Edge Node Service (ENS) instances can connect to each other using Elastic Network Adapters (ENAs). You can also establish a connection by deploying a FortiGate virtual appliance—a third-party Network Virtual Appliance (NVA). You can use a similar solution to connect ENS to an Internet Data Center (IDC) or an ECS instance.
Overview
This document outlines how to install and deploy a FortiGate virtual appliance on ENS to establish a VPN connection between the Virtual Private Clouds (VPCs) of different ENS nodes. The process includes four main steps:
Scenario description
Install FortiGate
Configure FortiGate
Test connectivity
Scenario description
When you use ENS nodes, you can interconnect them over a Wide Area Network (WAN) using dedicated private lines or a VPN. This guide focuses on the VPN interconnection method.
To begin, plan your IP address spaces. To verify the connection at the end of this guide, use `ping` tests between VM1 and VM4.
1. IP address planning
ENS VPC | CIDR block | Instance | Private IP | Public IP |
ENS VPC1 | 10.0.100.0/24 | VM2 (FortiGate deployed) | 10.0.100.2 | Assign during instance creation or associate an EIP |
VM1 | 10.0.100.3 | |||
ENS VPC2 | 172.16.100.0/24 | VM3 (FortiGate deployed) | 172.16.100.2 | Assign during instance creation or associate an EIP |
VM4 | 172.16.100.3 |
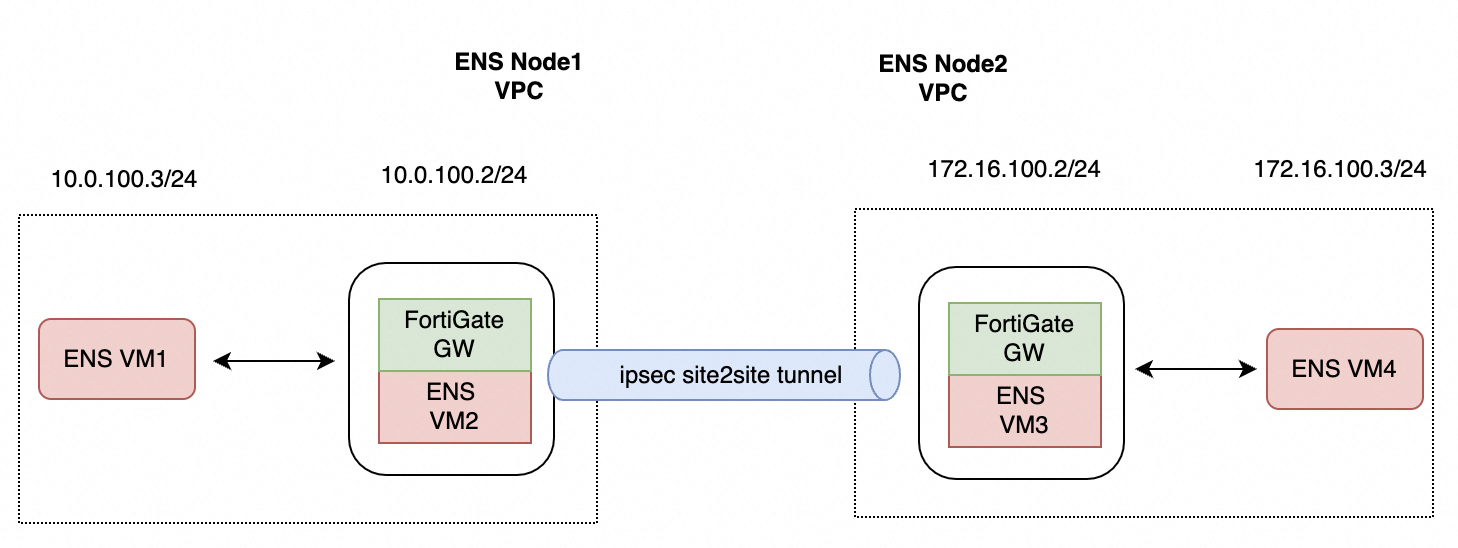
2. Network topology
The network topology is shown in the following diagram. You have a VPC in ENS Node 1 and another in ENS Node 2, each containing its own instances. The objective of this guide is to establish private network connectivity between "ENS VM1" and "ENS VM4".
Install FortiGate
This section explains how to create the necessary VPC, vSwitch, security group, and instance resources in the ENS console to deploy the FortiGate appliance. This process involves four steps:
Create a VPC and vSwitch on ENS
Configure a security group
Deploy the FortiGate instance
Deploying the traffic steering configuration
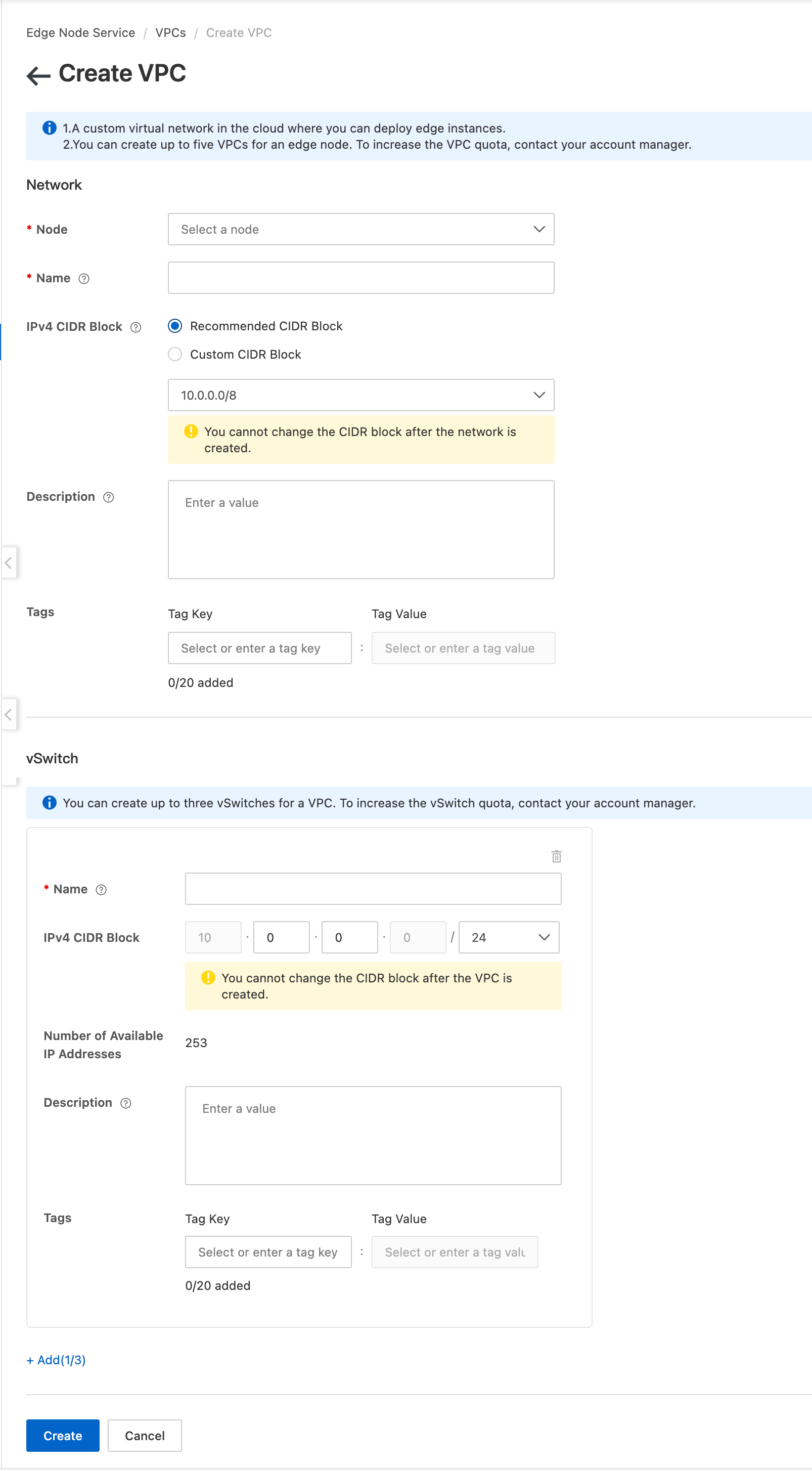
1. Create a VPC and vSwitch on ENS
Log on to the ENS console and choose . Select a Node, enter a Name and an IPv4 CIDR block, configure the vSwitch, and specify a subnet.
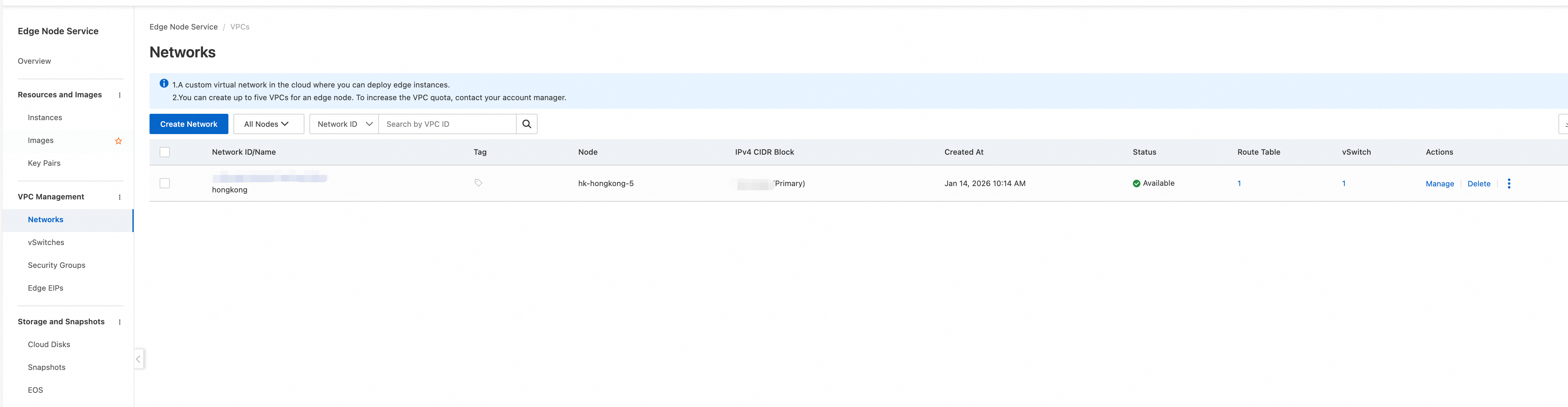
After you click Create, navigate to the Networks and vSwitches pages to verify that the new VPC and vSwitch are in the lists.
