When Security Assertion Markup Language (SAML) is used for single sign-on (SSO), the identity credentials of a user are passed to the NameID field of SAMLResponse or exist in other fields.
When you configure an application user, you need to specify the type of value to be used as the identity credentials of the account.
The most common choice is IDaaS Account Name or IDaaS Email.
SSO configuration items
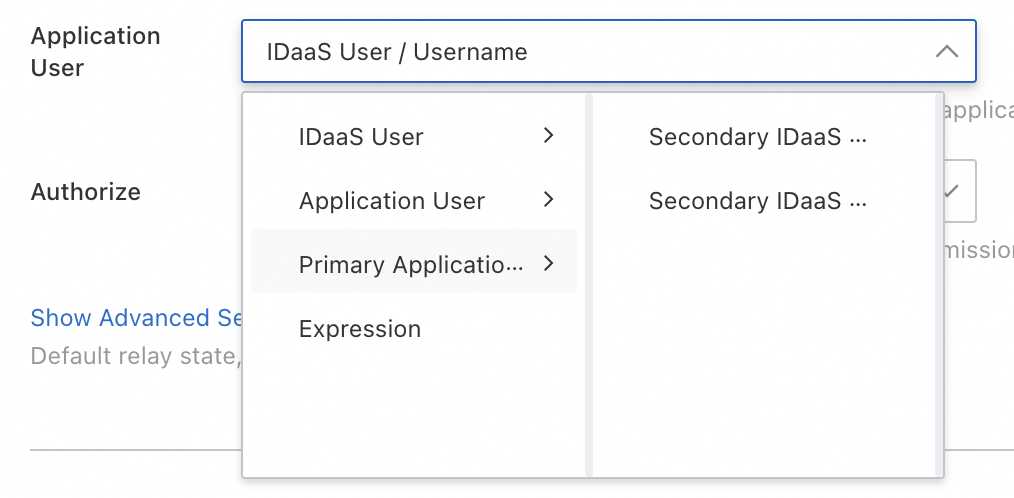
You can choose from the following four options.
Option | Description |
| When a user initiates a single sign-on request to the current application, the IDaaS account information is used as the identity credentials of the application. If you select this option, make sure that the account for SSO has the same username in IDaaS and in the application. Otherwise, logon may fail or account mismatch may occur. This is the most common configuration. This eliminates the need to configure a separate application account for each IDaaS account, saving time and effort. Two sub-options are provided:
|
2. Application user | An administrator must specify the application account that is used by each IDaaS account during the SSO to the current application. If this parameter is not specified, SSO cannot be performed. For example, if the test_user account exists in IDaaS and you want to log on to the application as an administrator, you can configure the application user. For more information about how to configure application users, see Add an application user. If the application has a small number of users, you can use this configuration to maximize flexibility. One sub-option is provided:
|
3. Primary application account | This option combines the advantages of the first two options. It allows administrators to configure application users and use the application users in preference. For more information about how to configure application users, see Add an application user. By default, if no application user is configured, the IDaaS identity credentials are used. Two sub-options are provided:
|
4. Expression | If the application user has specific rules, you can configure expressions. For example, the application uses the email prefix of each user as the user name. No sub-option is provided. Because expressions are complicated, contact the IDaaS team for configuration. You can enter an expression rule. |
Add an application user
If you select Application User or Primary Application User from the Application User drop-down list on the SSO tab, you can configure the identities used by different accounts when the accounts access the application.
Click the Application Account tab and then click Add Application Account. A dialog box appears.
