OpenID Connect (OIDC) is an OAuth 2.0-based identity authentication and authorization protocol, which is commonly used to implement single sign-on (SSO). After you configure a Service Mesh (ASM) security policy to implement OIDC SSO, you can use identity information provided by Alibaba Cloud Identity as a Service (IDaaS) or other identity providers (IdPs) that comply with the OIDC protocol to log on with a single ID to multiple related systems without the need to modify your applications. This improves application security and simplifies the development and management of your application.
Prerequisites
An ingress gateway is deployed, and the IP address of the ingress gateway is obtained.
An Istio gateway and a virtual service are created to ensure that the following paths are accessible. For more information, see Step 1 to Step 3 in Use Istio resources to route traffic to different versions of a service.
http://${IP address of the ingress gateway}/productpage http://${IP address of the ingress gateway}/api/v1/products/1 http://${IP address of the ingress gateway}/static/jquery.min.jsAn IdP is configured. For more information, see Step 1 and Step 2 in Integrate Alibaba Cloud IDaaS with ASM to implement single sign-on.
After an IdP is configured, you can obtain the following information that will be used in Step 5.
redirect uri: http://${IP address of the ingress gateway}/oauth2/callback issuer: https://eiam-api-cn-hangzhou.aliyuncs.com/v2/idaas_tbn25osdlmz6gtqfq3j2pz****/app_ml5tzapsl7zmfo53wb3nwk****/oidc client id: app_ml5tzapsl7zmfo53wb3nwk**** client secret: CSCfHeZ1nyvfMWyKHtE8ZRdif7j89dv9CvmJLurtGC****
Procedure
In this example, an Alibaba Cloud IDaaS instance is used as the IdP to implement SSO to applications in ASM. If you use a self-managed OIDC IdP, see Integrate Keycloak with ASM to implement SSO.
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose .
On the ASMSecurityPolicy page, click Create.
In the Create ASMSecurityPolicy dialog box, click OIDC Single Sign-On and then click OK.
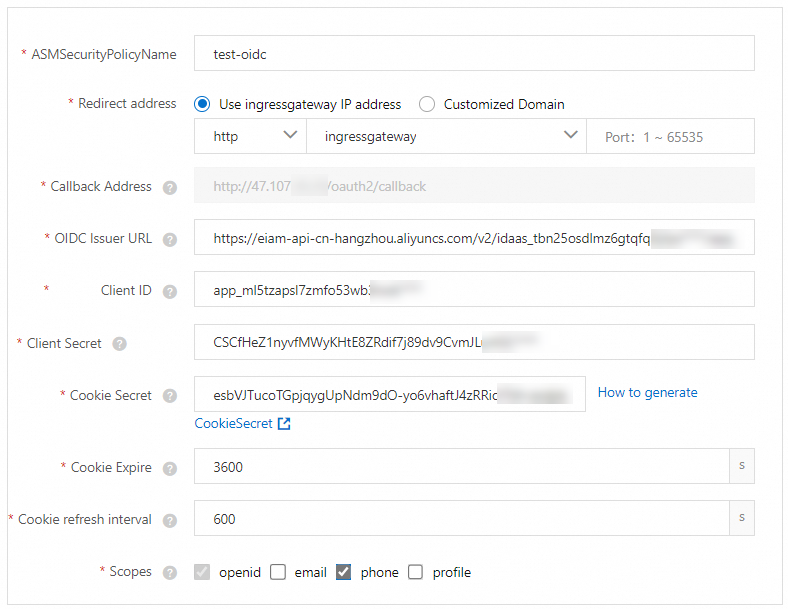
In the OIDC Config step of the configuration wizard, configure the parameters and click Next.
The following table describes the parameters.
Parameter
Description
ASMSecurityPolicyName
The name of the ASM security policy. In this example, the name is set to test-oidc.
Redirect address
The following options are provided: Use ingressgateway IP address and Customized Domain. In this example, Use ingressgateway IP address is selected. http and ingressgateway are selected.
Callback Address
The redirect URL.
OIDC Issuer URL
The URL used to identify and authenticate the OIDC issuer.
Client ID
The client ID provided by the issuer.
Client Secret
The client secret provided by the issuer.
Cookie Secret
The seed string for the secure cookies, which can be Base64-encoded.
