Gatekeeper uses Open Policy Agent (OPA) as an admission controller to enforce security policies that suit Kubernetes scenarios. After the Gatekeeper component is introduced in Container Service for Kubernetes (ACK) clusters, you can enable or customize security policies in the ACK console to verify the security of pod deployment and updates.
Introduction to policy governance
PodSecurityPolicy (PSP) is marked as Deprecated in Kubernetes 1.21 and later. Therefore, ACK optimizes the PSP-based policy governance feature. ACK uses OPA as a Gatekeeper admission controller to extend the features related to policy governance status monitoring, log collection, and log retrieval. In addition, a variety of policy libraries are provided to allow you to use more security policies that suit Kubernetes scenarios. You can directly configure security policies in the console, which greatly simplifies policy governance configuration.
Prerequisites
An ACK managed cluster or ACK dedicated cluster is created and the cluster runs Kubernetes 1.16 or later. For more information, see Create an ACK dedicated cluster or Create an ACK managed cluster. For more information about how to update an ACK cluster, see Update an ACK cluster.
When you manage security policies as a Resource Access Management (RAM) user, make sure that the RAM user is granted the following permissions:
cs:DescribePolicies: queries policies.cs:DescribePoliceDetails: queries information about a policy.cs:DescribePolicyGovernanceInCluster: queries information about policies in a cluster.cs:DescribePolicyInstances: queries a policy instance that is deployed in a cluster.cs:DescribePolicyInstancesStatus: queries information about policy instances in a cluster.cs:DeployPolicyInstance: deploys a policy instance in a cluster.cs:DeletePolicyInstance: deletes policy instances in a cluster.cs:ModifyPolicyInstance: modifies a policy instance in a cluster.
For more information about how to create custom RAM policies, see Create a custom RAM policy.
Considerations
The policy governance feature is applicable only to Linux nodes.
The policy governance feature does not allow you to configure custom policies. You can use only the predefined policies of ACK.
Step 1: Install or update the policy governance components
To enable the policy governance feature, you need to install the following components:
gatekeeper: an OPA-based Kubernetes admission controller. You can use this component to manage and enforce security policies executed by OPA in ACK clusters. This allows you to manage namespace labels.
NoteYou can use only the gatekeeper component provided by ACK. If you use a gatekeeper component that is not provided by ACK, uninstall it and then install the component provided by ACK. For more information about the release notes for the gatekeeper component, see gatekeeper.
logtail-ds: a log component. This component can be used to collect and retrieve blocking or alerting events that are generated due to security policy compliance issues.
policy-template-controller: a Kubernetes controller developed based on Alibaba Cloud security policy templates. You can use this component to manage the status of ACK clusters and policy instances deployed from different policy templates.
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, click the name of the cluster that you want to manage and choose in the left-side navigation pane.
On the Policy Governance page, follow the on-screen instructions to install or update the components.
Step 2: Work with the policy governance feature
Platform
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, click the name of the cluster that you want to manage and choose in the left-side navigation pane.
On the Policy Governance page, follow the on-screen instructions to install or update the components, and then perform the following operations on demand.
View information about security policies in the current cluster
You can click the Overview tab to view information about security policies in the current cluster.
An overview of security policies in the cluster, including the numbers of high-risk policies, high-risk policies that are enabled, medium-risk policies, and medium-risk policies that are enabled. Security policies that the system suggests you to enable are also listed.
The numbers of blocking events and alerting events that are generated within the previous seven days.
The policy enforcement records within the previous seven days. By default, the table displays the most recent 100 blocking or alerting events within the previous seven days. To view more events, move the pointer over the
 icon next to Actions within Last 7 Days and click the Simple Log Service hyperlink in the pop-up message to log on to the Simple Log Service console and view all logs in the corresponding Logstore.
