An Application Load Balancer (ALB) instance can be integrated with an ingress gateway in a Service Mesh (ASM) instance to access an Alibaba Cloud Container Service for Kubernetes (ACK) cluster that uses the Terway network plug-in on the data plane. This feature simplifies service management, ensures the security of communications between services, and improves observability, reducing development and O&M workloads. This topic describes how to integrate an ALB instance with an ingress gateway.Service Mesh
Prerequisites
An ACK cluster is added to an ASM instance. The ASM instance and the ACK cluster meet the following requirements:
The ASM instance is of Enterprise Edition.
ACK cluster:
The Terway network plug-in is used.
The Cloud Controller Manager (CCM) component is of v1.9.3.313-g748f81e-aliyun or later. For more information, see Cloud Controller Manager.
The ALB Ingress controller is installed. For more information, see Manage components.
Automatic sidecar proxy injection is enabled for the default namespace. For more information, see the "Enable automatic sidecar proxy injection" section of the Manage global namespaces topic.
An ingress gateway is created. For this ingress gateway, CLB Instance Type is set to Private Access and Service Port is set to 80. For more information, see Create an ingress gateway.
Step 1: Deploy a sample application
Connect to the cluster based on the content in the kubeconfig file of the cluster on the data plane and then run the following command to deploy the Bookinfo application. For more information, see Deploy an application in an ASM instance.
kubectl apply -f https://raw.githubusercontent.com/istio/istio/master/samples/bookinfo/platform/kube/bookinfo.yamlStep 2: Create Istio resources
In this example, an Istio gateway and a virtual service are created for testing.
Create an Istio gateway.
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose .
On the Gateway page, click Create and configure the parameters shown in the following figure.
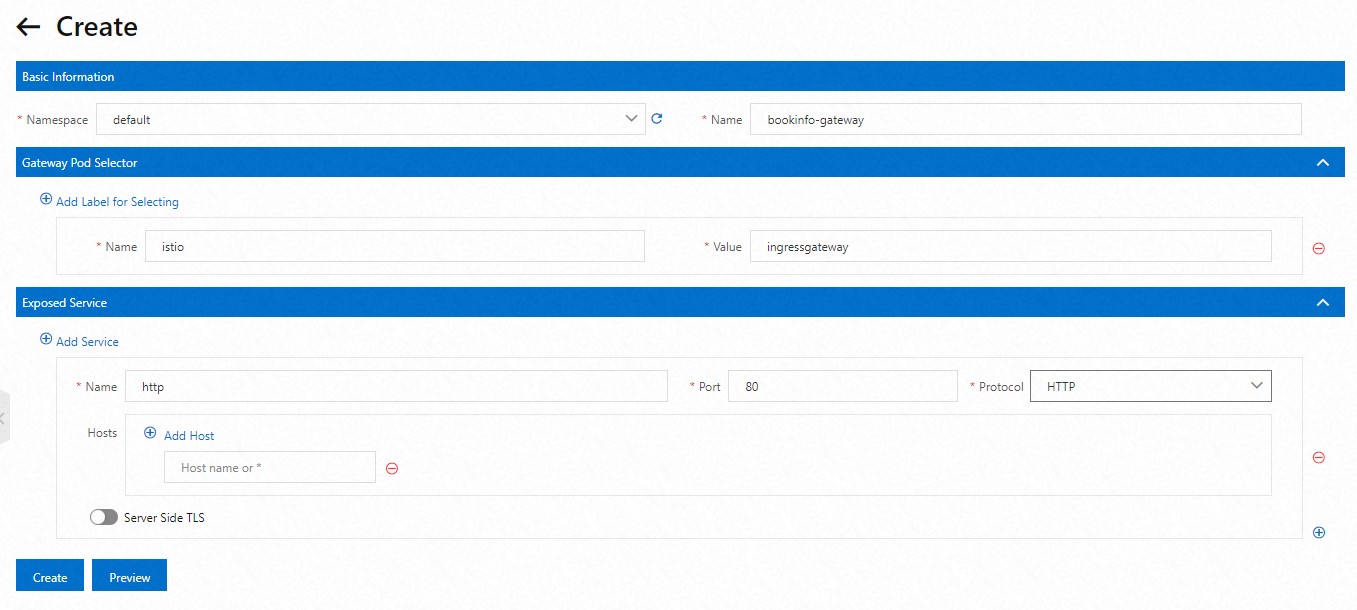
In the lower part of the Create page, click Preview to view the YAML file of the Istio gateway. After you confirm the information in the YAML file, click Submit. In the lower part of the Create page, click Create.
