName": "XrGp****",
"resourceId": "acs:kms:cn-shanghai:119285********60:secret/XrGp****",
"content": {
"eventId": "119285********60:XrGp****:175*****45",
"secretName": "XrGp****",
"deleteEntityArn": "acs:kms:cn-shanghai:119285********60:secret/XrGp****",
"plannedDeleteTime": "2025-09-01T06:10:45Z"
},
"product": "kms",
"time": 1756102268000,
"level": "WARN",
"regionId": "cn-shanghai",
"groupId": "0",
"name": "Secret:DeleteSecret:ScheduleDeletion"
}Description of the content fields:
Field | Description | Example |
eventId | The event ID. | 119285********60:0d603b4a-********71:175*****07 |
secretName | The secret name. | XrGp**** |
deleteEntityArn | The ARN of the resource to be deleted. | acs:kms:cn-shanghai:119285********60:secret/XrGp**** |
plannedDeleteTime | The scheduled secret deletion time. | 2025-08-22T09:39:50Z |
Secret deleted
{
"id": "a065edc8-********ba432",
"status": "normal",
"instanceName": "XrGp****",
"resourceId": "acs:kms:cn-shanghai:119285********60:secret/XrGp****",
"content": {
"eventId": "119285********60:XrGp****:1756102245",
"secretName": "XrGp****",
"deleteEntityArn": "acs:kms:cn-shanghai:119285********60:secret/XrGp****",
"deleteTime": "2025-09-01T06:10:45Z"
},
"product": "kms",
"time": 1756102268000,
"level": "WARN",
"regionId": "cn-shanghai",
"groupId": "0",
"name": "Secret:DeleteSecret:ScheduleDeletion"
}Description of the content fields:
Field | Description | Example |
eventId | The event ID. | 119285********60:0d603b4a-********71:175*****07 |
secretName | The secret name. | XrGp**** |
deleteEntityArn | The ARN of the deleted resource. | acs:kms:cn-shanghai:119285********60:secret/XrGp**** |
deleteTime | The actual secret deletion time. | 2025-08-22T09:39:50Z |
Managed secret rotation failed
{
"id": "ac54ac2b-********01aba",
"status": "Failed",
"instanceName": "acs/ecs/secret_rotator",
"resourceId": "acs:kms:cn-chengdu:119285********60:secret/acs/ecs/secret_rotator",
"content": {
"eventId": "119285********60:acs/ecs/secret_rotator:1755853996",
"secretName": "acs/ecs/secret_rotator",
"secretType": "ECS",
"rotationEntityArn": "acs:kms:cn-chengdu:119285********60:secret/acs/ecs/secret_rotator",
"rotationStatus": "Enabled",
"secretSubType": "ECSLoginPassword",
"failureInfo": {
"errorCode": "RotateError",
"errorMessage": "output , err stdout:[Module:DescribeECSInstances failed] "
},
"failureTime": "2025-08-22T09:13:16Z"
},
"product": "kms",
"time": 1755854045000,
"level": "CRITICAL",
"regionId": "cn-chengdu",
"groupId": "0",
"name": "Secret:RotateSecret:Failure"
}Description of the content fields:
Field | Description | Example |
eventId | The event ID. | 119285********60:0d603b4a-********71:175*****07 |
secretName | The secret name. | acs/ecs/secret_rotator |
secretType | Secret type:
| ECS |
secretSubType | Secret subtype:
| ECSLoginPassword |
rotationEntityArn | The ARN of the resource for which rotation is performed. | acs:kms:cn-hangzhou:119285********60:key/0d603b4a-********71be |
rotationStatus | Wheel status:
| 2025-08-22T09:39:50Z |
failureInfo | The reason for the rotation failure.
