Cloud Enterprise Network (CEN) supports communication, isolation, and policy redirection for virtual private clouds (VPCs) within the same region. This topic explains how to configure CEN to allow isolated VPCs to access a shared VPC.
You can run the sample code with one click.
Background
The following scenario is used as an example in this topic. An enterprise has deployed three VPCs in the China (Hangzhou) region. VPC 3 serves as the shared VPC. The enterprise wants to enable VPC 1 and VPC 2 to access VPC 3 while VPC 1 and VPC 2 remain isolated.

Networking
To allow VPC 1 and VPC 2 to access VPC 3, perform the following operations to configure the features provided by CEN, such as custom route tables, associated forwarding, and route learning:

When you attach VPC 3 to the transit router, enable the Associate with Default Route Table of Transit Router and Propagate System Routes to Default Route Table of Transit Router advanced features.
After these features are enabled, the default route table of the transit router automatically learns the system routes of VPC 3. VPC 3 can forward network traffic by querying the default route of the transit router.
When you attach VPC 1 and VPC 2 to the transit router, enable only the Propagate System Routes to Default Route Table of Transit Router advanced feature. Then, add a route that points to VPC 3 to a custom route table of the transit router, and associate VPC 1 and VPC 2 with the custom route table.
This way, the default route table of the transit router can learn the system routes of VPC 1 and VPC 2. VPC 1 and VPC 2 can forward traffic to VPC 3 by querying the custom route table. In this case, VPC 1 cannot communicate with VPC 2.
Add route 0.0.0.0/0 to the route tables of VPC 1, VPC 2, and VPC 3, and set the next hop to the route that points to the transit router.
In this example, three VPCs are created in the China (Hangzhou) region and vSwitches are created in specified zones of the region. The following table describes the CIDR blocks of the VPCs:
ImportantEnsure that the CIDR blocks of the VPCs do not overlap.
VPC
vSwitch
vSwitch Zone
CIDR block
ECS IP address
VPC 1
Primary CIDR block: 192.168.0.0/16
vSwitch 1
Zone A
192.168.0.0/24
192.168.0.224
vSwitch 2
Zone B
192.168.1.0/24
VPC 2
Primary CIDR block: 172.16.0.0/16
vSwitch 3
Zone A
172.16.0.0/24
172.16.0.222
vSwitch 4
Zone B
172.16.1.0/24
VPC 3
Primary CIDR block: 10.0.0.0/16
vSwitch 5
Zone A
10.0.0.0/24
10.0.0.112
vSwitch 6
Zone B
10.0.1.0/24
Procedure
This topic provides two configuration methods: console and Terraform. Choose the method that suits your needs.
Console
Step 1: Create a CEN instance
To connect network instances, you must create a CEN instance.
Log on to the CEN console.
On the Instances page, click Create CEN Instance.
In the Create CEN Instance dialog box, set the following parameters and click OK:
Name: Enter a name for the CEN instance.
Description: Enter a description for the instance.
Step 2: Attach VPCs to the CEN instance
On the Instances page, click the ID of the CEN instance.
On the Basic Information tab of the CEN instance, click the
 icon under VPC.
icon under VPC.On the Connection with Peer Network Instance page, set the following parameters and click OK:
Network Type: By default, Virtual Private Cloud (VPC) is selected.
Region: Select the region where the network instance is located. For this example, choose China (Hangzhou).
Transit Router: The system automatically creates a transit router in the selected region.
Resource Owner UID: Select the Alibaba Cloud account to which the VPC belongs. The default value Current Account is used.
Billing method: Select the default Pay-As-You-Go option.
Attachment Name: Enter a name for the connection.
Network Instance: Select the ID of the VPC to be connected. VPC 3 is chosen in this example.
VSwitch: Select a vSwitch in a zone that is supported by the transit router.
If the Enterprise Edition transit router is deployed in a region that supports only one zone, select a vSwitch in the zone.
If the Enterprise Edition transit router is deployed in a region that supports multiple zones, select at least two vSwitches. The two vSwitches must be in different zones. The two vSwitches support zone-disaster recovery to ensure uninterrupted data transmission between the VPC and the transit router.
We recommend that you select a vSwitch in each zone to reduce network latency and improve network performance because data can be transmitted over a shorter distance.
Advanced Settings: By default, the system automatically selects the following advanced features. In this example, only Associate with Default Route Table of Transit Router and Propagate System Routes to Default Route Table of Transit Router are selected for VPC 3.
Associate with Default Route Table of Transit Router
After this feature is enabled, the VPC connection is automatically associated with the default route table of the transit router. The transit router forwards the traffic of the VPC based on the default route table.
