This topic describes how to use the content analysis feature of container images in Container Registry to enhance the capability of checking image security and compliance.
Feature description
This feature is available only in the following regions: China (Hangzhou), China (Shanghai), China (Beijing), China (Shenzhen), China (Hong Kong), Singapore, US (Virginia), and Germany (Frankfurt).
Image content analysis
Image content analysis is used to audit and analyze the composition and characteristics of container images. This feature can detect vulnerabilities and compliance of images, and manage and track image tags. This way, you can optimize component dependencies and improves security and performance of containers. Image content analysis ensures that containerized applications can comply with standards and reduce risks. This feature also helps you implement efficient management and transparent software supply chain tracking.
Step 1: Create a content analysis rule
Procedure:
Log on to the Container Registry console.
In the top navigation bar, select a region.
In the left-side navigation pane, click Instances.
On the Instances page, click the Enterprise Edition instance that you want to manage.
In the left-side navigation pane of the Overview page, choose . On the Content Analysis page, click Create Rule. In the dialog box that appears, configure the following parameters and then click OK to complete the creation of the rule.
Parameter
Description
Rule Name
Specify a name for the rule.
Analytics Method
The Automatic Analysis method is automatically used.
Analytics Scope
Select a content analysis scope. Valid values:
Namespace: Select a namespace. By default, all repositories in the namespace are analyzed.
Repository: Select a repository that you want to analyze.
Step 2: Trigger content analysis
After you create a content analysis rule, you can perform content analysis on container images within the analysis scope.
Automatic analysis: When you manually push an image to an image repository that belongs to the specified analysis scope, the system automatically starts content analysis on the image. The automatic analysis method is not applicable to existing images.
Manual analysis: You can select to trigger the analysis of all images or specific images within the specified analysis scope.
Analyze all images within the scope.
In the left-side navigation pane of the Overview page, choose .
In the Analytics Rules section of the Content Analysis page, find the analytics rule that you want to use and then click Scan in the Actions column.
In the Task List section of the Content Analysis page, find the scan task and click View Task in the Actions column to view the scan information.
Analyze specific images within the scope.
On the Repositories page, click the name of the image repository that you want to analyze. On the repository details page, click Tags in the left-side navigation pane.
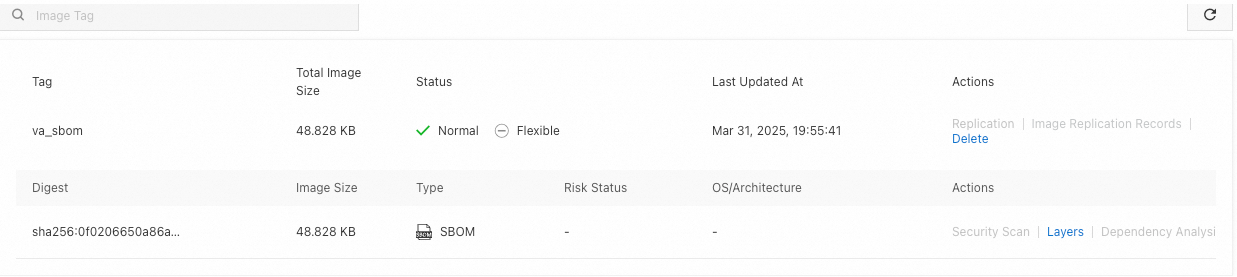
On the Tags page, find the tag that you want to analyze and click Dependency Analysis in the Actions column. On the Dependency Analysis page, click Analyze Now.
After the analysis is completed, in addition to the content analysis result, an SBOM OCI (Open Container Initiative) artifact with the _sbom suffix is generated. You can use OCI Registry as Storage (ORAS) and the image tag to obtain the SBOM file of the image. For more information, see Use ORAS and the image tag.
