If you want to allow a RAM user to view and manage only a specific cluster in the
Alibaba Cloud Elasticsearch console, you can use a resource group to grant permissions
on the cluster to the RAM user. This topic describes how to use a resource group to
grant permissions on a specific cluster to a RAM user in the Resource Access Management
(RAM) console.
Procedure
If you select the default resource group when you create an Alibaba Cloud Elasticsearch
cluster, the cluster is created in the default resource group. In this case, when
you grant permissions on the cluster to a RAM user, you can select a specific resource
group, but the resource group does not take effect for the authorization. To resolve
this issue, you must attach a custom policy whose effective scope is the Alibaba Cloud
account to which the RAM user belongs to the RAM user. Then, you must create a resource
group, transfer the Elasticsearch cluster to the resource group, and attach a system
policy whose effective scope is the resource group to the RAM user. After you complete
these operations, you can log on to the Elasticsearch console as the RAM user to check
whether the RAM user is granted the permissions on the desired cluster. The following
sections describe the detailed procedure.
Note If your Elasticsearch cluster is created in a custom resource group and you want to
grant permissions on the cluster to a RAM user, you need to only attach a custom policy
whose effective scope is the custom resource group to the RAM user. For more information,
see
Grant permissions to a RAM user. When you attach the custom policy to the RAM user in the RAM console, set the
Authorized Scope parameter to
Specific Resource Group and select the custom policy in the
Select Policy section.
- Step 1: Attach a custom policy whose effective scope is the entire Alibaba Cloud account
to a RAM user of the account
- Step 2: Create a resource group and attach a system policy whose effective scope is
a specific resource group to the RAM user
- Step 3: Check whether the permissions on the cluster are granted to the RAM user
Step 1: Attach a custom policy whose effective scope is the entire Alibaba Cloud account
to a RAM user of the account
- Log on to the RAM console by using your Alibaba Cloud account.
- Create a custom policy.
For more information, see
Create a custom policy. The following code provides an example for the policy document:
{
"Statement": [
{
"Action": [
"elasticsearch:*"
],
"Effect": "Allow",
"Resource": "acs:elasticsearch:*:<yourAccountId>:instances/<yourInstanceId>"
},
{
"Action": [
"elasticsearch:ListCollectors"
],
"Effect": "Allow",
"Resource": "acs:elasticsearch:*:<yourAccountId>:collectors/*"
},
{
"Action": [
"elasticsearch:ListInstance",
"elasticsearch:ListSnapshotReposByInstanceId"
],
"Effect": "Allow",
"Resource": "acs:elasticsearch:*:<yourAccountId>:instances/*"
},
{
"Effect": "Allow",
"Action": [
"cms:ListAlarm",
"cms:DescribeActiveMetricRuleList",
"cms:QueryMetricList"
],
"Resource": "*"
},
{
"Action": [
"elasticsearch:ListTags"
],
"Effect": "Allow",
"Resource": "acs:elasticsearch:*:*:tags/*"
},
{
"Action": [
"elasticsearch:GetEmonProjectList"
],
"Effect": "Allow",
"Resource": "acs:elasticsearch:*:*:emonProjects/*"
},
{
"Action": [
"elasticsearch:getEmonUserConfig"
],
"Effect": "Allow",
"Resource": "acs:elasticsearch:*:*:emonUserConfig/*"
},
{
"Action": "ims:*",
"Effect": "Allow",
"Resource": "acs:ims::<yourAccountId>:application/*"
}
],
"Version": "1"
}
Before you use the preceding code, you must replace the variables in the code with
the desired values.
| Variable |
Description |
| <yourAccountId> |
Replace this variable with the ID of your Alibaba Cloud account. Wildcards (*) are not supported. To obtain the ID of your Alibaba Cloud account, perform the following
operations: Log on to the Alibaba Cloud Management Console and move the pointer over
the profile picture in the upper-right corner. Then, you can view the ID of your Alibaba Cloud account.
|
| <yourInstanceId> |
Replace this variable with the ID of the Elasticsearch cluster whose permissions you
want to grant. Wildcards (*) are not supported. For information about how to obtain the ID, see View the basic information of a cluster.
|
External interfaces that are used to call specific services, such as Beats, Advanced
Monitoring and Alerting, and Tag, are integrated into the cluster management page
of the Elasticsearch console. If you want to manage only the clusters in a specific
resource group in the Elasticsearch console as a RAM user, you must configure a custom
policy whose effective scope is the Alibaba Cloud account to which the RAM user belongs
and attach the policy to the RAM user. This way, the RAM user can pass permission
verification on the cluster management page.
