Once your bastion host is running, this topic explains how to adjust its fundamental network settings. You will learn how to perform tasks such as changing its security group, limiting which IP addresses can access it, updating the default management port, moving its vSwitch between zones, and finding its egress IP address.
Log on to the Bastionhost console.
In the navigation pane on the left, click Instances.
On the Instances page, find the target bastion host and refer to the following table to configure the bastion host based on your requirements.
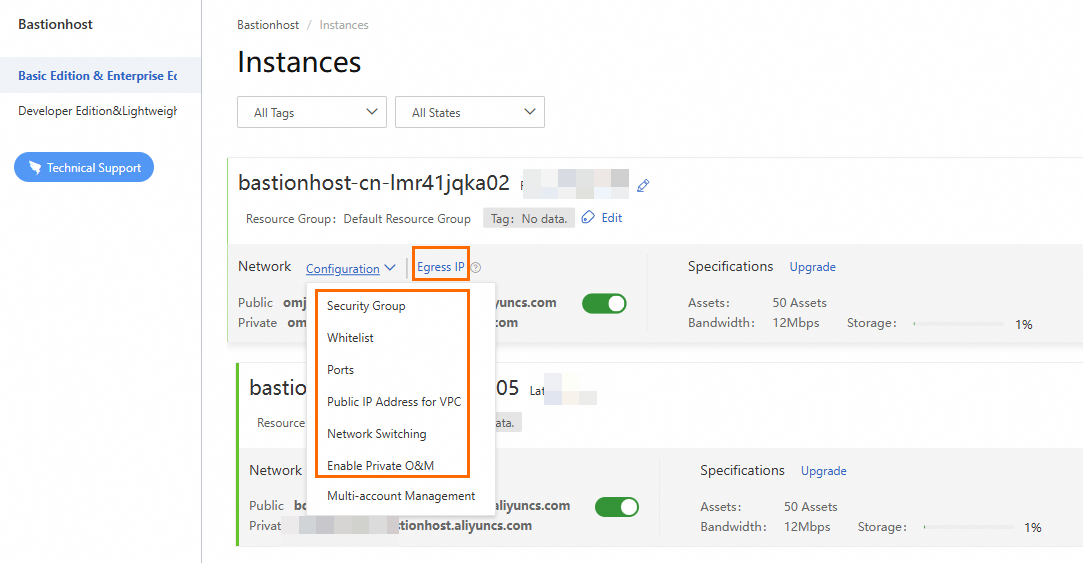
Feature
Scenario
Configure a security group
Allows a bastion host to access assets within the security group.
NoteYou can select more than one security group.
Configure a whitelist
Restricts the IP addresses that can access the public domain name of the bastion host.
Configure a port number
The default port for SSH protocol O&M of the bastion host is 60022, and the default port for RDP protocol O&M is 63389. If you want to customize the O&M port of the bastion host, use this feature.
NoteThe port numbers that range from 1 to 1,024 are reserved for Bastionhost. We recommend that you do not specify a port number in this range.
Obtain the egress IP address and related settings
The egress IP address of a bastion host is the source IP address from which the bastion host accesses assets. Egress IP addresses are divided into egress public IP addresses and egress private IP addresses. We recommend that you allow the egress IP addresses of the bastion host in your Elastic Compute Service (ECS) security group, firewall, and database whitelist to prevent connection failure. For more information about database whitelists, see Configure an IP address whitelist.
NoteIf you added your bastion host to a basic security group of ECS, a rule is automatically added to the security group to allow the egress IP addresses of the bastion host. If you added your ECS instances to an advanced security group, manually add a rule to the security group to allow the egress IP addresses of the bastion host. For more information, see Add a security group rule.
Configure privately used public IP addresses
If your asset is assigned a public IP address used within your private network, use this feature to configure the correct network mapping. This will enable the bastion host to access the asset normally. Specify a value for the privately used public IP addresses in the
IP address/Subnet maskformat. Separate multiple IP addresses or subnet masks with commas (,). You can specify up to 50 IP addresses or subnet masks. Example:192.168.XX.XX/32,172.16.XX.XX/32.WarningAfter you configure the privately used public IP addresses, the current O&M sessions are disconnected. We recommend configuring the privately used public IP addresses during off-peak hours.
Configure multi-zone
If you use Bastionhost Enterprise or SM2 Edition, use this feature to configure different zones for the vSwitches in your virtual private cloud (VPC) to ensure high network availability.
WarningAfter you configure primary and secondary zones, the current O&M connections are disconnected. We recommend configuring primary and secondary zones during off-peak hours.
After you configure the zones, the IP address to which the private O&M address of the bastion host is resolved is changed. Use the private O&M address displayed in the console of the bastion host to perform O&M operations.
The private egress IP address of your bastion host is also changed. If your security group rules are configured based on IP addresses, O&M may fail. Reconfigure the security group rules.
If other access control policies are configured based on the private O&M address, reconfigure the policies, such as the policies for your firewall.
If you configure different zones for the vSwitches, the private O&M address is resolved to two IP addresses.
Switch to a different zone
If you use Bastionhost Basic Edition, use this feature to switch a vSwitch in your VPC to a different zone. This prevents the bastion host from being inaccessible if the current zone becomes unavailable.
WarningAfter you switch the vSwitch to a different zone, current O&M connections may be terminated. We recommend switching the vSwitch to a different zone during off-peak hours.
After you configure the zones, the IP address to which the private O&M address of the bastion host is resolved is changed. Use the private O&M address that is displayed in the console of the bastion host to perform O&M operations.
The private egress IP address of your bastion host is also changed. If your security group rules are configured based on IP addresses, O&M may fail. Reconfigure the security group rules.
If other access control policies are configured based on the private O&M address, reconfigure the policies, such as the policies for your firewall.
Enable private network O&M
You can enable private network O&M to access the bastion host in a pure internal network environment. For more information, see Enable private network O&M.