icon next to Actions within Last 7 Days and click the Simple Log Service hyperlink in the pop-up message to log on to the Simple Log Service console and view all logs in the corresponding Logstore. 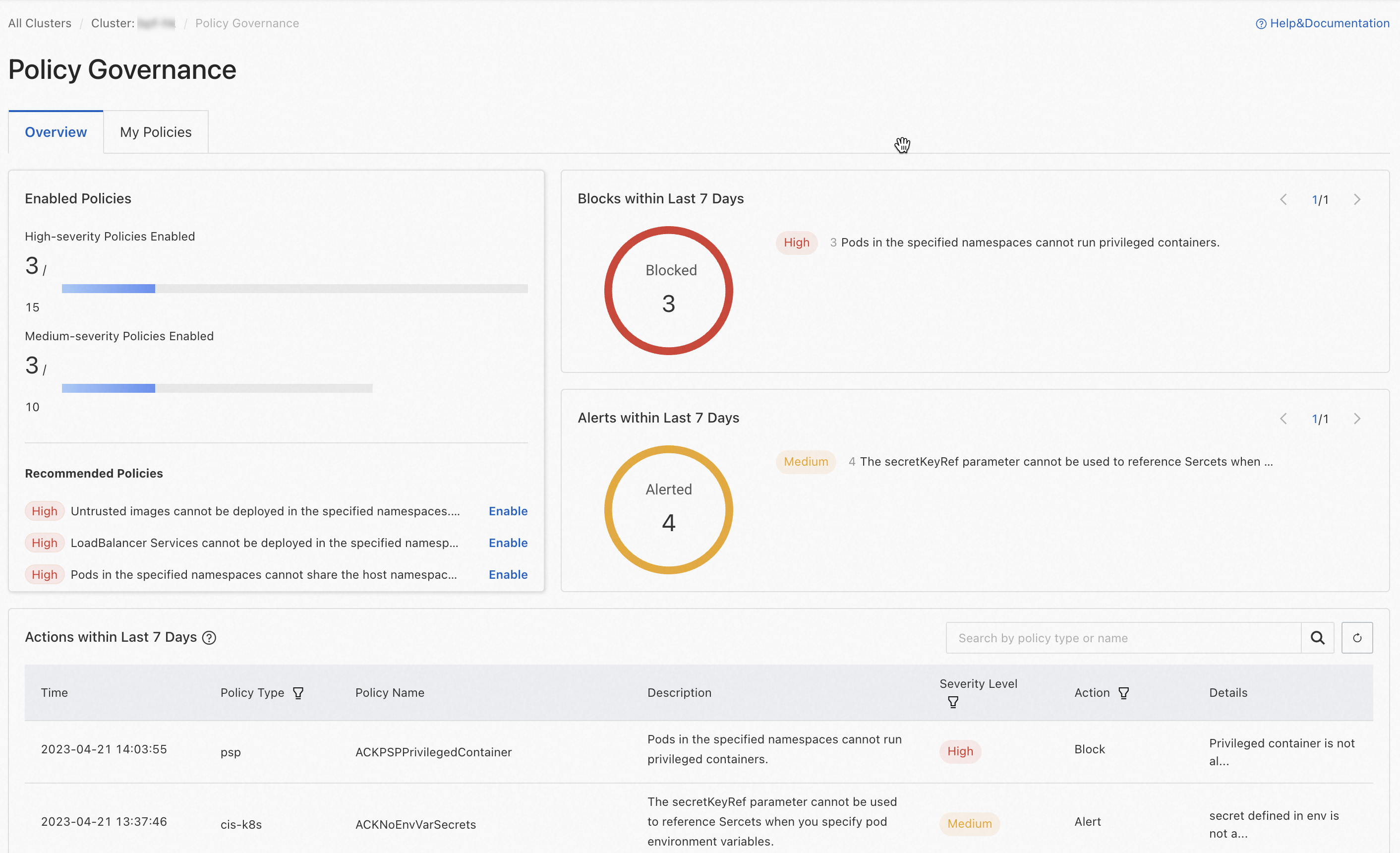
Create and manage policy instances
Click the My Policies tab. Then, click Create Policy Instance and configure parameters in the Create Policy Instance dialog box.
Parameter | Description |
Policy Type | Select a policy type. Valid values:
|
Action |
|
Policy Name | Select a policy name from the drop-down list. |
Applicable Scope | Select the namespaces to which you want to apply the policy instance. |
Parameters |
|
View policies and policy instances in the current cluster
Click the My Policies tab to view all policies in the current cluster.
You can click the filter conditions in the upper-right corner of the list to filter policies. Enabled policies are displayed at the top of the list. The Instances column displays the number of policy instances deployed for each policy.