Cookie Expire
The validity period of the cookie. The cookie expires after the period has elapsed. If you set this parameter to 0, the cookie does not expire.
Cookie refresh interval
The interval at which the cookie is refreshed. If you set this parameter to 0, the cookie is not refreshed.
Scopes
The types of user information that can be obtained. The specified scopes must be supported by the issuer.
For more information about how to set Scopes, see Integrate Alibaba Cloud IDaaS with ASM to implement single sign-on.
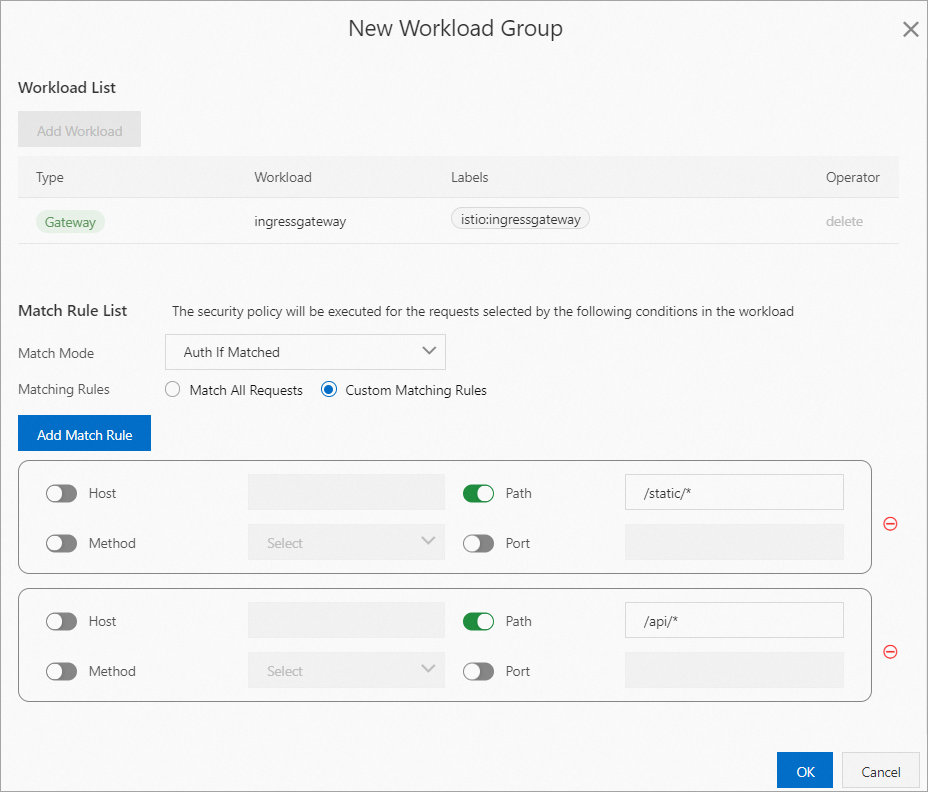
In the Workload and Match Rules step of the configuration wizard, click Add Workload Group. In the New Workload Group dialog box, configure the parameters, click OK, and then click Submit.
The following table describes how to configure the parameters in this example.
Parameter
Description
Workload Group Name
Set the parameter to test-policy.
Workload List
The ingress gateway that you specified for the Redirect address parameter in the previous step is selected by default and cannot be changed. If you want to select other workloads, go back to the OIDC Config step and change the Redirect address setting.
NoteIf you set the Redirect address parameter to Customized Domain in the OIDC Config step, perform the following steps:
In the New Workload Group dialog box, click Add Workload and select Gateway Scope.
In the Select workloads box, select the workload that you want to add, click the
 icon to add the selected workload to the selected box, and then click OK.
icon to add the selected workload to the selected box, and then click OK.
Match Rule List
The following two match modes are available:
Auth If Matched: Users must be authenticated before they can access the workload.
Bypass Auth If Matched: Authentication is not required to access the workload.
For this example, select Auth If Matched. Select Custom Matching Rules for Matching Rules. Then, click Add Match Rule and configure the following rules: The rules specify that requests to access resources in the paths that start with /static and /api require OIDC authentication.
Rule 1: Turn on the Path switch and set the parameter to /static/*.