Propagate System Routes to Default Route Table of Transit Router
After this feature is enabled, the system routes of the VPC are advertised to the default route table of the transit router. This way, the VPC can communicate with other network instances that are connected to the transit router.
Automatically Creates Route That Points to Transit Router and Adds to All Route Tables of Current VPC
After this feature is enabled, the system automatically adds the following three routes to all route tables of the VPC: 10.0.0.0/8, 172.16.0.0/12, and 192.168.0.0/16. The next hops of the routes point to the VPC. The routes are used to forward IPv4 traffic from the VPC to the transit router. By default, transit routers do not advertise routes to VPCs.
ImportantIf such a route is already in the route table of the VPC, the system cannot advertise this route. You must manually add a route that points to the VPC connection to the route table of the VPC. Otherwise, network communication cannot be established between the VPC and the transit router. To check whether such routes exist, click Check Route below Advanced Settings.
In order for the VPC to have IPv6 traffic enter and be forwarded, it is necessary to enable route synchronization for the VPC connection or manually add IPv6 route entries pointing to the VPC connection in the route table after creating the connection.
After you attach VPC 3 to the CEN instance, click Create More Connections.
After creating the VPC connections, click Return to the List to go back to the CEN instance details page.
Step 3: Associate VPC 1 and VPC 2 with a custom route table
On the details page of the CEN instance, click the ID of the transit router.
On the details page of the transit router, click the Route Table tab.
In the left-side section, click Create Route Table.
In the Create Route Table dialog box, set the following parameters and click OK:
Transit Router: The system automatically selects the transit router in the current region.
Route Table Name: Enter a name for the route table.
Route Table Description: Enter a description for the route table.
Multi-region ECMP Routing: Keep the default value.
Click View Route Table Details to return to the Route Table tab.
On the Route Table tab, choose the route table created in the previous step, click the Route Table Association tab, and then click Create Association.
In the Add Association dialog box, select the network instance connection to associate with the custom route table, and click OK.
In this example, VPC 1 and VPC 2 are associated with the custom route table to forward traffic by querying the custom route table.
On the details page of the custom route table, click the Route Entry tab, and then click Add Route Entry.
In the Add Route Entry dialog box, set the following parameters and click OK:
Route Table: The system defaults to the current custom route table.
Transit Router: The system selects the current custom route table by default.
Name: Enter a name for the route entry.
Destination CIDR Block: Enter a destination CIDR block for the route entry. 10.0.0.0/16 is used in this example.
Blackhole Route: If you select Yes, the traffic that is destined for this route is dropped. In this example, No is selected.
Next Hop: Select the next hop for the route entry. VPC 3 is selected in this example.
Description: Enter a description for the route entry.
Step 4: Add a default route to the VPCs
Add a default route with the destination CIDR block of 0.0.0.0/0 and the next hop as the transit router to the route tables of VPC 1, VPC 2, and VPC 3.
Log on to the VPC console.
In the left-side navigation pane, click Route Tables.
In the top navigation bar, select the region to which the route table belongs.
On the Route Tables page, click the ID of the route table.
In this example, the route table of VPC 3 is selected.
On the route table details page, click Route Entry under the Custom Route tab, and click Add Route Entry.
In the Add Route Entry panel, set the following parameters and click OK:
Name: Enter a name for the route entry.
Destination CIDR Block: Enter the destination CIDR block of the route entry. 0.0.0.0/0 is used in this example.
Next Hop Type: Select the next hop type. For this example, choose Transit Router.
Transit Router: Select the connection to the VPC. In this example, VPC 3 is selected.
For more information, see Use custom route tables to manage network traffic.
Repeat Step4 to Step6 to add a route whose destination CIDR block is 0.0.0.0/0 and next hop is the transit router to VPC 1 and VPC 2.
Then, you can view the route tables of VPC 1, VPC 2, VPC 3, and the transit router on the details page of the transit router in the CEN console.
On the details page of the transit router, click Network Routes to view the routes of VPC 1, VPC 2, and VPC 3.
On the details page of the transit router, click Network Routes.
Select the ID of VPC 1, VPC 2, or VPC 3 from the Network Instance drop-down list.
Figure 1. Routes of VPC 1

