If the source or destination database for a Data Transmission Service (DTS) instance is deployed on Amazon Web Services (AWS), you must configure the database to allow access from DTS servers. You can connect the AWS database to Alibaba Cloud using a public IP address or a virtual private cloud (VPC). This topic describes the required operations.
Connect over a public IP address
On the AWS platform, enable public network access for the database. Then, based on your task type, such as data synchronization, data migration, or data validation, add the IP addresses of the DTS servers in the corresponding region to the security settings of the database, such as security group rules, firewalls, or whitelists.
Connect over a VPC
Example scenario
In this topic, an enterprise has a VPC in the Alibaba Cloud Germany (Frankfurt) region and a VPC in the AWS Europe (Frankfurt) region. The enterprise wants to enable communication between the two VPCs.
The enterprise can use Alibaba Cloud VPN Gateway (a VPN Gateway instance that uses a public IP address) and AWS VPN to establish an IPsec-VPN connection. This connection enables encrypted communication between the two VPCs.

CIDR block planning
You can plan the CIDR blocks as needed. Make sure that the CIDR blocks of the networks that you want to connect do not overlap.
VPC instance CIDR block planning
Resource | VPC instance CIDR block | Instance IP address |
Alibaba Cloud VPC |
| ECS IP address: 10.0.0.223 |
AWS VPC |
| EC2 IP address: 192.168.10.113 |
IPsec-VPN connection BGP CIDR block planning
This topic describes how to use both static routing and BGP dynamic routing for the IPsec-VPN connection. If you plan to use only static routing, you can skip this section. The following table shows the BGP CIDR block planning used in this topic.
When you configure BGP dynamic routing for an IPsec-VPN connection, both tunnels on the Alibaba Cloud side must use the same Local ASN. The peer BGP ASNs for the two tunnels can be different, but we recommend that you use the same peer BGP ASN for both.
Resource | IPsec-VPN connection name | Tunnel | BGP tunnel CIDR block | BGP IP address | BGP ASN (Local ASN) |
Alibaba Cloud VPN Gateway | IPsec-VPN connection | Primary tunnel | 169.254.116.208/30 Note The CIDR block of each tunnel must be unique within a VPN Gateway instance. | 169.254.116.210 | 65530 |
Standby tunnel | 169.254.214.96/30 | 169.254.214.98 | |||
AWS virtual private gateway | Site-to-Site VPN Connection 1 | Tunnel 1 | 169.254.116.208/30 | 169.254.116.209 | 64512 |
Tunnel 2 | The standby tunnel is not used. | ||||
Site-to-Site VPN Connection 2 | Tunnel 1 | 169.254.214.96/30 | 169.254.214.97 | ||
Tunnel 2 | The standby tunnel is not used. | ||||
Preparations
Create a VPC in the Alibaba Cloud Germany (Frankfurt) region and deploy resources using Elastic Compute Service (ECS). For more information, see Create a VPC with an IPv4 CIDR block.
You have created a VPC in the AWS Europe (Frankfurt) region and deployed resources in it using EC2. For more information, see the AWS platform.
Configuration flow

Step 1: Create a VPN Gateway instance on Alibaba Cloud
First, you must create a VPN Gateway instance on Alibaba Cloud. After the instance is created, the system assigns two IP addresses to it. These IP addresses are used to establish the IPsec-VPN connection with the AWS platform.
Log on to the VPN Gateway console.
In the top navigation bar, select the region where you want to create the VPN gateway.
The VPN gateway must be in the same region as the VPC that you want to connect.
On the VPN Gateways page, click Create VPN Gateway.
On the purchase page, configure the VPN Gateway with the following settings. Then, click Buy Now and complete the payment.
Only the parameters relevant to this topic are described. For all other parameters, retain the default settings. For more information, see Create and manage a VPN Gateway instance.
Configuration
Description
Example value
Instance Name
Enter a name for the VPN Gateway instance.
Enter VPN Gateway.
