This topic describes how to add a whitelist for a self-managed Oracle database in a virtual private cloud (VPC).
Background
When you select Oracle >> OceanBase Oracle Mode for the assessment mode, the supported instance types are Self-Managed Database in VPC and Self-Managed Database with Public IP Address. OceanBase Migration Assessment (OMA) uses a public IP address to access the public network. Therefore, to use a public network data source, you must add a whitelist of public IP addresses for the data source. You do not need to add a whitelist when you use other types of data sources.
Procedure
If you select Oracle >> OceanBase Oracle Mode for the assessment mode and select Self-Managed Database in VPC for the instance type when you create an online assessment task, you must add the CIDR block of the OMA server to the whitelist of the corresponding database. This is because a self-managed database in VPC may have access restrictions on the Elastic Compute Service (ECS) platform but the data source for data assessment must be accessible to the IP address of the OMA server.
Copy the VPC ID selected from the VPC drop-down list.
Go to the Security Groups page of the ECS console. Select VPC ID from the drop-down list next to Create Security Group and paste the VPC ID to filter security groups.
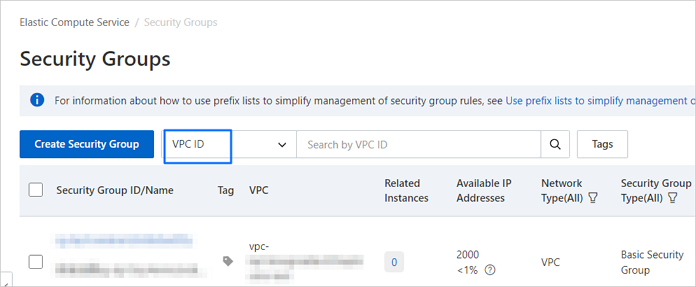
Click the name of the target security group to go to its details page.
Add an IP address on the Inbound tab.
Copy the IP address (CIDR block) of the OMA server from the Select Source Database Type dialog box in the OMA console.
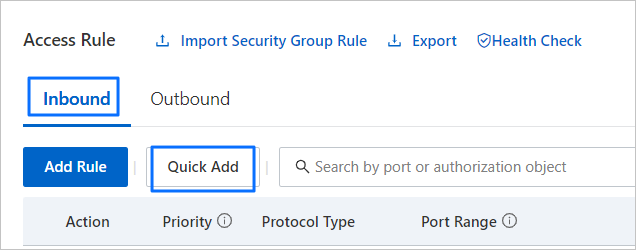
On the security group details page, click Quick Add on the Inbound tab in the Access Rule section.
You can also click Add Rule to manually add information such as Port Range and Authorization Object.
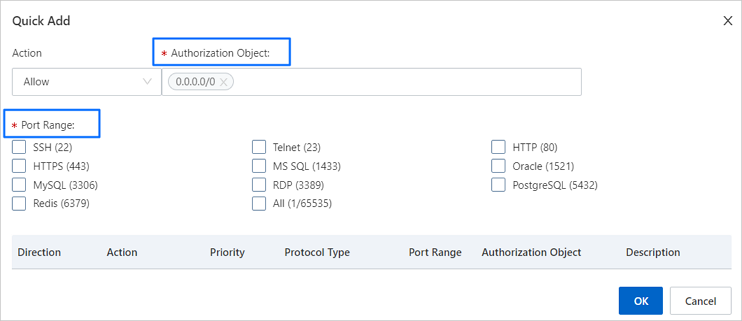
In the Quick Add dialog box, paste the IP address to the Authorization Object field and select a corresponding port range from the Port Range section.
For example, the port range may be 1521 for Oracle and 3306 for MySQL.
Click OK.