Alibaba Cloud IDaaS is an identity product from the Alibaba Cloud security team that is designed to be secure by default.
Design concept of security by default
In scenarios where it is difficult to balance availability and security, IDaaS prioritizes security while striving for maximum ease of use. Security requirements vary across industries. We cannot promise that the default configurations of IDaaS comply with the standards of all industries, nor do they imply absolute security. However, we always strive to provide the maximum out-of-the-box security.
Security is a lifeline. The enterprise identity system is a core component of information security and a primary target for external attacks. We strive to provide secure, trustworthy, and reliable identity services that meet high standards.
Example 1: Two-factor authentication is enabled by default
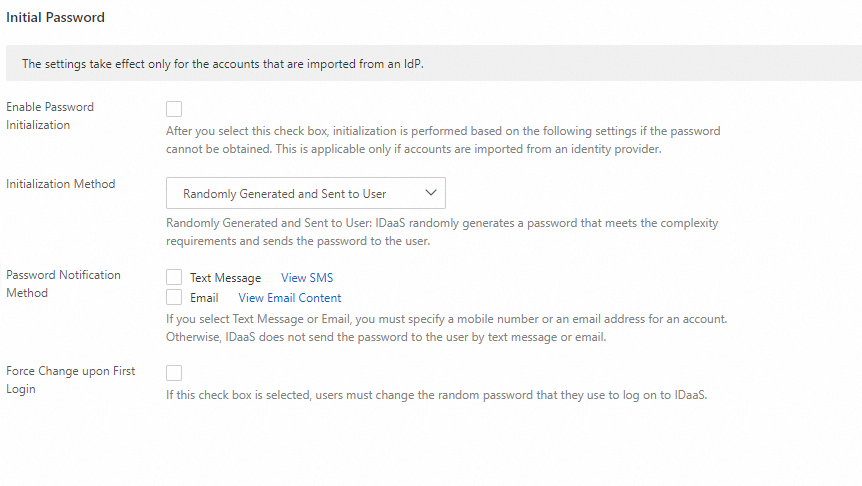
Although passwords have inherent security risks, they remain a primary identity verification method for many applications because they are convenient and easy to implement. Two-factor authentication is the most direct security measure for password-based authentication scenarios. After you log on with a password, you must perform an additional verification using a text message or email to access the service. To ensure the security of enterprise accounts, two-factor authentication is enabled by default for IDaaS instances. All accounts must use two-factor authentication to access applications. Access is granted only after the identity is confirmed. Therefore, all applications that are connected to IDaaS single sign-on (SSO) are immediately protected by IDaaS two-factor authentication.
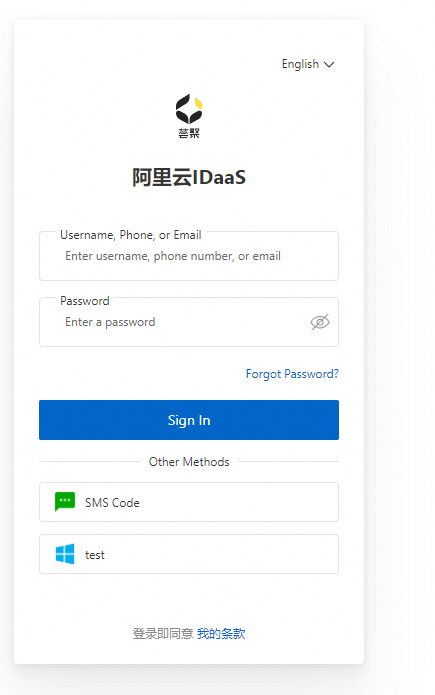
Advanced: Intelligent mode
To avoid the inconvenience of repeated two-factor authentication during multiple logons, IDaaS enables intelligent mode by default. Intelligent mode considers the current device, access environment, and account status to determine whether two-factor authentication is required.
If you are working normally, you may not need to use two-factor authentication for many days. This way, IDaaS ensures that secure logon is also easy to use.
Example 2: Risk control for management console operations
An administrator has far greater permissions than a regular user. If an administrator account is stolen, the resulting malicious behavior can cause a significant negative impact. When a sub-administrator performs sensitive, high-impact operations, the operations must be confirmed by the owner to ensure the situation is controllable and the process is compliant.
For key management operations, Alibaba Cloud IDaaS uses the risk control system developed by Alibaba Cloud over many years to determine the account status and access environment of the current administrator. If the operational risk exceeds the threshold, a risk control verification is triggered. This requires two-factor authentication using the mobile phone number that is attached to the Alibaba Cloud account.
IDaaS has preset risk control instrumentation for the following operations, which cover some of the most sensitive scenarios related to access, development, and data.
Delete an instance
Delete accounts in batches
Delete an application
Key rotation
... and more than 10 other types of operations
Example 3: Manual authorization for applications by default
When you use IDaaS for enterprise identity management, a core value, in addition to the convenience and security of SSO, is unified permission management. When all access is performed through IDaaS for SSO, you can easily assign application access permissions within IDaaS.
By default, Alibaba Cloud IDaaS requires all applications to be manually granted authorization.
No one can access a newly created application until an administrator specifies its authorization scope. Based on the principle of least privilege, this avoids the proliferation of application access permissions.
Example 4: Password policy security
When you must use a password to log on, a password security policy is essential. By default, IDaaS supports password-based logon. To ensure basic logon security, we recommend a set of common security configurations as the default configurations for instance initialization.
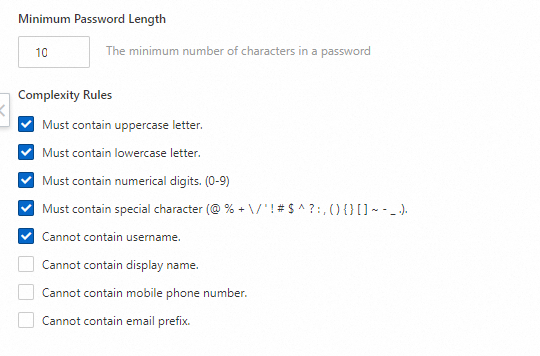
By default, we use a set of high-security complexity configurations to provide the highest possible standards for identity security. The default complexity requirements are as follows:
Must contain an uppercase letter
Must contain a lowercase letter
Must contain a number
Must contain a special character
Cannot contain the account name.
You can adjust this policy to achieve a balance between business requirements and security.
Example 5: Default signature and encryption
When you make a cross-origin request, its security during network transmission cannot be 100% guaranteed, even if you use HTTPS.
To achieve true end-to-end security protection, IDaaS provides an additional signature layer and encryption layer at the business layer. These layers are built on top of the global use of HTTPS and are enabled by default.
Signature layer: When a cross-origin request is made, the request content is signed with a private key. This allows the receiver to use a public key to verify that the information was not tampered with during transmission. This method is used in some SSO and outbound account synchronization scenarios.
Encryption layer: This layer supports end-to-end encryption and decryption of synchronized information. By default, data is encrypted before synchronization, and password information is not synchronized. This helps prevent information leakage that could be caused by negligent operations. In the future, full-process encryption of SAML SSO will be supported, which will allow SSO to meet the high-level security requirements of the finance and government sectors.