Region
Select the region where the VPN Gateway instance is located.
Select Germany (Frankfurt).
Gateway Type
Select the gateway type of the VPN Gateway instance.
Select Standard.
Network Type
Select the network type of the VPN Gateway instance.
Select Public.
Tunnel
The system displays the tunnel modes that are supported by IPsec-VPN connections in the current region.
Dual-Tunnel
Single-tunnel
For more information about single-tunnel and dual-tunnel modes, see Create an IPsec-VPN connection.
In this topic, the default value is Dual-tunnel.
VPC
Select the VPC to associate with the VPN Gateway instance.
Select the VPC instance in the Alibaba Cloud Germany (Frankfurt) region.
vSwitch
Select a vSwitch from the VPC.
If the tunnel mode is single-tunnel, you need to specify only one vSwitch.
If the tunnel mode is dual-tunnel, you must specify two vSwitches.
When the IPsec-VPN feature is enabled, the system creates an elastic network interface (ENI) in each of the two vSwitches. The ENIs are used as interfaces for traffic between the VPC and the IPsec-VPN connection. Each ENI occupies an IP address in its vSwitch.
NoteThe system selects the first vSwitch by default. You can change the vSwitch or use the default vSwitch.
After a VPN Gateway instance is created, you cannot change its associated vSwitches. You can view the associated vSwitches, the zones where they are located, and the ENI information on the instance details page.
Select a vSwitch in the VPC.
vSwitch 2
Select the second vSwitch from the VPC.
You must specify two vSwitches in different zones within the VPC that is associated with the VPN Gateway instance. This configuration implements zone-disaster recovery for the IPsec-VPN connection.
For regions that have only one zone, zone-disaster recovery is not supported. We recommend that you specify two different vSwitches in that zone to achieve high availability for the IPsec-VPN connection. You can select the same vSwitch for both.
NoteIf a second vSwitch is not available in the VPC, you can create one. For more information, see Create and manage a vSwitch.
Select the second vSwitch in the VPC.
IPsec-VPN
Specifies whether to enable the IPsec-VPN feature. The default value is Enable.
Enable the IPsec-VPN feature.
SSL-VPN
Select whether to enable or disable the SSL-VPN feature. The default value is Disable.
Disable the SSL-VPN feature.
Return to the VPN Gateway page to view the VPN Gateway instance that you created.
A new VPN Gateway instance has an initial status of Preparing. After about 1 to 5 minutes, the status changes to Normal. A Normal status indicates that the VPN Gateway is initialized and ready for use.
The following table lists the two IP addresses that are assigned by the system to the VPN Gateway instance:
VPN Gateway instance name
VPN Gateway instance ID
IP address
VPN Gateway
vpn-gw8dickm386d2qi2g****
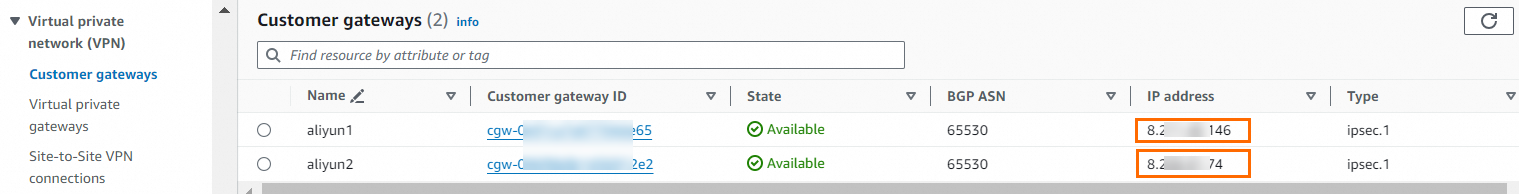
IPsec Address 1 (active tunnel address by default): 8.XX.XX.146
IPsec Address 2 (standby tunnel address by default): 8.XX.XX.74
Step 2: Deploy the VPN on the AWS platform
To establish the IPsec-VPN connection, you must deploy the VPN on the AWS platform based on the following information. For specific commands or operations, see the official AWS documentation.
