Disclaimer: This article may contain information about third-party products. Such information is for reference only. Alibaba Cloud does not make a guarantee, explicitly or implicitly, with respect to the performance and reliability of the third-party products, and potential impacts of operations on the products.
Overview
This topic describes how to troubleshoot and solve the problem of high bandwidth usage in Windows instances.
Details
Take note of the following points:
- Before you perform high-risk operations such as modifying or changing the specifications or data of an Alibaba Cloud instance, we recommend that you familiarize yourself with the disaster recovery and fault tolerance capabilities of the instance to ensure data security.
- Before you modify the specifications or data of an Alibaba Cloud instance, such as an Elastic Compute Service (ECS) instance or an ApsaraDB RDS instance, we recommend that you create snapshots or enable backups. For example, you can enable log backups for an ApsaraDB RDS instance.
- If you have granted specific users the permissions on sensitive information, such as logon accounts and passwords, or submitted sensitive information in the Alibaba Cloud Management Console, we recommend that you modify the sensitive information at the earliest opportunity.
This topic describes the following steps.
- Locate the problem. Find the specific process that affects the excessive bandwidth usage.
-
Analyze and process. Check whether the processes that affect the high bandwidth usage are normal and classify them for processing.
- For normal processes, you must optimize the program or upgrade the bandwidth.
- For abnormal processes: You can manually check and kill processes or use third-party security tools to check and kill processes.
- Example. An example is used to describe how to troubleshoot and resolve issues.
Locate the problem
Microsoft has several tools to locate problems with high bandwidth usage, such as Task Manager, Resource Monitor, Performance Monitor, Process Explorer, and Xperf (after Windows Server 2008). Grab the system Full Memory Dump to check. In the case of heavy traffic, you can also use Wireshark to crawl network packets over a period of time and analyze traffic usage.
Tip :Windows Server 2008 the above systems, the system's own resource monitor is usually used to monitor the bandwidth.
- At the bottom of the desktop, click the Start menu and select Run.
- After you open the Run box, enter a
perfmon -resin the box and click OK. - On the Resource Monitor page, check whether the bandwidth usage of each process is too high.
- For a process that consumes a high amount of resources, view the process ID and the program name of the process.
- After locating the process ID, combine the task manager to determine whether the program is abnormal and locate the specific location of the program.
- Before locating abnormal processes, you must click View (V) > Select Column (S) in the task manager.
- In the dialog box that appears, select PID (process identifier) and click OK.
- In the process page of the task manager, PID will be added. Click PID and sort to find the abnormal process previously viewed by Resource Monitor. Right-click the process name and select the location to open the file. Check whether the process is a malicious program.
Analysis and processing
Analysis and Processing of Excessive Bandwidth Usage
You need to determine whether the processes that affect the excessive bandwidth usage are normal or abnormal, and classify them for processing.
Analysis and processing of high normal usage rate
Under normal circumstances, when customers frequently access the service, or due to Windows's own services (update services, etc.) may occupy a high level of network traffic. If the bandwidth usage is too high due to normal processes, troubleshoot them one by one in the following order.
Tip: We recommend that you configure the memory of Windows Server 2008 or Windows Server 2012 instances at or above 2 GB.
- Check whether the background has performed Windows Update behavior.
- We recommend that you install antivirus software on the server to perform antivirus. If anti-virus software is installed, check whether the anti-virus software performs scanning operations in the background when the bandwidth is high. If possible, upgrade the antivirus software to the latest version, or delete the antivirus software.
- Check whether the application in the ECS has a large amount of disk access, network access, or high computing requirements. You can use more cores or memory specifications to solve resource bottlenecks, such as bandwidth upgrade.
- If your server configuration is high, it doesn't make much sense to upgrade the configuration. In terms of architecture, it is not that the higher the server configuration, the better. In this case, you need to try to separate applications and optimize related programs. An example is described as follows.
Problem description: If multiple applications such as MySQL, PHP, and Web are deployed on a server at the same time, even if the configuration is relatively high, the resource load is likely to occur.
Solution: Try to separate applications and use different servers to host different applications. For example, the database is completely carried by RDS, which reduces the resource consumption of the server itself and the large number of calls within the server. In terms of program optimization, you can adjust your configuration, such as adjusting the number of connections and cache configurations, as well as various parameters for Web and database calls.
Analysis and Processing of Exception Usage
If the bandwidth usage is too high, it may be caused by malicious viruses and Trojans. Sometimes three-party malicious programs may use svchost.exe or Tcpsvcs.exe of the operating system to disguise, causing high bandwidth usage. You need to manually check and kill abnormal processes.
Tip: If you cannot determine whether the process is a virus or a Trojan, we recommend that you search for the process name on the Internet and confirm it. We recommend that you create a snapshot to complete the backup before you delete the process.
- Use commercial antivirus software, or use Microsoft's free security tool Microsoft Safety Scanner to scan for antivirus in safe mode.
- Run Windows Update to install the latest Microsoft security patches.
- Use MSconfig to disable all non-Microsoft service drivers and check whether the problem occurs again. For more information, see How to perform clean startup in Windows.
- If the server or site suffers from distributed denial of service attack or CC attacks, a large number of access requirements are generated in a short period of time. You can log on to the Security Center to check whether the protection distributed denial of service attack in Apsara Stack Security has adjusted the threshold and check whether CC protection is enabled. If the attack does not reach the threshold and Apsara Stack Security is not cleaned, you can contact after-sales assistance to start cleaning.
