A VPC Firewall helps you inspect and control traffic between network instances connected through Cloud Enterprise Network (CEN) or Express Connect. By default, the firewall allows all traffic. You can use access control policies to manage traffic between instances, allowing trusted connections and blocking suspicious or malicious activity. This topic describes how to configure access control policies for a VPC Firewall.
Prerequisites
A VPC Firewall is created and enabled. For more information, see Configure a VPC Firewall for an Enterprise Edition transit router.
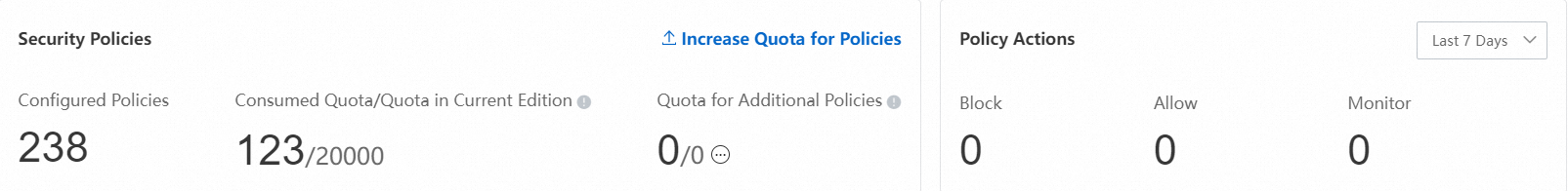
You have a sufficient quota for access control policies. You can view your current quota usage on the page. For details on how policy quotas are calculated, see Overview of Access Control Policies.
If your policy quota is insufficient, click Increase Quota to purchase more Quota for Additional Policy capacity. For more information, see Purchase Cloud Firewall.
Configure an access control policy
To manage traffic between two VPCs, you can use either a blacklist or a whitelist. In blacklist mode, you configure a policy to deny untrusted or unnecessary traffic for your workloads and another policy to allow all other traffic. In whitelist mode, you configure a policy to allow trusted or required traffic for your workloads and another policy to deny all other traffic. For examples of how to configure access control policies for VPC firewalls, see Examples of access control policy configurations.
Log on to the Cloud Firewall console.
In the navigation pane on the left, choose .
On the VPC Border page, switch to the business instance where you want to configure a policy.
Click Create Policy, configure the policy according to the following table, and then click OK.
Configuration item
Description
Source Type
The initiator of the network connection. Select a source type and specify the source address that sends traffic based on the source type.
If you set Source Type to IP, you must enter CIDR blocks. Enter CIDR blocks in standard format, such as 192.168.0.0/16. You can enter up to 2,000 CIDR blocks. Separate multiple CIDR blocks with commas (,).
If you enter multiple CIDR blocks at a time, Cloud Firewall automatically creates an address book that includes the entered CIDR blocks. When you save the access control policy, Cloud Firewall prompts you to specify a name for this address book.
If you set Source Type to Address Book, you must create an address book in advance. For more information, see Address book management.
Source
Destination Type
The receiver of the network traffic. Select a destination type and specify the destination address based on the destination type.
If you set Source Type to IP, you must enter CIDR blocks. Enter CIDR blocks in standard format, such as 192.168.0.0/16. You can enter up to 2,000 CIDR blocks. Separate multiple CIDR blocks with commas (,).
If you enter multiple CIDR blocks at a time, Cloud Firewall automatically creates an address book that includes the entered CIDR blocks. When you save the access control policy, Cloud Firewall prompts you to specify a name for this address book.
If you set Destination Type to Address Book, you can select an existing address book, such as an IPv4 address book or a domain name address book.
If you have not created an address book, you can click Create Address Book to create an IPv4 address book or a domain name address book for this policy. For more information about address books, see Address book management.
If you set Destination Type to Domain Name, you need to select a domain name recognition mode. Three modes are available:
FQDN-based Resolution (Extract Host or SNI Field in Packets): We recommend that you select this mode to manage traffic of the HTTP, HTTPS, SMTP, SMTPS, SSL, POPS, and IMAPS protocols.
DNS-based Dynamic Resolution: We recommend that you select this mode to manage traffic of protocols other than HTTP, HTTPS, SMTP, SMTPS, SSL, POPS, and IMAPS.
ImportantThis mode does not support wildcard domain names or wildcard domain names in address books.
FQDN-based And DNS-based Dynamic Resolution: We recommend that you select this mode to manage traffic of the HTTP, HTTPS, SMTP, SMTPS, SSL, POPS, and IMAPS protocols if some or all of the traffic does not contain HOST or SNI fields.
ImportantThis mode takes effect only when the strict mode is enabled for ACL Engine Management. This mode does not support wildcard domain names or wildcard domain names in address books.
Destination
Protocol Type
The transport-layer protocol. Valid values: TCP, UDP, ICMP, and ANY. If you are not sure about the protocol, select ANY.
Port Type
Set the destination port type and destination port.
