This topic describes the mapping relationship between common NGINX configurations and those of a Service Mesh (ASM) gateway, which helps you migrate NGINX configurations to an ASM gateway.
NGINX parameter | Description | Configuration on an ASM gateway |
allow-backend-server-header | Allows the backend to return the | The default configuration of the corresponding parameter on an ASM gateway is true. |
allow-snippet-annotations | Allows you to add a custom script to the annotations of an Ingress object to modify NGINX configurations. | An ASM gateway does not have a parameter that corresponds to this parameter. You must edit the IstioGateway YAML file to modify the configurations of an ASM gateway. |
compute-full-forwarded-for | Adds the remote address to the X-Forwarded-For header instead of replacing the header. | The configuration depends on the use_remote_address parameter of Envoy, and the default value is true. For more information about how Istio processes the X-Forwarded-For header, see Configuring Gateway Network Topology. |
enable-underscores-in-headers | Allows for underscores in header names. | This parameter corresponds to the headers_with_underscores_action parameter of Envoy, and the default value is true. |
forwarded-for-header | Sets the header field that is used to identify the originating IP address of a client. | ASM gateways do not support custom configurations of this parameter, and the default value is X-Forwarded-For. |
generate-request-id | Generates a random value of X-Request-ID if X-Request-ID does not exist in a request. | This parameter corresponds to the generate_request_id parameter of Envoy. You can change the value by using an ASM plug-in. The default value is true. |
ignore-invalid-headers | Sets whether to ignore headers with invalid names. A valid header name must contain letters, digits, and hyphens (-), and may contain underscores (_). Note Whether a valid header name can contain underscores (_) is controlled by the underscores_in_headers parameter. | Envoy provides Header Validator. If the Header Validator is not configured, the default value is used. In case of an invalid header, the system prompts 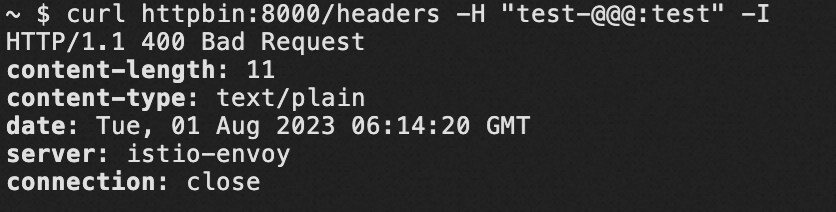 |
keep-alive-requests | Sets the maximum number of requests that can be processed by one keep-alive connection. After the maximum number of requests is reached, the connection is closed. | For more information about how to configure the maximum number of requests for a connection, see |
log-format-upstream | Customizes the format of logs. | ASM allows you to customize the format of logs on the Observability Settings page in the ASM console. For more information, see Configure Observability Settings. |
max-worker-connections | Sets the maximum number of connections that can be opened by a worker process at the same time. | ASM allows you to configure the |
proxy-body-size | Sets the maximum size of a request body that is allowed to a client. If the size of a request body exceeds this value, a 413 error is reported. | ASM does not support this configuration. We recommend that you transmit requests in blocks and do not use large bodies. |
proxy-connect-timeout | Sets the timeout period for establishing a connection with a proxy server. The timeout period cannot exceed 75 seconds. | For more information about how to configure the timeout period, see |
reuse-port | Sets NGINX to create a separate listening socket for each worker process (by using the SO_REUSEPORT parameter) to allow a kernel to distribute incoming connections between worker processes. The default value is true. | The default configuration of the corresponding parameter on an ASM gateway is true. |
server-tokens | Sets whether to send the NGINX Server header in responses and display the NGINX version in error pages. The default value is disabled. | By default, an ASM gateway sets the server header to the header of Envoy. However, error pages do not display Envoy versions. |
ssl-redirect | Sets the global value for redirection to HTTPS if the server has a Transport Layer Security (TLS) certificate. | For more information about how to configure the redirection, see |
upstream-keepalive-connections | Sets the maximum number of idle keepalive connections to upstream servers that are kept in the cache of each worker process. | ASM allows you to configure the |
upstream-keepalive-timeout | Sets a timeout period, during which idle connections to an upstream server are kept alive. | For more information about how to configure the timeout period for idle connections, see |
use-forwarded-headers |
| For more information about how Istio processes the X-Forwarded-For header, see Configuring Gateway Network Topology. |
worker-cpu-affinity | Binds worker processes to the sets of CPUs. | In container environments, we recommend that you use the default value and do not configure this option. |
For more information, see Ingress Nginx.