This topic describes the definition, classification, scenarios, and basic concepts of Resource Access Management (RAM) roles. This topic also describes the process and limits of using RAM roles.
What is a RAM role?
A RAM role is a virtual identity to which policies can be attached. Unlike a RAM user, a RAM role does not have permanent identity credentials, such as a logon password or an AccessKey pair. A RAM role can be used only after the role is assumed by a trusted entity. After a RAM role is assumed by a trusted entity, the trusted entity can obtain a Security Token Service (STS) token and use the STS token to access Alibaba Cloud resources as the RAM role.
RAM role types
RAM roles are classified into the following types based on trusted entities:
RAM role whose trusted entity is an Alibaba Cloud account: RAM users or RAM roles within an Alibaba Cloud account can assume this type of role. RAM users or RAM roles that assume this type of role can belong to their owner Alibaba Cloud accounts or other Alibaba Cloud accounts. This type of RAM role is used for cross-account access and temporary authorization.
RAM role whose trusted entity is an Alibaba Cloud service: Alibaba Cloud services can assume this type of RAM role. RAM roles that a trusted Alibaba Cloud service can assume are classified into two types: normal service role and service-linked role. For more information about service-linked roles, see service-linked roles. This type of RAM role is used to authorize access across Alibaba Cloud services.
RAM role whose trusted entity is an identity provider (IdP): Users of a trusted IdP can assume this type of RAM role. This type of RAM role is used to implement role-based single sign-on (SSO) between Alibaba Cloud and a trusted IdP.
Scenarios
Authorize temporary access
In most cases, we recommend that you call API operations on the server to prevent AccessKey pair leaks. However, in some scenarios, we recommend that you directly upload files from the client to prevent overheads that are caused by resource transfer by using the server. In this case, the server can issue an STS token and the client can use the STS token to directly transfer resources.
For more information, see Use STS tokens to grant mobile apps access to Alibaba Cloud resources.
Grant permissions across Alibaba Cloud accounts
For example, you own Alibaba Cloud accounts Account A and Account B, and you want Account B to access specific resources of Account A. You can create a RAM role whose trusted entity is Account B within Account A and authorize a RAM user or RAM role that belongs to Account B to assume the RAM role whose trusted entity is Account B. Then, you can use the RAM role whose trusted entity is Account B to access specific resources of Account A.
For more information, see Use a RAM role to grant permissions across Alibaba Cloud accounts.
Grant permissions across Alibaba Cloud services
An Alibaba Cloud service may need to access other services to implement a feature. In this case, the Alibaba Cloud service must be authorized to access other services. For example, to retrieve resource lists and log data from Elastic Compute Service (ECS) and ApsaraDB RDS, Cloud Config requires the access permissions on ECS and ApsaraDB RDS. In this case, you can create a RAM role whose trusted entity is an Alibaba Cloud service. We recommend that you use a service-linked role. For Alibaba Cloud services that do not support service-linked roles, use a normal service role.
For more information, see Services that work with service-linked roles.
Implement role-based SSO
If Alibaba Cloud and the identity management system of an enterprise work together to implement role-based SSO, Alibaba Cloud is the service provider (SP) and the identity management system is the IdP. Role-based SSO allows the enterprise to manage users in the local IdP without the need to synchronize users from the IdP to Alibaba Cloud. In addition, employees of the enterprise can access Alibaba Cloud by using a specific RAM role. In this case, you can create a RAM role whose trusted entity is an IdP.
For more information, see Overview of SAML-based SSO and Overview of OIDC-based role SSO.
Terms
Term | Description |
trusted entity | A trusted entity is an entity user who can assume a role. When you create a role, you must specify a trusted entity. A RAM role can be assumed only by a trusted entity. A trusted entity can be an Alibaba Cloud account, Alibaba Cloud service, or IdP. |
Alibaba Cloud Resource Name (ARN) of a RAM role | The Alibaba Cloud Resource Name (ARN) of a RAM role is the globally unique resource identifier of the RAM role. ARNs follow the ARN naming conventions of Alibaba Cloud. An ARN is in the |
policy | A set of permissions that are described based on the policy structure and syntax. You can use policies to describe the authorized resource sets, authorized operation sets, and authorization conditions. A policy is a type of simple language specification that describes a set of permissions. One or more policies can be attached to a RAM role. A RAM role without a policy cannot access Alibaba Cloud resources. |
role assuming | A method that is used by entities to obtain the STS tokens of RAM roles. Valid value:
|
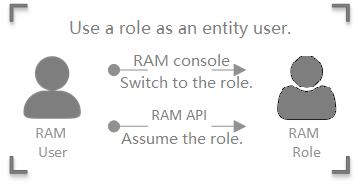
identity switching | Identity switching is the method by which entity users can switch from the logon identity to the role identity in the RAM console. After an entity user logs on to the RAM console, the entity user can switch to a RAM role that the entity user can assume. Then, the entity user can use the RAM role to manage Alibaba Cloud resources. If the entity user no longer requires the role identity, the RAM user can switch back to the logon identity. |
STS token | An STS token is a temporary AccessKey pair for a RAM role. A RAM role does not have a specific logon password or AccessKey pair. If an entity user wants to use a RAM role, the entity user must assume the RAM role to obtain a role token. Then, the entity user can use the role token to call API operations of Alibaba Cloud services. |
Procedure
Log on to the RAM console with an Alibaba Cloud account or as a RAM administrator.
Create a RAM role based on your business requirements.
Grant permissions to the RAM role by attaching system policies or custom policies to it. For more information, see Grant permissions to a RAM role.
A trusted entity can obtain an STS token of the RAM role in the Alibaba Cloud Management Console or by calling an operation. For more information, see the following topics:
The trusted entity assumes the RAM role to access specific Alibaba Cloud resources.
Limitations
For more information about the limits on using RAM roles, see Limitations.