ApsaraMQ for Kafka Professional Edition instances allow you to use access control lists (ACLs) to manage the permissions of Simple Authentication and Security Layer (SASL) users on topics and consumer groups. You can use Terraform to integrate ACL configurations into Infrastructure as Code (IaC) processes. For example, you can define a Terraform configuration file to specify user permissions and then execute Terraform commands to automatically apply the configurations.
You can run the sample code in this topic with a few clicks.
Before you start
An Alibaba Cloud account has full permissions on all resources that belong to this account. If the credentials of an Alibaba Cloud account are leaked, security risks may arise. We recommend that you use a Resource Access Management (RAM) user and create an AccessKey pair for the RAM user. For more information, see Create a RAM user and Create an AccessKey pair.
You must use RAM to manage access permissions on cloud resources in an efficient manner. This helps meet the requirements for multi-user collaboration and allows you to grant permissions to users based on the principle of least privilege to prevent security vulnerabilities caused by excessive permissions. For more information, see Grant permissions to RAM users.
{ "Version": "1", "Statement": [ { "Effect": "Allow", "Action": [ "vpc:DescribeVpcAttribute", "vpc:DescribeRouteTableList", "vpc:DescribeVSwitchAttributes", "vpc:DeleteVpc", "vpc:DeleteVSwitch", "vpc:CreateVpc", "vpc:CreateVSwitch" ], "Resource": "*" }, { "Effect": "Allow", "Action": "bss:ModifyAgreementRecord", "Resource": "*" }, { "Effect": "Allow", "Action": [ "bss:DescribeOrderList", "bss:DescribeOrderDetail", "bss:PayOrder", "bss:CancelOrder" ], "Resource": "*" }, { "Effect": "Allow", "Action": [ "ecs:CreateSecurityGroup", "ecs:ModifySecurityGroupPolicy", "ecs:DescribeSecurityGroups", "ecs:ListTagResources", "ecs:DeleteSecurityGroup", "ecs:DescribeSecurityGroupAttribute", "ecs:AuthorizeSecurityGroup", "ecs:RevokeSecurityGroup" ], "Resource": "*" }, { "Action": "alikafka:*", "Resource": "*", "Effect": "Allow" }, { "Action": "ram:CreateServiceLinkedRole", "Resource": "*", "Effect": "Allow", "Condition": { "StringEquals": { "ram:ServiceName": [ "connector.alikafka.aliyuncs.com", "instanceencryption.alikafka.aliyuncs.com", "alikafka.aliyuncs.com", "etl.alikafka.aliyuncs.com" ] } } } ] }Prepare the runtime environment for Terraform by using one of the following methods:
Use Terraform in Terraform Explorer: Alibaba Cloud provides Terraform Explorer, an online runtime environment for Terraform. You can use Terraform after you log on to Terraform Explorer without the need to install Terraform. This method is suitable for scenarios in which you want to use and debug Terraform in a fast and convenient manner at no additional costs.
Use Terraform in Cloud Shell: Terraform is preinstalled in Cloud Shell and identity credentials are configured. You can directly run Terraform commands in Cloud Shell. This method is suitable for scenarios in which you want to use and debug Terraform in a fast and convenient manner at low costs.
Install and configure Terraform on your on-premises machine: This method is suitable for scenarios in which network connections are unstable or a custom development environment is required.
Required resources
You are charged for specific resources required in this topic. If you no longer require the resources, release or unsubscribe from the resources at the earliest opportunity.
alicloud_vpc: creates a virtual private cloud (VPC).
alicloud_vswitch: creates a vSwitch for a VPC.
alicloud_zones: queries zones.
alicloud_security_group: creates a security group.
alicloud_alikafka_instance: creates an ApsaraMQ for Kafka instance.
alicloud_alikafka_topic: creates an ApsaraMQ for Kafka topic.
alicloud_alikafka_sasl_user: creates a SASL user.
alicloud_alikafka_sasl_acl: grants permissions to a SASL user.
alicloud_alikafka_sasl_acls: queries the permissions of a SASL user.
