After adding an ingress gateway to an ASM instance, you can deploy applications to the clusters associated with the instance. This topic describes how to deploy the sample application Bookinfo to an ACK cluster associated with an ASM instance
Application description
In this example, a book review application that is named Bookinfo is used. The following figure shows the microservices model of the application.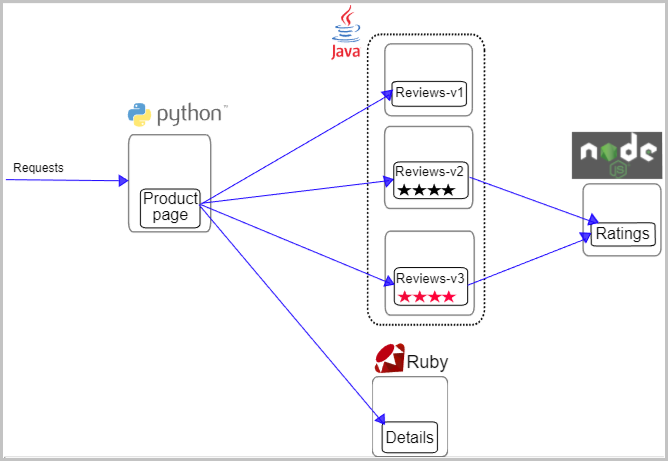
The Bookinfo application consists of the following microservices:
Productpage: generates pages by calling the Details and Reviews microservices.
Details: contains the information about books.
Reviews: contains book reviews and may call the Ratings microservice.
Ratings: contains book ratings that are generated based on book reviews.
The Reviews microservice has the following versions:
Version 1 does not call the Ratings microservice.
Version 2 calls the Ratings microservice and rates a book with one to five black stars.
Version 3 calls the Ratings microservice and rates a book with one to five red stars.
Prerequisites
Prometheus Monitoring or a self-managed Prometheus has been integrated in the ACK cluster for monitoring metrics collection. This topic uses Prometheus Monitoring as an example. For more information, see Integrate Prometheus Monitoring to implement mesh monitoring or Integrate self-managed Prometheus to implement mesh monitoring.
Deploy the Bookinfo application
Create a bookinfo.yaml file with the following content.
Run the following command to deploy the sample application in the default namespace.
kubectl apply -f bookinfo.yaml
Deploy and configure the ingress gateway
Create a bookinfo-gateway.yaml file.
apiVersion: networking.istio.io/v1beta1 kind: Gateway metadata: name: bookinfo-gateway namespace: default spec: selector: istio: ingressgateway servers: - port: number: 80 name: http protocol: HTTP hosts: - '*' --- apiVersion: networking.istio.io/v1beta1 kind: VirtualService metadata: name: vs-demo namespace: default spec: hosts: - '*' http: - name: gw-to-productage match: - uri: exact: /productpage - uri: prefix: /static - uri: exact: /login - uri: exact: /logout - uri: prefix: /api/v1/products route: - destination: host: productpage port: number: 9080 gateways: - bookinfo-gatewayDeploy the ingress gateway.
kubectl apply -f bookinfo-gateway.yaml
Access the application
You will connect to the Bookinfo productpage service through the gateway you just configured.
Obtain the gateway IP address.
echo $(kubectl -n istio-system get istiogateway ingressgateway -o jsonpath="{.status.GatewayAddress[0]}")In your browser, visit
http://{IP address of the ingress gateway}/productpageto view the Bookinfo application.
Refresh the page multiple times, and you will see that the ratings under Book Reviews change, corresponding to versions v1, v2, and v3 of the reviews application.
Enable Ambient mode for Bookinfo
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose .
Click Switch To Ambient Mesh Mode in the Data Plane Mode column of the Default namespace.
You can switch the Data Plane Mode of a namespace back to Sidecar mode at any time on the
In your browser, visit
http://{IP address of the ingress gateway}/productpageto view the Bookinfo application. You can see that the service is still accessible, but mTLS encryption is now enabled between all Bookinfo application pods.
View the mesh topology
Enable monitoring metric collection.
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose .
Click Collect Metrics to Managed Service for Prometheus. In the Submit dialog box, select the cluster name and click OK.
If you are using self-managed Prometheus, you can skip this step.
Enable mesh topology.
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose .
Click To Enable. Configure the mesh topology with the following parameters and click Confirm Enabling.
The following example shows how to configure access through an ASM gateway.
Configuration item
Example value
Service deployment mode
Data plane deployment mode within Kubernetes cluster.
When using the managed deployment mode, only access through a Serverless ASM gateway is supported.
Observability cluster
c6118d720xxxxxxxxxxxxxx58410a9c7d0.
Prometheus scrape address
This parameter is ignored in this example.
If you are using self-managed Prometheus, enter the read address here.
When multiple clusters are added to ASM, you need to first create an aggregation instance and enter the read address of the aggregation instance.
Identity authentication - logon method
Token
Entry
ASM.
Select an ASM gateway: Select the ingress gateway name, which is ingressgateway in this example.
Select an ASM gateway port: Select 443.
You can also add a dedicated port for mesh topology by editing the gateway.
Send test traffic to generate a traffic topology diagram.
export GATEWAY_ADDRESS=$(kubectl -n istio-system get istiogateway ingressgateway -o jsonpath="{.status.GatewayAddress[0]}") for i in $(seq 1 100); do echo "Request $i: $(curl -sSI -o /dev/null -w "%{http_code}" "http://${GATEWAY_ADDRESS}:80/productpage")" doneIn the Logon Method section of Mesh Topology page, click View the logon token and copy the Token content.
Click Access ASM mesh topology after Topology address. On the Kiali page, paste the copied content into the Token input box and click Log in.