ApsaraMQ for MQTT allows you to use device certificates to authenticate access from clients. Certificate authority (CA) certificates can be used to issue device, server, and validation certificates. If an ApsaraMQ for MQTT client uses a device certificate to perform authentication, the ApsaraMQ for MQTT broker uses the CA certificate associated with the device certificate to authenticate the validity of the device certificate. You can use a CA certificate only after you register the certificate with an ApsaraMQ for MQTT broker.
Background information
If an ApsaraMQ for MQTT client uses a device certificate to perform authentication, the ApsaraMQ for MQTT broker uses the CA certificate associated with the device certificate to authenticate the validity of the device certificate. You can use a CA certificate only after you register the certificate with an ApsaraMQ for MQTT broker.
To register a CA certificate with an ApsaraMQ for MQTT broker, you must upload the certificate information to the broker and then bind the certificate to the specified instance. The following items describe the relationship between a CA certificate and an instance:
Multiple CA certificates can be bound to an instance.
A CA certificate can be bound to multiple instances.
Limits
You can manage CA certificates only on ApsaraMQ for MQTT Enterprise Platinum Edition instances.
The serial number of an obtained CA certificate must be unique.
The serial number of a CA certificate cannot exceed 128 bytes in size.
CA certificates support Rivest-Shamir-Adleman (RSA) and Elliptic Curve Cryptography (ECC) algorithms.
Prerequisites
OpenSSL v1.1.1i or later is installed.
Self-signed CA certificates
You can purchase a CA certificate from a CA. You can also create a self-signed CA certificate. This topic describes how to create a self-signed CA certificate by using OpenSSL.
Download and install OpenSSL
- Note
After you install OpenSSL, if you use the Windows operating system, you must add the bin subdirectory of the OpenSSL installation directory to the PATH environment variable.
Open a command prompt window.
RSA CA certificates
Run the following command to generate a private key for the RSA CA certificate:
openssl genrsa -out CA.key 2048Run the following command to use the private key of the CA certificate to create a certificate signing request (CSR) file for the certificate:
openssl req -new -key CA.key -out CA.csrThe following code is returned. Enter values for the corresponding parameters.
Country Name (2 letter code) [AU]: State or Province Name (full name) []: Locality Name (for example, city) []: Organization Name (for example, company) []: Organizational Unit Name (for example, section) []: Common Name (e.g. server FQDN or YOUR name) []: Email Address []:Run one of the following commands to create a self-signed RSA CA certificate named
CA.crtbased on the operating system. The location of the extfile file varies based on the operating system.Mac
openssl x509 -req -extfile /System/Library/OpenSSL/openssl.cnf -extensions v3_ca -in CA.csr -out CA.crt -signkey CA.key -CAcreateserial -days 3650CentOS
openssl x509 -req -extfile /etc/pki/tls/openssl.cnf -extensions v3_ca -in CA.csr -out CA.crt -signkey CA.key -CAcreateserial -days 3650Windows
openssl x509 -req -extfile C:\Progra~1\OpenSSL-Win64\bin\cnf\openssl.cnf -extensions v3_ca -in CA.csr -out CA.crt -signkey CA.key -CAcreateserial -days 3650
Run the following command to view the created RSA CA certificate:
openssl x509 -in CA.crt -text
ECC CA certificates
Run the following command to generate a private key for the ECC CA certificate:
openssl ecparam -genkey -name prime256v1 -out CA.keyRun one of the following commands to create a self-signed CA certificate named
CA.crtbased on the operating system:Mac
openssl req -new -x509 -days 3650 -config /System/Library/OpenSSL/openssl.cnf -extensions v3_ca -key CA.key -out CA.crtCentOS
openssl req -new -x509 -days 3650 -config /etc/pki/tls/openssl.cnf -extensions v3_ca -key CA.key -out CA.crtWindows
openssl req -new -x509 -days 3650 -config C:\Progra~1\OpenSSL-Win64\bin\cnf\openssl.cnf -extensions v3_ca -key CA.key -out CA.crtNoteIf an error is reported in this step, check whether the openssl.cnf file path in the command is correct.
The following code is returned. Enter values for the corresponding parameters.
Country Name (2 letter code) [AU]: State or Province Name (full name) []: Locality Name (for example, city) []: Organization Name (for example, company) []: Organizational Unit Name (for example, section) []: Common Name (e.g. server FQDN or YOUR name) []: Email Address []:Run the following command to view the created ECC CA certificate:
openssl x509 -in CA.crt -text
Register a CA certificate
After a CA certificate is registered, it is activated by default.
Obtain the registration code of the CA certificate.
Log on to the ApsaraMQ for MQTT console. In the left-side navigation pane, click Instances.
In the top navigation bar, select the region where the ApsaraMQ for MQTT instance that you want to manage resides. On the Instances page, click the name of the desired instance to go to the Instance Details page. In the left-side navigation pane, choose .
On the CA Certificate page, click Register Certificate.
In the panel that appears, you can obtain the registration code of the CA certificate.