Create a SASL user and grant permissions to the user
In the following example, a SASL user named example is created for a topic named example-topic on an ApsaraMQ for Kafka instance that resides in the China (Shenzhen) region, and the write permission on the topic is granted to the SASL user.
Create a working directory and a configuration file named main.tf in the directory. Copy the following code to the main.tf configuration file:
Create the required resources.
NoteYou can create SASL users only for ApsaraMQ for Kafka Professional Edition instances whose ACL feature is enabled.
variable "name" { default = "tf-example" } variable "region" { default = "cn-shenzhen" } data "alicloud_zones" "default" { available_resource_creation = "VSwitch" } variable "zone_id" { default = "cn-shenzhen-f" } provider "alicloud" { region = var.region } resource "alicloud_vpc" "default" { vpc_name = var.name cidr_block = "10.4.0.0/16" } resource "alicloud_vswitch" "default" { vswitch_name = var.name cidr_block = "10.4.0.0/24" vpc_id = alicloud_vpc.default.id zone_id = data.alicloud_zones.default.zones.0.id } # Create a security group. resource "alicloud_security_group" "default" { vpc_id = alicloud_vpc.default.id } resource "random_integer" "default" { min = 10000 max = 99999 } resource "alicloud_alikafka_instance" "default" { name = "${var.name}-${random_integer.default.result}" partition_num = 50 disk_type = "1" disk_size = "500" deploy_type = "5" io_max = "20" spec_type = "professional" service_version = "2.2.0" config = "{\"enable.acl\":\"true\"}" vswitch_id = alicloud_vswitch.default.id security_group = alicloud_security_group.default.id } resource "alicloud_alikafka_topic" "default" { instance_id = alicloud_alikafka_instance.default.id topic = "example-topic" remark = "topic-remark" } resource "alicloud_alikafka_sasl_user" "default" { instance_id = alicloud_alikafka_instance.default.id username = var.name password = "tf_example123" }In the main.tf configuration file, add the
resource "alicloud_alikafka_sasl_acl" "default"configuration item.resource "alicloud_alikafka_sasl_acl" "default" { instance_id = alicloud_alikafka_instance.default.id username = alicloud_alikafka_sasl_user.default.username acl_resource_type = "Topic" acl_resource_name = alicloud_alikafka_topic.default.topic acl_resource_pattern_type = "LITERAL" acl_operation_type = "Write" }
Run the following command to initialize the runtime environment for Terraform:
terraform initIf the following information is returned, Terraform is initialized:
Initializing the backend... Initializing provider plugins... - Checking for available provider plugins... - Downloading plugin for provider "alicloud" (hashicorp/alicloud) 1.90.1... ... You may now begin working with Terraform. Try running "terraform plan" to see any changes that are required for your infrastructure. All Terraform commands should now work. If you ever set or change modules or backend configuration for Terraform, rerun this command to reinitialize your working directory. If you forget, otherCreate an execution plan and preview the changes.
terraform planRun the following command to create the resources:
terraform applyDuring the execution, enter
yesas prompted and press the Enter key. Wait until the command is executed. If the following information appears, the operation is successful:random_integer.default: Creating... random_integer.default: Creation complete after 0s [id=****] alicloud_vpc.default: Creating... alicloud_vpc.default: Creation complete after 7s [id=vpc-****] alicloud_security_group.default: Creating... alicloud_vswitch.default: Creating... alicloud_security_group.default: Creation complete after 1s [id=sg-****] alicloud_vswitch.default: Creation complete after 4s [id=vsw-****] alicloud_alikafka_instance.default: Creating... alicloud_alikafka_instance.default: Still creating... [10s elapsed] ··· alicloud_alikafka_instance.default: Still creating... [4m20s elapsed] alicloud_alikafka_instance.default: Creation complete after 4m22s [id=alikafka_post-cn-****] alicloud_alikafka_sasl_user.default: Creating... alicloud_alikafka_topic.default: Creating... alicloud_alikafka_sasl_user.default: Creation complete after 3s [id=alikafka_post-cn-****:tf-example] alicloud_alikafka_topic.default: Creation complete after 8s [id=alikafka_post-cn-****:example-topic] alicloud_alikafka_sasl_acl.default: Creating... alicloud_alikafka_sasl_acl.default: Still creating... [10s elapsed] ··· alicloud_alikafka_sasl_acl.default: Still creating... [1m0s elapsed] alicloud_alikafka_sasl_acl.default: Creation complete after 1m1s [id=alikafka_post-cn-****:tf-example:Topic:example-topic:LITERAL:Write] Apply complete! Resources: 8 added, 0 changed, 0 destroyed.Verify the result.