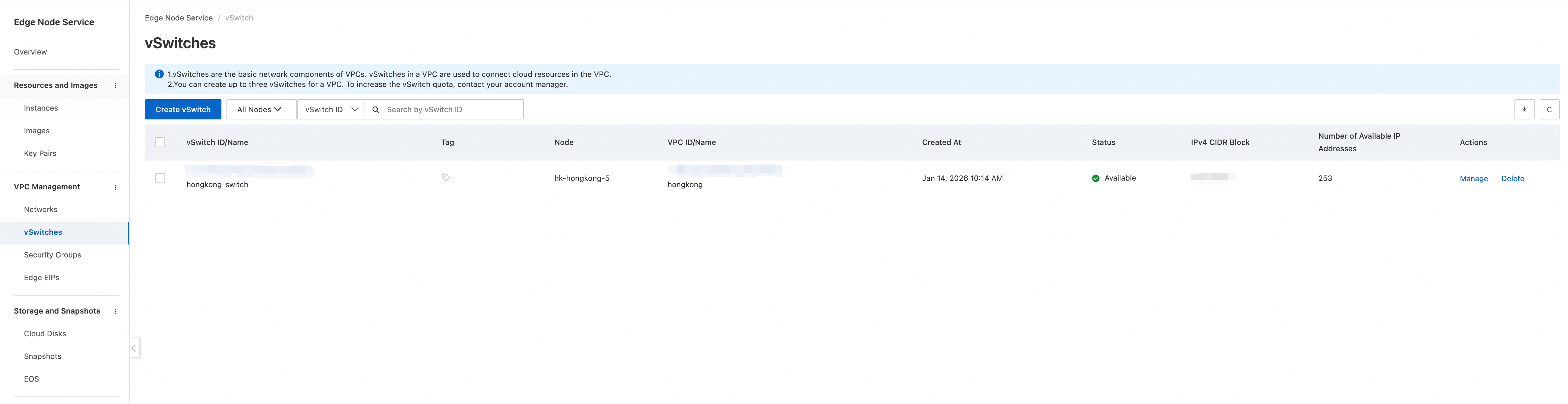
2. Configure a security group
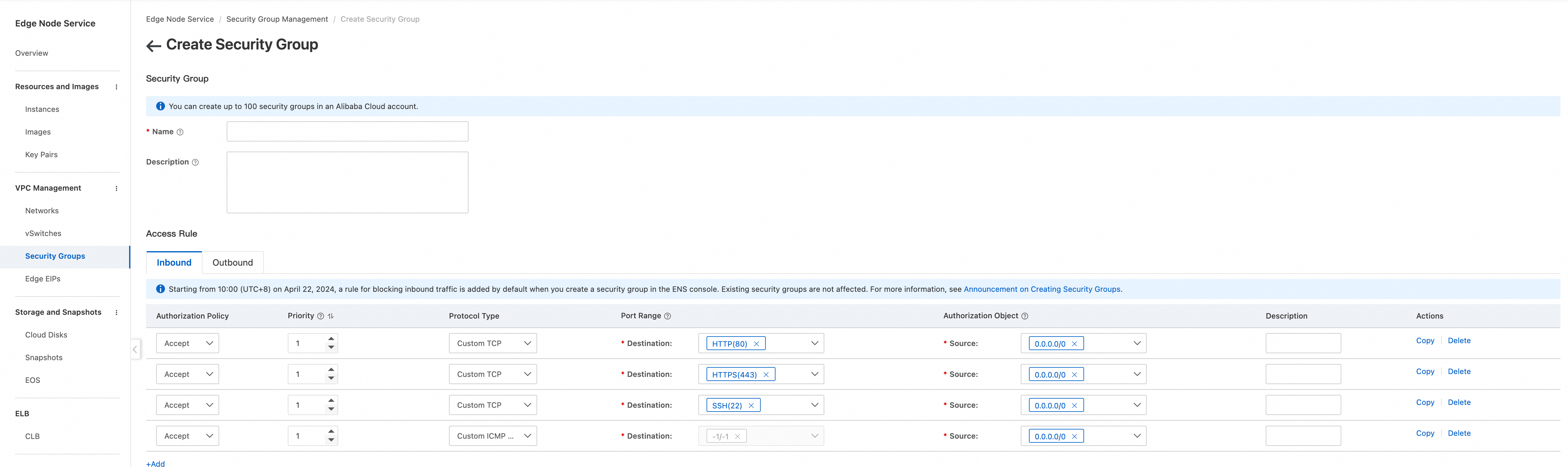
By default, security groups block most inbound traffic. You must create rules to allow specific traffic. For simplicity, this guide creates a rule that allows all inbound traffic. In a production environment, you must follow the principle of least privilege and allow only required traffic, such as SSH, ICMP, HTTPS, and the UDP ports necessary for IPsec.
Choose .
Configure the Outbound direction, which allows all traffic by default.
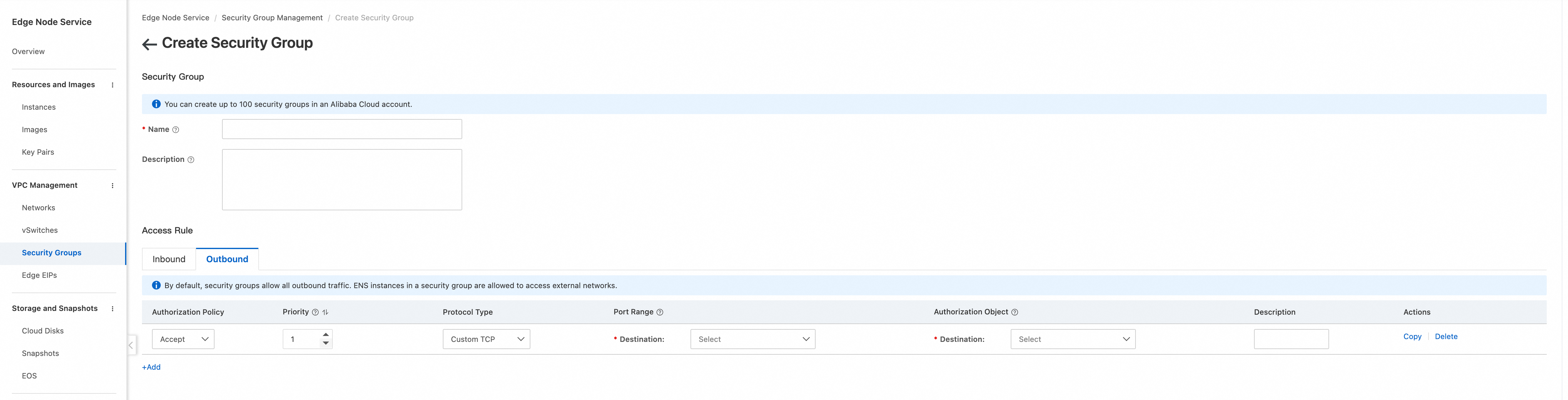
3. Deploy the FortiGate instance
This step explains how to create the FortiGate instance in the ENS console. This instance, corresponding to VM2 in the topology diagram, will act as the NVA to handle VPN traffic.
Choose and click Create Instance.
In the Basic Configurations section, set Instance Type to X86 Computing. For more information about Instance Type, see the FortiGate Specifications Reference. Set Image to Custom Image and select the prepared FortiGate image. For more information about creating a custom image in ENS, see Create a custom image.
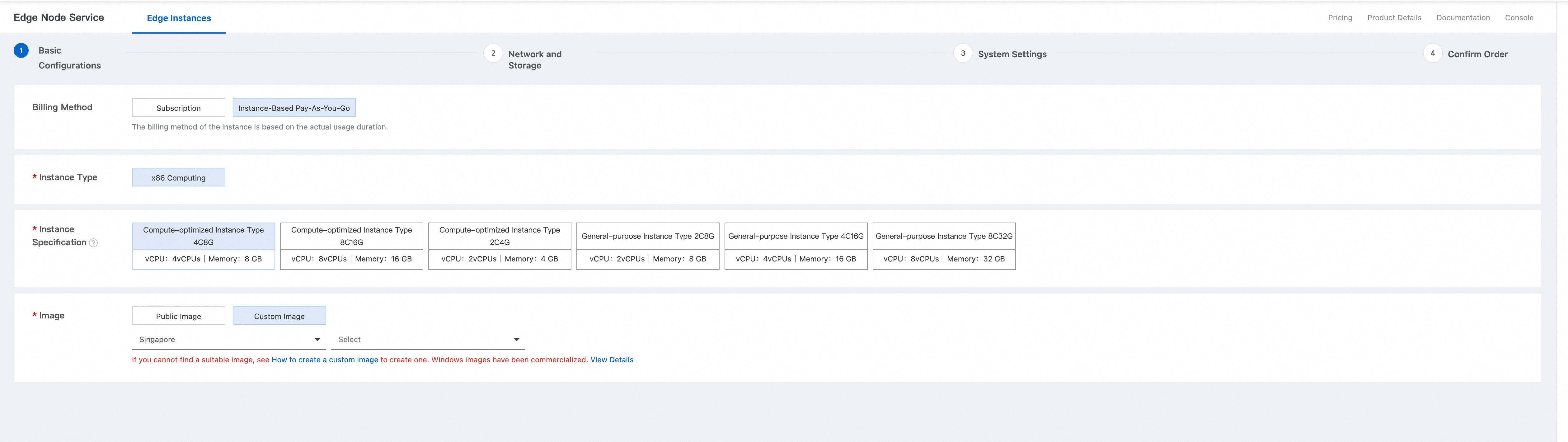
Configure Network and Storage. Set Network to Self-built Network. For Region, select the region where the VPC is located. Then, set the Network, vSwitch, and Security Group for the node. You must also select Create a Public NIC and set a Max Bandwidth.
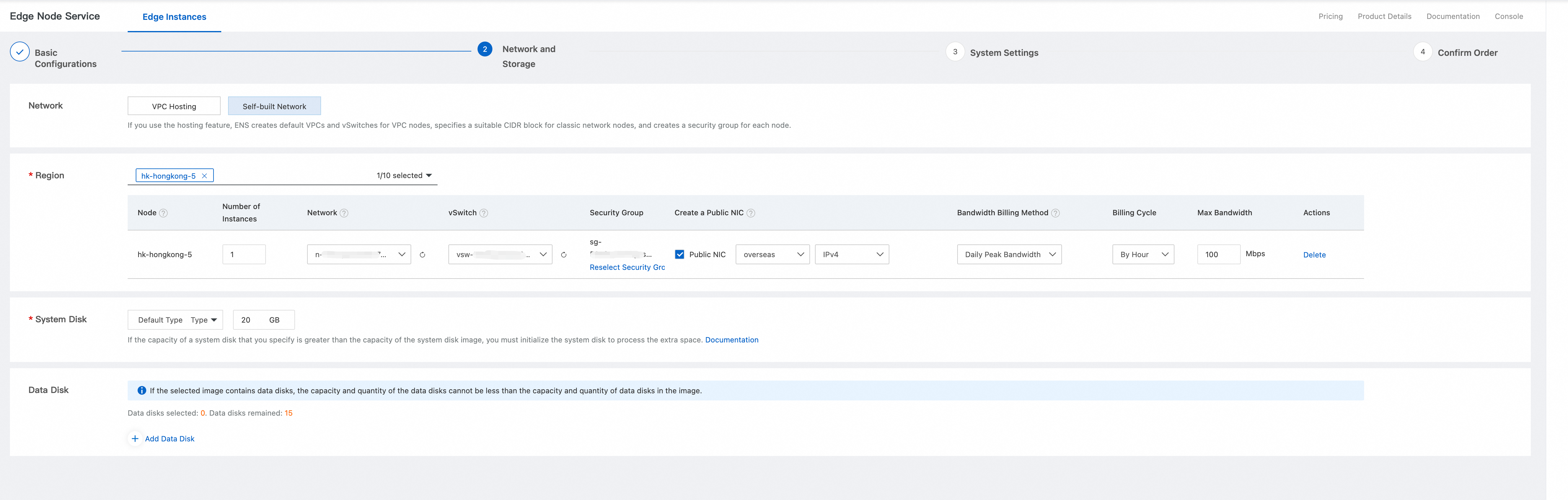
In the System Settings section, you can set the key and instance name. For information about the default password, see the official FortiGate documentation.