Step 3: View the analysis result
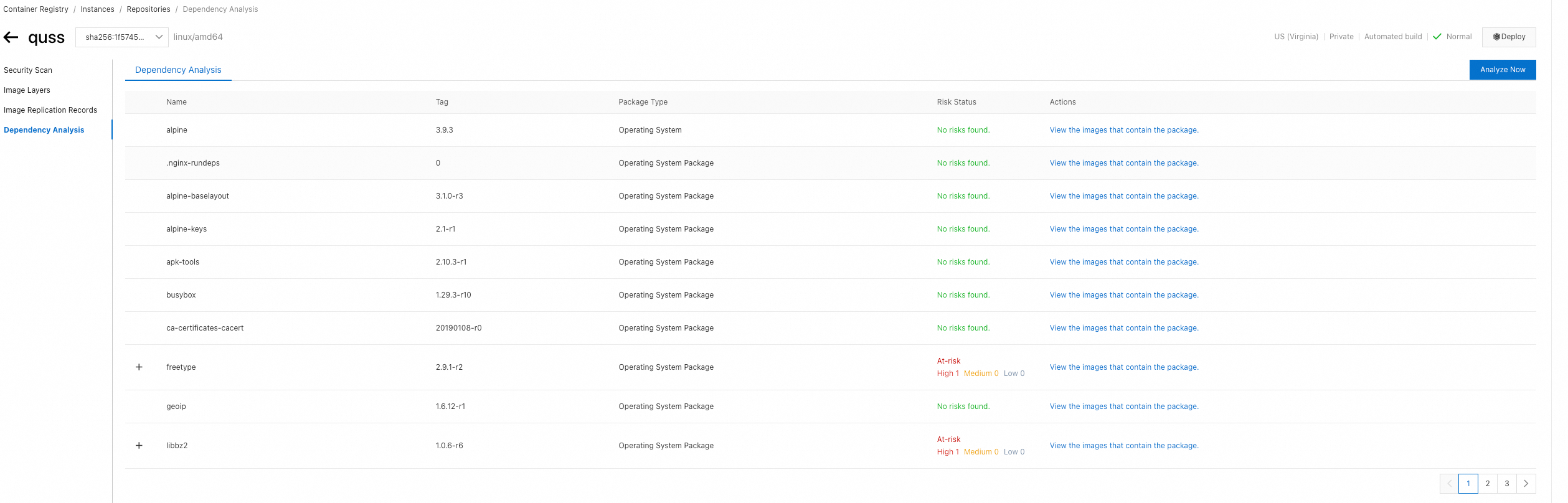
In the image content analysis result, you can view the components of the operating system package of the image tag, the dependencies of the components, tag information, risk status, and all image tags that contain the operating system package.
On the Repositories page, click the name of the image repository that you want to analyze. On the repository details page, click Tags in the left-side navigation pane.
On the Tags page, find the tag that you want to analyze and click Dependency Analysis in the Actions column.
On the Dependency Analysis page, view the content analysis result of the image. The content analysis result includes Package Type (Operating System, Operating System Package, and Language Package), the Tags of the packages, and the Risk Status of the packages.
NoteDue to the limits of some operating systems, images of those operating systems cannot be scanned. You can submit a ticket to request for a scan.
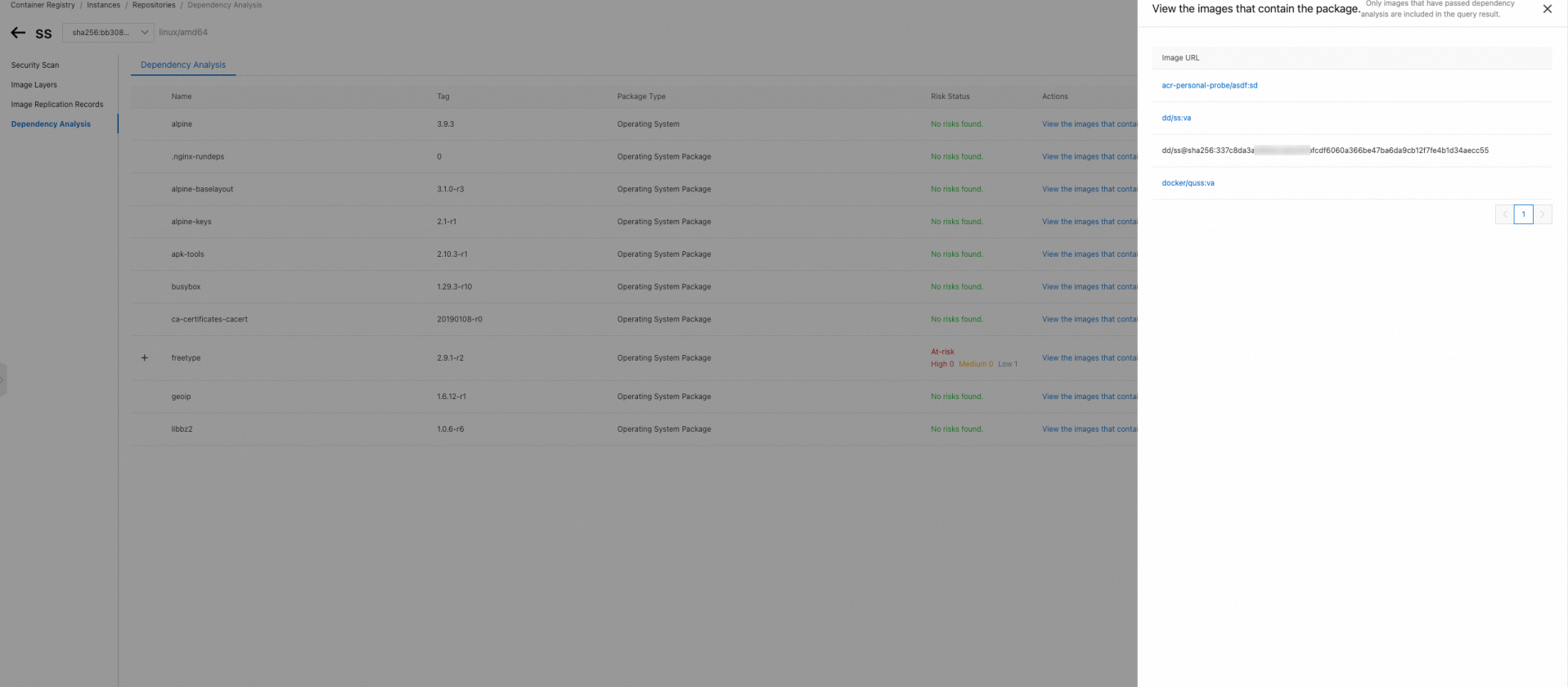
In the Actions column that corresponds to the package, click View the images that contain the package. Then, in the panel that appears, you can view all image tags that contain the operating system package within the analysis scope.