If the number of policy instances is zero, the corresponding policy is not deployed in the cluster. You can click Enable in the Actions column of the policy to configure and deploy policy instances.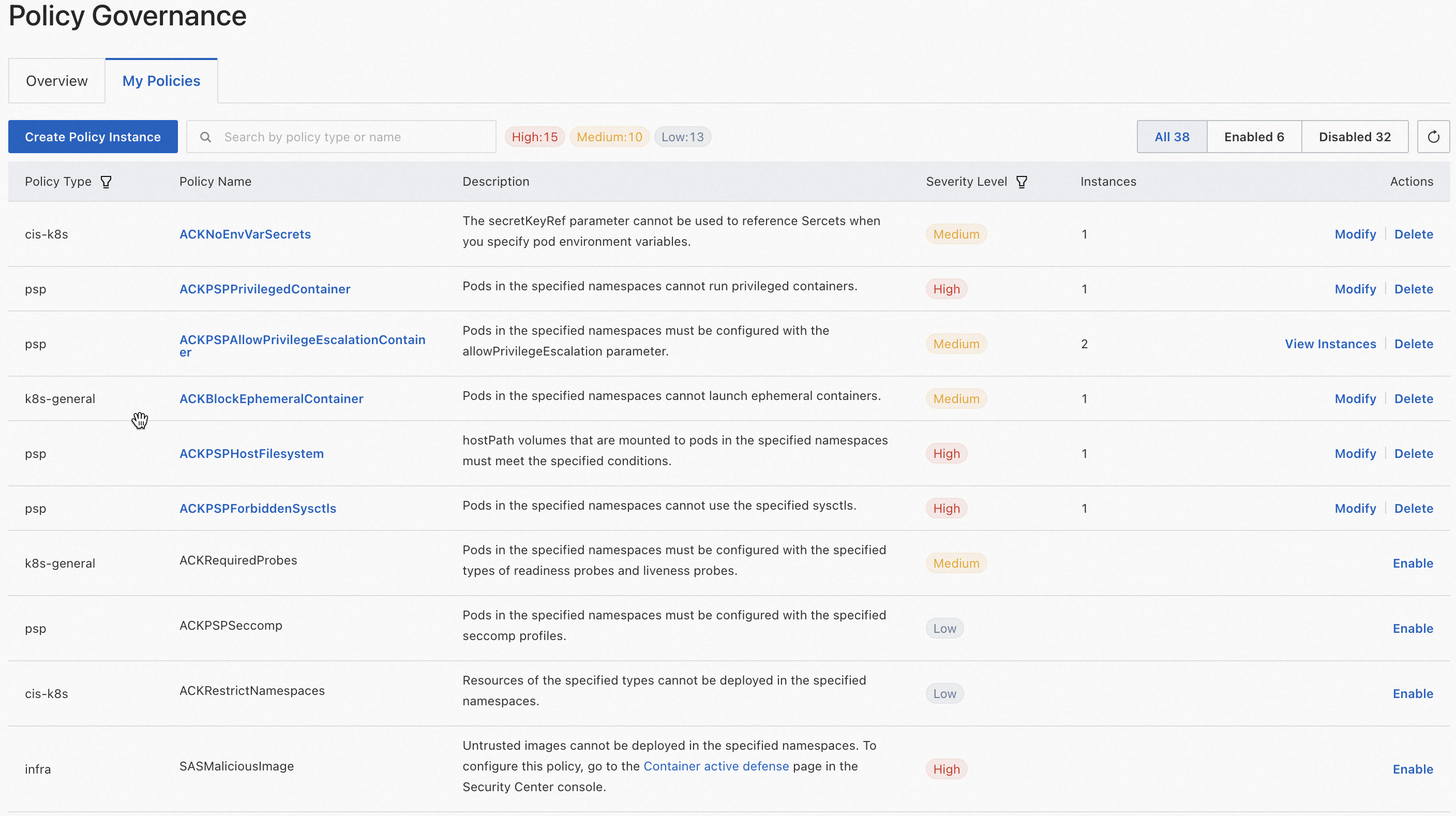
To modify the configuration of policy instances, click Modify in the Actions column.
If more than one policy instance is deployed for a policy, you can click View Instances in the Actions column and click Modify to modify the configuration.
To delete all policy instances deployed for a policy, click Delete in the Actions column.
For more information about security policies and their templates, see Predefined security policies of ACK.
References
For more information about the predefined security policies supported by policy governance, including Compliance, Infra, K8s-general, and PSP, see Predefined security policies of ACK.
You can configure cluster inspection to identify potential security risks in workload configurations in your cluster. For more information, see Use the inspection feature to detect security risks in the workloads of an ACK cluster.