Use the terraform show command
Run the
terraform showcommand to view the permissions of the SASL user.terraform show# alicloud_alikafka_sasl_acl.default: resource "alicloud_alikafka_sasl_acl" "default" { acl_operation_type = "Write" acl_resource_name = "example-topic" acl_resource_pattern_type = "LITERAL" acl_resource_type = "Topic" host = "*" id = "alikafka_post-cn-****:tf-example:Topic:example-topic:LITERAL:Write" instance_id = "alikafka_post-cn-****" username = "tf-example" }Use the ApsaraMQ for Kafka console
Log on to the ApsaraMQ for Kafka console to view the permissions of the SASL user.
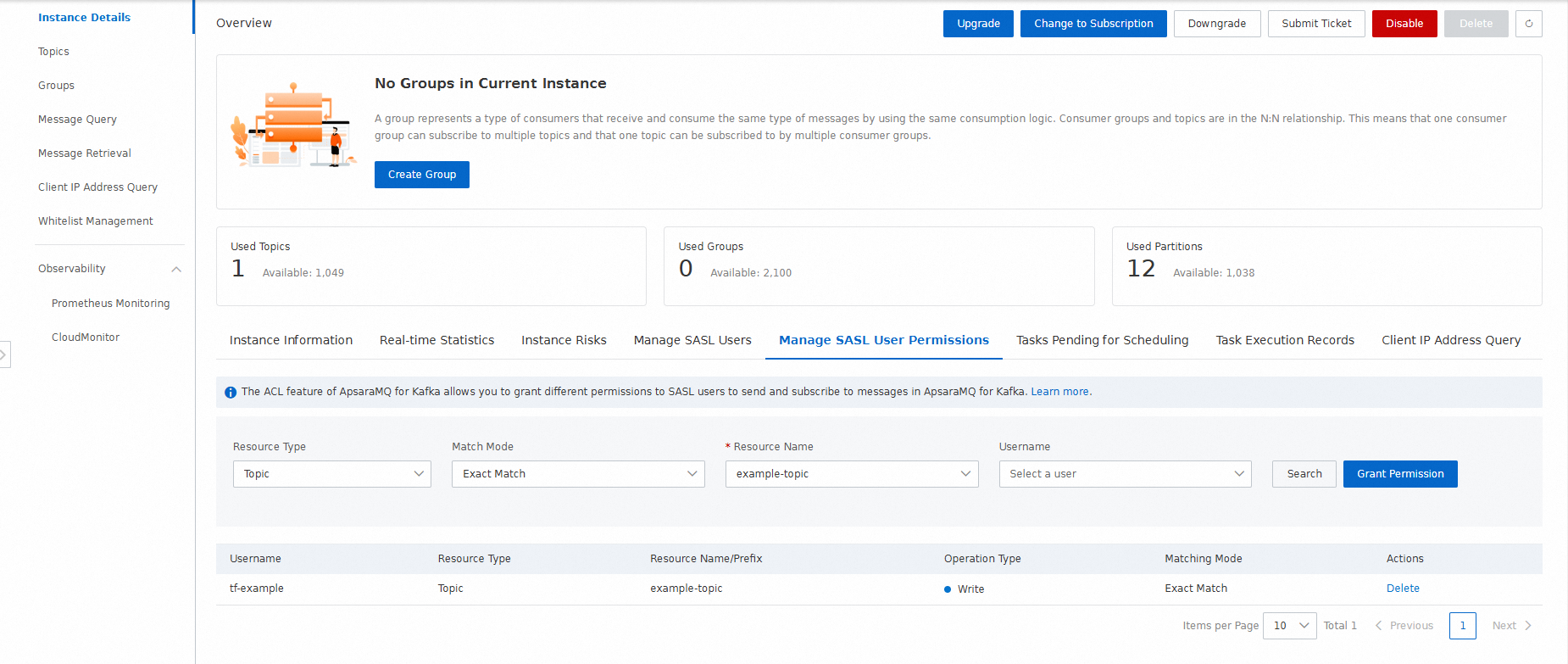
Query the permissions of a SASL user
In the main.tf configuration file, add the
data "alicloud_alikafka_sasl_users" "sasl_acls_ds"configuration item and configure the configuration item based on the following code snippet:data "alicloud_alikafka_sasl_acls" "sasl_acls_ds" { instance_id = "<The ID of the ApsaraMQ for Kafka instance>" username = "<The name of the SASL user>" acl_resource_type = "<The type of the resource with which the ACL is associated>" acl_resource_name = "<The name of the resource with which the ACL is associated>" output_file = "saslAcls.txt" }Create an execution plan and preview the changes.
terraform planRun the following command to create the resources:
terraform applyDuring the execution, enter
yesas prompted and press the Enter key. Wait until the command is executed. If the following information appears, the operation is successful:random_integer.default: Refreshing state... [id=****] data.alicloud_zones.default: Reading... alicloud_vpc.default: Refreshing state... [id=vpc-****] alicloud_security_group.default: Refreshing state... [id=sg-****] data.alicloud_zones.default: Read complete after 2s [id=****] alicloud_vswitch.default: Refreshing