This topic describes how to integrate Web Application Firewall (WAF) to enhance the security of your APIs on API Gateway.
Overview
API Gateway provides core security features, such as authentication, anti-tampering, anti-replay, parameter validation, end-to-end signing, and throttling. However, to defend against sophisticated attacks, such as application-layer attacks (including the OWASP Top 10) and brute-force attacks, you can integrate WAF. This integration helps prevent intrusions and data breaches to better protect your business.
API Gateway and WAF are fully compatible. You can follow the steps in this topic to integrate WAF with your APIs.
Prerequisites
-
You have activated WAF.
-
You have published APIs on API Gateway.
Procedure
-
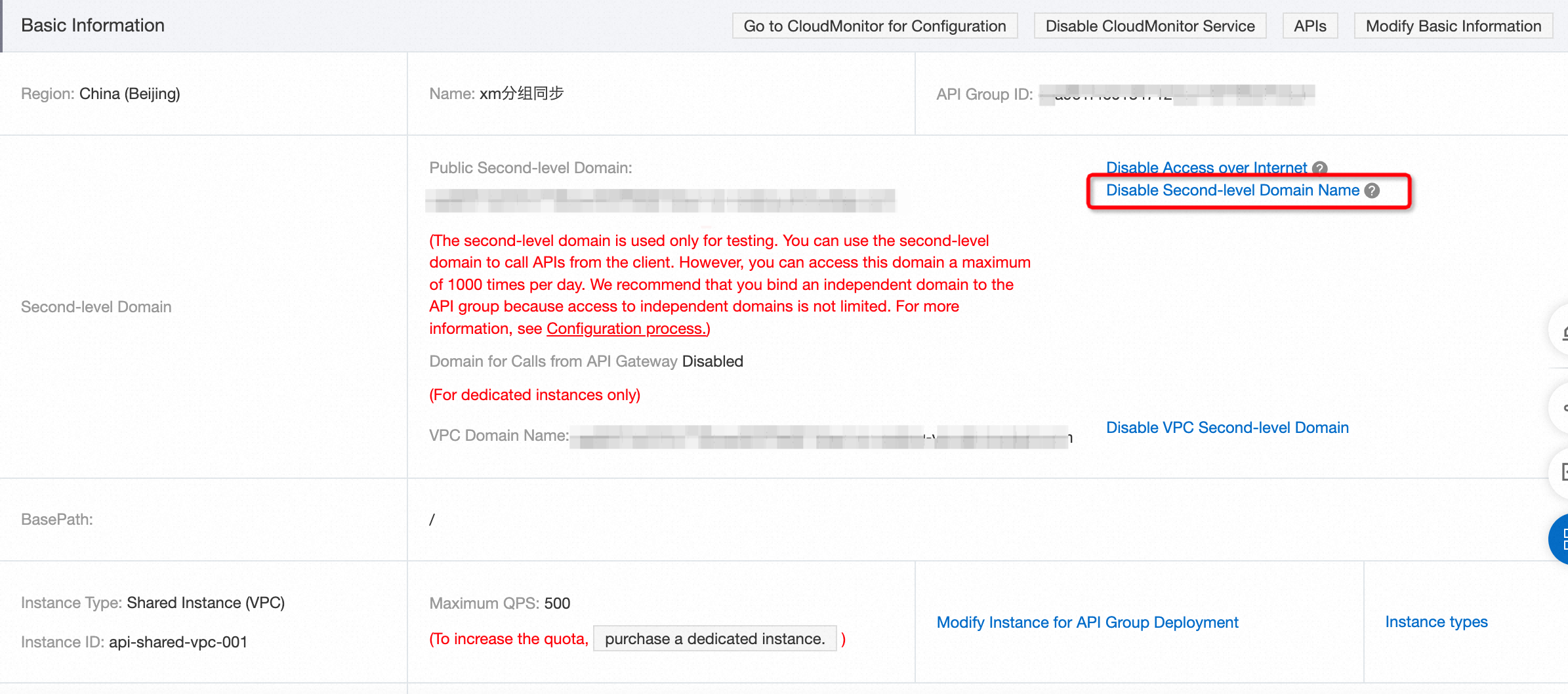
Bind a domain name to the API group. For details, see Make API calls through a custom domain name. After you successfully bind the domain name, the page appears as shown in the following figure:
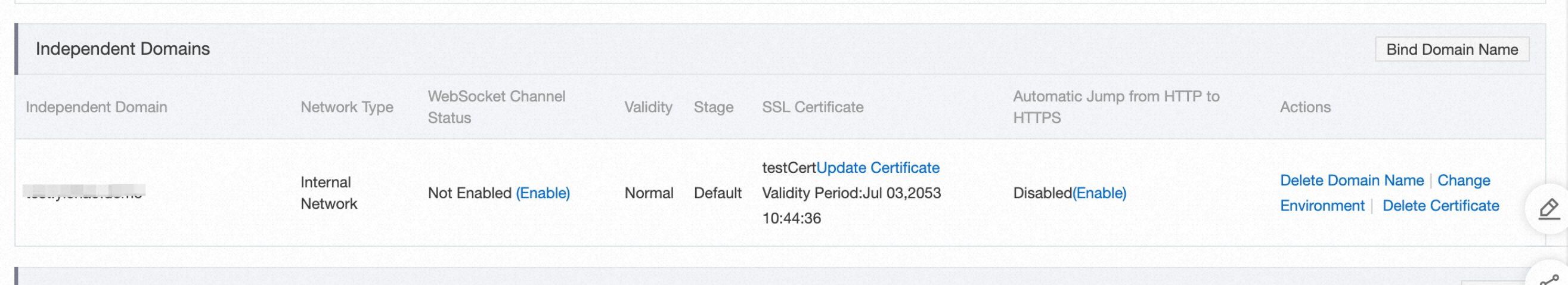 Important
ImportantWe recommend using a TXT record for domain verification to simplify the upcoming WAF configuration.
-
Go to the WAF console and add the domain name.
WAF 2.0
-
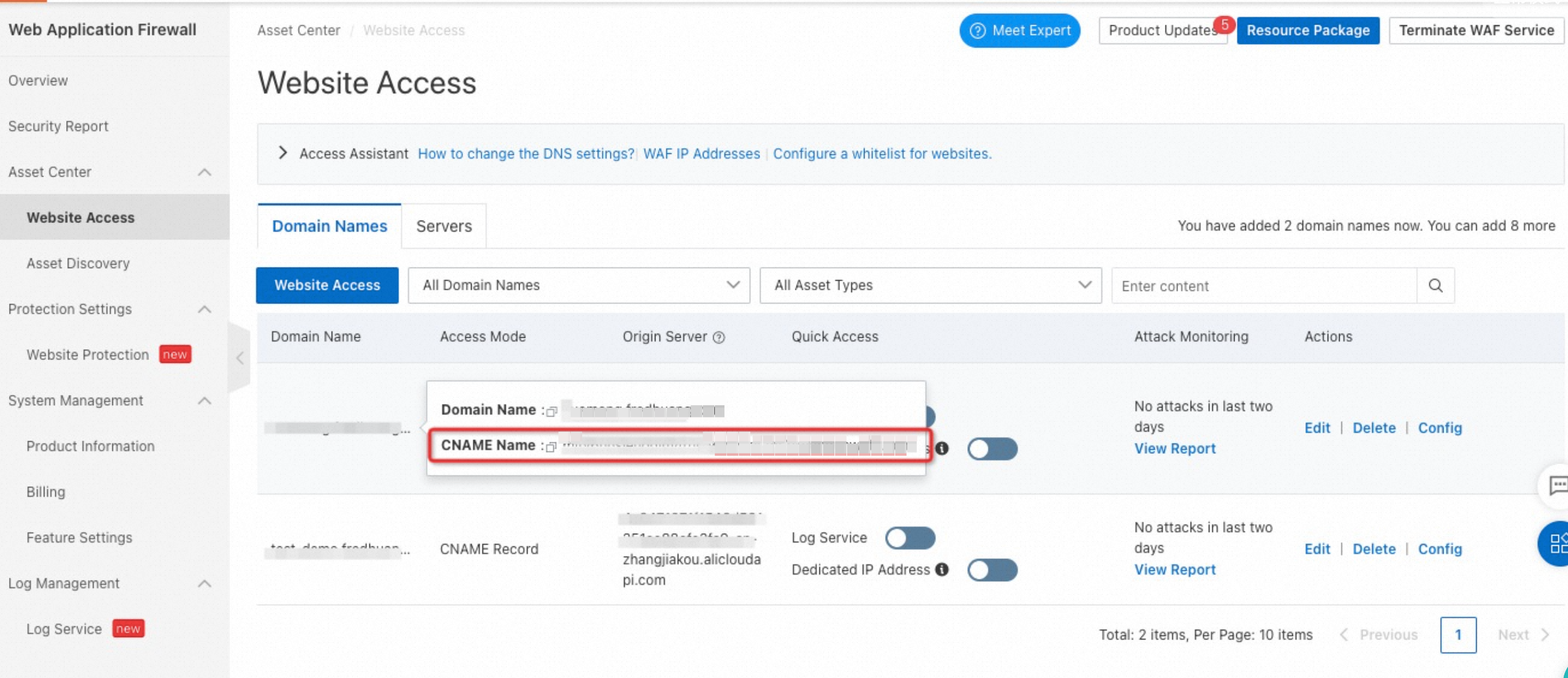
In the left-side navigation pane, choose Asset Center, and click Website Access. Configure the following parameters:
-
Domain Name: Enter the domain name that you bound to the API group in Step 1.