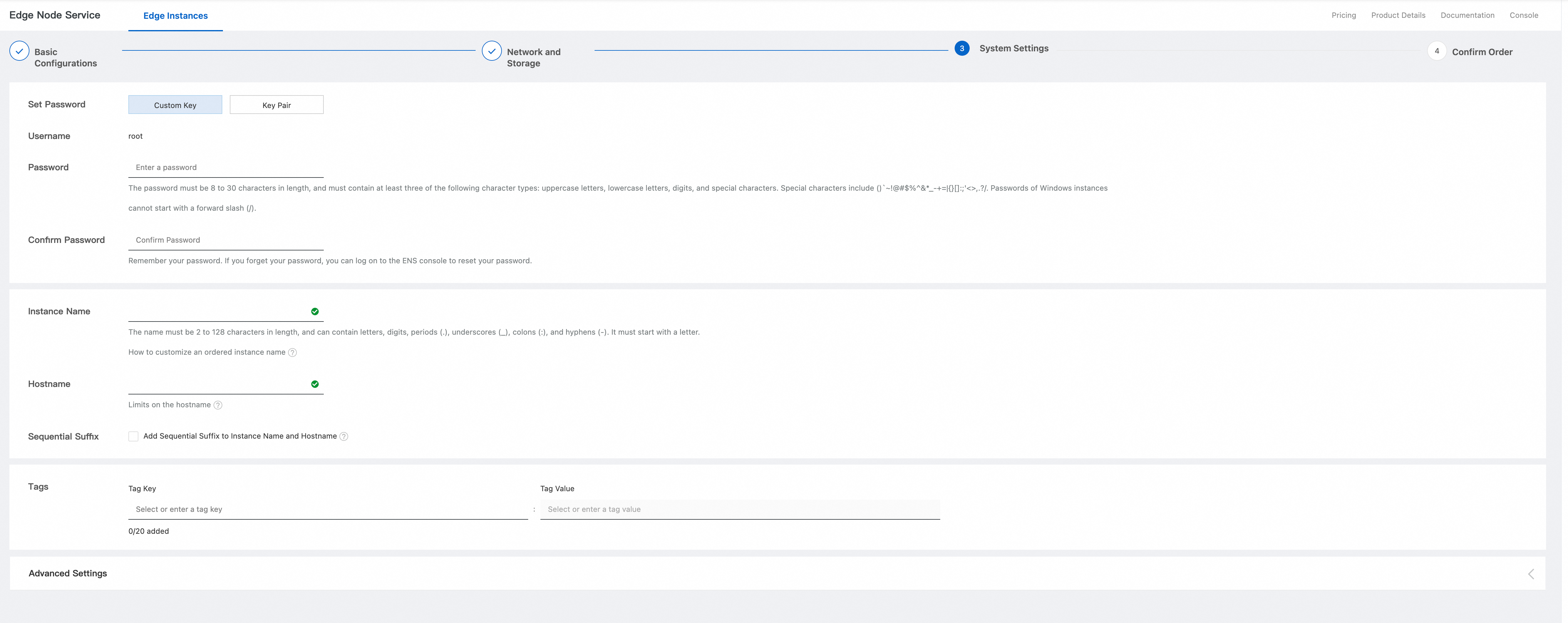
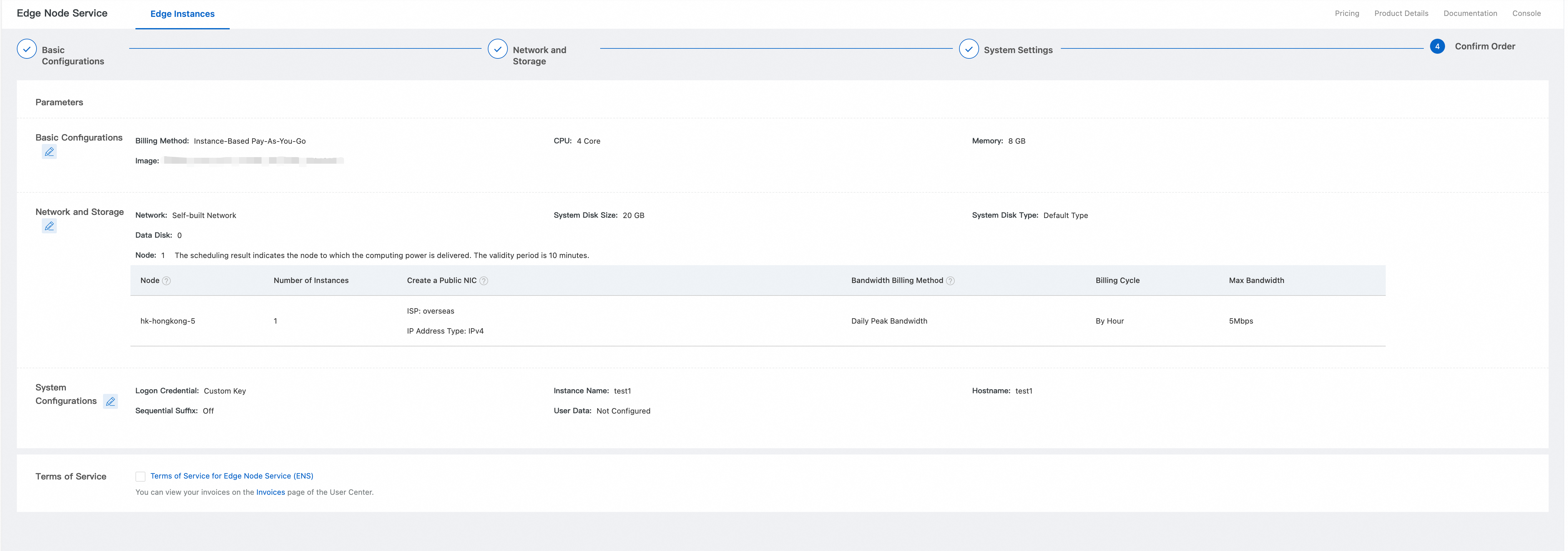
Confirm the order. Review the Basic Configurations, Network and Storage, and System Configurations sections. Select the Subscription Duration, and then click Confirm Order.
After the instance is created, check the instance list to verify that the instance was created.
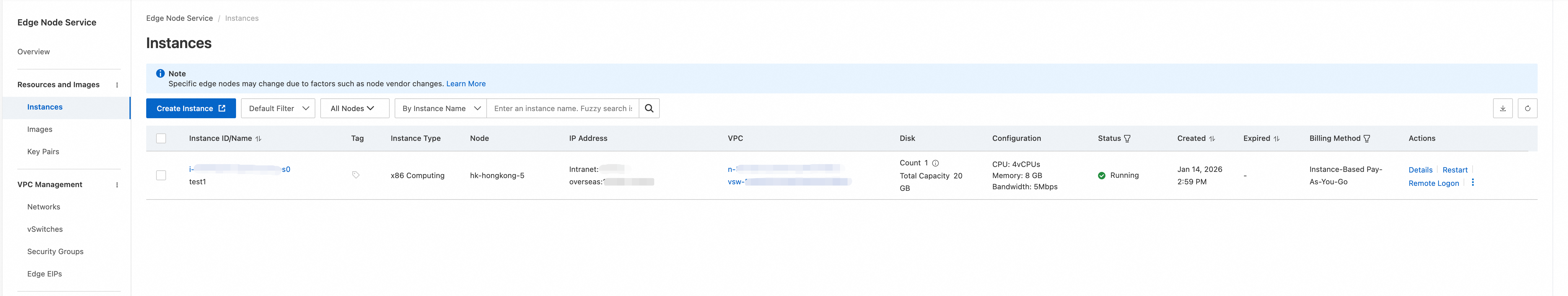
The preceding steps describe how to create VM2. For verification purposes, you can create another VM in the same VPC. However, do not select the FortiGate image for this VM.
4. Configure traffic routing
Using the first ENS node as an example, route traffic from VM1 destined for VM4 through the FortiGate appliance (VM2). This ensures the traffic enters the VPN tunnel. To do this, add a custom route to the VPC's route table.
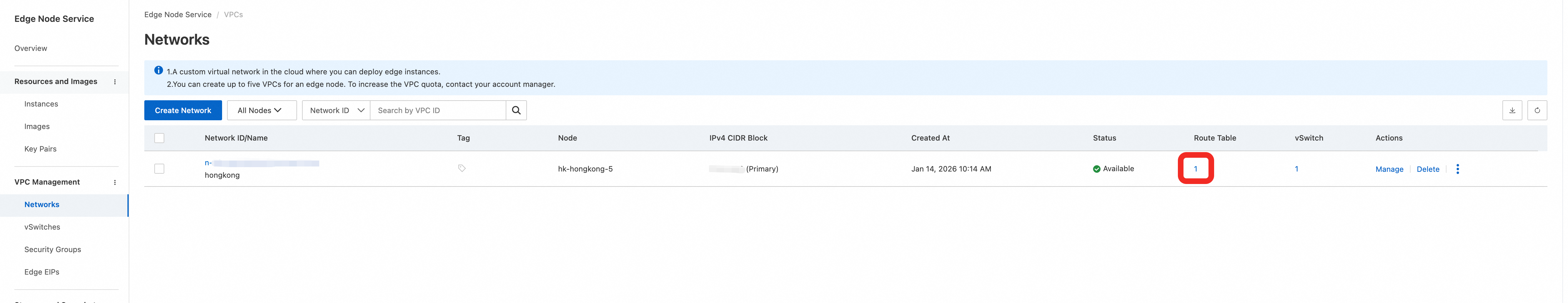
Choose . In the network list, select the network that you created and click its route table.
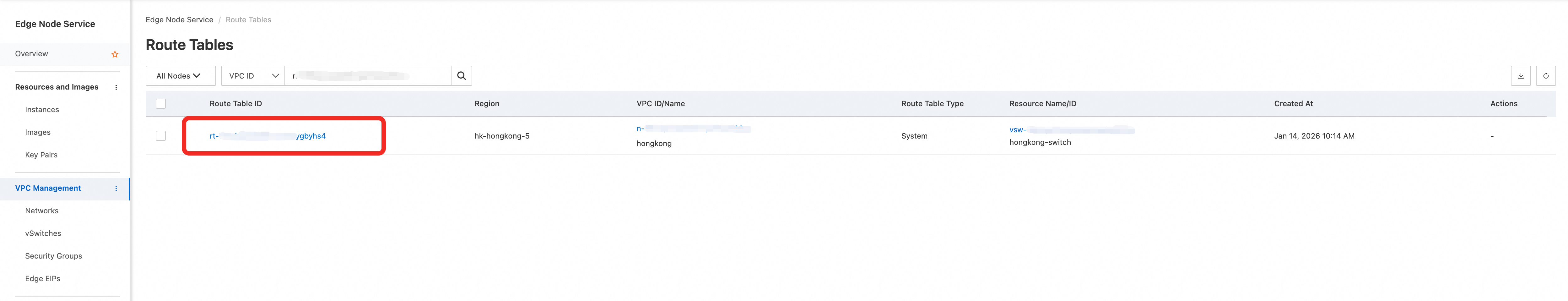
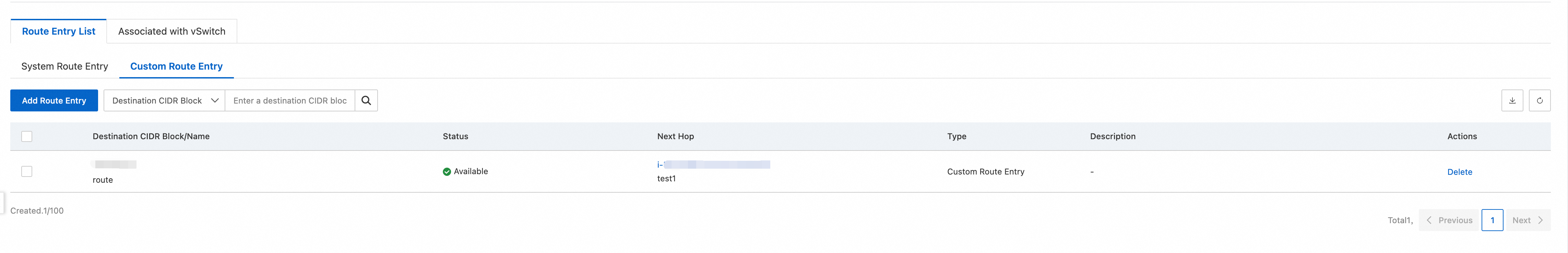
Click the route table ID. In the route table details, choose . Configure the destination IPv4 CIDR block and set the next hop to the FortiGate instance that you configured.