Use static routing
Create customer gateways.
You must create two customer gateways on the AWS side. Use the two IP addresses of the Alibaba Cloud VPN Gateway instance as the IP addresses of the customer gateways.
Create a virtual private gateway.
You must create a virtual private gateway on the AWS side and attach it to the VPC that you want to connect to Alibaba Cloud.

Create site-to-site VPN connections.
ImportantBoth Alibaba Cloud and AWS IPsec-VPN connections support dual-tunnel mode. However, the two tunnels on the AWS platform are associated with the same customer gateway by default, whereas the two tunnels on the Alibaba Cloud side have different IP addresses. This prevents a one-to-one connection between the tunnels. To ensure that both tunnels of the Alibaba Cloud IPsec-VPN connection are enabled, you must create two site-to-site VPN connections on the AWS platform. Each site-to-site VPN connection must be associated with a different customer gateway.
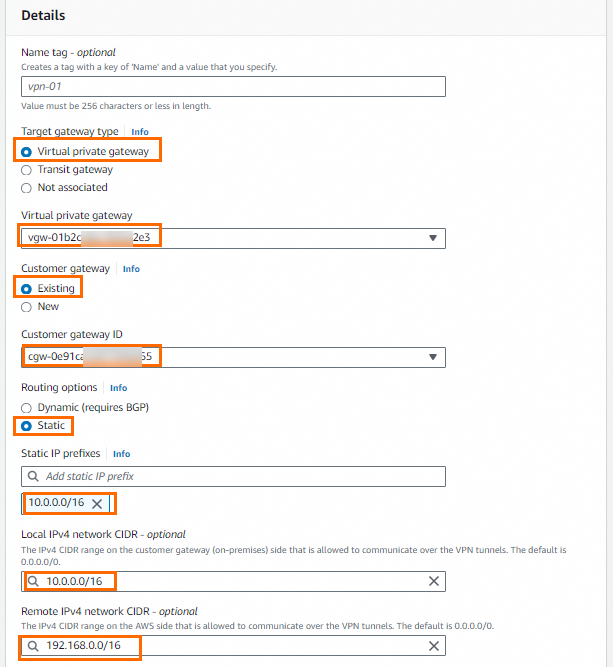
The following figure shows the configuration of one site-to-site VPN connection. The tunnel options use default values. The other site-to-site VPN connection is associated with a different customer gateway, but the remaining configurations are the same.
 Note
NoteIn the figure above, Local IPv4 Network CIDR must be the CIDR block of the Alibaba Cloud VPC, and Remote IPv4 Network CIDR must be the CIDR block of the AWS VPC.
After the site-to-site VPN connections are created, you can view the tunnel address information. This information is required later to create the IPsec-VPN connection on the Alibaba Cloud side.
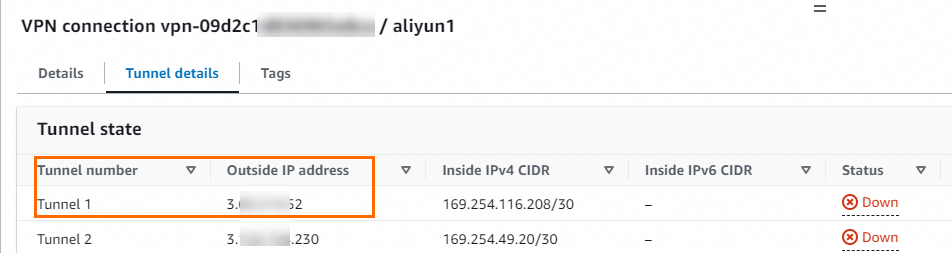
In this topic, the outside IP addresses of Tunnel 1 for the two VPN connections and their associated customer gateway IP addresses are as follows:
Site-to-site VPN connection
Tunnel
Outside IP Address
Associated customer gateway IP address
Site-to-Site VPN Connection 1
Tunnel 1
3.XX.XX.52
8.XX.XX.146
Site-to-Site VPN Connection 2
Tunnel 1
3.XX.XX.56
8.XX.XX.74
Configure route propagation.