-
Protocol Type: Select the protocol that matches the API published in API Gateway.
-
Origin Server Address: Select Domain Name (Such as CNAME) and enter the public subdomain that API Gateway assigns to your API group.
-
-
Click Next and follow the prompts to add the site. After you add the site, add a CNAME record for your domain name to point it to the WAF CNAME address. This process routes your traffic through WAF.
WAF 3.0
-
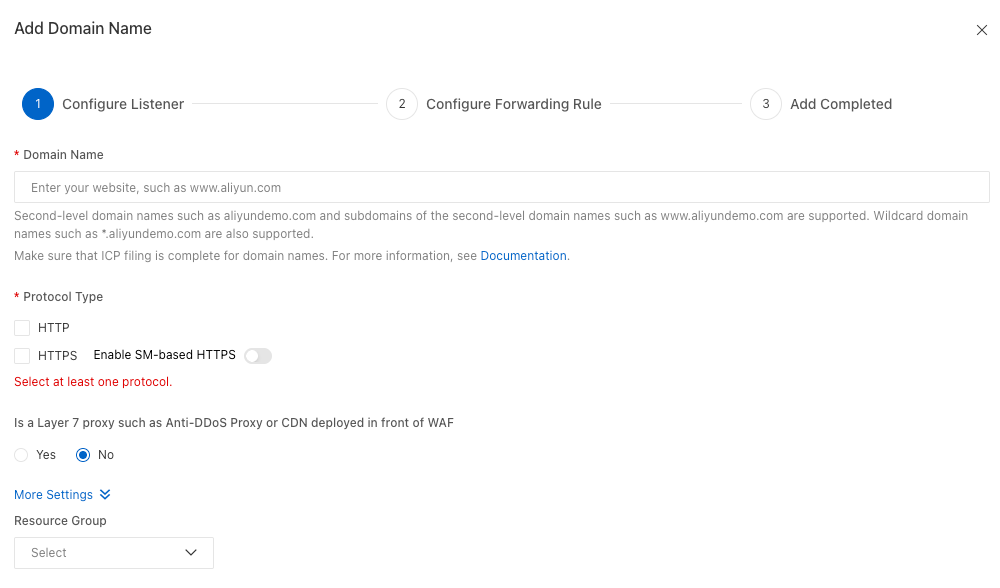
In the left-side navigation pane, click Onboarding. On the CNAME Record tab, click Add. For more information, see Add a domain name.
-
In the Configure Listener section, configure the following parameters:
-
Domain Name: Enter the domain name that you bound to the API group in Step 1.
-
Protocol Type: Select the protocol that matches the API published in API Gateway.
-
-
In the Configure Forwarding Rule section, configure the following parameters:
-
Origin Domain Name: Enter the public subdomain that API Gateway assigns to your API group.
-
-
-
-
Go to the API Gateway console and disable access to the group's public subdomain. This step prevents users from bypassing WAF and accessing your APIs directly. Once this access is disabled, direct requests to the public subdomain fail. Requests routed through your WAF-protected domain name are unaffected.