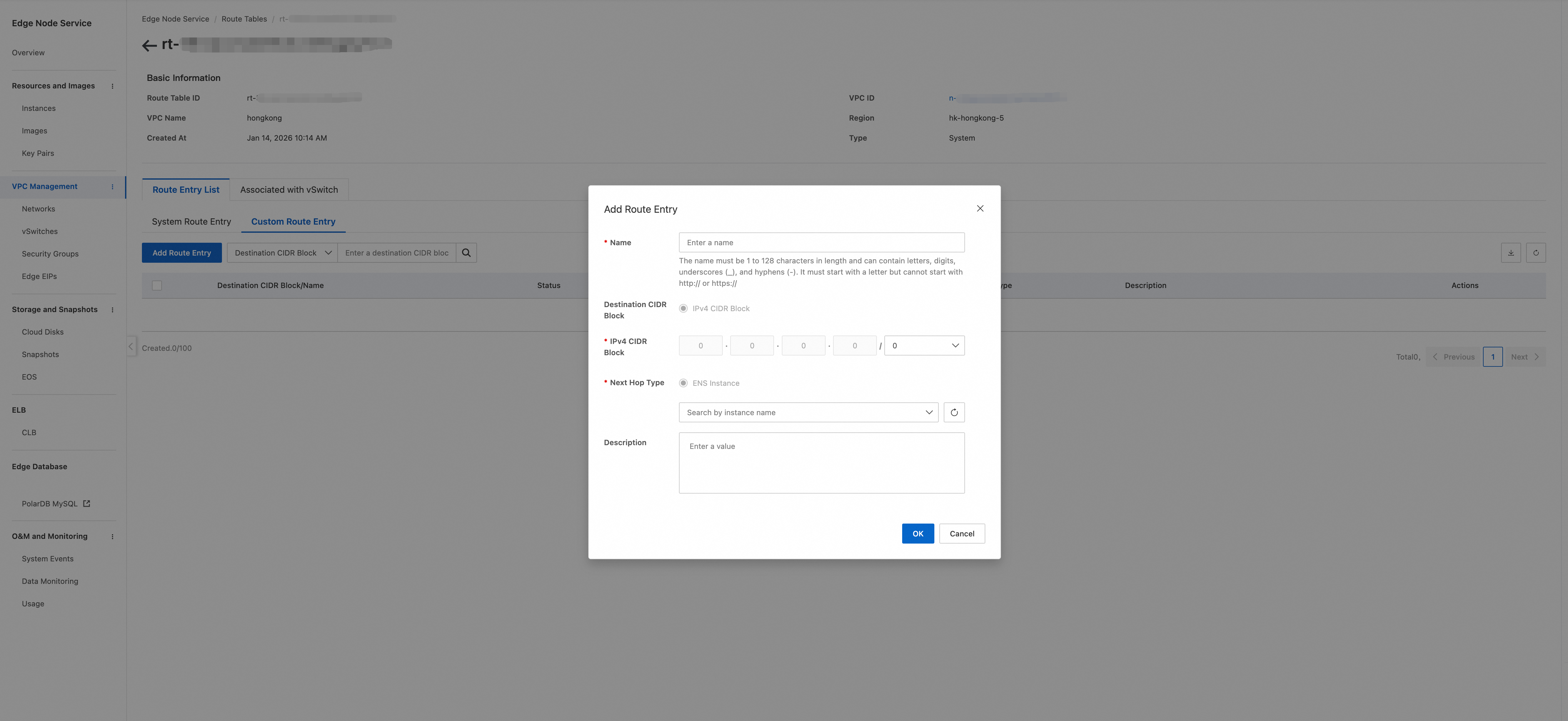
After the configuration is complete, the interface appears as shown in the following figure. This indicates that traffic is directed to the FortiGate instance.
5. Configure the Site2 VPC and FortiGate
Create a second VPC and assign a subnet.

Create and configure the FortiGate instance.
Add the routing rule.

Configure FortiGate
For instructions on how to configure FortiGate, see the official documentation. Minor differences may exist between versions. For more information, see https://handbook.fortinet.com.cn/.
The configuration process involves the following steps:
Notes
Import the license
Network initialization
System initialization
Network check
Configure IPsec
1. Notes
In the Chinese mainland, an ICP filing is required for Internet access over HTTP and HTTPS. Ports 80 and 443 are blocked without a valid ICP filing.
Log on to the FortiGate device using Secure Shell (SSH). Change the HTTPS port number, and then complete the ICP filing.
The following command changes the port to 8443:
config system global
set admin-sport 8443
end
2. Import the license and initialize the system
After you import the license, perform a basic initialization. Configure IPsec only after you verify that the network configuration is active.
2.1 Import the license
The default initial account credential is the username `admin`. To prevent security threats, change the default password as soon as possible after the configuration is complete.
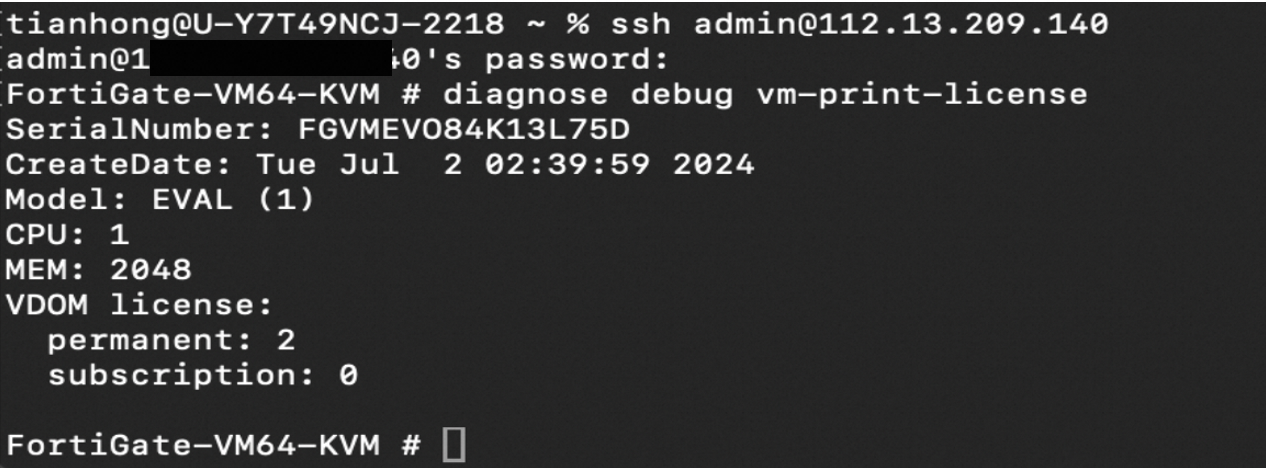
You must bind a FortiGate license. This topic uses the Bring Your Own License (BYOL) method.
The device automatically restarts after the license is imported. You must log on again after the restart to begin the IPsec configuration.
2.2 System initialization
After the restart, enter the IP address in your web browser to access the console. You must access FortiGate over HTTPS.
Perform the standard initialization configuration.
For the initial deployment, you can upgrade to the latest version, such as 7.4.X, or consult the vendor. Newer versions can reduce the need for manual configuration, such as when you configure IPsec. Then, log on to the console.
The system must be initialized before you can proceed. In the navigation pane on the left, choose settings and configure parameters such as the hostname and time zone.
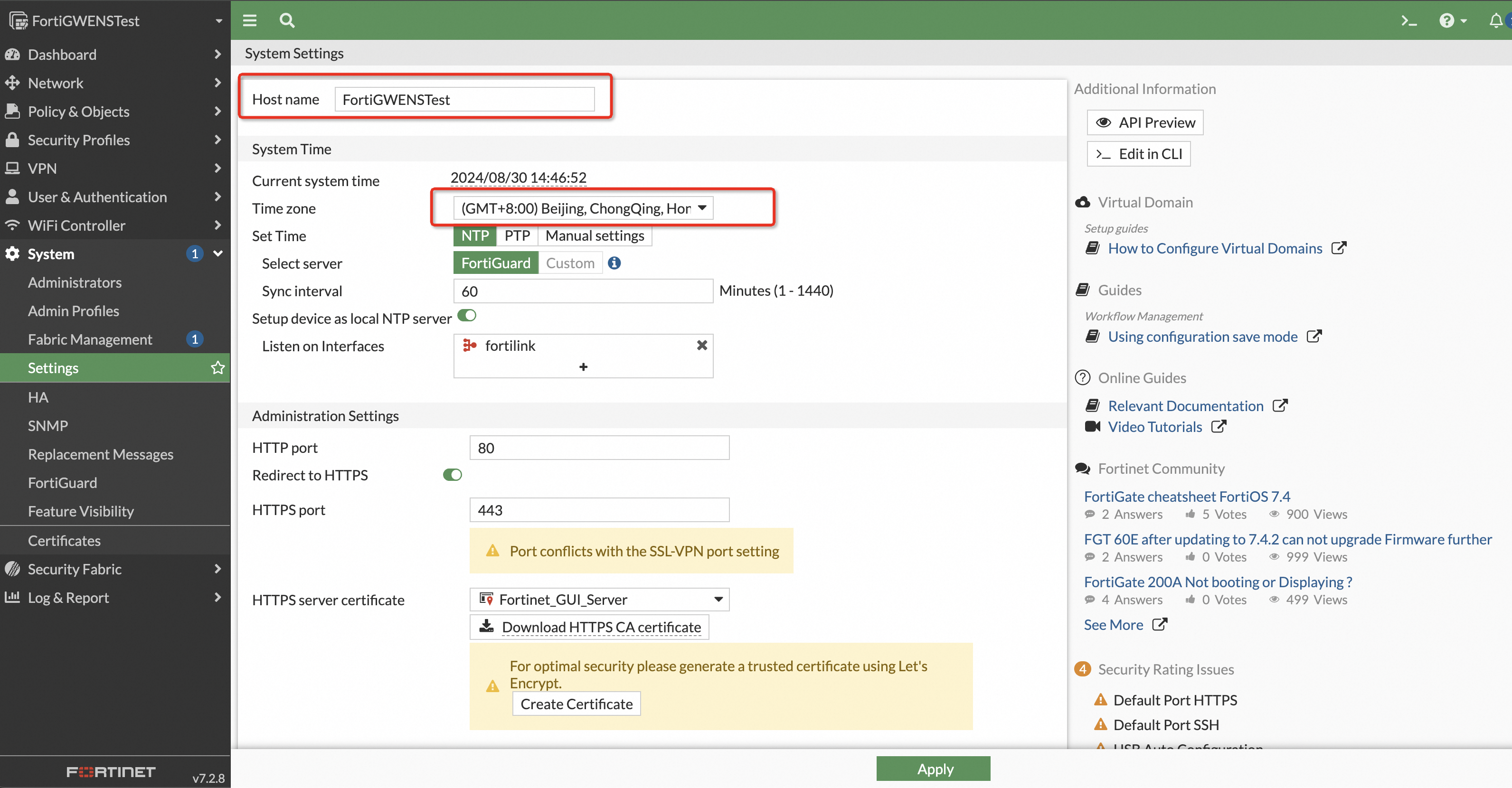
2.3 Verify that the network configuration is active
Ping the local machine at
ping 10.0.100.2.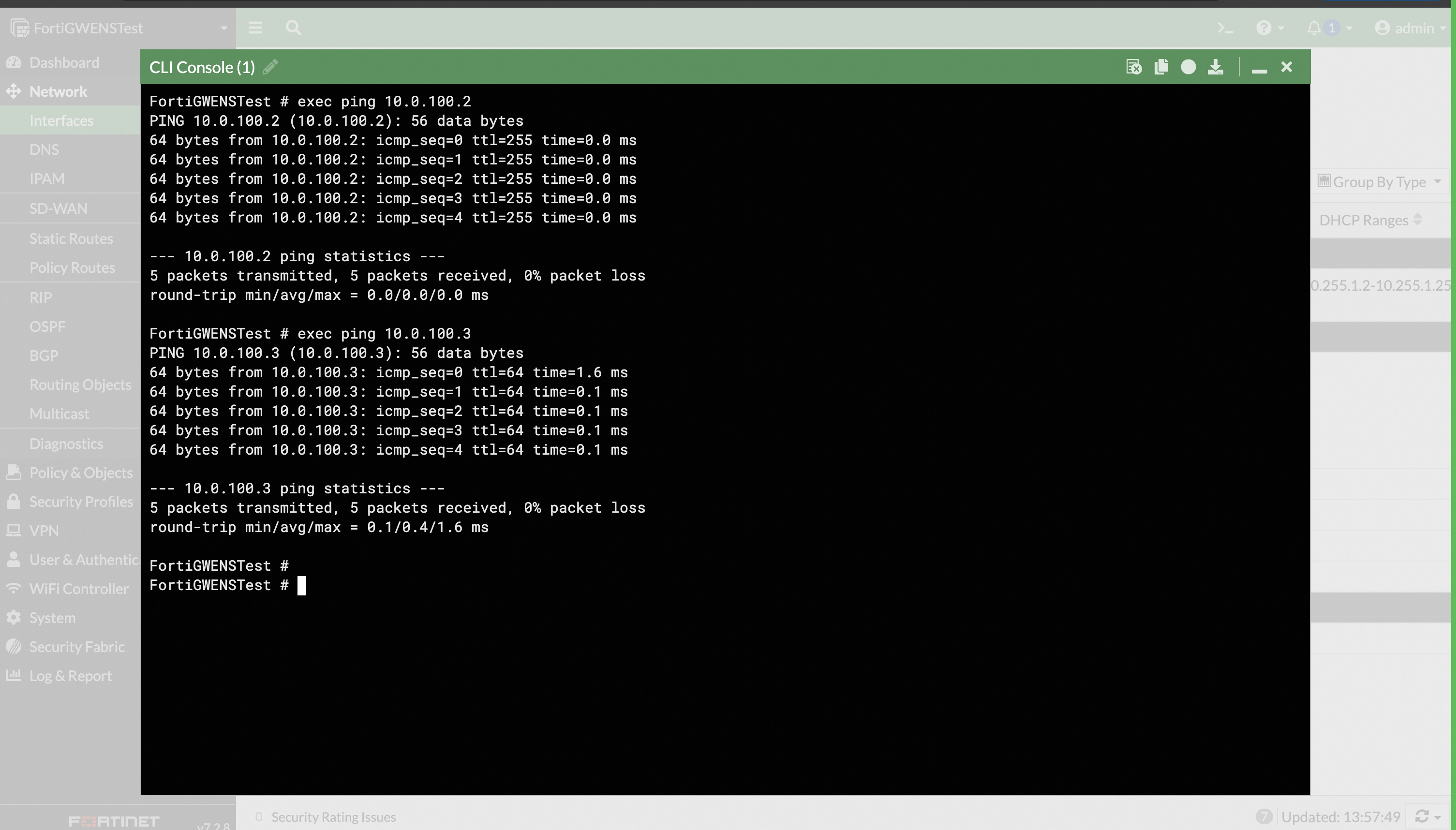
Ping the VM in the same VPC at
ping 10.0.100.3.