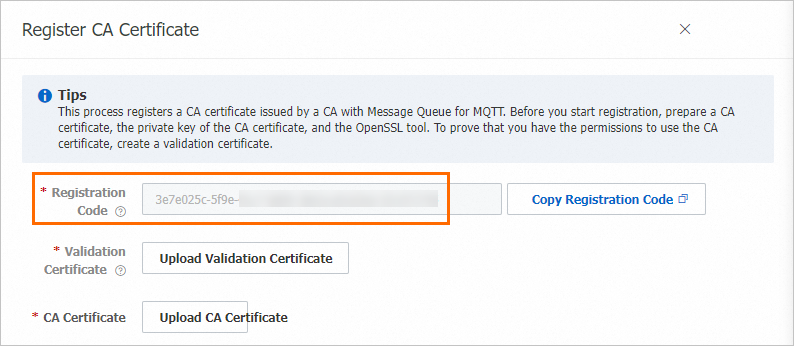
Create a validation certificate for the CA certificate.
If you want to register a CA certificate with an ApsaraMQ for MQTT broker, you must prove that you have the private key of the CA certificate. You must use the CA certificate to create a validation certificate. When you create the validation certificate, specify the registration code provided by ApsaraMQ for MQTT. The system determines whether you can use the CA certificate based on the created validation certificate and specified registration code.
RSA CA certificates
Run the following command to generate a private key for the validation certificate:
openssl genrsa -out verificationCert.key 2048Run the following command to create a CSR file for the validation certificate:
openssl req -new -key verificationCert.key -out verificationCert.csrThe following code is returned. Enter values for the corresponding parameters.
Country Name (2 letter code) [AU]: State or Province Name (full name) []: Locality Name (for example, city) []: Organization Name (for example, company) []: Organizational Unit Name (for example, section) []: Common Name (e.g. server FQDN or YOUR name) []:i29adsjfp29jfj92jlajsdf****** Email Address []:ImportantAll parameters are optional except for the
CommonNameparameter. Replace the value of the CommonName parameter with the registration code that you obtained in Step 1.Run the following command to create a validation certificate named
verificationCert.crtfor the CA certificate:openssl x509 -req -in verificationCert.csr -CA CA.crt -CAkey CA.key -CAcreateserial -out verificationCert.crt -days 300 -sha512NoteIf the CA certificate is not self-signed, you can submit the CSR file to the CA that issued the certificate to generate the certificate.
ECC CA certificates
Run the following command to generate a private key for the validation certificate:
openssl ecparam -out verificationCert.key -name prime256v1 -genkeyRun the following command to create a CSR file for the validation certificate:
openssl req -new -key verificationCert.key -out verificationCert.csrThe following code is returned. Enter values for the corresponding parameters.
Country Name (2 letter code) [AU]: State or Province Name (full name) []: Locality Name (for example, city) []: Organization Name (for example, company) []: Organizational Unit Name (for example, section) []: Common Name (e.g. server FQDN or YOUR name) []:i29adsjfp29jfj92jlajsdf****** Email Address []:ImportantAll parameters are optional except for the
CommonNameparameter. Replace the value of the CommonName parameter with the registration code that you obtained in Step 1.Run the following command to create a validation certificate named
verificationCert.crtfor the CA certificate:openssl x509 -req -in verificationCert.csr -CA CA.crt -CAkey CA.key -CAcreateserial -out verificationCert.crt -days 300 -sha512NoteIf the CA certificate is not self-signed, you can submit the CSR file to the CA that issued the certificate to generate the certificate.
Upload the
CA.crtCA certificate and theverificationCert.crtvalidation certificate.On the CA Certificate page, click Register Certificate.
In the Register CA Certificate panel, click Upload Validation Certificate and Upload CA Certificate, follow the on-screen instructions to upload the CA certificate and the validation certificate, and then click OK.
Download a CA certificate
You can download a CA certificate to your on-premises machine to back up the certificate or view the details of the certificate.
In the CA certificate list, find the CA certificate that you want to download and click Download in the Actions column.
Query CA certificates
Query all CA certificates
All CA certificates registered with an ApsaraMQ for MQTT instance are displayed on the CA Certificate page.
Query a single CA certificate
In the upper part of the CA certificate list, enter the serial number of the CA certificate that you want to query and click Search.
Query the device certificates issued by a CA certificate
In the CA certificate list, find the CA certificate that you want to manage and click Device Certificate in the Actions column.
You are redirected to the Device Certificate page. This page displays all device certificates issued by the CA certificate and registered with the ApsaraMQ for MQTT broker.
Activate or deregister a CA certificate
You can activate or deregister a CA certificate to change its status. A CA certificate can be in the Activated or Inactivated state. By default, a CA certificate is activated after it is registered with an ApsaraMQ for MQTT broker.
After you deregister a CA certificate, all device certificates that are issued by the CA certificate and registered with the ApsaraMQ for MQTT broker are deregistered. Similarly, after you activate a CA certificate, all device certificates issued by the CA certificate are activated.
CA certificates in the Activated state: If you want to temporarily disable a CA certificate, you can deregister the certificate. After you deregister a CA certificate, the certificate becomes unavailable.
CA certificates in the Inactivated state: If you want to reuse a disabled CA certificate, you can reactivate the certificate.
In the CA certificate list, find the CA certificate that you want to manage and click Deregister or Activate in the Actions column.
Delete a CA certificate
After you delete a CA certificate, the information about the CA certificate and the information about all device certificates issued by the CA certificate are deleted from the storage records of the ApsaraMQ for MQTT broker. After you delete a CA certificate, you can use the certificate and the device certificates issued by the certificate to perform authentication only after you register them with the ApsaraMQ for MQTT broker again.
In the CA certificate list, find the CA certificate that you want to delete and click Delete in the Actions column.
In the message that appears, click OK.