| |
Managed secret rotation succeeded
{
"id": "21c9b9e0-********f3e678",
"status": "normal",
"instanceName": "acs/ram/user/secrettest",
"resourceId": "acs:kms:cn-shanghai:119285********60:secret/acs/ram/user/secrettest",
"content": {
"eventId": "119285********60:acs/ram/user/secrettest:17******59",
"secretName": "acs/ram/user/secrettest",
"secretType": "RAMCredentials",
"rotationEntityArn": "acs:kms:cn-shanghai:119285********60:secret/acs/ram/user/secrettest",
"rotationStatus": "Enabled",
"secretSubType": "RamUserAccessKey",
"successTime": "2025-08-20T09:37:19Z",
"message": ""
},
"product": "kms",
"time": 1755855610000,
"level": "INFO",
"regionId": "cn-shanghai",
"groupId": "0",
"name": "Secret:RotateSecret:Success"
}Description of the content fields:
Field | Description | Example |
eventId | The event ID. | 119285********60:acs/ram/user/secrettest:17******59 |
secretName | The secret name. | acs/ram/user/secrettest |
secretType | Secret type:
| RAMCredentials |
secretSubType | Secret subtype:
| RamUserAccessKey |
rotationEntityArn | The ARN of the rotated object. | acs:kms:cn-shanghai:119285********60:secret/acs/ram/user/secrettest |
rotationStatus | Rotation status:
| Enabled |
successTime | The time when the rotation succeeded. | 2025-08-20T09:37:19Z |
Key sync failed
{
"product": "kms",
"resourceId": "acs:kms:cn-hangzhou:119285********60:key/<resource-id>",
"level": "CRITICAL",
"instanceName": "instanceName",
"regionId": "cn-hangzhou",
"name": "Instance:KeySync:Failure",
"content": {
"eventId": "119285********60:8071aa27-********87",
"syncTaskId": "8071aa27-********0fc87",
"masterInstanceId": "kst-ph********z6",
"shadowInstanceId": "kst-ps********qq",
"syncStatus": "SyncFailure",
"errorCode": "",
"resourceId": "key-ph********4d",
"resourceType": "KEY",
"eventTime": "2024-03-22T07:41:17Z"
},
"status": "Normal"
}Description of the content fields:
eventId | The event ID. | 119285********60:8071aa27-********87 |
syncTaskId | The sync task ID. | 8071aa27-********0fc87 |
masterInstanceId | The primary instance ID. | kst-ph********z6 |
shadowInstanceId | The replica instance ID. Note The key is synced from the primary instance to the replica instance. | kst-ps********qq |
syncStatus | The sync status: SyncFailure (sync failed). | SyncFailure |
errorCode | The error code. | "" |
resourceId | The resource ID. | key-ph********04d |
resourceType | The resource type. Only KEY is supported. | KEY |
eventTime | The sync time. | 2024-03-22T07:41:17Z |
Key sync succeeded
{
"product": "kms",
"resourceId": "acs:kms:cn-hangzhou:119285********60:key/<resource-id>",
"level": "INFO",
"instanceName": "instanceName",
"regionId": "cn-hangzhou",
"name": "Instance:KeySync:Success",
"content": {
"eventId": "119285********60:8071aa27-********0fc87",
"syncTaskId": "8071aa27-********420fc87",
"masterInstanceId": "kst-ph********z6",
"shadowInstanceId": "kst-ps********qq",
"syncStatus": "SyncSuccess",
"errorCode": "",
"resourceId": "key-ph********04d",
"resourceType": "KEY",
"eventTime": "2024-03-22T07:41:17Z"
},
"status": "Normal"
}Description of the content fields:
Field | Description | Example |
eventId | The event ID. | 119285********60:8071aa27-********0fc87 |
syncTaskId | The sync task ID. | 8071aa27-********420fc87 |
masterInstanceId | The primary instance ID. | kst-ph********z6 |
shadowInstanceId | The replica instance ID. Note The key is synced from the primary instance to the replica instance. | kst-ps********qq |
syncStatus | The sync status: SyncSuccess (sync succeeded). | SyncSuccess |
errorCode | The error code. | "" |
resourceId | The resource ID. | key-ph********04d |
resourceType | The resource type. Only KEY is supported. | KEY |
eventTime | The sync time. | 2024-03-22T07:41:17Z |
ClientKey expiration reminder
{
"product": "kms",
"resourceId": "<aap_arn>",
"level": "CRITICAL",
"instanceName": "instanceName",
"regionId": "cn-hangzhou",
"name": "Instance:ClientKey:ExpireReminder",
"content": {
"clientKeyName": "clientKeyName",
"eventId": "eventId",
"dateOfExpiration": "2024-09-30T18:23:46Z",
"daysToExpire": "180",
"affectedKmsInstanceId": "kst-exxxx"
},
"status": "Normal"
}Description of the content fields:
Field | Description | Example |
eventId | The event ID. | 119285********60:0d603b4a-********71:175*****07 |
clientKeyName | The application access point (AAP) name. | kms-client. |
dateOfExpiration | The expiration time. | 2024-09-30T18:23:46Z |
daysToExpire | The remaining validity period of the ClientKey in days. | 180 |
affectedKmsInstanceId | The scope (KMS instance ID). | kst-hzz********bxt |
QPS has reached 70%
{
"product": "kms",
"resourceId": "acs:kms:cn-hangzhou:1192******18460:instance/<resource-id>",
"level": "INFO",
"instanceName": "instanceName",
"regionId": "cn-hangzhou",
"name": "Instance:QPS:Reminder:70%",
"content": {
"eventId": "130***756",
"qps": "***",
"kmsInstanceId": "kst***e4x",
"time": "2025-12-12 07:49:00",
"qpsQuota": "10***"
},
"status": "normal"
}Description of the content fields:
Field | Description | Example |
eventId | The event ID. | 119285********60:0d603b4a-********71:175*****07 |
qps | The current QPS. | 10000 per second |
kmsInstanceId | The KMS instance ID. | kst***pn8 |
qpsQuota | The QPS limit. | 10000 per second |
Access management usage has reached 70%
{
"product": "kms",
"resourceId": "acs:kms:cn-shanghai:1192******18460:instance/<resource-id>",
"level": "INFO",
"instanceName": "instanceName",
"regionId": "cn-hangzhou",
"name": "Instance:Quota:AccessManagement:70%",
"content": {
"eventId": "119***d:2",
"quota": "***",
"kmsInstanceId": "kst***em7",
"used": "***"
},
"status": "normal"
}Description of the content fields:
Field | Description | Example |
eventId | The event ID. | 119***d:2 |
kmsInstanceId | The KMS instance ID. | kst***pn8 |
quota | The total number of access management policies. | 1000 |
used | Quantity used. | 700 |
Access management usage has reached 90%
"product": "kms",
"resourceId": "acs:kms:ap-southeast-6:1192******18460:instance/<resource-id>",
"level": "WARN",
"instanceName": "instanceName",
"regionId": "cn-hangzhou",
"name": "Instance:Quota:AccessManagement:90%",
"content": {
"eventId": "119***d:1",
"quota": "***",
"kmsInstanceId": "kst***rz5",
"used": "***"
},
"status": "normal"
}Description of the content fields:
Field | Description | Example |
eventId | The event ID. | 119***d:2 |
kmsInstanceId | The KMS instance ID. | kst***pn8 |
quota | The total number of access management policies. | 1000 |
used | Quantity used. | 900 |
Key usage has reached 70%
{
"product": "kms",
"resourceId": "acs:kms:cn-shanghai:1192******18460:instance/<resource-id>",
"level": "INFO",
"instanceName": "instanceName",
"regionId": "cn-hangzhou",
"name": "Instance:Quota:Key:70%",
"content": {
"eventId": "119***774",
"quota": "10***",
"kmsInstanceId": "kst***urs",
"used": "***"
},
"status": "normal"
}Description of the content fields:
Field | Description | Example |
eventId | The event ID. | 119***d:2 |
kmsInstanceId | The KMS instance ID. | kst***pn8 |
quota | The total number of keys. | 1000 |
used | Quantity used. | 700 |
Key usage has reached 90%
{
"product": "kms",
"resourceId": "acs:kms:cn-shanghai:1192******18460:instance/<resource-id>",
"level": "INFO",
"instanceName": "instanceName",
"regionId": "cn-hangzhou",
"name": "Instance:Quota:Key:90%",
"content": {
"eventId": "119***774",
"quota": "10***",
"kmsInstanceId": "kst***urs",
"used": "***"
},
"status": "normal"
}Description of the content fields:
Field | Description | Example |
eventId | The event ID. | 119***d:2 |
kmsInstanceId | The KMS instance ID. | kst***pn8 |
quota | The total number of keys. | 1000 |
used | Quantity used. | 900 |
Log analysis log volume has reached 70%
{
"product": "kms",
"resourceId": "key-phzz******jro04d",
"level": "INFO",
"instanceName": "instanceName",
"regionId": "cn-hangzhou",
"name": "Instance:Quota:Log:70%",
"content": {
"eventId": "eventId",
"quota": "1000",
"kmsInstanceId": "key-phzz******jro04d",
"used": "700"
},
"status": "Normal"
}Description of the content fields:
Field | Description | Example |
eventId | The event ID. | 119***d |
kmsInstanceId | The KMS instance ID. | kst***pn8 |
quota | The total log analysis capacity (GB). | 1000 |
used | The used capacity. | 700 |
Log analysis log volume has reached 90%
{
"product": "kms",
"resourceId": "key-phzz******jro04d",
"level": "INFO",
"instanceName": "instanceName",
"regionId": "cn-hangzhou",
"name": "Instance:Quota:Log:90%",
"content": {
"eventId": "eventId",
"quota": "1000",
"kmsInstanceId": "key-phzz******jro04d",
"used": "900"
},
"status": "Normal"
}Description of the content fields:
Field | Description | Example |
eventId | The event ID. | 119***d |
kmsInstanceId | The KMS instance ID. | kst***pn8 |
quota | The total log analysis capacity (GB). | 1000 |
used | The used capacity. | 900 |
Secret usage has reached 70%
{
"product": "kms",
"resourceId": "key-phzz******jro04d",
"level": "INFO",
"instanceName": "instanceName",
"regionId": "cn-hangzhou",
"name": "Instance:Quota:Secret:70%",
"content": {
"eventId": "eventId",
"quota": "1000",
"kmsInstanceId": "key-phzz******jro04d",
"used": "700"
},
"status": "Normal"
}Description of the content fields:
Field | Description | Example |
eventId | The event ID. | 119***d |
kmsInstanceId | The KMS instance ID. | kst***pn8 |
quota | The total number of secrets. | 1000 |
used | Quantity used. | 700 |
Secret usage has reached 90%
{
"product": "kms",
"resourceId": "key-phzz******jro04d",
"level": "INFO",
"instanceName": "instanceName",
"regionId": "cn-hangzhou",
"name": "Instance:Quota:Secret:70%",
"content": {
"eventId": "eventId",
"quota": "1000",
"kmsInstanceId": "key-phzz******jro04d",
"used": "900"
},
"status": "Normal"
}Description of the content fields:
Field | Description | Example |
eventId | The event ID. | 119***d |
kmsInstanceId | The KMS instance ID. | kst***pn8 |
quota | The total number of secrets. | 1000 |
used | Quantity used. | 900 |