Run
ping www.aliyun.comto check whether the Internet connection is working correctly.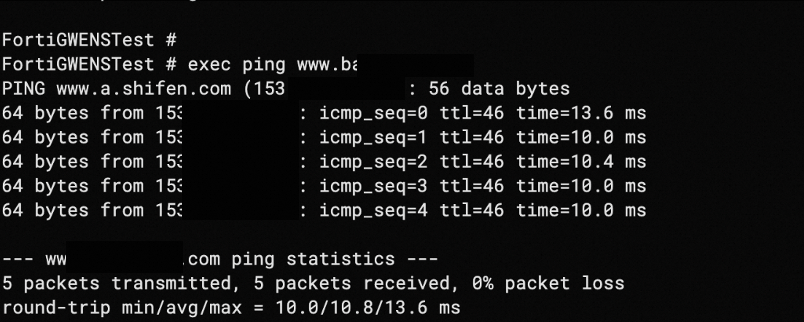
You have now completed the basic configuration of FortiGW on ENS.
3. Configure IPsec
You can configure IPsec in several ways. For this topology, use a Site-to-Site deployment. This deployment enables VPN connectivity between VM1 and VM4. The two endpoints are defined as Site1 and Site2.
3.1 Site1 configuration
Follow the steps in the configuration wizard to complete the configuration:
In the navigation pane on the left, choose VPN > IPsec Tunnels and click Create New. Then, click IPsec Tunnel.
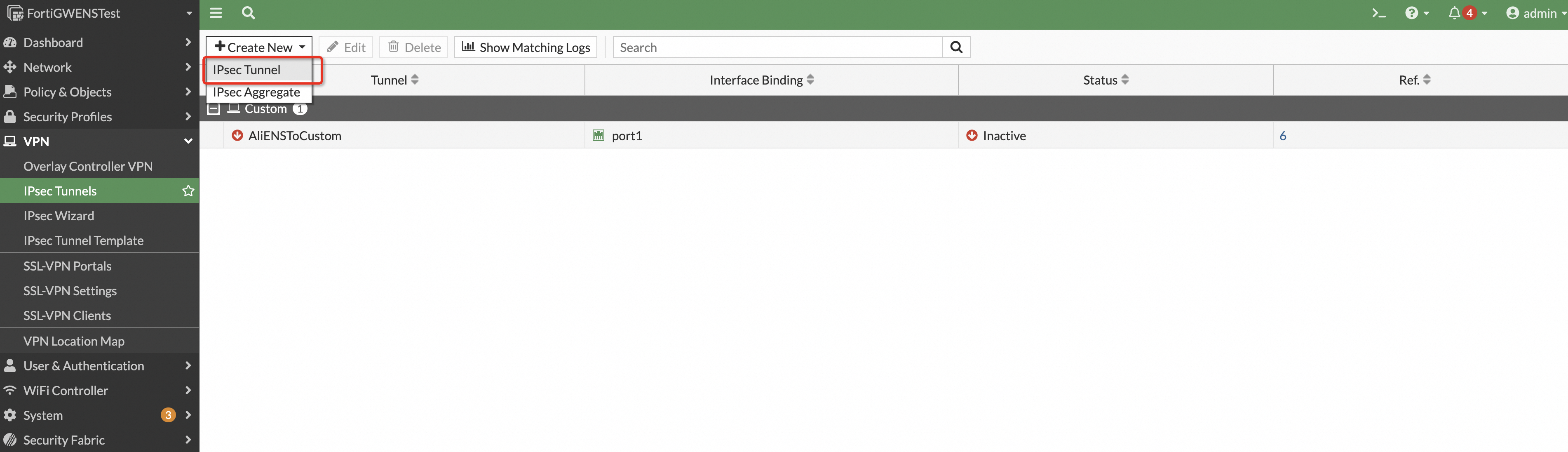
Enter a name and select Site to Site as the template type.
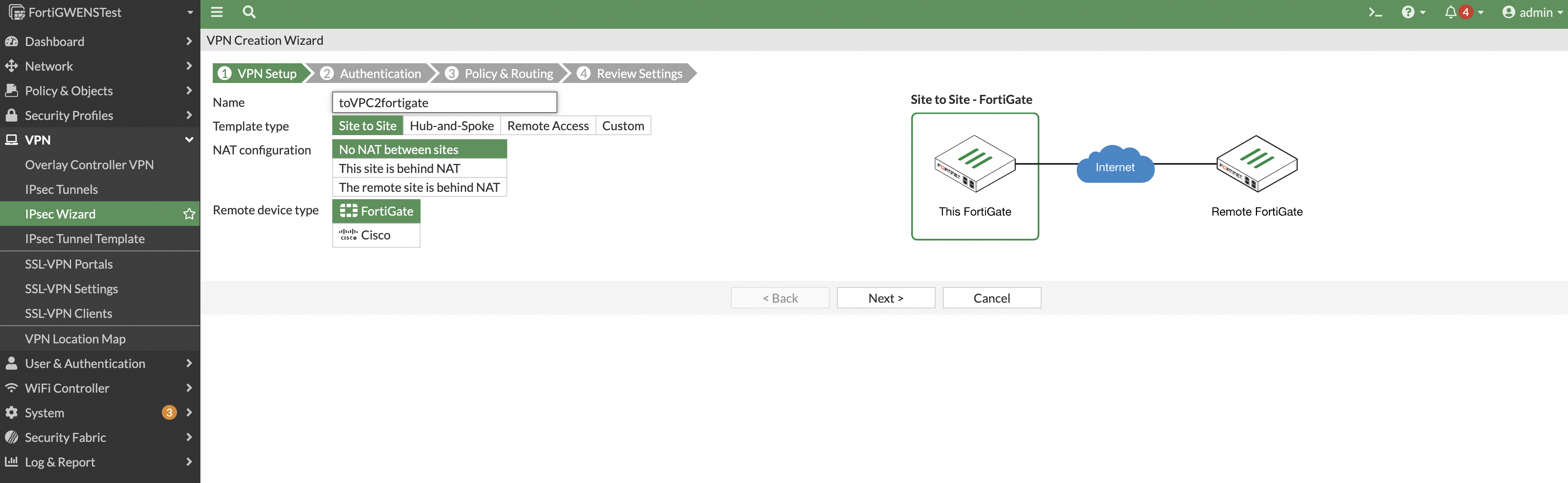
You can configure the interface and the shared key.
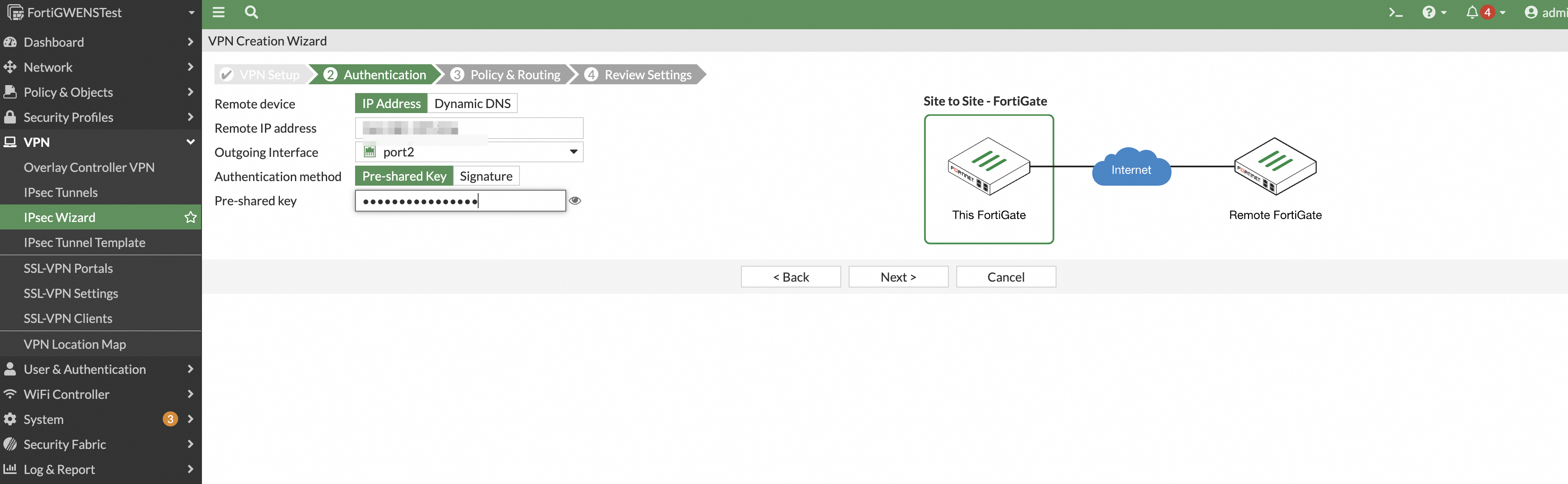
Configure the local and remote subnets for the private network.
