This topic describes how to synchronize users or groups in Microsoft Entra ID (formerly Azure AD) to CloudSSO by using System for Cross-domain Identity Management (SCIM).
Prerequisites
All configuration operations within Microsoft Entra ID must be performed by a user with the Global Administrative role. To learn how to create a user and assign it the administrator role in Microsoft Entra ID, please refer to the official Microsoft Entra ID documentation.
Step 1: Create SCIM credentials in the CloudSSO console
Log on to the CloudSSO console.
In the left-side navigation pane, click Settings.
In the SCIM-based User Synchronization Configuration section of the User Settings tab, click Generate New SCIM Credential.
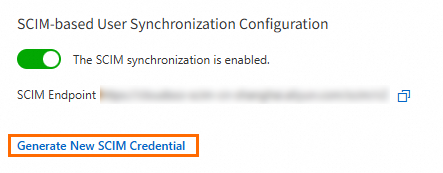
In the SCIM Credential Generated dialog box, copy the generated SCIM credential and click OK.
Step 2: Enable SCIM synchronization in the CloudSSO console
Log on to the CloudSSO console.
In the left-side navigation pane, click Settings.
In the SCIM-based User Synchronization Configuration section of the Settings page, turn on the switch.
Copy and save the SCIM endpoint for later use.
Step 3: Configure SAML in Microsoft Entra ID
Log on to the Azure portal as the global administrator of Microsoft Entra ID.
In the upper-left corner of the homepage, click the
 icon.
icon. In the left-side navigation pane, choose .
Click New application.
On the Browse Microsoft Entra App Gallery page, click Create your own application.
In the Create your own application panel, enter a name for your application. In this example, enter CloudSSODemo. Then, select Integrate any other application you don't find in the gallery (Non-gallery) and click Create.
Step 4: Assign users or groups to the application in Microsoft Entra ID
On the CloudSSODemo details page, in the left-side navigation pane, choose .
On the page that appears, click Add user/group.
Select users or groups.
Click Assign.
Step 5: Configure SCIM synchronization in Microsoft Entra ID
In the left-side navigation pane of the CloudSSODemo page, choose .
Click New configuration in the upper-left corner to create a provisioning configuration and configure administrator credentials.
Enter the SCIM endpoint for Tenant URL.
To obtain the endpoint, go to the Settings page of the CloudSSO console and copy the value of SCIM Endpoint.
Enter a SCIM credential for Secret token.
To obtain the credential, perform the operations in Step 1: Create SCIM credentials in the CloudSSO console.
Click Test Connectivity.
If the test is successful, click Create.
In the left-side navigation pane of the Provisioning page, choose .
In the Mappings section, configure attribute mappings.
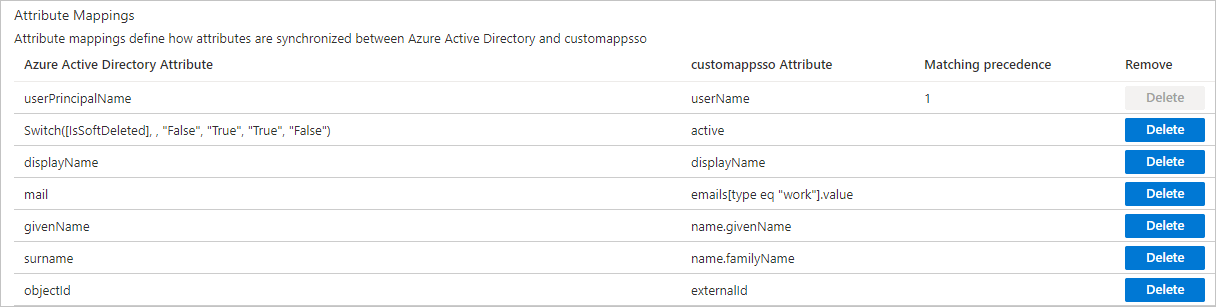
Click Provision Microsoft Entra ID Users to configure attribute mappings for users.
On the page that appears, find externalId in the customappsso Attribute column and click the value in the Azure Active Directory Attribute column. Then, change the value of Source attribute to objectId.
Retain only the attribute mappings shown in the following figure and delete all other attribute mappings.
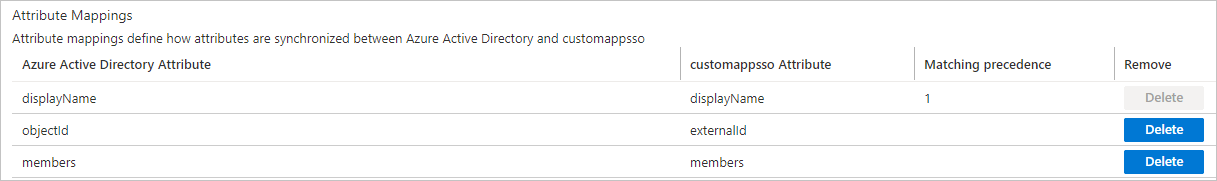
Click Provision Microsoft Entra ID Groups to configure attribute mappings for groups. Retain only the attribute mappings shown in the following figure and delete all other attribute mappings.
NoteThe names of CloudSSO users and user groups have requirements on characters. If the name of an Microsoft Entra ID user or user group contains characters that are not supported in the names of CloudSSO users or user groups, the mapping fails. To handle the failure, click displayName in the Azure Active Directory Attribute column. Then, set Mapping type to Expression and enter an expression for Expression. The expression that you enter is applied to remove the unsupported characters or replace the unsupported characters with supported characters. For more information, see Microsoft Entra ID documentation.
In the Settings section, select Sync only assigned users and groups for Scope.
In the Provisioning Status section, turn on the switch.
Click Save.
Go to the Overview page, refresh the page, and then view the synchronization results.
Verify the synchronization results
Log on to the CloudSSO console.
Go to the User or Group page to view the synchronized users or groups.
Source for the synchronized users or groups is automatically displayed as SCIM Synchronization. For more information, see View user information and View the information about a group.