Figure 2. Routes of VPC 2

Figure 3. Routes of VPC 3

On the Route Table tab, view the routes that the default route table has learned from VPC 1, VPC 2, and VPC 3.
On the details page of the transit router, click the Route Table tab.
On the Route Table tab, view the routes in the route table.
Figure 4. System route table

Figure 5. Custom route table

Step 5: Test network connectivity
After you complete the preceding steps, you can perform the following operations to test the connectivity among VPC1, VPC 2, and VPC 3:
Before you start, make sure that the security group rules of VPC 1, VPC 2, and VPC 3 allow the ECS instances in the VPCs to communicate with each other. For more information, see View security group rules.
Log on to an ECS instance in VPC 1. For more information, see Overview of ECS remote connection methods.
Run the ping command to ping the IP address of the ECS instance deployed in VPC 3 to test the connectivity between VPC 1 and VPC 3.
This result shows that VPC 1 and VPC 3 can communicate with each other.
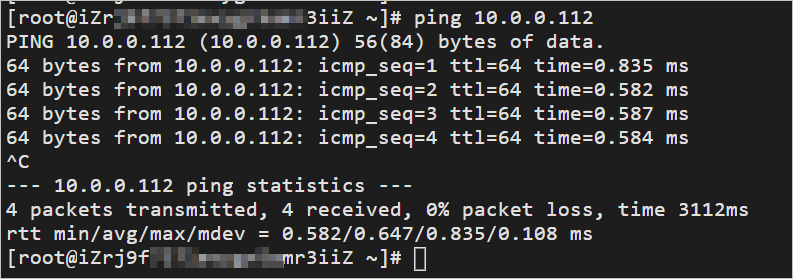
Log on to an ECS instance in VPC 2 and run the ping command to ping the IP address of an ECS instance in VPC 3. This tests the connectivity between VPC 2 and VPC 3.
The result shows that VPC 2 and VPC 3 can communicate with each other.
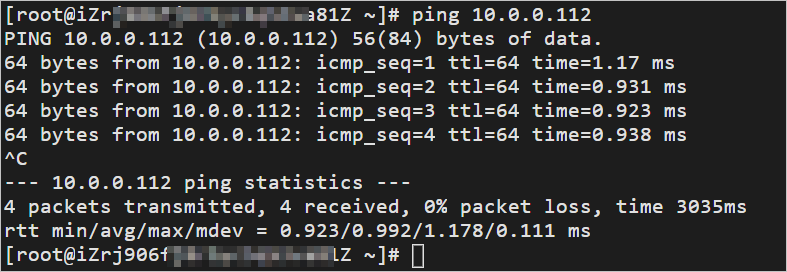
Log on to an ECS instance in VPC 1 and run the ping command to ping the IP address of an ECS instance in VPC 2 to test the connectivity between VPC 1 and VPC 2.
The result shows that VPC 1 can communicate with VPC 2.
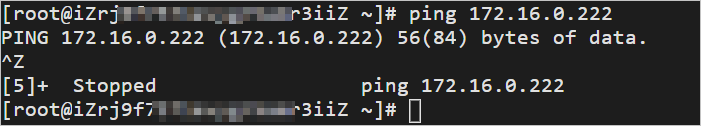
Terraform
You can use Terraform to set up the environment in this topic. For details on installing and configuring Terraform, see Install Terraform.
The steps below show how to run Terraform v1.9.8 on a Linux host. Make sure you have completed the Authentication.
Note that specific resources in this example may incur costs. Release or unsubscribe from the resources when they are no longer needed.
Step 1: Create resources
Create a directory for the scenario and navigate to it.
mkdir tf-CenSharedVpc && cd tf-CenSharedVpcCreate a
main.tffile to define resources.touch main.tfOpen the
main.tffile, paste the following code into the file, and save the changes. This file includes all the necessary resources and configurations.variable "pname" { description = "The prefix name for the resources" type = string default = "tf-CenSharedVpc" } variable "default_region" { description = "Default region" type = string default = "cn-hangzhou" } variable "az_list" { description = "List of availability zones to use" type = list(string) default = ["cn-hangzhou-j", "cn-hangzhou-k"] } variable "vpc_cidr_list" { description = "List of VPC CIDR block" type = list(string) default = ["192.168.0.0/16", "172.16.0.0/12", "10.0.0.0/16"] } variable "vsw_cidr_list" { description = "List of VSW CIDR block" type = list(string) default = [ "192.168.0.0/24", "192.168.1.0/24", "172.16.0.0/24", "172.16.1.0/24", "10.0.0.0/24", "10.0.1.0/24" ] } variable "ecs_ip_list" { description = "List of ECS ip" type = list(string) default = ["192.168.0.124", "172.16.0.222", "10.0.0.112"] } provider "alicloud" { region = var.default_region } # --- 3vpc 6vsw 3ecs resource "alicloud_vpc" "vpc" { count = length(var.vpc_cidr_list) vpc_name = "${var.pname}-vpc${count.index + 1}" cidr_block = var.vpc_cidr_list[count.index] } resource "alicloud_vswitch" "vsw" { count = length(var.vsw_cidr_list) vpc_id = alicloud_vpc.vpc[floor(count.index / length(var.az_list))].id cidr_block = var.vsw_cidr_list[count.index] zone_id = var.az_list[count.index % length(var.az_list)] vswitch_name = "${var.pname}-vsw${count.index + 1}" } resource "alicloud_instance" "ecs" { count = length(var.vpc_cidr_list) instance_name = "${var.pname}-ecs${count.index + 1}" instance_type = "ecs.e-c1m1.large" security_groups = [alicloud_security_group.sg[count.index].id] vswitch_id = alicloud_vswitch.vsw[count.index * length(var.az_list)].id image_id = "aliyun_3_x64_20G_qboot_alibase_20230727.vhd" system_disk_category = "cloud_essd" private_ip = var.ecs_ip_list[count.index] instance_charge_type = "PostPaid" } # --- 3 sg resource "alicloud_security_group" "sg" { count = length(var.vpc_cidr_list) name = "${var.pname}-${count.index + 1}" vpc_id = alicloud_vpc.vpc[count.index].id } resource "alicloud_security_group_rule" "allow_inbound_ssh" { count = length(var.vpc_cidr_list) type = "ingress" ip_protocol = "tcp" nic_type = "intranet" policy = "accept" port_range = "22/22" priority = 1 security_group_id = alicloud_security_group.sg[count.index].id cidr_ip = "0.0.0.0/0" } resource "alicloud_security_group_rule" "allow_inbound_icmp" { count = length(var.vpc_cidr_list) type = "ingress" ip_protocol = "icmp" nic_type = "intranet" policy = "accept" port_range = "-1/-1" priority = 1 security_group_id = alicloud_security_group.sg[count.index].id cidr_ip = "0.0.0.0/0" } # --- cen and tr resource "alicloud_cen_instance" "cen" { cen_instance_name = "${var.pname}-cen1" } resource "alicloud_cen_transit_router" "tr" { transit_router_name = "${var.pname}-tr" cen_id = alicloud_cen_instance.cen.id } data "alicloud_cen_transit_router_route_tables" "tr" { # get tr sys table transit_router_id = alicloud_cen_transit_router.tr.transit_router_id transit_router_route_table_type = "System" } # 3 attach resource "alicloud_cen_transit_router_vpc_attachment" "attach" { count = length(var.vpc_cidr_list) cen_id = alicloud_cen_instance.cen.id transit_router_id = alicloud_cen_transit_router.tr.transit_router_id vpc_id = alicloud_vpc.vpc[count.index].id zone_mappings { zone_id = var.az_list[0] vswitch_id = alicloud_vswitch.vsw[count.index * length(var.az_list)].id } zone_mappings { zone_id = var.az_list[1] vswitch_id = alicloud_vswitch.vsw[count.index * length(var.az_list) + 1].id } transit_router_vpc_attachment_name = "attach${count.index + 1}" } # 3 propa resource "alicloud_cen_transit_router_route_table_propagation" "propa" { count = length(var.vpc_cidr_list) transit_router_route_table_id = data.alicloud_cen_transit_router_route_tables.tr.tables[0].id transit_router_attachment_id = alicloud_cen_transit_router_vpc_attachment.attach[count.index].transit_router_attachment_id } # 1 custom_table resource "alicloud_cen_transit_router_route_table" "custom_table" { # create tr custom_table transit_router_id = alicloud_cen_transit_router.tr.transit_router_id transit_router_route_table_name = "custom_table" } resource "alicloud_cen_transit_router_route_entry" "tr_entry" { transit_router_route_table_id = alicloud_cen_transit_router_route_table.custom_table.transit_router_route_table_id transit_router_route_entry_destination_cidr_block = "10.0.0.0/16" transit_router_route_entry_next_hop_type = "Attachment" transit_router_route_entry_name = "entry1_name" transit_router_route_entry_description = "entry1_desc" transit_router_route_entry_next_hop_id = alicloud_cen_transit_router_vpc_attachment.attach[2].transit_router_attachment_id } # associate attach1\2 custom_table resource "alicloud_cen_transit_router_route_table_association" "ass1" { transit_router_route_table_id = alicloud_cen_transit_router_route_table.custom_table.transit_router_route_table_id transit_router_attachment_id = alicloud_cen_transit_router_vpc_attachment.attach[0].transit_router_attachment_id } resource "alicloud_cen_transit_router_route_table_association" "ass2" { transit_router_route_table_id = alicloud_cen_transit_router_route_table.custom_table.transit_router_route_table_id transit_router_attachment_id = alicloud_cen_transit_router_vpc_attachment.attach[1].transit_router_attachment_id } # ass attach3 sys_table resource "alicloud_cen_transit_router_route_table_association" "ass3" { transit_router_route_table_id = data.alicloud_cen_transit_router_route_tables.tr.tables[0].id transit_router_attachment_id = alicloud_cen_transit_router_vpc_attachment.attach[2].transit_router_attachment_id } # vpc entry resource "alicloud_route_entry" "vpc_entry" { count = length(var.vpc_cidr_list) route_table_id = alicloud_vpc.vpc[count.index].route_table_id destination_cidrblock = "0.0.0.0/0" nexthop_type = "Attachment" nexthop_id = alicloud_cen_transit_router_vpc_attachment.attach[count.index].transit_router_attachment_id } output "ecs1_login_address" { value = "https://ecs-workbench.aliyun.com/?from=EcsConsole&instanceType=ecs®ionId=${var.default_region}&instanceId=${alicloud_instance.ecs[0].id}" } output "ecs2_login_address" { value = "https://ecs-workbench.aliyun.com/?from=EcsConsole&instanceType=ecs®ionId=${var.default_region}&instanceId=${alicloud_instance.ecs[1].id}" } output "ecs3_login_address" { value = "https://ecs-workbench.aliyun.com/?from=EcsConsole&instanceType=ecs®ionId=${var.default_region}&instanceId=${alicloud_instance.ecs[2].id}" }Initialize the folder to complete Terraform setup.
terraform initCreate resources. Terraform will preview the resources to be created. After verification, enter
yesto initiate the creation process.terraform apply
Step 2: Test the connectivity
You can perform the following steps to test connectivity among VPC 1, VPC 2, and VPC 3:
Log on to ECS 1 in VPC 1 (the instance name is
tf-CenSharedVpc-ecs1).The logon address for ECS 1 is available in the Terraform Outputs. Copy this address into a browser to access it. Upon logging on, choose Temporary SSH Key-based as the method of authentication.

To test the connectivity between VPC 1 and VPC 3, run the ping command to ping the IP address of an ECS instance in VPC 3.
ping 10.0.0.112The result below confirms that VPC 1 and VPC 3 can communicate with each other.

Log on to the ECS 2 instance in VPC 2 (the instance name is
tf-CenSharedVpc-ecs2). Run the ping command to ping the IP address of the ECS 3 instance in VPC 3 to test the connectivity between VPC 2 and VPC 3.ping 10.0.0.112The result shows that VPC 2 and VPC 3 can communicate with each other.

To test the connectivity between VPC 1 and VPC 2, log on to the ECS 1 instance in VPC 1 (the instance name is
tf-CenSharedVpc-ecs1). Run the ping command to ping the IP address of the ECS 2 instance in VPC 2.ping 172.16.0.222The result shows that VPC 1 cannot communicate with VPC 2.

Step 3: Release resources
When verification is complete and you no longer need the resources, run the command below to release them and stop billing.
terraform destroy --auto-approve