state... [id=vsw-****] alicloud_alikafka_instance.default: Refreshing state... [id=alikafka_post-cn-****] alicloud_alikafka_sasl_user.default: Refreshing state... [id=alikafka_post-cn-****:tf-example] data.alicloud_alikafka_sasl_acls.sasl_acls_ds: Reading... alicloud_alikafka_topic.default: Refreshing state... [id=alikafka_post-cn-****:example-topic] data.alicloud_alikafka_sasl_acls.sasl_acls_ds: Read complete after 0s [id=0] alicloud_alikafka_sasl_acl.default: Refreshing state... [id=alikafka_post-cn-****:tf-example:Topic:example-topic:LITERAL:Write] No changes. Your infrastructure matches the configuration. Terraform has compared your real infrastructure against your configuration and found no differences, so no changes are needed. Apply complete! Resources: 0 added, 0 changed, 0 destroyed.Verify the result. Run the
terraform showcommand to view the permissions of the SASL user.terraform show# data.alicloud_alikafka_sasl_acls.sasl_acls_ds: data "alicloud_alikafka_sasl_acls" "sasl_acls_ds" { acl_resource_name = "testTopic" acl_resource_type = "Topic" acls = [] id = "0" instance_id = "alikafka_post-cn-****" output_file = "saslAcls.txt" username = "tf-example" }
Clear resources
If you no longer require the preceding resources that are created or managed by using Terraform, run the following command to release the resources. For more information about the terraform destroy command, see Common commands.
terraform destroySample code
You can run the sample code with a few clicks.
Sample code
References
You can also grant permissions to SASL users in the ApsaraMQ for Kafka console or by calling API operations. For more information, see Grant permissions to SASL users and CreateAcl.
For information about other arguments provided by the
alicloud_alikafka_sasl_aclresource, see alicloud_alikafka_sasl_acl.