A security group acts as a virtual firewall that can control inbound and outbound traffic for Elastic Compute Service (ECS) instances. Improper configuration of security group rules may cause security risks. You can use the security group check feature that is provided by Cloud Firewall to check for and fix vulnerable security group rules of ECS. This allows you to manage security groups in a more secure and efficient manner. The security group check feature supports both basic and advanced security groups.
Supported editions
Premium Edition, Enterprise Edition, and Ultimate Edition of Cloud Firewall support the security group check feature.
If you use Free Edition of Cloud Firewall, you can click Upgrade Now or Fix in Security Group.
Upgrade Now: You can purchase Premium Edition or a higher edition and use the security group check feature to fix vulnerable security group rules. You can use Cloud Firewall to manage security groups and access control policies of public IP addresses in a centralized manner. This reduces the risks of asset exposure and improves the efficiency of security management. This method is recommended.
Fix in Security Group: For more information, see Modify a security group rule.
Supported check items
The following table describes the supported check items. You can enable the check items based on your business requirements. You can only enable or disable a check item. You cannot modify a check item.
Name | Risk | Handling suggestion |
Open remote O&M ports of Linux servers | Port 22 allows requests from all IP addresses. The associated Linux servers may be cracked. | We recommend that you deny the access of public IP addresses to port 22 on the Security Groups page of the ECS console. If your services require access to port 22, we recommend that you allow only specific public IP addresses to access port 22 or use Bastionhost for remote O&M. For more information, see Introduction to the Basic and Enterprise editions. We recommend that you also enable the threat intelligence and basic protection features on the Protection Configuration page of the Cloud Firewall console. |
Open remote O&M ports of Windows servers | Port 3389 allows requests from all IP addresses. The associated Windows servers may be cracked. | We recommend that you deny the access of public IP addresses to port 3389 on the Security Groups page of the ECS console. If your services require access to port 3389, we recommend that you allow only specific public IP addresses to access port 3389 or use Bastionhost for remote O&M. For more information, see Introduction to the Basic and Enterprise editions. We recommend that you also enable the threat intelligence and basic protection features on the Protection Configuration page of the Cloud Firewall console. |
Open remote O&M ports of DB2 databases | Port 50000 allows requests from all IP addresses. The associated DB2 databases may be cracked. | We recommend that you deny the access of public IP addresses to port 50000 on the Security Groups page of the ECS console. We recommend that you also enable the threat intelligence and basic protection features on the Protection Configuration page of the Cloud Firewall console. |
Excessive security groups | An ECS instance is added to three or more security groups. This makes O&M difficult and increases the risk of incorrect configurations. | We recommend that you add an ECS instance to a maximum of two security groups. For more information, see Overview. We recommend that you also enable the threat intelligence and basic protection features on the Protection Configuration page of the Cloud Firewall console. |
Open remote O&M ports of Elasticsearch | Ports 9200 and 9300 allow requests from all IP addresses. The associated Elasticsearch clusters may be cracked. | We recommend that you deny the access of public IP addresses to ports 9200 and 9300 on the Security Groups page of the ECS console. We recommend that you also enable the threat intelligence and basic protection features on the Protection Configuration page of the Cloud Firewall console. |
Open remote O&M ports of Hadoop YARN | Port 8088 allows requests from all IP addresses. The associated Hadoop YARN may be cracked. | We recommend that you deny the access of public IP addresses to port 8088 on the Security Groups page of the ECS console. We recommend that you also enable the threat intelligence and basic protection features on the Protection Configuration page of the Cloud Firewall console. |
Open remote O&M ports of Hadoop | Ports 50070 and 50030 allow requests from all IP addresses. The associated Hadoop may be cracked. | We recommend that you deny the access of public IP addresses to ports 50070 and 50030 on the Security Groups page of the ECS console. We recommend that you also enable the threat intelligence and basic protection features on the Protection Configuration page of the Cloud Firewall console. |
Open remote O&M ports of MongoDB databases | Port 27017 allows requests from all IP addresses. The associated MongoDB databases may be cracked. | We recommend that you deny the access of public IP addresses to port 27017 on the Security Groups page of the ECS console. We recommend that you also enable the threat intelligence and basic protection features on the Protection Configuration page of the Cloud Firewall console. |
Open remote O&M ports of MySQL databases | Port 3306 allows requests from all IP addresses. The associated MySQL databases may be cracked. | We recommend that you deny the access of public IP addresses to port 3306 on the Security Groups page of the ECS console. We recommend that you also enable the threat intelligence and basic protection features on the Protection Configuration page of the Cloud Firewall console. |
Open remote O&M ports of Oracle databases | Port 1521 allows requests from all IP addresses. The associated Oracle databases may be cracked. | We recommend that you deny the access of public IP addresses to port 1521 on the Security Groups page of the ECS console. We recommend that you also enable the threat intelligence and basic protection features on the Protection Configuration page of the Cloud Firewall console. |
Open remote O&M ports of PostgreSQL databases | Port 5432 allows requests from all IP addresses. The associated PostgreSQL databases may be cracked. | We recommend that you deny the access of public IP addresses to port 5432 on the Security Groups page of the ECS console. We recommend that you also enable the threat intelligence and basic protection features on the Protection Configuration page of the Cloud Firewall console. |
Open remote O&M ports of Redis databases | Port 6379 allows requests from all IP addresses. The associated Redis databases may be cracked. | We recommend that you deny the access of public IP addresses to port 6379 on the Security Groups page of the ECS console. We recommend that you also enable the threat intelligence and basic protection features on the Protection Configuration page of the Cloud Firewall console. |
Open remote O&M ports of SQL Server databases | Port 1433 allows requests from all IP addresses. The associated SQL Server databases may be cracked. | We recommend that you deny the access of public IP addresses to port 1433 on the Security Groups page of the ECS console. We recommend that you also enable the threat intelligence and basic protection features on the Protection Configuration page of the Cloud Firewall console. |
Open remote O&M ports of Spark clusters | Port 6066 allows requests from all IP addresses. The associated Spark clusters may be cracked. | We recommend that you deny the access of public IP addresses to port 6066 on the Security Groups page of the ECS console. We recommend that you also enable the threat intelligence and basic protection features on the Protection Configuration page of the Cloud Firewall console. |
Open remote O&M ports of Splunk instances | Ports 8089 and 8090 allow requests from all IP addresses. The associated Splunk instances may be cracked. | We recommend that you deny the access of public IP addresses to ports 8089 and 8090 on the Security Groups page of the ECS console. We recommend that you also enable the threat intelligence and basic protection features on the Protection Configuration page of the Cloud Firewall console. |
Open ports of security groups | Security groups are configured to allow all IP addresses to access any ports. The associated servers may be cracked. | We recommend that you configure security groups to allow requests from specific IP addresses. We recommend that you also enable the threat intelligence and basic protection features on the Protection Configuration page of the Cloud Firewall console. |
Check for risks in security groups
Log on to the Cloud Firewall console.
