This article describes how to configure whitelists for different DataWorks modules. When a DataWorks module, such as Data Integration, Data Service, Metadata Collection, or Data Analysis, accesses your data source, the connection may be blocked if the source is protected by a whitelist. To ensure these modules can connect, add their outbound IP addresses or CIDR blocks to the data source's whitelist.
Background
Different DataWorks modules use different network paths to access data sources. If your data source uses a whitelist, you must grant access differently depending on the module type:
Resource group-dependent modules (such as Data Integration and Data Service): These modules use the resource group's network to access data sources. To run tasks, add the vSwitch CIDR block or public IP address of the resource group to the data source's whitelist.
Platform service modules (such as Metadata Collection and Data Analysis): These modules use service nodes that are independently maintained by DataWorks to send access requests. These nodes operate outside the resource group network. Therefore, also add the platform's dedicated IP CIDR blocks to the data source's whitelist. This practice prevents connection failures caused by an incomplete whitelist.
Prerequisites
Ensure that your data source and the resource group can connect over the network. For more information, see Overview of network connection solutions.
Obtain IP addresses for whitelists
For Data Integration resource groups
Serverless resource group
Get the private IP CIDR block of the resource group
Use this method if your data source and DataWorks are connected over an internal network.
Go to the DataWorks resource group list page. In the top navigation bar, switch to the region where your resource group is located. Then, find your resource group in the list.
Find the target resource group and click Network Settings in the Actions column. This opens the VPC Binding page.
Under Data Scheduling & Data Integration, view the corresponding vSwitch CIDR block.
Add this vSwitch CIDR block to your data source's whitelist.
Get the public IP address of the resource group
This method applies when your data source and DataWorks are connected over the internet. You need to add the EIP of the resource group to the data source's whitelist.
By default, serverless resource groups cannot access the internet. To enable public access to data sources, configure an Internet NAT gateway and an EIP for the VPC bound to the resource group.
Go to the DataWorks resource group list page. In the top navigation bar, switch to the region where your resource group is located. Then, find your resource group in the list.
Find the target resource group and click Network Settings in the Actions column.
Under Data Scheduling & Data Integration, find the bound VPC and click the
 icon next to the VPC to go to the VPC Details page.
icon next to the VPC to go to the VPC Details page.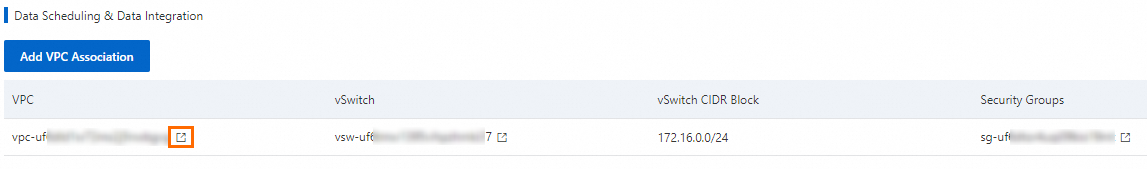
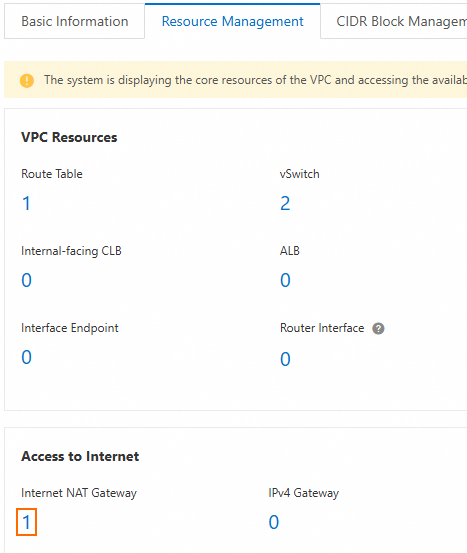
Click the Resource Management tab. In the Access to Internet section, click the number under Internet NAT Gateway to go to the list of Internet NAT gateways created for this VPC.
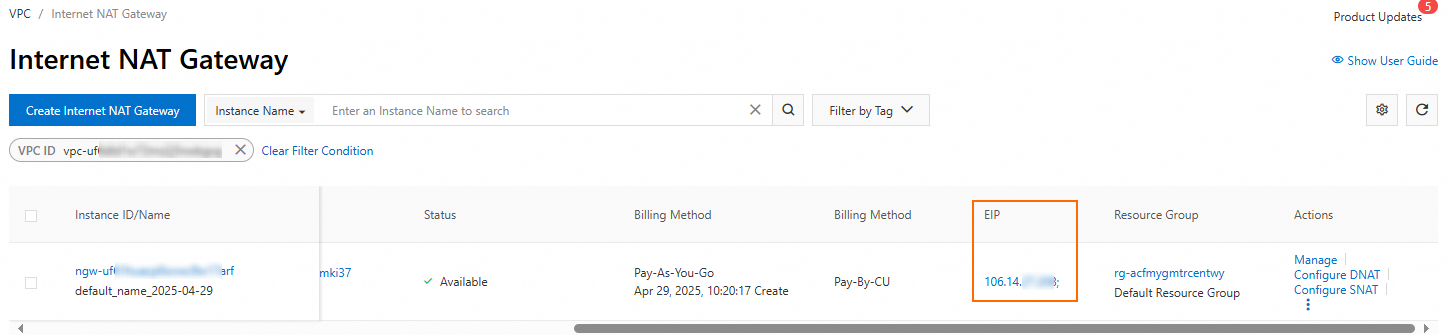
On the Internet NAT gateway list page, view the bound EIPs.
Legacy exclusive Data Integration resource groups
Get the private IP CIDR block of the resource group
Use this method if your data source and DataWorks are connected over an internal network.
Go to the DataWorks resource group list page. In the top navigation bar, switch to the region where your resource group is located. Then, find your resource group in the list.
Find the target resource group and click Network Settings in the Actions column.
Find the VPC bound to the resource group and view its corresponding vSwitch CIDR block.
Get the public IP address of the resource group
This method applies when your data source and DataWorks are connected over the internet. You need to add the EIP of the resource group to the data source's whitelist.
Go to the DataWorks resource group list page. In the top navigation bar, switch to the Region where your resource group is located. Then, find your resource group in the list.
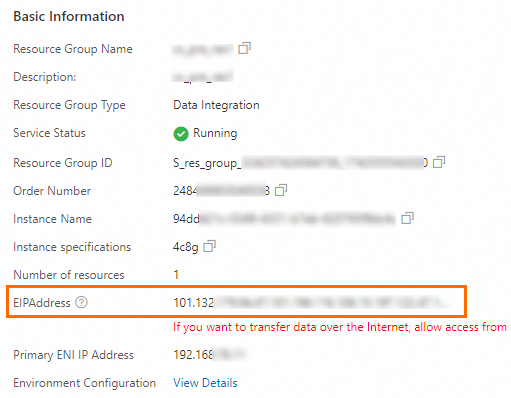
Find the target resource group and click Details in the Actions column. This opens the resource group details page.
Obtain the EIP address.
Shared resource group for Data Integration
If you use a shared resource group for Data Integration, add the IP addresses listed in the whitelist for the shared resource group for Data Integration to your data source's whitelist.
For Data Service whitelists
Serverless resource group
Get the private IP CIDR block of the resource group
Use this method if your data source and DataWorks are connected over an internal network.
Go to the DataWorks resource group list page. In the top navigation bar, switch to the region where your resource group is located. Then, find your resource group in the list.
Find the target resource group and click Network Settings in the Actions column. This opens the VPC Binding page.
Under DataService Studio, view the corresponding vSwitch CIDR block.
NoteIf no VPC and vSwitch are bound under DataService Studio, click Add VPC Association to manually bind them. Then, you can obtain the vSwitch CIDR block.
Add this vSwitch CIDR block to your data source's whitelist.
Get the public IP address of the resource group
This method applies when your data source and DataWorks are connected over the internet. You need to add the EIP of the resource group to the data source's whitelist.
By default, serverless resource groups cannot access the internet. To enable public access to data sources, configure an Internet NAT gateway and an EIP for the VPC bound to the resource group.
Go to the DataWorks resource group list page. In the top navigation bar, switch to the region where your resource group is located. Then, find your resource group in the list.
Find the target resource group and click Network Settings in the Actions column.
Under DataService Studio, find the bound VPC and click the
 icon next to the VPC to go to the VPC Details page.
icon next to the VPC to go to the VPC Details page.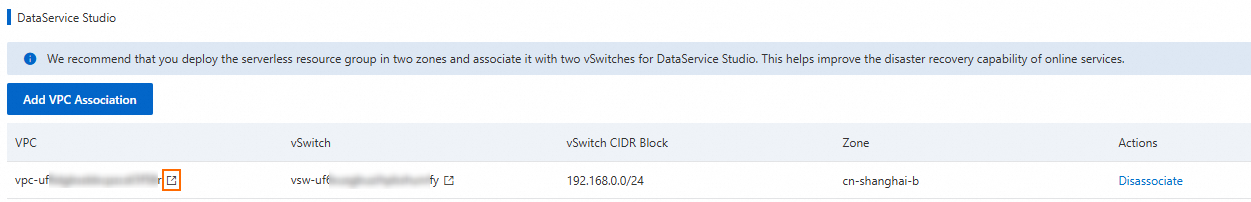
Click the Resource Management tab. In the Access to Internet section, click the number under Internet NAT Gateway to go to the list of Internet NAT gateways created for this VPC.

On the Internet NAT gateway list page, view the bound EIPs.

Legacy exclusive Data Service resource groups
Get the private IP CIDR block of the resource group
Use this method if your data source and DataWorks are connected over an internal network.
Go to the DataWorks resource group list page. In the top navigation bar, switch to the region where your resource group is located. Then, find your resource group in the list.
Find the target resource group and click Network Settings in the Actions column.
Find the vSwitch bound to the resource group. Then, go to the VPC console, search for the vSwitch, and find its IPv4 CIDR.
Shared resource group for Data Service
If you use a shared resource group for Data Service, add the IP addresses from the whitelist for Data Service to your data source's whitelist.
For Metadata Collection whitelists
If your data source for Metadata Collection uses a whitelist for access control, add the IP addresses from the Metadata Collection whitelist to your data source's whitelist.
For Data Analysis whitelists
If the target MaxCompute project for Data Analysis has whitelist-based access control enabled, add the IP addresses listed in the Data Analytics whitelist to the MaxCompute project's whitelist.
Add IP addresses to a whitelist
If your data source is an Alibaba Cloud product, refer to the following documentation to add the obtained IP addresses to the data source's whitelist:
The table below provides links to whitelist configuration guides for some common Alibaba Cloud products. For data sources not listed, consult their official documentation.
If your data source is not an Alibaba Cloud product, consult its official documentation for whitelist configuration instructions.
Configure an IP address whitelist for AnalyticDB for PostgreSQL | |
References
For FAQs about network connectivity, see Resource group operations and network connections.
For FAQs about adding a whitelist, see FAQs about adding a whitelist.