NoteThe query result displays the image tags that meet one of the following requirements and contain the package:
The image was analyzed.
The image was not analyzed, but the digest of an image layer is the same as the digest of the layer where the queried package is located. This indicates the image layer is used by multiple images.
In addition, the current content analysis also queries the image tags that are overwritten when repeated images are pushed and multi-arch images. Those images are listed in the form of repo@digest.
SBOM files
An SBOM ( software bill of materials) is a list of software components and similar to a bill of materials in manufacturing. An SBOM describes the components and version of a software and the dependencies of the components. It is essential for understanding the software structure and ensuring the security and compliance of the software. An SBOM file helps you streamline audit processes, improve emergency response capabilities, support transparent software supply chains, and optimize development and maintenance processes. The following code provides an example of an SBOM file:
{
"bomFormat": "CycloneDX", # The type of the SBOM format.
"specVersion": "1.3",
"serialNumber": "urn:uuid:47c90508-80a5-4cec-91f3-9920d765e3b5",
"version": 1,
"components": [ # A list of software components and the type, name, version, license, and package URL of each component.
{
"type": "library",
"name": "openssl",
"version": "1.1.1",
"licenses": [
{
"license": {
"id": "Apache-2.0"
}
}
],
"purl": "pkg:generic/openssl@1.1.1"
},
{
"type": "library",
"name": "curl",
"version": "7.76.1",
"licenses": [
{
"license": {
"id": "MIT"
}
}
],
"purl": "pkg:generic/curl@7.76.1"
}
],
"dependencies": [ # The dependencies between the components.
{
"ref": "pkg:generic/openssl@1.1.1",
"dependsOn": []
},
{
"ref": "pkg:generic/curl@7.76.1",
"dependsOn": [
"pkg:generic/openssl@1.1.1"
]
}
]
}
Use ORAS to obtain the SBOM file of an image
Prerequisites
An ORAS client is installed on your on-premises machine and is connected to Container Registry. For more information about how to install an ORAS client, see Installation.
The region to which the Container Registry Enterprise Edition instance belongs supports the SBOM content analysis feature. For more information about the regions that support the SBOM content analysis feature, see Feature description.
Use ORAS and the image tag
You must append the _sbom suffix to the image tag when you use this method to obtain the SBOM file of an image.
Run the following command to log on to your image repository:
oras login --username=<Username that is used to log on to the image repository> <Name of the Enterprise Edition instance>-registry.-<Region where the Enterprise Edition instance resides>.cr.aliyuncs.com Password: Login SucceededObtain the SBOM file.
oras pull <Name of the Enterprise Edition instance>-registry.<Region where the Enterprise Edition instance resides>.cr.aliyuncs.com/<Namespace name>/<Image repository name>:<Image tag>_sbom
Use ORAS
Run the following command to log on to your image repository:
oras login --username=<Username that is used to log on to the image repository> <Name of the Enterprise Edition instance>-registry.-<Region where the Enterprise Edition instance resides>.cr.aliyuncs.com Password: Login SucceededObtain the image digest ID.
oras discover <Name of the Enterprise Edition instance>-registry.<Region where the Enterprise Edition instance resides>.cr.aliyuncs.com/<Namespace name>/<Image repository name>:<Image tag>Expected output:
<Name of the Enterprise Edition instance>-registry.<Region where the Enterprise Edition instance resides>.cr.aliyuncs.com/<Namespace name>/<Image repository name>@sha256:1f5745d79a9f820f5bXXXXXXXXXX5f626eb49aff9 └── application/vnd.cyclonedx+json └── sha256:0f0206650a86a16XXXXXXXX3891b22a9d649501229f83Obtain the SBOM file.
oras pull <Name of the Enterprise Edition instance>-registry.<Region where the Enterprise Edition instance resides>.cr.aliyuncs.com/<Namespace name>/<Image repository name>@sha256:0f0206650a86a16XXXXXXXX3891b22a9d649501229f83