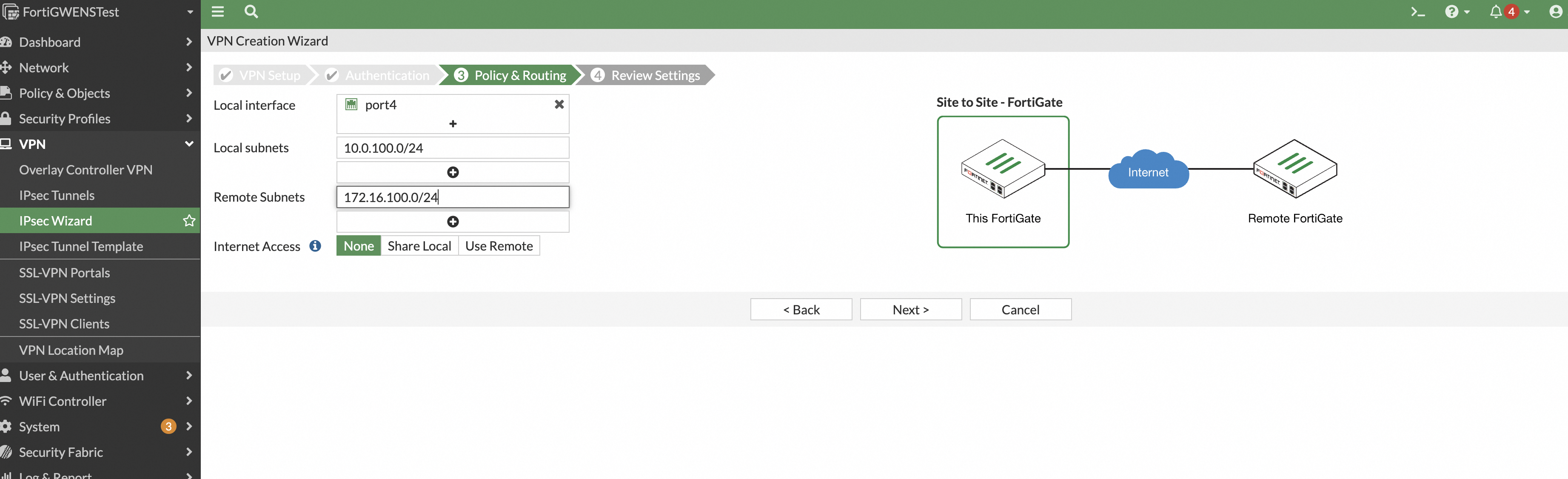
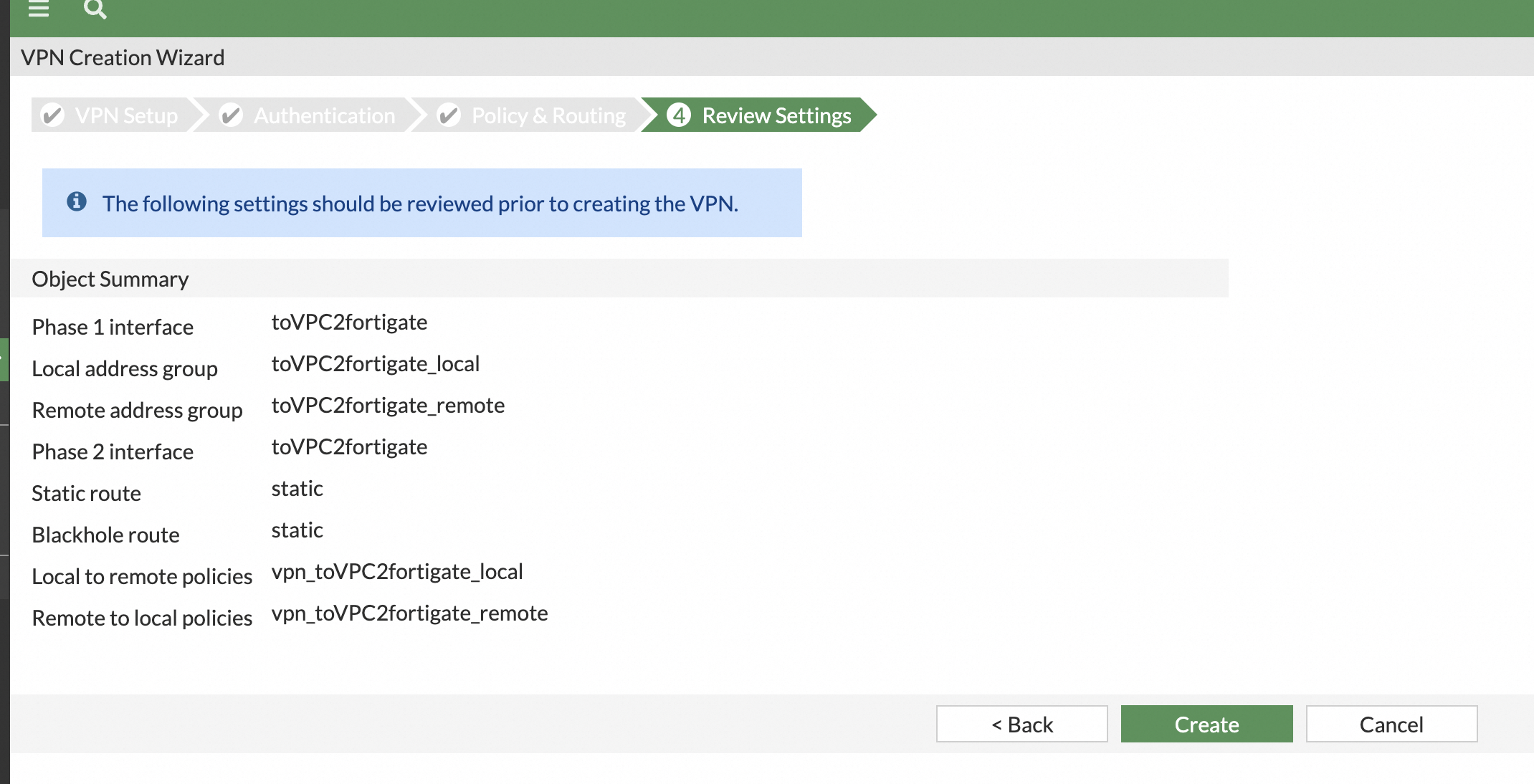
Click Create, verify that the information is correct, and then click Create.
Configure the firewall policy. In the Policy & Objects section, create a firewall policy to allow traffic from the private network to the IPsec VPN tunnel and from the IPsec VPN tunnel to the private network. This step may differ between versions. In later versions, this policy is automatically configured by the VPN configuration template. For more information, see the official FortiGate manual.
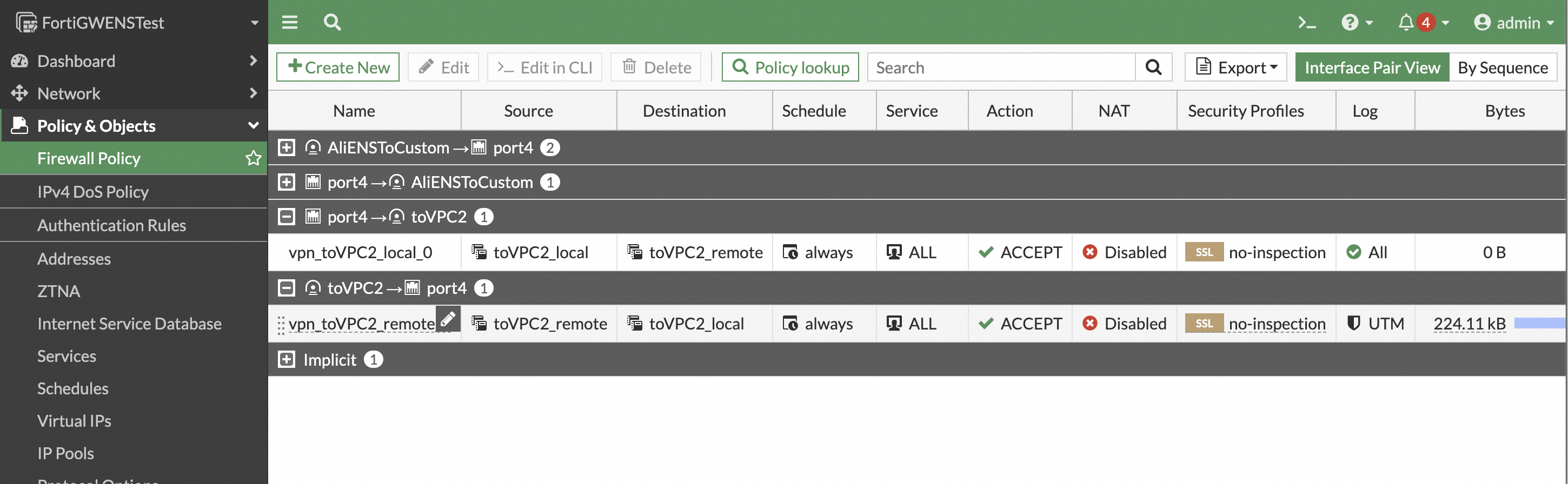
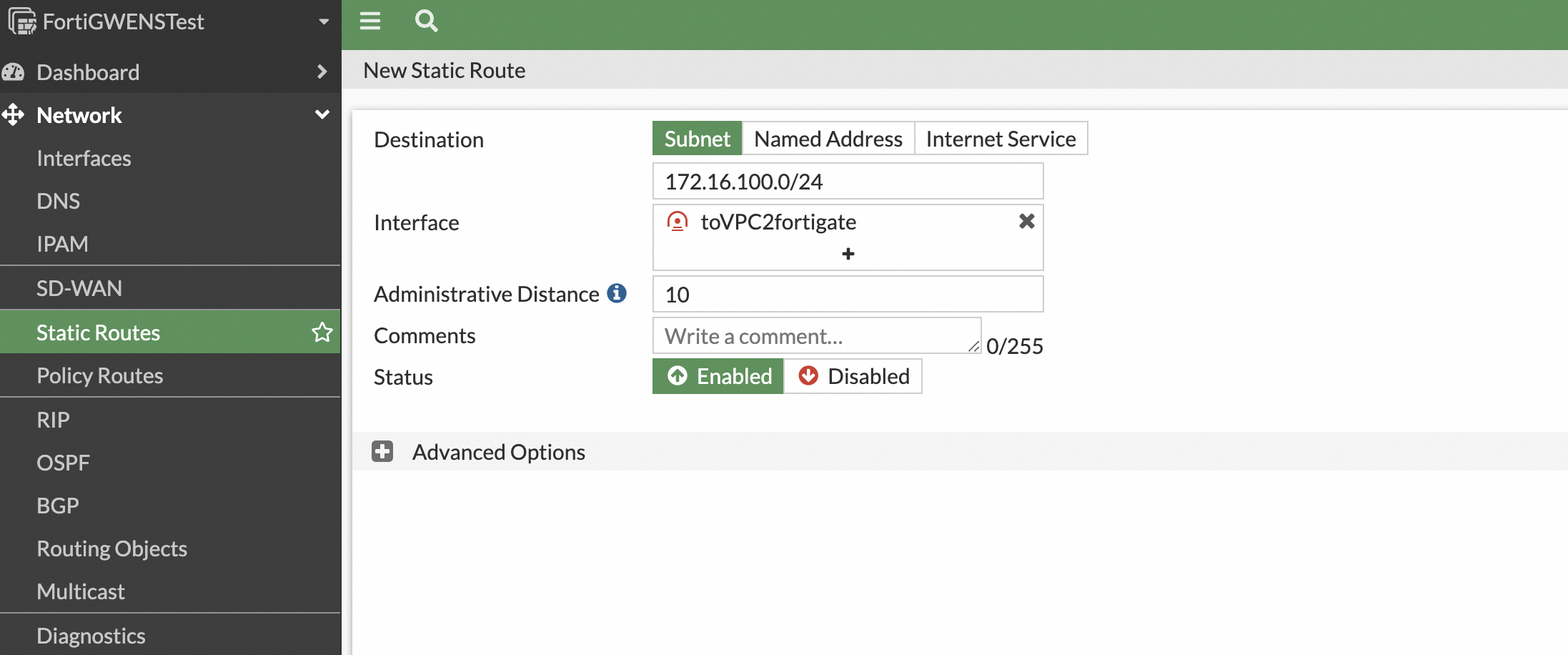
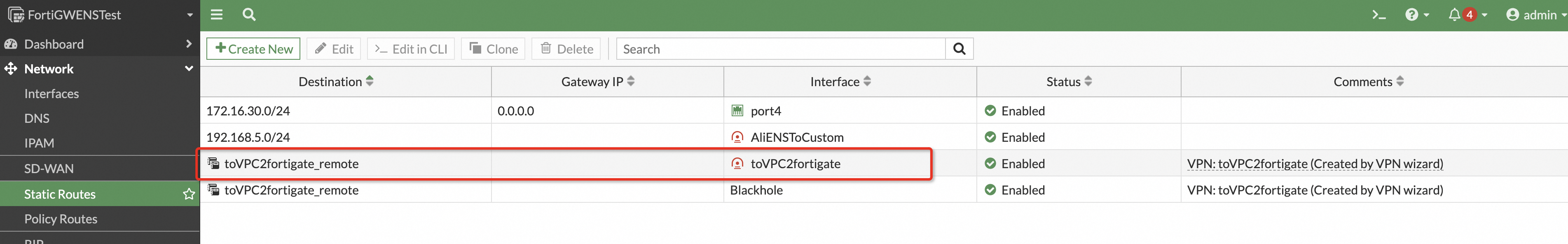
Configure a static route for your services. In the navigation pane on the left, choose Network > Static Routes. Manually configure a route to direct traffic destined for the remote service network through the IPsec VPN tunnel. In later versions, this route is automatically configured by the VPN configuration template.