Create a virtual service and configure traffic routing.
On the details page of the ASM instance, choose in the left-side navigation pane.
On the VirtualService page, click Create to configure a virtual service for the bookinfo-gateway gateway.
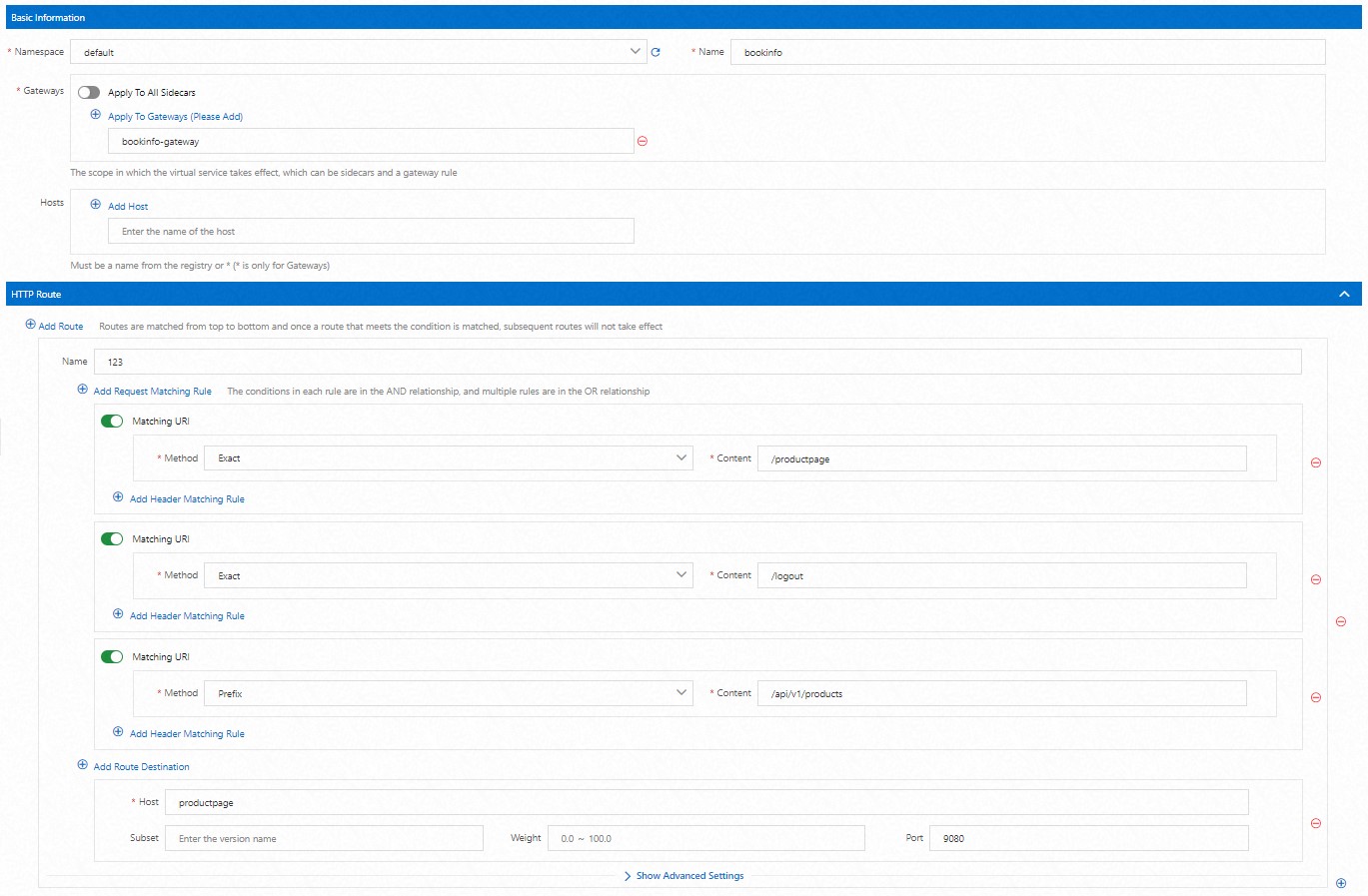
In the lower part of the Create page, click Preview to view the YAML file of the virtual service. After you confirm the information in the YAML file, click Submit. In the lower part of the Create page, click Create.