Examples
Description
A Windows instance has a large network traffic, that is, the server network bandwidth usage is high, as shown in the following figure.
Cause
The network bandwidth usage of the server may be high due to the following reasons.
- Your normal application service is frequently accessed and occupies a high bandwidth.
- Network traffic caused by malicious viruses and Trojans. Sometimes third-party malicious programs may use svchost.exe or Tcpsvcs.exe of the operating system to disguise, causing high bandwidth usage.
- Windows's own services may consume high network traffic, such as update services.
Method
Analyze why high traffic is occupied by the following two methods.
- Monitor real-time traffic using the Resource Monitor, a tool that comes with Windows.
- In the case of heavy traffic, use the Wireshark tool to grab network packets over a period of time and analyze the traffic usage.
Resource Monitor
Windows Server 2008 R2 and Windows Server 2012 R2 are used as examples to illustrate how to use Resource Monitor to monitor real-time network traffic.
- Log on to the instance. For more information about how to log on to the instance, see Connect to a Windows instance from a local client.
- Right-click the blank space in the taskbar and select Start Task Manager.
- Click Performance, and then click Resource Monitor.
- In the Resource Monitor window, click Network.
- In the Resource Monitor window, you can analyze the current network traffic of an instance in real time by using the processes of network activity, network activity, TCP connection, and listening port.
- Windows Server 2008 R2
- Windows Server 2012 R2
- If the process is a normal business process and the bandwidth usage is high due to the large client page view, please consider upgrading the bandwidth as appropriate.
- If the process is a process with a suspicious name, try to kill the process directly, or use professional antivirus software to monitor the instance after antivirus.
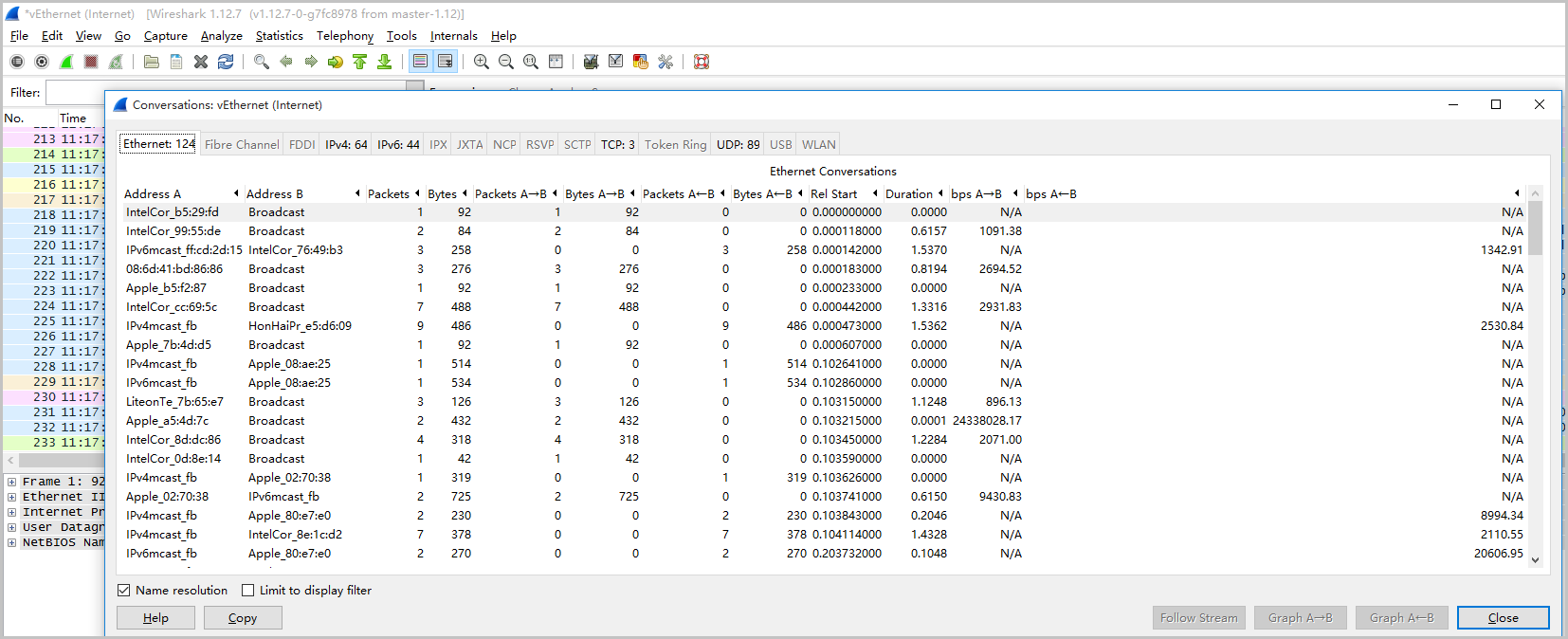
Wireshark
Wireshark is a commonly used network analysis tool. You can download and install software from the Wireshark official website on Windows instances.
Perform the following steps to use Wireshark to analyze network traffic:
- Log on to the instance. For more information about how to log on to the instance, see Connect to a Windows instance from a local client.
- Start Wireshark and select Statistics > Conversations from the toolbar.
- On the Conversations page, you can see all the network communication. The traffic details and traffic conditions at both ends of the communication are given from the link layer, IP layer, and TCP layer respectively. By crawling network packets over a period of time, you can analyze which connections and ports occupy a high level of traffic.
Application scope
- Elastic Compute Service (ECS)