You must enable route propagation in the route table of the VPC that is associated with the virtual private gateway. This ensures that routes from the site-to-site VPN connection are automatically propagated to the VPC route table.

Use BGP dynamic routing
Create customer gateways.
You must create two customer gateways on the AWS side. Use the two IP addresses of the Alibaba Cloud VPN Gateway instance as the customer gateway IP addresses. Also, register the BGP ASN of the Alibaba Cloud IPsec-VPN connection on AWS.

Create a virtual private gateway.
You must create a virtual private gateway on the AWS side and attach it to the VPC that you want to connect to Alibaba Cloud. When you create the virtual private gateway, you must specify the BGP ASN for the AWS side.
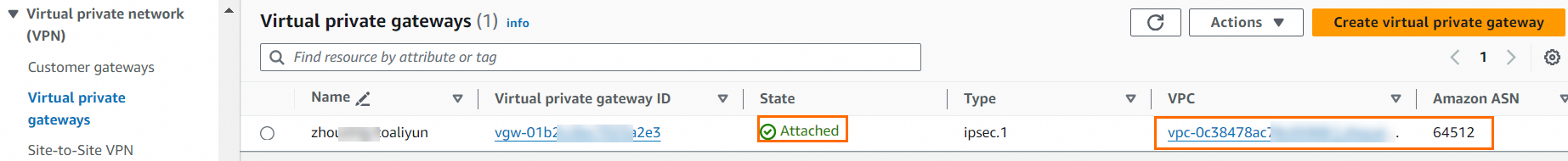
Create site-to-site VPN connections.
ImportantBoth Alibaba Cloud and AWS IPsec-VPN connections support dual-tunnel mode. However, the two tunnels on the AWS platform are associated with the same customer gateway by default, whereas the two tunnels on the Alibaba Cloud side have different IP addresses. This prevents a one-to-one connection between the tunnels. To ensure that both tunnels of the Alibaba Cloud IPsec-VPN connection are enabled, you must create two site-to-site VPN connections on the AWS platform. Each site-to-site VPN connection must be associated with a different customer gateway.
The following figure shows the configuration for one site-to-site VPN connection. Configurations not shown use default values. The other site-to-site VPN connection is associated with a different customer gateway. Its Tunnel 1 Inside IPv4 CIDR is set to 169.254.214.96/30, and the remaining configurations are the same.
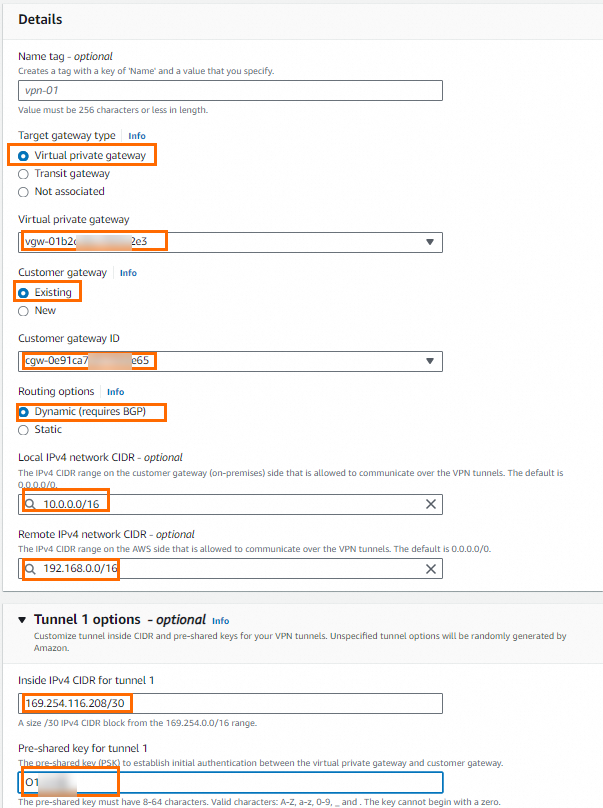 Note
NoteIn the figure above, Local IPv4 Network CIDR must be the CIDR block of the Alibaba Cloud VPC, and Remote IPv4 Network CIDR must be the CIDR block of the AWS VPC.
