Row-level permissions allow you to control the data access scope for different users on the same table by row. This ensures that different roles can only view the data they need without creating views or splitting into sub-tables, reducing maintenance costs while effectively ensuring data security. This topic describes how to add and manage row-level permissions.
Prerequisites
You have purchased the row-level permission value-added service and the current tenant has enabled the row-level permission feature.
Limits
Super administrators have permissions for all data table rows and columns and are not subject to row-level permission control.
If row-level permissions are enabled for a data table and the table owner is not in the authorization list of row-level permissions, the table owner will not have any row-level permissions for that data table.
Row-level permissions are effective for tables in the compute engine, not for tables in data sources.
In offline development and analysis, you can view and download all row data that you have permissions for (row-level permissions only apply to table data queries, not to table structure modifications, table data modifications, or table deletions).
In offline integration, when the data table source is set to project, you can synchronize row data that you have permissions for.
In folder-data preview, you can view row data that you have permissions for.
When creating behavior relationships and offline views, tenant accounts can read row data that they have permissions for.
When calling APIs, users are not subject to row-level permission control.
Row-level permissions cannot be published across tenants. You must create row-level permissions in the target tenant.
Permission description
System roles including super administrators and security administrators, along with custom global roles with Permission Management-Row-Level Permission Management can add and manage row-level permissions.
Add row-level permissions
On the Dataphin homepage, choose Management Hub > Permission Management from the top navigation bar.
Click Row-Level Permission in the navigation pane on the left. On the Row-Level Permission Management page, click the +Add Row-Level Permission button to go to the Add Row-Level Permission page.
On the Add Row-Level Permission page, configure the parameters.
Parameter
Description
Permission Name
The name of the row-level permission, which must be globally unique and cannot exceed 64 characters.
Description
The description of the row-level permission, which cannot exceed 128 characters.
Control Column
Enter the fields that need to be controlled. You can combine multiple fields from one table for control. The field name and field description cannot exceed 64 characters. The field type can be text type or numeric type.
Click the Add Control Field button to add up to 10 control fields.
Control Rule
Add control rules for the permission. For configuration details, see Create a control rule.
When adding a new rule, the system adds an all-rows-visible rule by default. You can authorize visible users or enable or disable this rule.
Other rules: Support edit and delete operations.
Edit: Modify the configuration information of the rule.
Delete: After deletion, the permissions of users authorized under this rule will be revoked.
Associated Tables
Add tables to be controlled. You can perform go-to-asset and delete operations on added tables. For configuration details, see Add associated tables.
Go to Asset: Navigate to the details page of the current table in the folder to view more information.
Delete: The deletion of a data table cannot be undone.
View Affected Tenant Accounts
If the selected associated tables have downstream tables, enabling row-level permissions may affect the production tasks of downstream tables. It is recommended to add all rows visible permissions to the tenant accounts of the projects where the downstream tables are located. For details, see View affected tenant accounts.
Click OK to complete the row-level permission rule configuration.
Create a control rule
Click the +Create Control Rule button. In the Add Control Rule dialog box, configure the parameters and click OK.
Parameter | Description |
Rule Name | The name of the permission rule. The name must be unique and contain no more than 64 characters. This rule name is displayed when you request permissions for the related data tables. |
Expression | Add an expression for the controlled fields. By default, the system fills in the first control field. You can select all control fields if needed. The supported operators are as follows:
You can add up to 20 rules. Each rule can have a maximum of five relationship layers. The filter condition between rules or relationships is AND or OR. Expression Preview: The system generates an SQL statement in real time based on the expression configuration. |
Authorized Users | Click the Add Authorized Account button to grant permissions to users. The supported account types are Individual Account, Production Account, User Group, and Data Service Application. Click the Save Note You cannot re-authorize users who are already authorized by the current rule. To do so, you must first delete the user and then grant the permission again. |
Add associated tables
Click the +Add Associated Table button. In the Add Associated Table dialog box, configure the parameters and click OK.
You can add up to 50 data tables.
Tables that have already been associated cannot be associated again. If a table's field has already been associated with one control field, it cannot be associated with another control field.
When the associated field of a data table is empty, it cannot be saved. You can use quick filtering to modify it and then save it.
You can search for and associate compute engine source tables and data source tables. The system automatically matches binding fields that have the same name and data type as the control fields. You can modify these matched fields. To add data tables in batches, click Batch Search and Add. In the Batch Search dialog box, you can perform an exact search. For compute engine source tables, use the format `project_name.table_name` or `board_name.table_name`. For data source tables, use the format `DB/Schema.table`. You can separate multiple table names with semicolons (;), commas (,), or line feeds (\n). You can add up to 100 tables.
Associated table list
You can use fuzzy search to find associated tables by data table name, filter associated tables by control field, or quickly filter associated tables with Empty Associated Fields.
The system displays the filtered associated table information, including the associated table name, the board/project/data source to which it belongs, the associated field, and the control field. You can also perform the following operations on the filtered tables.
Operation
Description
Go To Asset
Click the Go To Asset icon to open the table's product page under Administration > Asset Checklist.
Edit
Click the Edit icon to modify the associated fields.
Delete
Click the Delete icon to delete all associated fields in the current table.
View affected tenant accounts
Click the View Affected Tenant Accounts button. In the Affected Tenant Accounts dialog box, configure the parameters and click OK.

Area | Description |
①Search | Search for affected tenant accounts. |
② Affected tenant account list | Displays the tenant account for the project that the node belongs to, the current permissions, and the granted permissions. You can also view the affected descendant tables.
|
③ Authorization | Allows you to grant all row-level rules from the current row-level permission to tenant accounts in batch. The permissions configured here overwrite the permissions configured under Granted Permissions. |
Manage row-level permissions
You can view the configured row-level permission rules, related tables, and other information in the row-level permission management list.
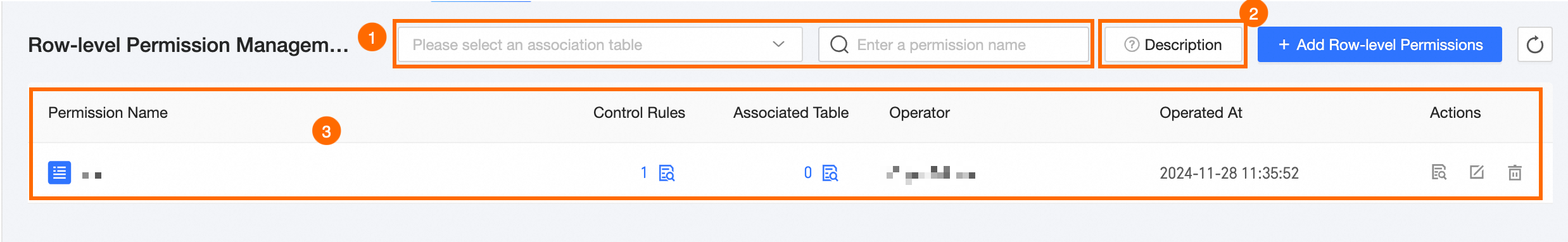
Area | Description |
①Filter and search | You can search by row-level permission name or filter by related table. |
②Description | You can view the introduction to row-level permission principles, including the legend pattern and SQL code.
|
③Row-level permission list | The system displays information about the row-level permission name, control rules, associated tables, operator, and operation time. You can also view, edit, and delete permissions.
|
