This topic describes how to create an account in a tenant.
Background information
Before you use a database, you must create an account that has the privilege to connect to the database in the tenant. The privileges of an account vary based on the account type. You must use an account with database operation privileges to log on to a database.
When you create an account in a MySQL tenant, you can associate the account with multiple databases. When you create an account in an Oracle tenant, the account has only privileges on the corresponding schema.
Prerequisites
Before you create an account in a tenant, make sure that the following conditions are met:
The current tenant is not in the Creating state.
The current tenant is not in the Deleting state.
The current tenant is not in the Deleted state.
Procedure
Log on to the ApsaraDB for OceanBase console.
In the left-side navigation pane, click Instances.
In the instance list, click the name of the target cluster instance to go to the Cluster Instance Workspace page.
In the left-side navigation pane, click Tenant Management. In the tenant list, click the name of the target tenant.
On the Tenant Workspace page, click Create Account in the upper-right corner and then configure the parameters.
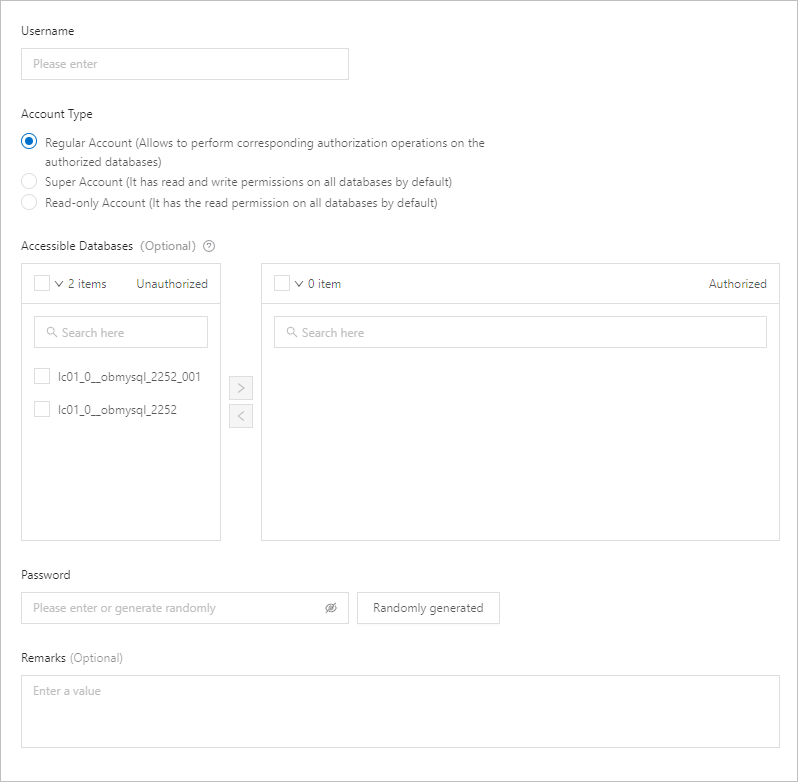
Parameter
Description
Username
The username of the account.
The username must start with a letter and be 2 to 32 characters in length. It can contain letters, hyphens (-), underscores (_), and digits, and cannot contain reserved keywords (case-insensitive), such as SYS, OCEANBASE, ROOT, OPERATOR, LBACSYS, ORAAUDITOR, OBMIGRATE, OMC, IDB_DDL, ODC_RND, ODC_DDL, and DWEXP.
Account Type
The type of the account. Valid values: Normal Account, Super Administrator, and Read-only Account.
A normal account has the privileges to execute DML and DDL statements in the database. For more information, see Account privileges.
By default, the super administrator has the read/write privileges on all databases.
By default, a read-only account has the read privilege on all databases.
NoteDML statements access and manipulate data in existing schema objects. DDL statements create, alter, and drop schema objects. For more information, see SQL statement overview.
Accessible Databases
This parameter is optional and is displayed only when a normal account is created in a MySQL tenant. You can grant privileges of the following types to an unauthorized account: Read-only, Read/Write, Only DDL, and Only DML.
In MySQL mode, you can grant the following database privileges to the account:
Read-only: CREATE SESSION, SELECT, and SHOW VIEW
Read/Write: ALL PRIVILEGES
Only DDL: CREATE, DROP, ALTER, SHOW VIEW, and CREATE VIEW
Only DML: SELECT, INSERT, UPDATE, DELETE, SHOW VIEW, and PROCESS
Password
The password of the account. You can enter a password or choose to randomly generate a password. The password must be 10 to 32 characters in length and contain three or more types of the following characters: uppercase letters, lowercase letters, digits, and special characters. The supported special characters are
! @ # $ % ^ & * ( ) _ + - =
Remarks (Optional)
Enter the remarks on the restore job. The length of the remarks cannot exceed 30 characters.
Click OK.