After the site-to-site VPN connections are created, you can view the tunnel address information.
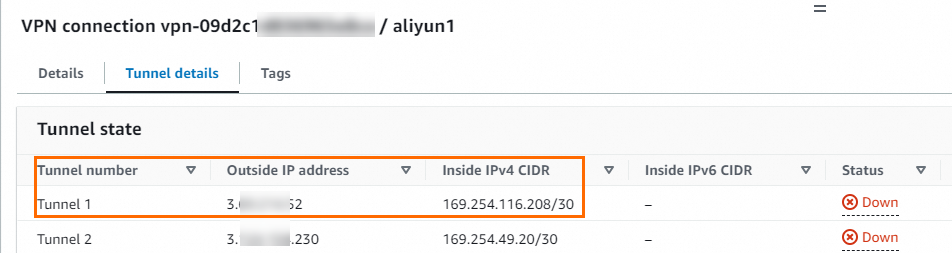
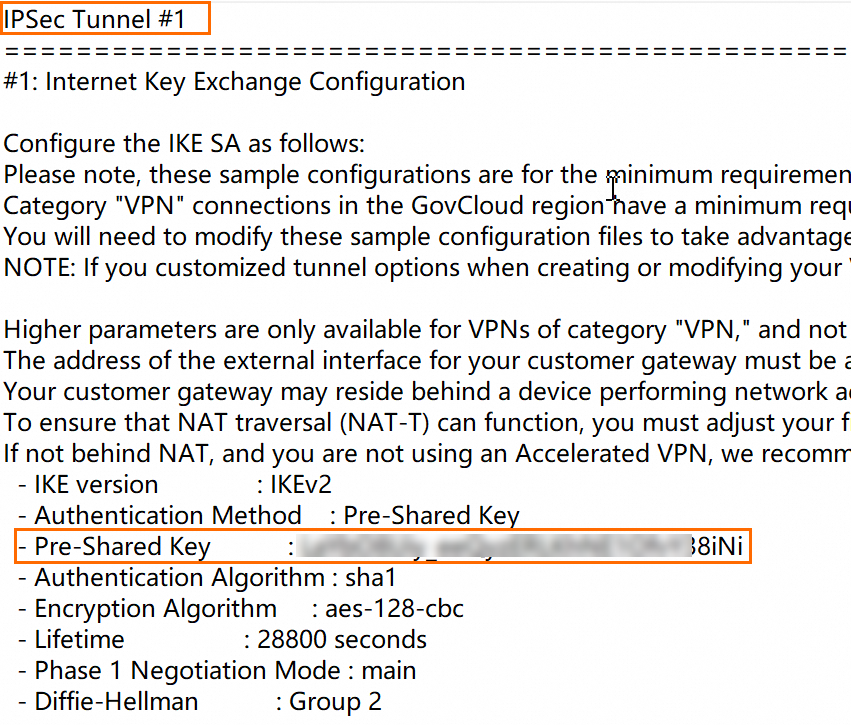
View the pre-shared key and the BGP IP address for the Alibaba Cloud side.
After the site-to-site VPN connection is created, download the VPN configuration file for the peer device (the Alibaba Cloud VPN gateway) from the AWS platform. The VPN configuration file contains the pre-shared keys and BGP IP addresses required for the configuration on Alibaba Cloud. For instructions on how to download the configuration file, see Download the configuration file. When you download the configuration file, select Generic for Vendor and IKEv2 for IKE version.