Step 3: Create an AlbConfig object
Scenario 1: You need to integrate an existing standard ALB instance with the ingress gateway
Obtain the ID of the ALB instance in the ALB console.
Create an alb-demo.yaml file that contains the following content.
Replace the value of
idin the config section with the ID of your ALB instance.apiVersion: alibabacloud.com/v1 kind: AlbConfig metadata: name: default spec: config: id: alb-xxxxx forceOverride: falseRun the following command to create an AlbConfig object:
kubectl apply -f alb-demo.yaml
Scenario 2: You need to create an ALB instance and integrate it with the ingress gateway
Create an alb-demo.yaml file that contains the following content. For more information, see Access Services by using an ALB Ingress.
Set the name of the automatically created ALB instance to alb-demo.
apiVersion: alibabacloud.com/v1 kind: AlbConfig metadata: name: default spec: config: name: alb-demo addressType: Internet zoneMappings: - vSwitchId: vsw-uf6ccg2a9g71hx8go**** - vSwitchId: vsw-uf6nun9tql5t8nh15****Parameter
Description
spec.config.nameThe name of the ALB instance that you want to create.
addressTypeThe type of IP address that the ALB instance uses to provide services. This parameter is required. Valid values:
Internet: The ALB instance uses a public IP address. The domain name of the Ingress is resolved to the public IP address of the ALB instance. Therefore, the ALB instance is accessible over the Internet. This is the default value.
Intranet: The ALB instance uses a private IP address. The domain name of the Ingress is resolved to the private IP address. Therefore, the ALB instance is accessible only within the virtual private cloud (VPC) where the ALB instance is deployed.
zoneMappingsThe IDs of the vSwitches that are used by the ALB Ingress. You must specify at least two vSwitch IDs and the vSwitches must be deployed in different zones. The zones of the vSwitches must be supported by ALB Ingresses. This parameter is required. For more information about the regions and zones that are supported by ALB Ingresses, see Supported regions and zones. For more information about how to create a vSwitch, see Create and manage a vSwitch.
Run the following command to create an AlbConfig object:
kubectl apply -f alb-demo.yaml
Step 4: Create an IngressClass resource
Create an alb.yaml file that contains the following content:
apiVersion: networking.k8s.io/v1 kind: IngressClass metadata: name: alb spec: controller: ingress.k8s.alibabacloud/alb parameters: apiGroup: alibabacloud.com kind: AlbConfig name: default scope: ClusterRun the following command to create an IngressClass resource:
kubectl apply -f alb.yamlExpected output:
ingressclass.networking.k8s.io/alb created
Step 5: Create an Ingress instance
The ingress gateway is created in the istio-system namespace. You need to create an Ingress instance in the istio-system namespace in the ACK cluster on the data plane. The port number is 80, which is the same as that specified when you create the ingress gateway.
Create an asm-gateway-ingress.yaml file that contains the following content:
apiVersion: networking.k8s.io/v1 kind: Ingress metadata: name: asm-gateway-ingress namespace: istio-system spec: ingressClassName: alb rules: - http: paths: - backend: service: name: istio-ingressgateway port: number: 80 path: /* pathType: ImplementationSpecificRun the following command to create an Ingress instance:
kubectl apply -f asm-gateway-ingress.yaml
Step 6: Access the ingress gateway
Run the following command to query the endpoint of the Ingress instance:
kubectl get ing -n istio-systemExpected output:
NAME CLASS HOSTS ADDRESS PORTS AGE asm-gateway-ingress alb * alb-xxxx.xxxx.alb.aliyuncs.com 80 18hIn the output, you can see that the endpoint of the Ingress instance is
alb-xxxx.xxxx.alb.aliyuncs.com.Access the ingress gateway by using one of the following methods:
Method 1: Enter
http://alb-xxxx.xxxx.alb.aliyuncs.com/productpagein a browser to access the ingress gateway. alb-xxxx.xxxx.alb.aliyuncs.com is the endpoint of the Ingress instance obtained in the previous step.Method 2: Log on to the ALB console to obtain the public IP address of the ALB instance and use it to access the ingress gateway. If the ALB instance is bound to a domain name, you can use the domain name to access the ingress gateway.