This topic describes how to view the attack protection reports of Anti-DDoS Pro and Anti-DDoS Premium for the last year.
Report statistics
Timestamp range:
Anti-DDoS Proxy (Chinese Mainland): Data for dates on or after August 8, 2024 is available.
Anti-DDoS Proxy (Outside Chinese Mainland): Data for dates on or after September 17, 2025 is available.
Data precision: Attack analysis is based on data sampling. The statistical results may be inaccurate.
View and download statistical reports
Go to the Statistical Reports page of the Traffic Security console.
Select an instance type: Anti-DDoS Proxy (Chinese Mainland) or Anti-DDoS Proxy (Outside Chinese Mainland).
Select an instance and a domain name, specify a timestamp range, and then click the
 icon.
icon.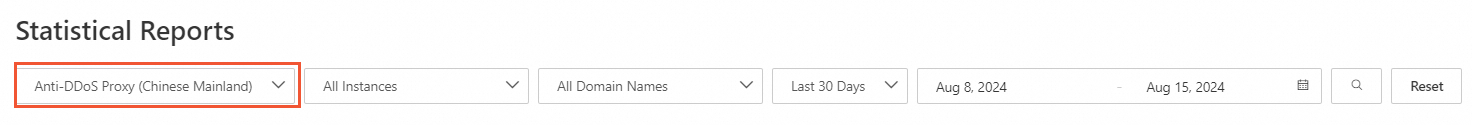 Important
ImportantInstance and domain name configuration:
All instances + All domain names: Queries network-layer and application-layer traffic statistics for all services.
All instances or a specific instance + No domain name: Queries network-layer traffic statistics for the specified instance or instances.
No instance + All domain names or a specific domain name: Queries application-layer traffic statistics for the specified domain name or domain names.
Not supported: No instance + No domain name.
Not supported: Some instances + Some domain names.
In the upper-right corner, click Export Report to export the report in image or PDF format.
Metric descriptions
Overall operational metrics
Metric | Description |
Data Metrics |
|
Traffic Scrubbing Events | The total number and type distribution of all scrubbing events. The types include volumetric, connection flood, and web resource exhaustion. Blackhole filtering events are not included. The displayed data varies based on the query object:
|
Protected Assets | The total number of protected assets. This data is independent of the specified timestamp range and reflects real-time data from the previous day (T-1).
|
Traffic metrics
Metric | Description |
Traffic Trend in bit/s |
|
Request Trend in QPS | This metric is displayed only if the query includes a domain name.
|
Top 5 Source Regions of Network Layer Attacks | This metric is displayed only if the query includes an instance. The top five source regions of attacks are ranked by the number of requests from source IPs.
Statistical logic:
|
Top 5 Source Regions of Application Layer Attacks | This metric is displayed only if the query includes a domain name. The top five source regions of attacks are ranked by the number of requests from source IPs, in QPS.
Statistical logic:
|
Attack distribution
Metric | Description |
Attack Type Distribution | The distribution of attacks based on the number of occurrences for each attack type. This includes sub-types of volumetric, connection flood, and web resource exhaustion attacks. Blackhole filtering events are not included. |
Top 10 Attack Source ISPs | The distribution of global ISPs for attack sources, based on the number of requests from source IPs in attack events. Attack events include scrubbing events and blackhole filtering events. |
Volumetric Attacks by Peak Attack Throughput | The number of events in different peak attack throughput ranges. Blackhole filtering events are not included. The ranges are: 0 Gbps to 30 Gbps, 30 Gbps to 100 Gbps, 100 Gbps to 300 Gbps, 300 Gbps to 600 Gbps, and over 600 Gbps. |
Attack Duration Distribution | The number of events in different attack duration ranges. This includes volumetric, connection flood, and web resource exhaustion events. Blackhole filtering events are not included. The ranges are: 0 to 30 minutes, 30 to 60 minutes, 1 to 3 hours, 3 to 12 hours, and over 12 hours. |
Attack ranking metrics
Metric | Description |
Top 20 Source IP Addresses by Peak Attack Throughput | This metric is displayed only if the query includes an instance. The top 20 source IP addresses with the highest peak attack throughput. The statistical logic is as follows:
|
Top 10 Destination IP Addresses by Peak Attack Throughput | This metric is displayed only if the query includes an instance. The top 10 destination IP addresses with the highest peak attack throughput. The statistical logic is as follows:
|
Top 10 Destination Domain Names by Peak Attack Throughput | This metric is displayed only if the query includes a domain name. The top 10 destination domain names with the highest peak attack throughput. The statistical logic is as follows:
|
Protection metrics
Metric | Description |
Top 10 Destination Ports by Attack | This metric is displayed only if the query includes an instance. The top 10 destination ports targeted by attacks. The statistical logic is as follows:
|
Defense Against Application Layer Attacks by Module | This metric is displayed only if the query includes a domain name. It shows which mitigation policies filtered the application-layer attacks. |
Attack events
This section lists all attack events for the selected instance or domain name within the specified time range. Click View Details in the Actions column of a target event to go to the Attack Analysis page for more event details.
References
For more information about the report metrics for Anti-DDoS Origin, see Statistical report (Anti-DDoS Origin).