NoteIf you specified a pre-shared key when you created the site-to-site VPN connection, you do not need to view it in the configuration file. If you used a system-generated pre-shared key, you can find the key in the configuration file. The pre-shared keys for the tunnels on the Alibaba Cloud and AWS sides must be the same.
In this topic, the outside IP addresses, BGP IP addresses, and associated customer gateway IP addresses for Tunnel 1 of the two VPN connections are as follows:
Site-to-site VPN connection
Tunnel
Outside IP Address
AWS BGP IP address
Alibaba Cloud BGP IP address
Associated customer gateway IP address
Site-to-Site VPN Connection 1
Tunnel 1
3.XX.XX.52
169.254.116.209
169.254.116.210
8.XX.XX.146
Site-to-Site VPN Connection 2
Tunnel 1
3.XX.XX.56
169.254.214.97
169.254.214.98
8.XX.XX.74
Configure route propagation.
You must enable route propagation in the route table of the VPC that is associated with the virtual private gateway. This ensures that routes from the site-to-site VPN connection are automatically propagated to the AWS VPC route table.

Step 3: Deploy the VPN Gateway on Alibaba Cloud
After you complete the VPN configuration on the AWS platform, you must deploy the VPN Gateway on the Alibaba Cloud side based on the following information. This establishes the IPsec-VPN connection between the AWS VPC and the Alibaba Cloud VPC.
Create customer gateways.
Log on to the VPN Gateway console.
In the left-side navigation pane, choose .
In the top navigation bar, select the region in which you want to create the customer gateway.
Make sure that the customer gateway and the VPN gateway to be connected are deployed in the same region.
On the Customer Gateways page, click Create Customer Gateway.
In the Create Customer Gateway panel, set the following parameters and click OK.
You must create two customer gateways and use the outside IP addresses of the tunnels from the AWS site-to-site VPN connections as the IP addresses for the customer gateways. This establishes two encrypted tunnels. Only the parameters relevant to this topic are described. For all other parameters, retain the default settings. For more information, see Customer gateways.
ImportantUse only the outside IP address of Tunnel 1 from each site-to-site VPN connection as the customer gateway address. The outside IP address of Tunnel 2 from each site-to-site VPN connection is not used by default. After the IPsec-VPN connection is created, Tunnel 2 of each site-to-site VPN connection is not connected by default.
Configuration
Description
Customer Gateway 1
Customer Gateway 2
Name
Enter a name for the customer gateway.
Enter Customer Gateway 1.
Enter Customer Gateway 2.
IP Address
Enter the outside IP address of the tunnel on the AWS platform.
Enter 3.XX.XX.52.
Enter 3.XX.XX.56.
ASN
Enter the BGP ASN of the AWS virtual private gateway.
NoteThis parameter is required when you use BGP dynamic routing.
Enter 64512.
Enter 64512.
Create an IPsec-VPN connection.
In the left-side navigation pane, choose .
On the IPsec Connections page, click Bind VPN Gateway.
On the Create IPsec-VPN Connection page, set the parameters for the IPsec-VPN connection and click OK.
Configuration
Description
Example value
IPsec-VPN Connection Name
Enter a name for the IPsec-VPN connection.
Enter IPsec-VPN connection.
Region
Select the region where the VPN gateway to be associated with the IPsec-VPN connection is deployed.
The IPsec-VPN connection is created in the same region as the VPN gateway.
Select Germany (Frankfurt).
Attach a VPN Gateway
Select the VPN Gateway instance to associate with the IPsec-VPN connection.
Select the created VPN Gateway.
Routing Mode
Select a routing mode.
Destination-based Routing: Routes traffic based on the destination IP address.
Traffic Of Interest Pattern: Provides precise routing and forwarding of traffic based on source and destination IP addresses.
When you use the static routing method in this topic, select the Interested Stream Pattern (Recommended).
Set Local Network to 10.0.0.0/16.
