Before you can use Secrets Manager to manage Resource Access Management (RAM) secrets, you must authorize Secrets Manager to manage AccessKey pairs of RAM users. To perform the authorization, you can assign a RAM role with the required permissions to Secrets Manager. This topic describes how to authorize Secrets Manager to manage AccessKey pairs of RAM users.
Step 1: Create a custom policy
Log on to the RAM console as a RAM user who has administrative rights.
In the left-side navigation pane, choose .
On the Policies page, click Create Policy.
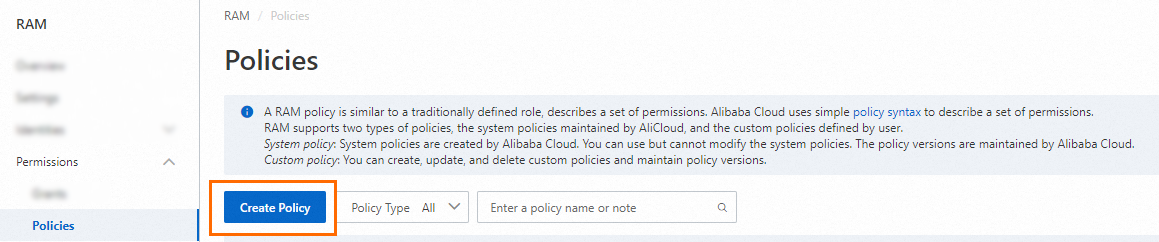
Click JSON and enter the following script:
{ "Statement": [ { "Effect": "Allow", "Action": [ "ram:ListAccessKeys", "ram:CreateAccessKey", "ram:DeleteAccessKey", "ram:UpdateAccessKey" ], "Resource": "*" } ], "Version": "1" }Optional. Click Optimize in the upper part and click Perform to optimize the policy.
The system performs the following operations during the advanced optimization:
Split resources or conditions that are incompatible with actions.
Narrow down resources.
Deduplicate or merge policy statements.
The optimized document may not be as expected.
Click OK.
On the page that appears, configure the Name and Description parameters, then click OK.
Set the Name parameter to AliyunKMSManagedRAMCrendentialsRolePolicy.
Step 2: Create a RAM role and attach the policy to the RAM role
Log on to the RAM console as a RAM user who has administrative rights.
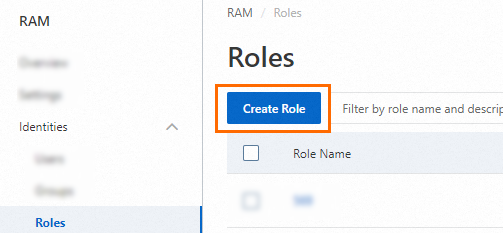
In the left-side navigation pane, choose .
On the Roles page, click Create Role.
On the Create Role page, set Principal Type to Cloud Service, select an Key Management Service for the Principal Name parameter, and then click OK.
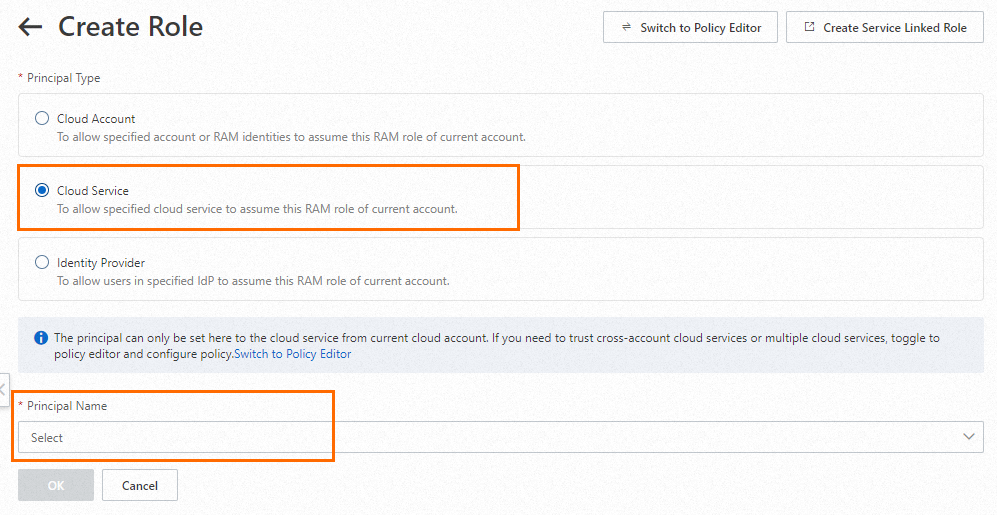
Set the Role Name parameter to AliyunKMSManagedRAMCrendentialsRole.
Click OK.
Select the Permissions tab and click Grant Permission to grant permissions to the role.
In the Grant Permission panel, click All Types and select Custom Policy.
Select the AliyunKMSManagedRAMCrendentialsRolePolicy
Click Grant permissions.