In the left-side navigation pane, choose .
On the Security Group Check page, click Obtain Latest Check Results.
The check requires 1 to 5 minutes.
NoteThe latest results are obtained based on the static analysis of security group rules and may not include all port risks. You can view complete check results about port exposure on the Internet Exposure page. For more information, see Internet Exposure.
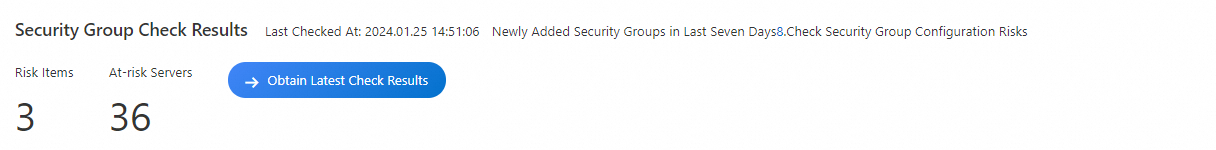
View the check results
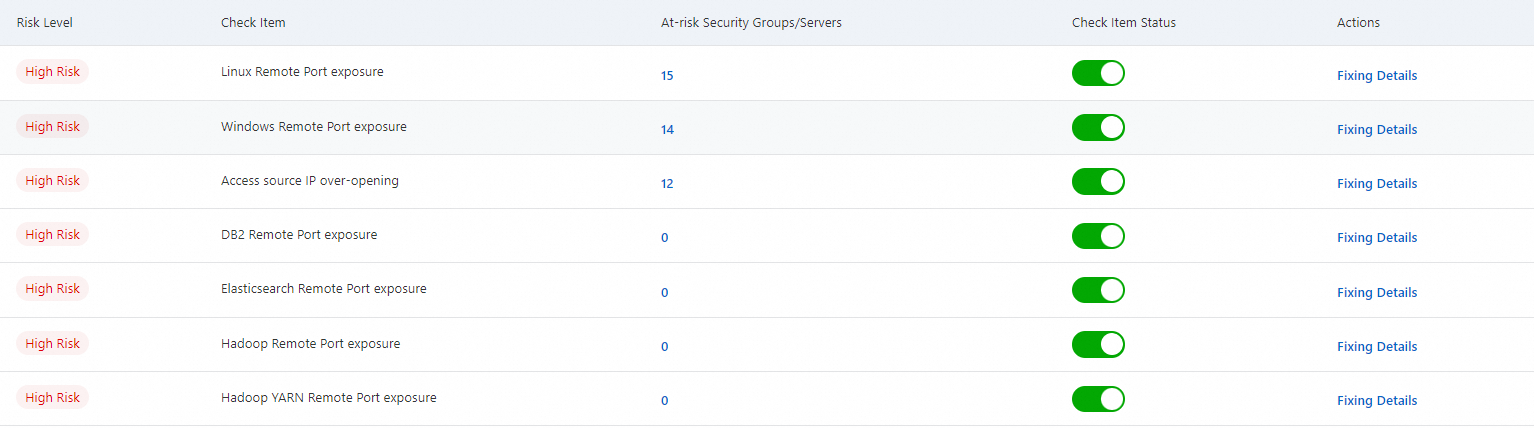
In the Check Result Details section, view the details about the check items based on which security risks are detected. You can view the following information about a check item: Risk Level, Check Item, At-risk Security Groups/Servers, and Check Item Status. If High Risk is displayed in the Risk Level column of a check item, a security group rule is configured to allow the inbound traffic from all IP addresses to all ports, and the associated servers may be cracked.
You can turn on or off Check Item Status based on your business requirements. If you turn off Check Item Status for a check item, the check item is not used.
Modify the security group rules that put your assets at risk
Find the check item that you want to manage and click Fixing Details in the Actions column.
You can also click the number in the At-risk Security Groups/Servers column to go to the Security Group Check page. If the number is greater than 0, you must fix the risks at the earliest opportunity.
On the Security Group Check page, find the security group whose rules you want to modify and click Fix in Security Group in the Actions column.
You can also click the security group ID in the At-risk Security Group ID/Name column to go to the Security Groups page of the ECS console and modify the vulnerable security group rules.
WarningImproper configuration of security group rules may cause security risks. The Security Group Check page provides Fixing Suggestions to modify the security group rules that put your assets at risk. We recommend that you modify the security group rules that put your assets at risk based on the Fixing Suggestions at the earliest opportunity.