Note After the policy for a specific Elasticsearch or Logstash cluster is created and attached
to a RAM user, you can use one of the following URLs to directly access the Elasticsearch
or Logstash cluster as the RAM user:
- https://elasticsearch.console.aliyun.com/{regionId}/instances/{instanceId}/base
- https://elasticsearch.console.aliyun.com/{regionId}/logstashes/{instanceId}/base
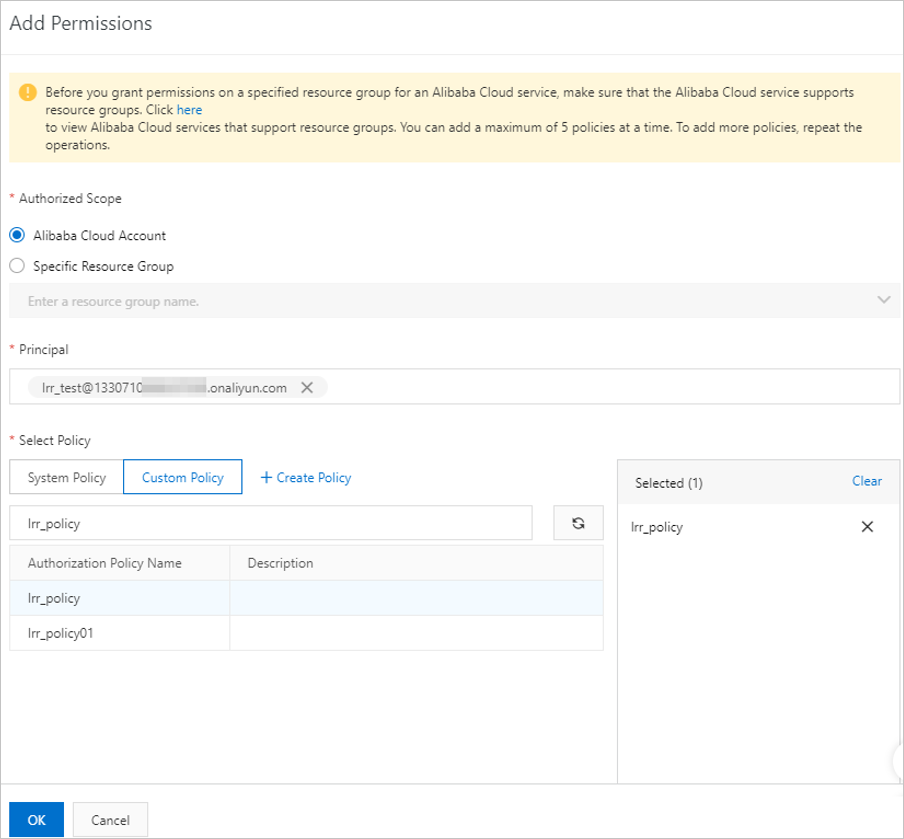
- Create a RAM user.
- Attach the newly created custom policy whose effective scope is the Alibaba Cloud
account to which the RAM user belongs to the RAM user.
For more information, see
Grant permissions to a RAM user. When you attach the custom policy to the RAM user, set the
Authorized Scope parameter to
Alibaba Cloud Account and select the custom policy in the
Select Policy section.
Step 2: Create a resource group and attach a system policy whose effective scope is
a specific resource group to the RAM user
- Log on to the Resource Management console.
- Create a resource group.
- Transfer the desired cluster from the default resource group to the newly created
resource group.
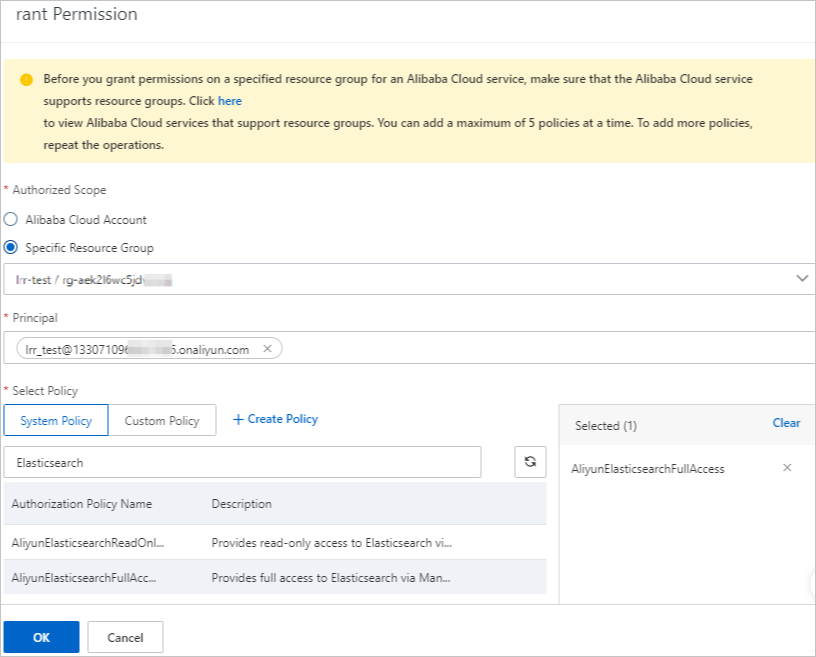
- Attach a system policy whose effective scope is the newly created resource group to
the RAM user.
For more information, see
Add RAM authorization. When you attach the system policy to the RAM user, the
Authorized Scope parameter is automatically set to
Specific Resource Group, and the newly created resource group is automatically selected. You need to only
select the system policy
AliyunElasticsearchFullAccess in the Select Policy section.
- View the authorization information of the RAM user.
- Click the Permissions tab.
- Click the name of the RAM user in the Principal column.
- On the page that appears, click the Permissions tab and view the authorization information of the RAM user.
Step 3: Check whether the permissions on the cluster are granted to the RAM user
- Log on to the Elasticsearch console as the RAM user.
- In the top navigation bar, select the region where the desired cluster resides.
- In the left-side navigation pane, click Elasticsearch Clusters.
- In the top navigation bar, select the newly created resource group and view the information
about the cluster.

