This topic describes how to configure a Knox user account in the E-MapReduce (EMR) console to access the web UIs of specific services, such as Hadoop Distributed File System (HDFS), YARN, Spark, and Ganglia, over the Internet.
Prerequisites
An EMR cluster that contains the Knox service is created. For more information, see Create a cluster.
If your cluster does not contain the Knox service, you can add Knox. For more information, see Add services.
Preparations
Add a security group rule
Obtain the public IP address of your on-premises machine.
For security purposes, we recommend that you allow access only from the current public IP address when you configure a security group rule. To obtain the current public IP address, visit http://myip.ipip.net/.
Add a security group rule.
In this example, port 8443 is enabled.
Go to the Basic Information tab of the desired cluster. In the Security section, click the link to the right of Cluster Security Group.
On the Security Group Details tab of the page that appears, click Add Rule on the Inbound sub-tab.
Set the Authorization Object parameter to the public IP address obtained in the previous step and the Port Range parameter to 8443/8443.
Click Save in the Actions column.
To prevent attacks from external users, you are not allowed to set Authorization Object to 0.0.0.0/0.
If you did not turn on the Assign Public IP Address switch when you create the cluster, no public IP address is available. In this case, you can add a public IP address to the master node of the cluster in the ECS console.
Configure a Knox user account
When you access Knox, you must enter your username and password. The authentication is based on Lightweight Directory Access Protocol (LDAP). You can use the LDAP service of Apache Directory Server in the cluster.
Method 1 (recommended)
On the EMR on ECS page, click the name of the desired cluster. On the page that appears, click the Users tab. On the tab, click Add User to add a Knox user account. For more information, see Manage user accounts.
Method 2
Log on to the desired cluster in SSH mode. For more information, see Log on to a cluster.
Prepare your username, such as Tom.
Run the following commands to open the users.ldif file:
su knox vim /opt/apps/KNOX/knox-current/templates/users.ldifIn the file, replace
emr-guestandEMR GUESTwithTom, and set the userPassword parameter to the password of the username.Run the following commands to import user data to LDAP:
cd /opt/apps/KNOX/knox-current/templates sh ldap-sample-users.sh
Access the web UIs of a service
For more information, see Access the web UIs of open source components in the EMR console.
FAQ
Q: What do I do if Knox abnormally stops and the error
Failed to start gateway: org.apache.hadoop.gateway.services.ServiceLifecycleException: Gateway SSL Certificate is Expiredis reported when I start Knox?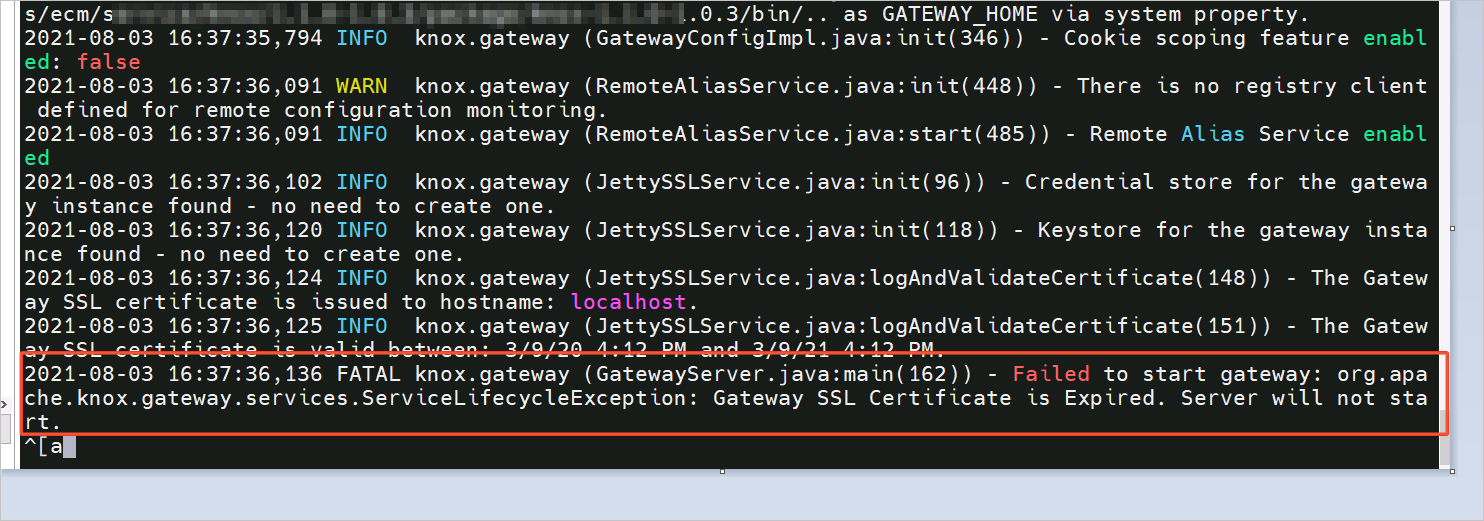
A: You can perform the following steps to resolve the issue:
Log on to your cluster in SSH mode. For more information, see Log on to a cluster.
Run the following command to rename the SSL certificate that expires:
sudo mv /opt/apps/KNOX/knox-current/data/security/keystores/gateway.jks /opt/apps/KNOX/knox-current/data/security/keystores/bak_gateway.jksNoteYou can also move the expired SSL certificate to another directory.
Start Knox.
Go to the Services tab of the cluster. On the Services tab, find Knox, move the pointer over the
 icon, and then select Start.
icon, and then select Start.In the dialog box that appears, configure the Execution Reason parameter and click OK.
In the Confirm message, click OK.