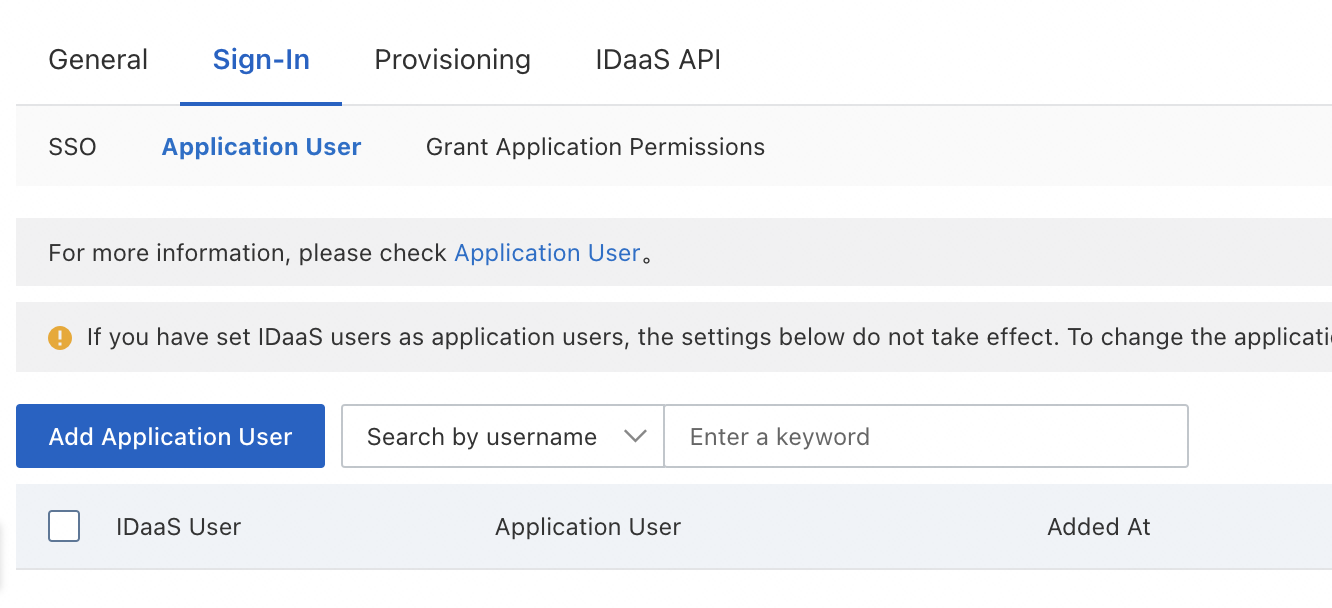
Search for the IDaaS account you want to manage by entering a keyword such as admin, root, mobile number, or Jerry. After you find the IDaaS account, click the account and add an application account for the account. Click Save to complete the configuration.
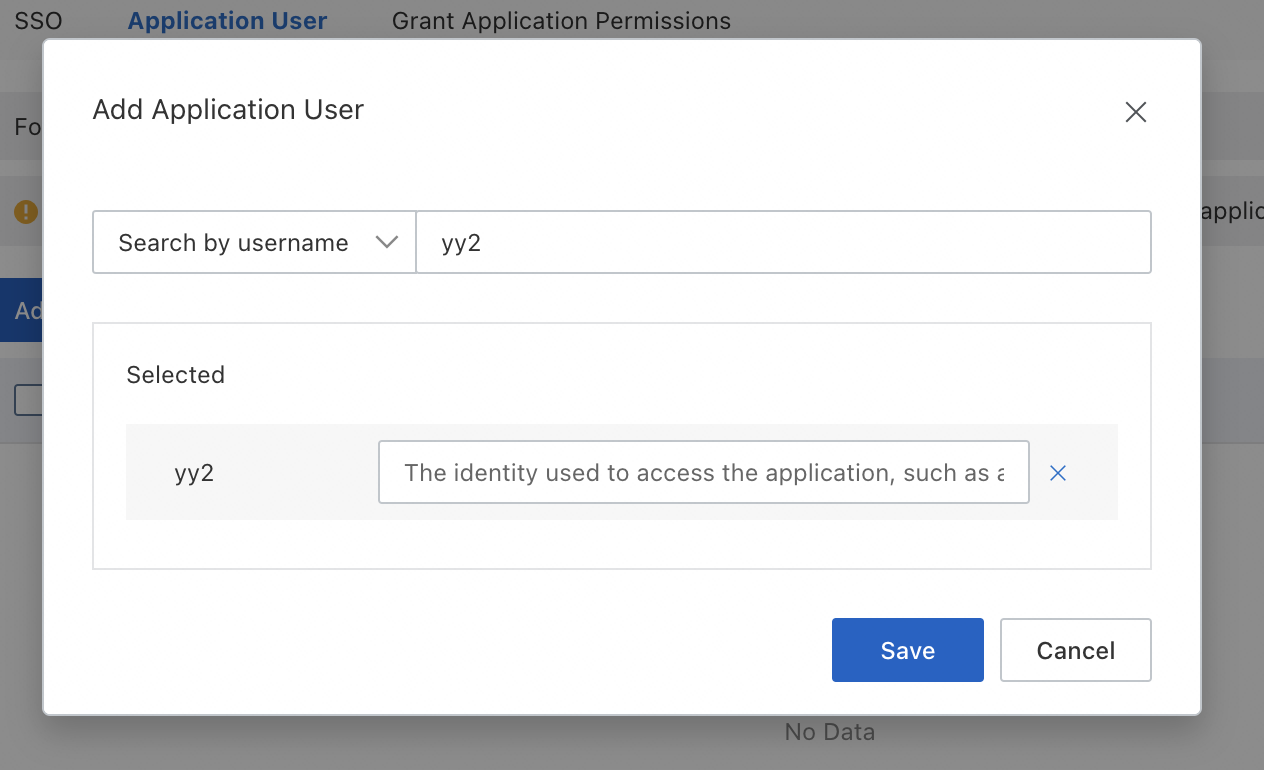
You can configure multiple application accounts for an IDaaS account. When a user initiates an SSO request, the user can select one of the configured application accounts to log on to the application.