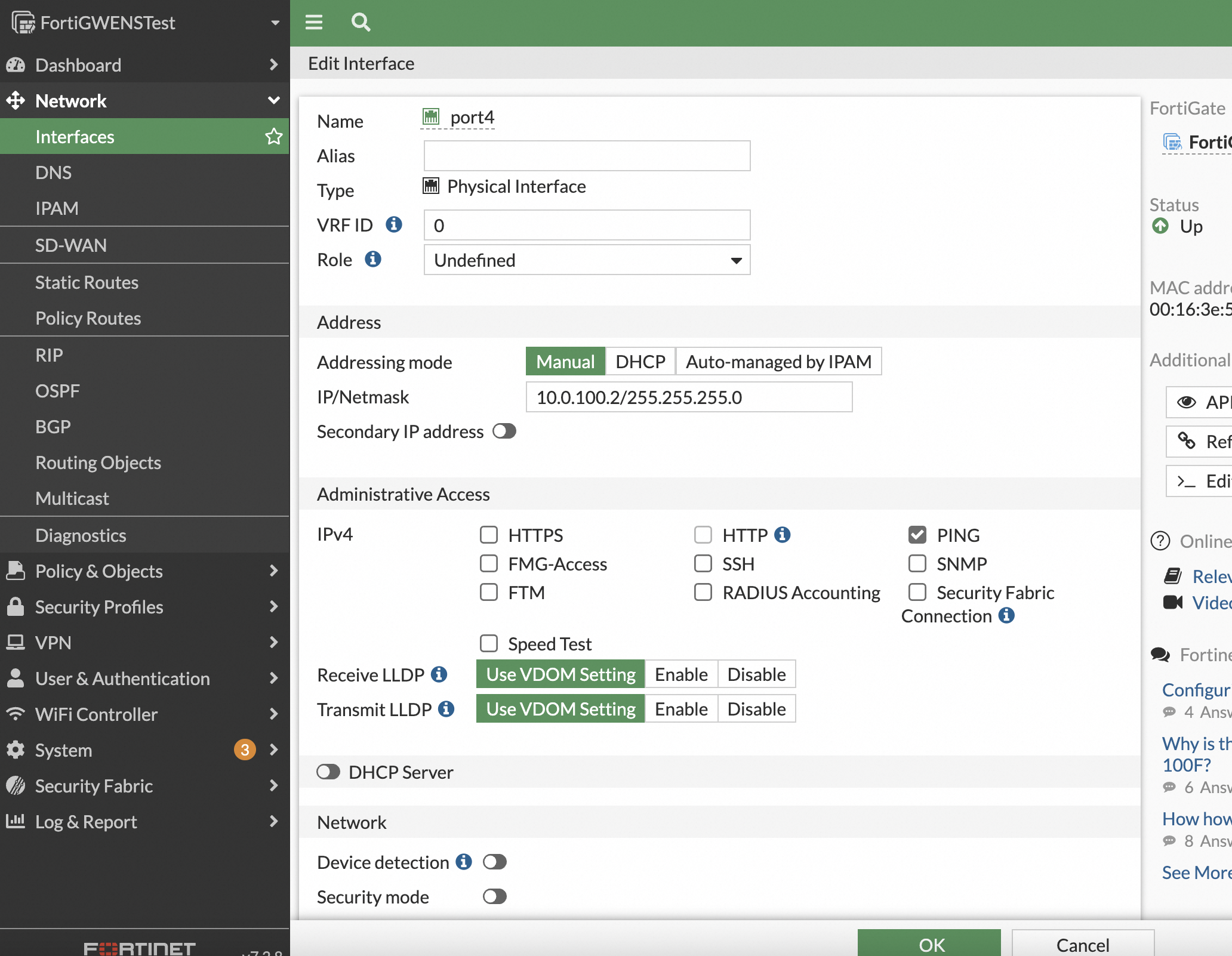
Enable ping on the interface for testing. To run a ping test, you must enable ping on the interface address because it is disabled by default. Double-click the port to open its settings and manually enable ping.
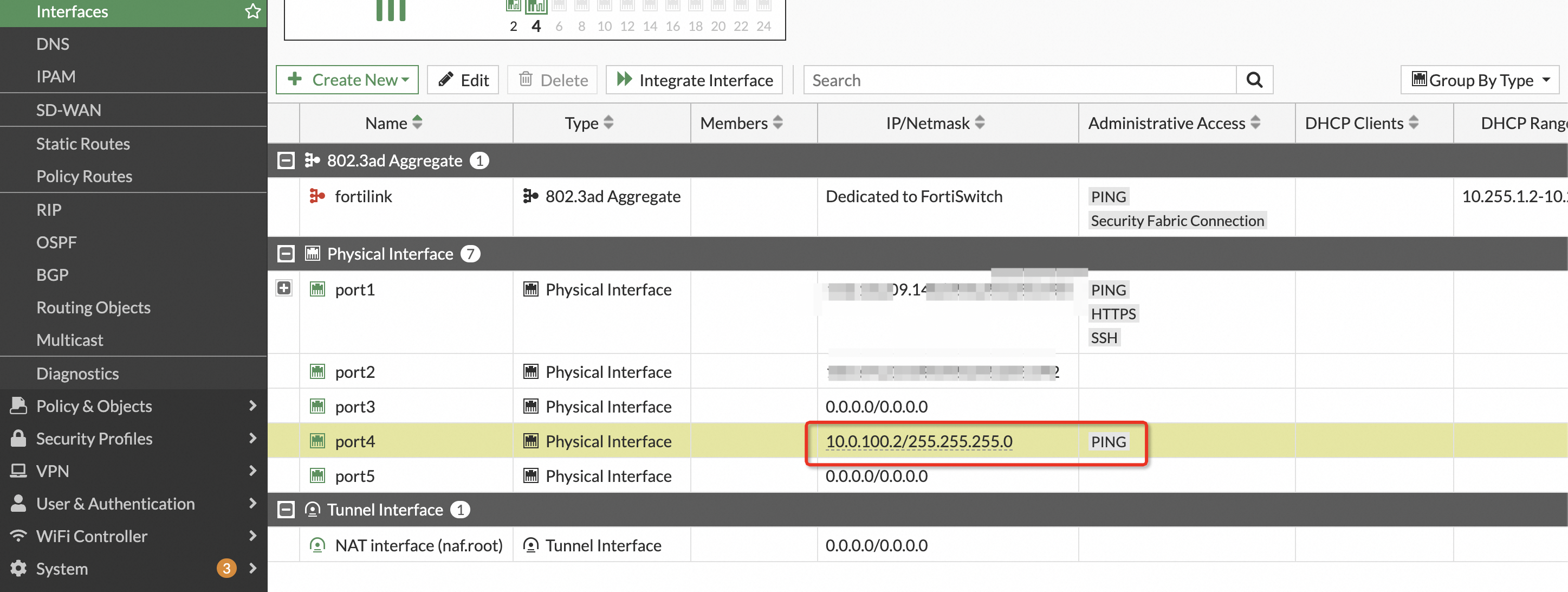
3.2 Site2 configuration
The following is the configuration for site2:
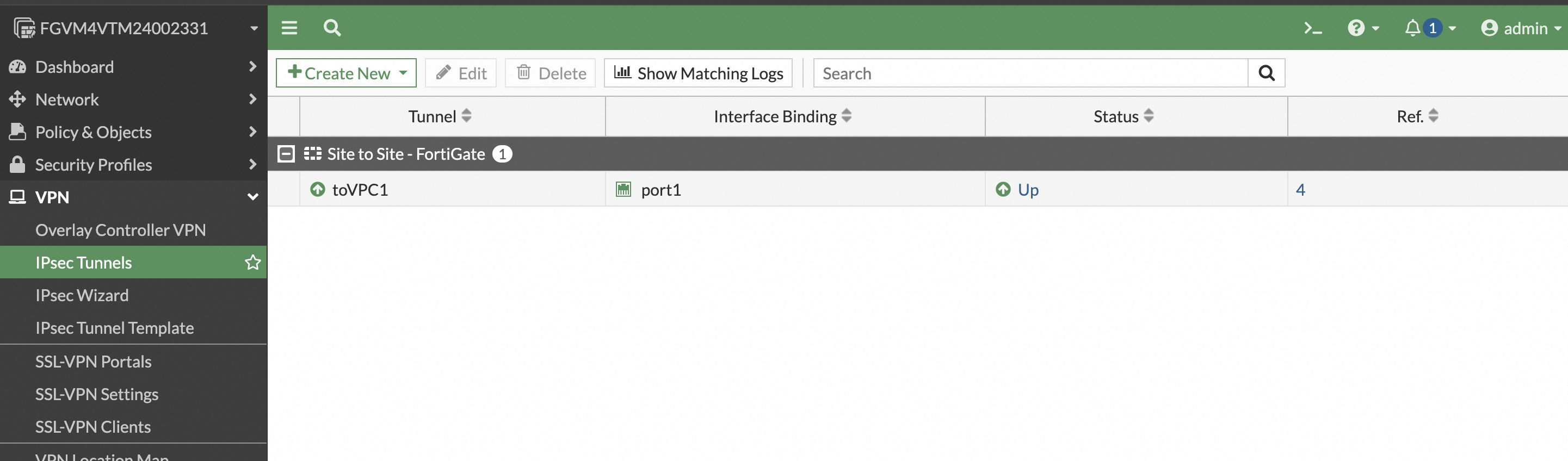
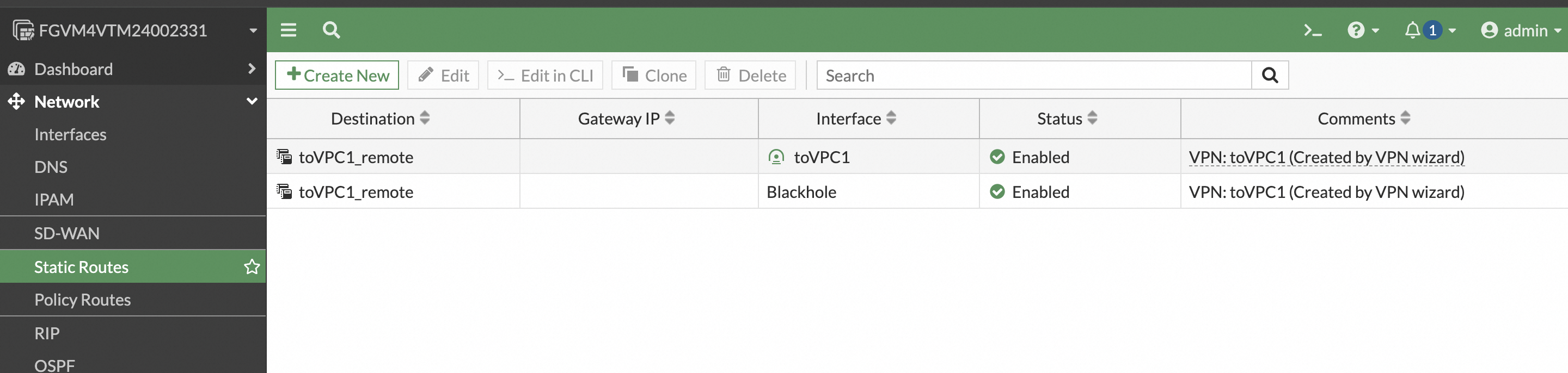
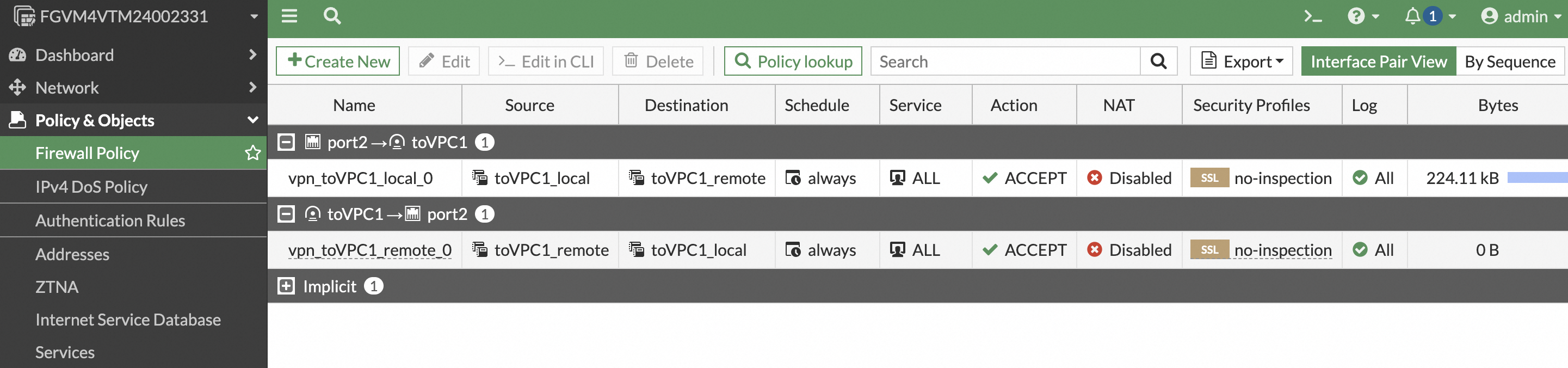
Test connectivity
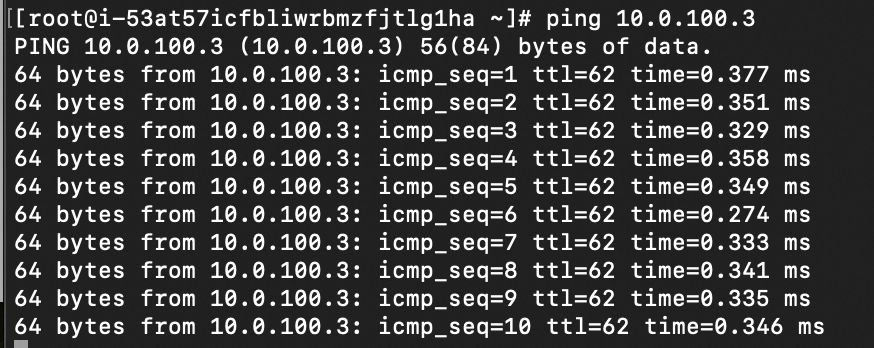
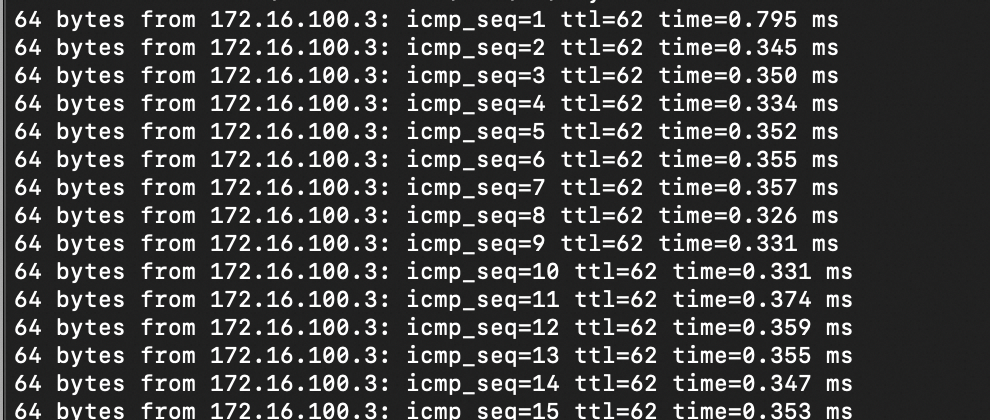
After the configuration is complete, you can test the connection. A successful ping between VM1 and VM4 indicates that the VPN connection is established. The following data is from the staging environment:
Ping from VM4 to VM1
Ping from VM1 to VM4
Other scenarios
The preceding sections describe how to use FortiGate to establish a VPN connection between two ENS nodes. In this scenario, ENS serves as the infrastructure for FortiGate and provides underlying capabilities such as computing power and Internet access. Using this infrastructure, FortiGate also supports other wide area network (WAN) VPN connection methods, such as the following:
VPN connection between ENS and Alibaba Cloud ECS
Connecting ENS to an office VPN
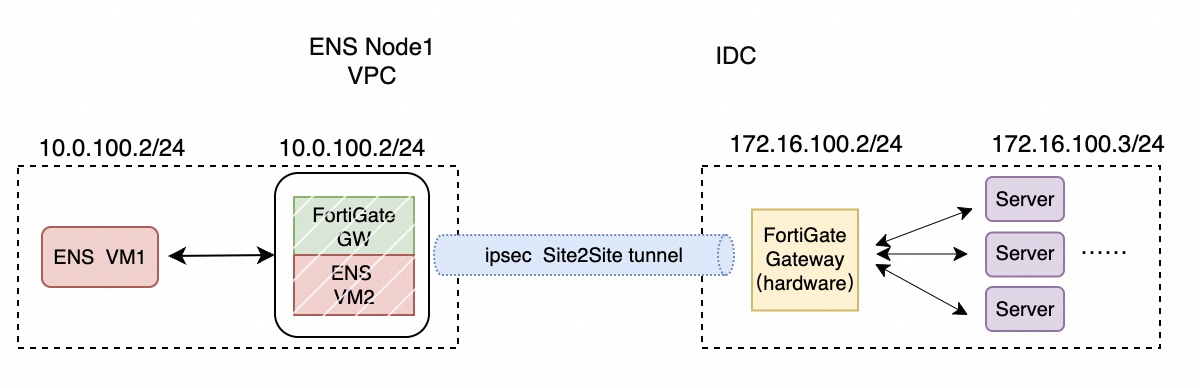
Connection between ENS and an IDC
In these scenarios, the process of installing the FortiGate image on ENS is the same as described previously. Ensure that the image is correct and the network is stable. For detailed configuration steps, see the official FortiGate documentation.
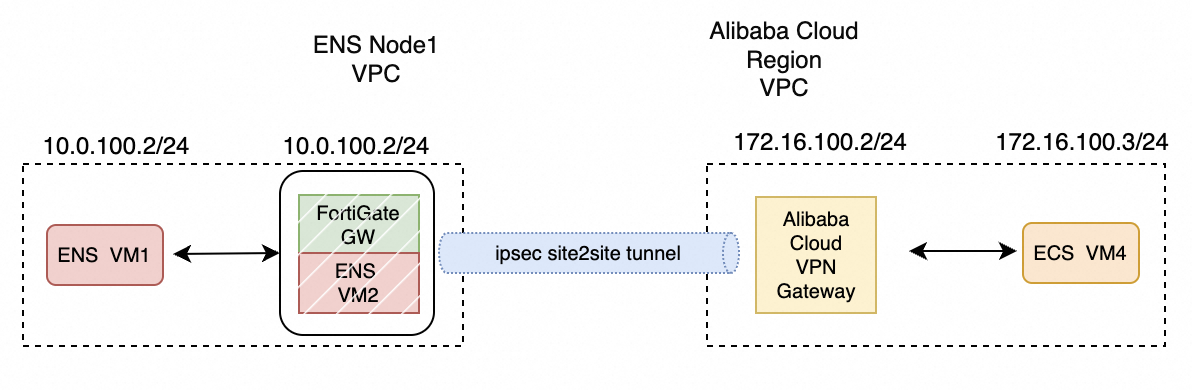
Use FortiGate on ENS to connect to a VPC in an Alibaba Cloud region using a site-to-site connection. This process is similar to connecting two ENS instances.
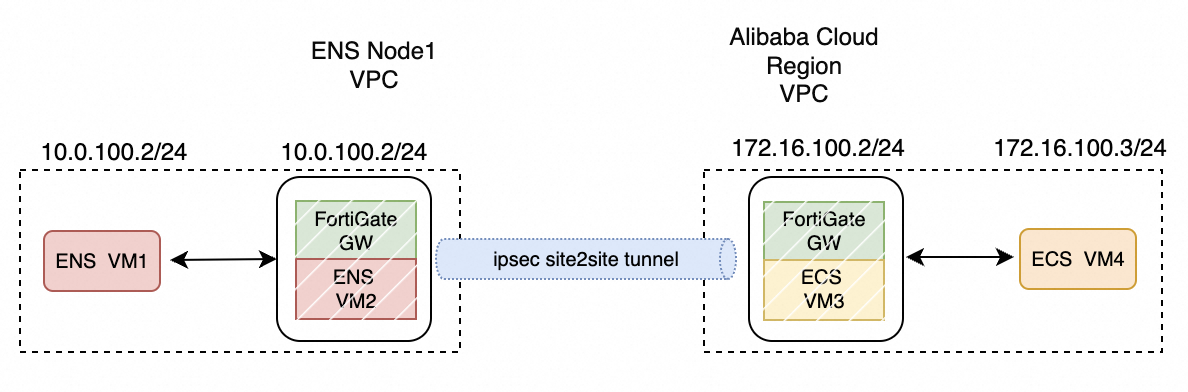
Use FortiGate on ENS to connect to a VPC in an Alibaba Cloud region using a site-to-site connection. The connection is established directly between the FortiGate instance and a VPN Gateway.
Use FortiGate on ENS to connect to a customer's office using a Site2CPE connection.
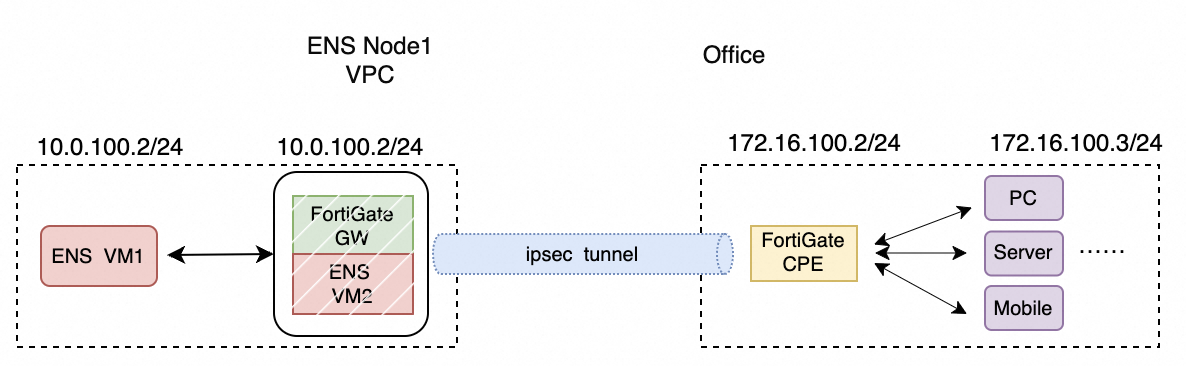
Use FortiGate on ENS to connect to a customer's IDC using a site-to-site connection: