X-Data Security analyzes selected data tables using a large language model, identifies core fields, and intelligently recommends corresponding classifications and grades. You can then apply or reject the recommended identification results. This topic describes how to use X-Data Security.
Prerequisites
X-Data Security must be configured and enabled. For more information, see Intelligent Assistant.
Permissions
Super administrators, security administrators, and custom global roles with the Classification Result-Management permission can use X-Data Security.
Intelligent recommendation flow for data classification and grading
This section describes the end-to-end flow for recommending data classifications and grades using a large language model. The flow consists of the following steps: Configure data scope > Identify core fields > Recommend classification and grading.
Data scope: Select the data scope for which you want intelligent identification results.
Identify core fields: The large language model performs semantic analysis on the selected data assets to identify core fields for subsequent recommendations.
Recommend classification and grading: The service combines classification semantics with sample data to intelligently recommend classifications and grades. This strengthens data security and enhances sensitive data protection.
Procedure
On the Dataphin homepage, in the top menu bar, choose Super X > X-Data Security to open the X-Data Security page.
On the X-Data Security page, manage the recommended classifications and grades to enhance sensitive data protection.
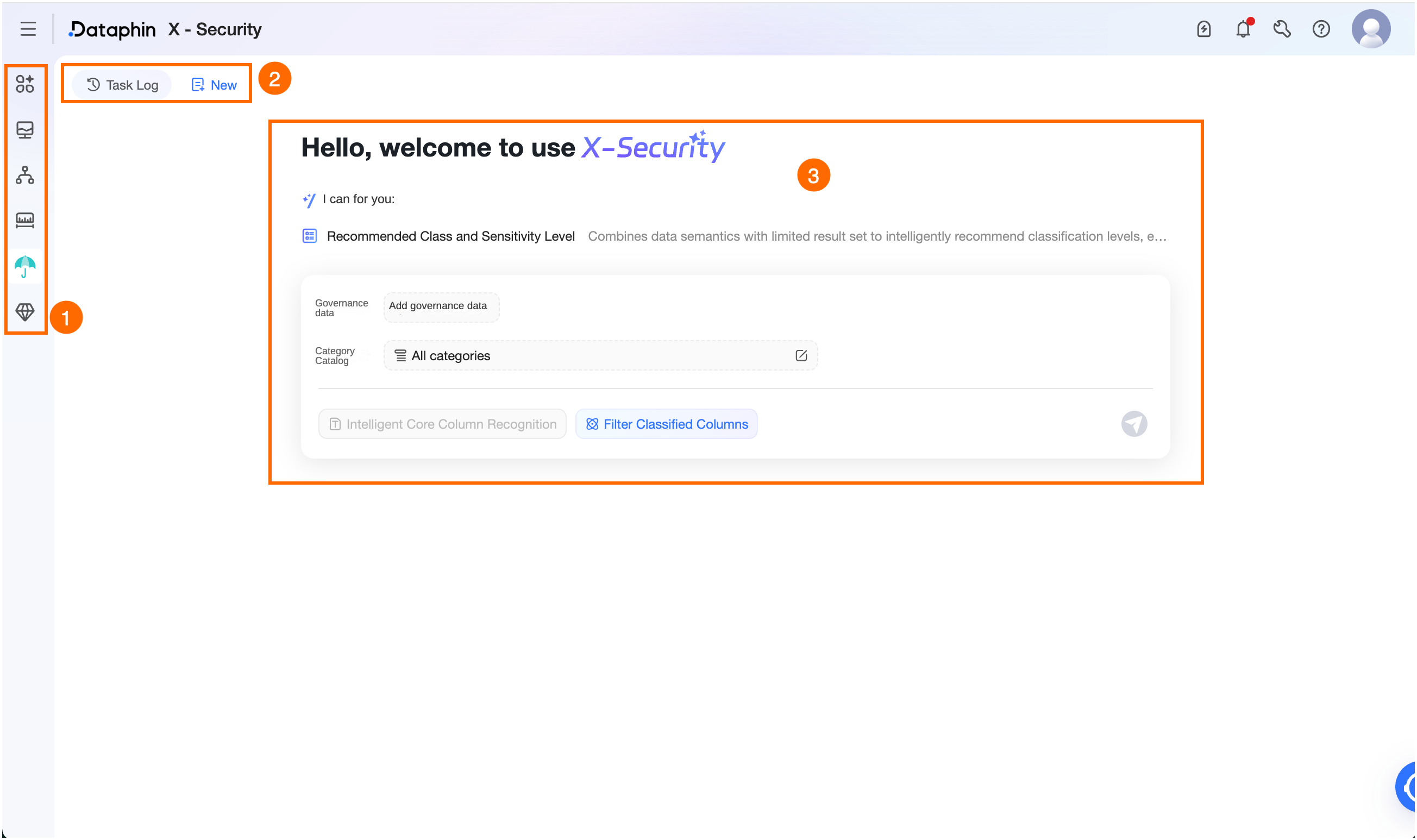
Area
Description
①Intelligent Assistant
Switch between enabled intelligent applications that you have permission to use.
②Task Records/New Task
Task Records: Click Task Records in the upper-left corner. In the Task Records dialog box, view up to 20 task records from the last 7 or 30 days and perform the following operations:
Search and filter: Search for task records by keyword. You can also click the filter icon to filter by governance operation or data source.
Rename: Click the Rename icon next to a task record name to rename it. The name can be up to 256 characters long.
Delete: Click the Delete icon next to a task record name to delete a single task record.
New Task: Click New Task in the upper-left corner to open a new task page.
③Intelligent recommendation for classification and grading
Select the data scope from asset sources for which you want identification results.
Add Data: Add source data for the asset. Projects contain only physical tables, and business segments contain only logical tables. Click Select governed data or the Add Data Source button. In the Add Data Source panel, select an asset object and click OK. You can select up to 5 data sources.
Asset search and filter: Search for assets by keyword. You can also filter by environment or asset type.
Asset rule configuration: After you select an asset, click the Edit icon under Data Scope. In the Data Scope Configuration dialog box, configure the data scope for the asset and click OK.
Data Scope: You can select All Tables or Given Table. If you select Given Table, you can configure filter conditions based on the full table name, asset checklist tag, table description, or db/schema (This property is supported only by the data source origin) to filter assets with finer granularity. You can configure a maximum of 10 filter conditions. The relationship between the filter conditions can be AND or OR.
Full Table Name/Table Description/db/schema: The supported filter conditions are prefix match, suffix match, contains (only for Table Description), and belongs to (only for db/schema).
Prefix Match, Suffix Match, Contains: Enter up to 256 characters.
Belongs To: Select up to 500 asset objects of the corresponding type from the current asset source.
Asset Checklist Tags: The supported filter conditions are Contains any and Contains all.
Contains Any: The condition is met if the asset checklist tags contain any of the selected tag values.
Contains All: The condition is met if the asset checklist tags contain all of the selected tag values.
All Classification Directories: Recommend data classifications for the selected data assets based on the chosen data classification directories. This improves the accuracy of classification and grading. To create a new data classification, click Go To to navigate to the Governance > Data Security > Data Classification page.
Intelligent Core Field Detection: If enabled, the system performs semantic analysis on the selected data scope to detect core fields when a task is executed, and then recommends classifications and grades. If disabled, the system recommends classifications and grades for all fields of the selected asset object.
ImportantIntelligently identifying core fields can reduce interference from irrelevant information. Note that this may also cause some objects that require governance to be overlooked.
Filter Classified Fields: If selected, identification result recommendations are not provided for fields that already have an identification result from automatic or manual identification.
Start Execution: After you configure the data scope, click the
 icon to trigger the task.
icon to trigger the task.For more information about the task execution flow, see Intelligent recommendation flow for data classification and grading. After the task is successfully executed, you can view the intelligent identification results.
Manage identification results
The identification result recommendation list displays the results generated for your configured assets. These results are intelligent recommendations from the large language model based on semantic analysis, classification, and grading.
You can search by the name of a data table, field, or classification. You can also filter by data source or classification directory, or filter for identification results with a status of Pending Review or Application Failed.
The list displays the parent table/data source, field, data classification, data grade, and review status for each identified object.
Parent table/Data source: For Dataphin physical tables, the project name is displayed. For logical tables, the business segment name is displayed. For data sources, the db/schema (parent data source) is displayed. You can click a name to go to the object's details page in Governance > Asset Checklist to view more asset information.
Data classification: You can click a classification name to view the details of the classification that is applied to the object in the View Classification dialog box.
You can perform the following operations on the identification results.
Operation
Description
Application
This operation is available when the review status is Pending Review, Application Failed, or Discarded. This adds the current identification result to the Governance > Data Security > Identification Results list. To apply a single result, click the Apply icon in the Actions column. For batch applications, you can select and apply results with a status of Pending Review or Application Failed.
Discard
This operation is available when the review status is Pending Review or Application Failed. To discard a single identification result, click the Discard icon in the Actions column. For batch discards, you can select and discard results with a status of Pending Review or Application Failed. After a result is discarded, you can apply it again if you make modifications.
Delete Identification Result
This operation is available when the review status is Applied. This deletes the current identification result. You can re-add it on the Data Security page by importing identification results in a batch or by creating an identification rule.