Rule 2: Turn on the Path switch and set the parameter to /api/*.
In the Complete step of the configuration wizard, the "ASMSecurityPolicy Creation successfully" message appears, indicating that the ASM security policy is created. You can click YAML to view the created resources, or click Complete to go back to the ASMSecurityPolicy page to view the created security policy.
Verify whether the OIDC SSO configuration takes effect.
Open a browser and visit the following URLs:
http://${IP address of the ingress gateway}/productpage http://${IP address of the ingress gateway}/api/v1/products/1 http://${IP address of the ingress gateway}/static/jquery.min.jsThe following results indicate that the OIDC SSO configuration takes effect:
The requests to access the paths that start with
/productpageare allowed without authentication.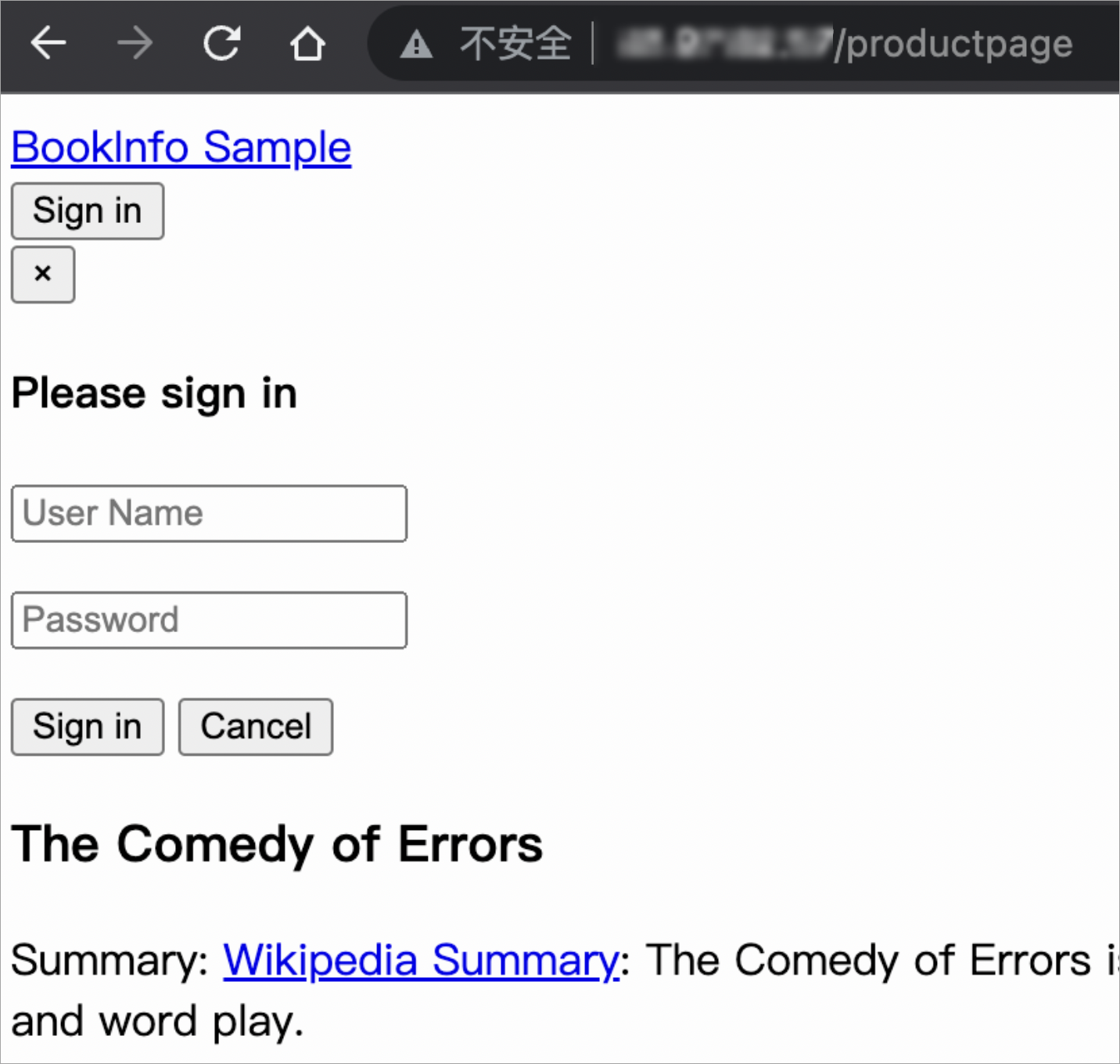
The requests to access the paths that start with
/apiand/staticrequire authentication.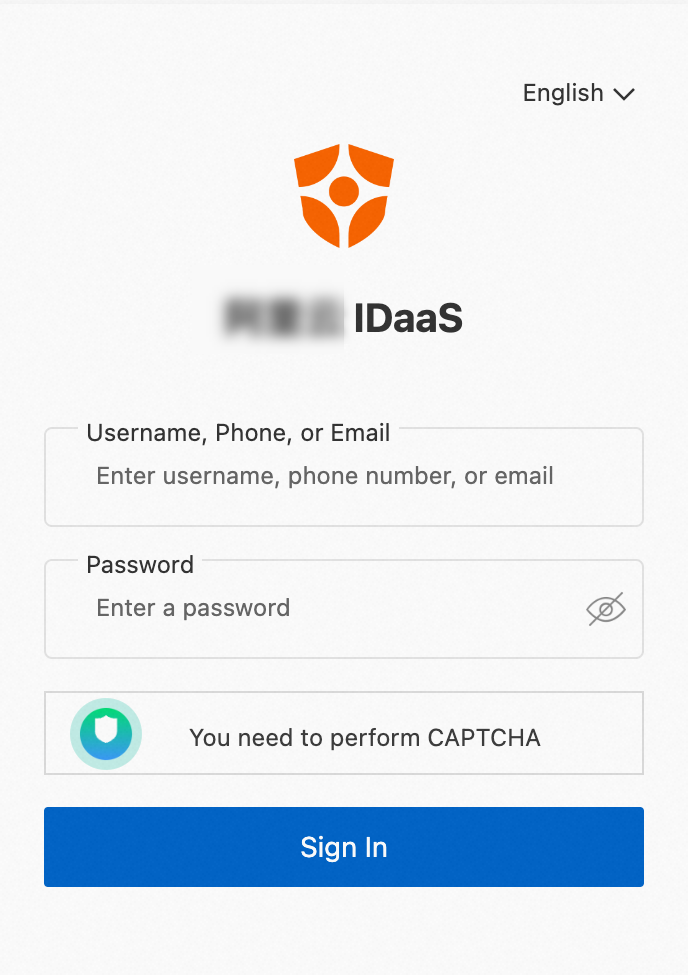
Modify the OIDC SSO configuration.
On the ASMSecurityPolicy page, find the OIDC SSO security policy that you want to modify and click Edit in the Actions column.
In the OIDC Config step of the configuration wizard, click Next.
In the Workload and Match Rules step, find the workload group that you want to modify and click Edit in the Operator column. Modify the parameter settings, click OK, and then click Submit.
The following table describes how to modify the parameter settings in this example.
Parameter
Description
Match Mode
Select Bypass Auth If Matched.
Matching Rules
Click Add Match Rule and configure the following rules: The rules specify that requests to access the paths that start with /productpage and /static are allowed without OIDC authentication.
Rule 1: Turn on the Path switch and set the parameter to /productpage.
Rule 2: Turn on the Path switch and set the parameter to /static/*.
Open a browser in incognito mode and visit the following URLs:
http://${IP address of the ingress gateway}/productpage http://${IP address of the ingress gateway}/api/v1/products/1 http://${IP address of the ingress gateway}/static/jquery.min.jsThe following results indicate that the new OIDC SSO configuration takes effect.
The requests to access the paths that start with
/productpageand/staticare allowed without authentication.The request to access the path that starts with
/apirequires authentication.
References
For more information about configuration items of OIDC applications, such as API operations, secret rotation, OIDC grant types supported by IDaaS, configurations in IDaaS, and configurations in applications, see General Config, Configure SSO, OIDC SSO Configuration, and Rules for OIDC id_token Extended Fields.
When a user who has logged on to an application by using SSO powered by IDaaS wants to log out, the user can initiate a global logout on the application to terminate the application sessions as well as the primary IDaaS logon session. For more information, see SLO.