Set Remote Network to 192.168.0.0/16.
In this topic, when you use BGP dynamic routing, select Destination-based Routing (recommended).
Effective Immediately
Select whether the IPsec-VPN connection configuration takes effect immediately. The valid values are:
Yes: Negotiation begins immediately after configuration is complete.
No: Negotiation is triggered by traffic.
Select Yes.
Enable BGP
If the IPsec-VPN connection needs to use BGP, enable BGP. The BGP feature is disabled by default.
Retain the default setting and do not enable BGP. This defaults to static routing. To use BGP dynamic routing after the IPsec-VPN connection is created, you must add the BGP configuration separately.
Tunnel 1
Add VPN configurations for Tunnel 1 (active tunnel).
By default, the system sets Tunnel 1 as the active tunnel and Tunnel 2 as the standby tunnel. This cannot be changed.
Customer Gateway
Add the customer gateway to be associated with the active tunnel.
Select Customer Gateway 1.
Pre-Shared Key
Enter the authentication key for the active tunnel. This key is used for identity authentication.
The key must be 1 to 100 characters long and can contain digits, uppercase and lowercase letters, and the following special characters:
~`!@#$%^&*()_-+={}[]\|;:',.<>/?.If you do not specify a pre-shared key, the system randomly generates a 16-character string as the pre-shared key.
ImportantThe pre-shared key that is configured for the tunnel and its peer gateway device must be the same. Otherwise, the system cannot establish the IPsec-VPN connection.
The authentication key for this tunnel must be the same as the key for the connected AWS tunnel.
Encryption Configurations
Configure IKE, IPsec, DPD, and NAT traversal.
Under IKE Configurations, the SA Life Cycle (seconds) must match the value on the AWS platform. In this topic, the value is set to 28800.
In the IPsec Configurations section, the SA Life Cycle (seconds) must match the value on the AWS platform. In this topic, the value is set to 3600.
For all other parameters, use the default values. For more information about the default values, see IPsec-VPN connections (VPN Gateway).
Tunnel 2
Add VPN configurations for Tunnel 2 (standby tunnel).
Customer Gateway
Add the customer gateway to be associated with the standby tunnel.
Select Customer Gateway 2.
Pre-Shared Key
Enter the authentication key for the standby tunnel. This key is used for identity authentication.
The authentication key for this tunnel must be the same as the key for the connected AWS tunnel.
Encryption Configuration
Configure IKE, IPsec, DPD, and NAT traversal.
For IKE Configurations, the SA Life Cycle (seconds) must match the value on the AWS platform. This topic uses an example value of 28800.
For IPsec Configurations, the SA Life Cycle (seconds) must match the value on the AWS platform. This topic uses a value of 3600.
For all other parameters, use the default values. For more information about the default values, see IPsec-VPN connections (VPN Gateway).
In the Created message, click Cancel.
Configure VPN gateway routes.
Use static routing
After you create an IPsec-VPN connection, you must configure routes for the VPN Gateway instance. If you selected Policy-based Routing for Routing Mode when you created the IPsec-VPN connection, the system automatically creates a policy-based route in the VPN Gateway instance. The route is created in the Unpublished state. You must then publish the route from the VPN Gateway instance to the VPC.
In the left navigation pane, choose .
In the top navigation bar, select the region where the VPN gateway instance resides.
On the VPN Gateways page, click the ID of the target VPN gateway.
On the details page of the VPN gateway, click the Policy-based Route Table tab, find the route that you want to manage, and then click Advertise in the Actions column.
In the Advertise Route dialog box, click OK.
Use BGP dynamic routing
Add BGP configurations to the IPsec-VPN connection.
In the navigation pane on the left, go to .
On the IPsec Connections page, click the ID of the IPsec-VPN connection.
In the IPsec Connections section, turn on Enable BGP. In the BGP Configuration dialog box that opens, configure the required settings and click OK.