If you set Port Type to Port, you need to enter a port range. Separate the start port and end port with a forward slash (/). Examples: 22/22 and 80/88. You can add up to 2,000 port ranges. Separate multiple port ranges with commas (,).
If you enter multiple port ranges, Cloud Firewall automatically creates an address book that includes the entered port ranges. When you save the access control policy, Cloud Firewall prompts you to specify a name for this address book.
Address Book: If you set Port Type to Address Book, you must create a port address book in advance. For more information, see Address book management.
Port
Application
Set the application type of the access traffic. You can select multiple application types.
If you set Protocol Type to TCP:
If you set Destination Type to IP or IP Address Book, you can select all applications.
If you set Destination Type to Domain Name or Domain Name Address Book:
If you set Domain Name Mode to FQDN-based Dynamic Resolution (Extract Host and SNI Fields), you can select only HTTP, HTTPS, SMTP, SMTPS, SSL, POPS, and IMAPS.
If you set Domain Name Mode to DNS-based Dynamic Resolution, you can select all applications.
If you set Protocol Type to UDP, you can set Application to ANY or DNS.
If you set Protocol Type to ICMP or ANY, you can set Application only to ANY.
NoteCloud Firewall identifies applications based on packet features. The protocol is not identified based on the port. If Cloud Firewall fails to identify an application, the session traffic is allowed. If you want to block traffic of unknown application types, enable the strict mode for the Internet firewall. For more information, see Introduction to modes of the access control engine.
Action
Set the action on the traffic that matches the policy.
Allow: allows the traffic.
Deny: blocks the traffic and does not send a notification.
Monitor: In this mode, traffic is allowed by default. You can filter and observe this traffic using the relevant fields in traffic logs. After a period of observation, you can change the action to Allow or Deny as needed.
Description
Enter a description for the policy. This helps you quickly identify the purpose of each policy.
Priority
Select the priority of the policy. The default value is Last, which indicates the lowest priority.
First: The access control policy has the highest priority and takes effect first.
Last: The access control policy has the lowest priority and takes effect last.
Policy Validity Period
Set the validity period for the policy. The policy can match traffic only within the validity period.
Always
One-Time: Select a single time period.
Recurring: Select a recurring time period and effective dates.
NoteThe start time of the effective date must be earlier than the end time. The policy is expected to take effect in 3 to 5 minutes.
If you select Repeat Indefinitely, the end time is automatically set to 2099-12-31.
Related FAQ: Does a policy take effect if the recurrence cycle spans multiple days?
Status
Set whether to enable the policy. If you do not enable the policy when you create it, you can enable it in the policy list.
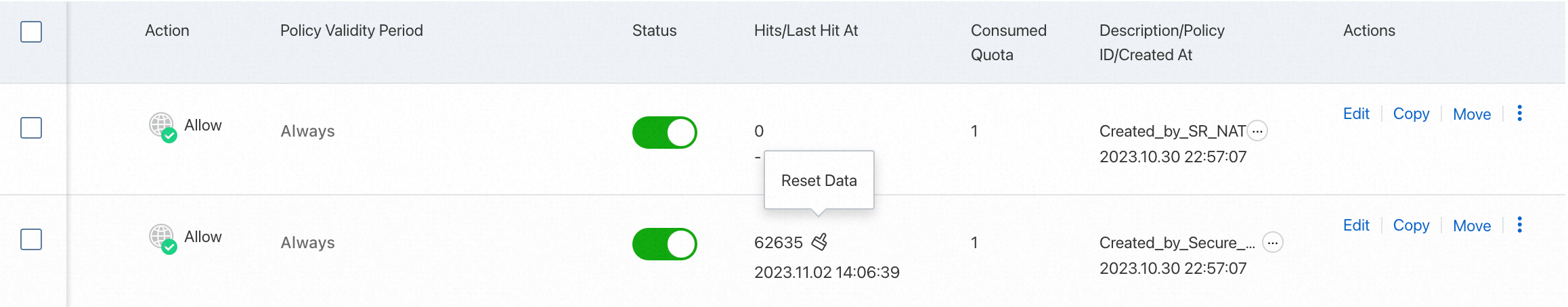
View policy hits
After your service has been running for a period of time, you can view the hit count and last hit time of access control policies in the Hits/Last Hit At column of the access control policy list.
Click the hit count to view the traffic logs on the Traffic Logs page. For more information, see Log audit.
Related operations
After you create a policy, you can Edit, Delete, Copy, or Move it from the access control policy list. Moving a policy changes its priority.
Policy priority is set as a number from 1 to N, where N is the total number of policies. A smaller number indicates a higher priority. When you move a policy, its priority is updated, and the priorities of other policies are adjusted accordingly.
If you delete a policy, Cloud Firewall will no longer control the traffic that the policy managed. Proceed with caution.
Related documents
How can I increase the protected traffic throughput between VPCs?
For more information, see Configure access control policies.
For more information about how access control policies work, see Overview of access control policies.
For more information about how to view and manage IP address books, port address books, and domain address books in access control policies, see Manage address books.
For more information about how to configure and use access control policies, see FAQ about access control policies.