Configuration
Description
IPsec-VPN connection configuration
Local ASN
Enter the autonomous system number for the IPsec-VPN connection.
Enter 65530.
Tunnel 1
Add BGP configurations for the active tunnel.
Add BGP configurations for the active tunnel of the IPsec-VPN connection.
Tunnel CIDR Block
Enter the CIDR block used to establish the encrypted tunnel.
Enter 169.254.116.208/30.
Local BGP IP address
Enter the BGP IP address for the IPsec-VPN connection.
This address is an IP address within the tunnel CIDR block.
Enter 169.254.116.210.
Tunnel 2
Add BGP configurations for the standby tunnel.
Add BGP configurations for the standby tunnel of the IPsec-VPN connection.
Tunnel CIDR Block
Enter the CIDR block used to establish the encrypted tunnel.
Enter 169.254.214.96/30.
Local BGP IP address
Enter the BGP IP address for the IPsec-VPN connection.
This address is an IP address within the tunnel CIDR block.
Enter 169.254.214.98.
Enable automatic BGP route propagation for the VPN Gateway instance.
In the navigation pane on the left, choose .
On the VPN Gateways page, find the target VPN gateway instance. In the Actions column, choose .
In the Enable Automatic BGP Propagation dialog box, click OK.
Step 4: Test the connectivity
After the configuration is complete, an IPsec-VPN connection is established between the Alibaba Cloud VPC and the AWS VPC. The following steps describe how to test the connectivity between the VPCs by accessing an AWS EC2 instance from an Alibaba Cloud ECS instance.
Before you test the connectivity, check the access control policies, such as network ACLs and security group rules, that are applied to the VPCs on both the AWS and Alibaba Cloud platforms. Ensure that the policies allow resources in the two VPCs to access each other.
Log on to an ECS instance in the Alibaba Cloud VPC. For more information about how to log on to an ECS instance, see Select a remote connection method for an ECS instance.
On the ECS instance, run the
pingcommand to access the AWS EC2 instance and verify that the two instances can communicate with each other.If the ECS instance receives reply messages from the AWS EC2 instance, the VPCs can communicate with each other.
ping <private IP address of the AWS EC2 instance>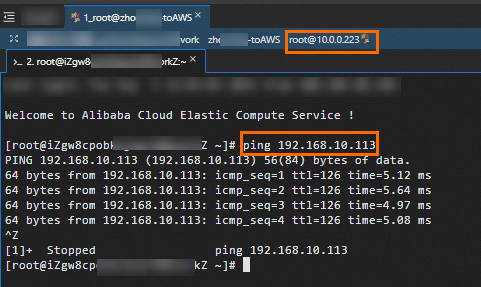
Test the high availability of the IPsec-VPN connection.
A dual-tunnel IPsec-VPN connection provides high availability. If the active tunnel is interrupted, traffic is automatically routed through the standby tunnel. The following steps describe how to verify the high availability of a dual-tunnel IPsec-VPN connection.
Stay logged on to the ECS instance in the Alibaba Cloud VPC.
Run the following command to enable the Alibaba Cloud ECS instance to continuously access the AWS EC2 instance.
ping <private IP address of the AWS EC2 instance> -c 10000Interrupt the active tunnel of the IPsec-VPN connection.
In this topic, the active tunnel is interrupted by modifying its pre-shared key on the Alibaba Cloud side. If the pre-shared keys at both ends of the active tunnel do not match, the tunnel is interrupted.
Check the communication status on the Alibaba Cloud ECS instance. You will notice that communication resumes after a brief interruption. This indicates that traffic is automatically routed through the standby tunnel after the active tunnel is interrupted.
You can monitor the traffic of each tunnel on the Monitoring tab in the Alibaba Cloud console. For more information, see Monitor an IPsec-VPN connection.
What to do next
Depending on your task type, such as data synchronization, data migration, or data validation, add the DTS server IP addresses to the security settings, such as security group rules, firewalls, and whitelists, of the corresponding database.